New Waves of Scans Detected by an Old Rule
Who remembers the famous ShellShock (CVE-2014-6271)? This bug affected the bash shell in 2014 and was critical due to the facts that it was easy to exploit and that bash is a widespread shell used in many tools/applications. So, at this time, I created an OSSEC alerts to report ShellShock exploitation attempts against my servers. Still today, I'm getting a hit on this rule from time to time.
But, for 15 days, I started to get more alerts like this one:
Received From: (xxxx) x.x.x.x->/www/log/xxxxxxx.access
Rule: 100705 fired (level 10) -> "Shellshock Attempt"
Src IP: x.x.x.x
Portion of the log(s):
x.x.x.x - - [04/Apr/2019:07:31:19 +0200] "GET /type.php?template=tag_(){};@unlink(_FILE_);assert($_POST[T00ls]);{//../rss HTTP/1.1" 301 604 "http://xxxxxxx" "Mozilla/5.0 (compatible; Baiduspider/2.0; +http://www.baidu.com/search/spider.html\xa3\xa9"
This rule fired 34 times since mid-March and I'm still getting, at least, one per day. This query is related to CVE-2018-19127 which affects phpcms[1]. By exploiting the vulnerability, the attackers get a webshell on the server (details are available on a Github page[2]). Some details about the hits I found:
Three different User-Agents have been used:
Mozilla/4.0 (compatible; MSIE 9.0; Windows NT 6.1) 24 Mozilla/5.0 (compatible; Baiduspider/2.0; +http://www.baidu.com/search/spider.html\xa3\xa9 2 python-requests/2.21.0 8
Scan sources are clearly identifiable:
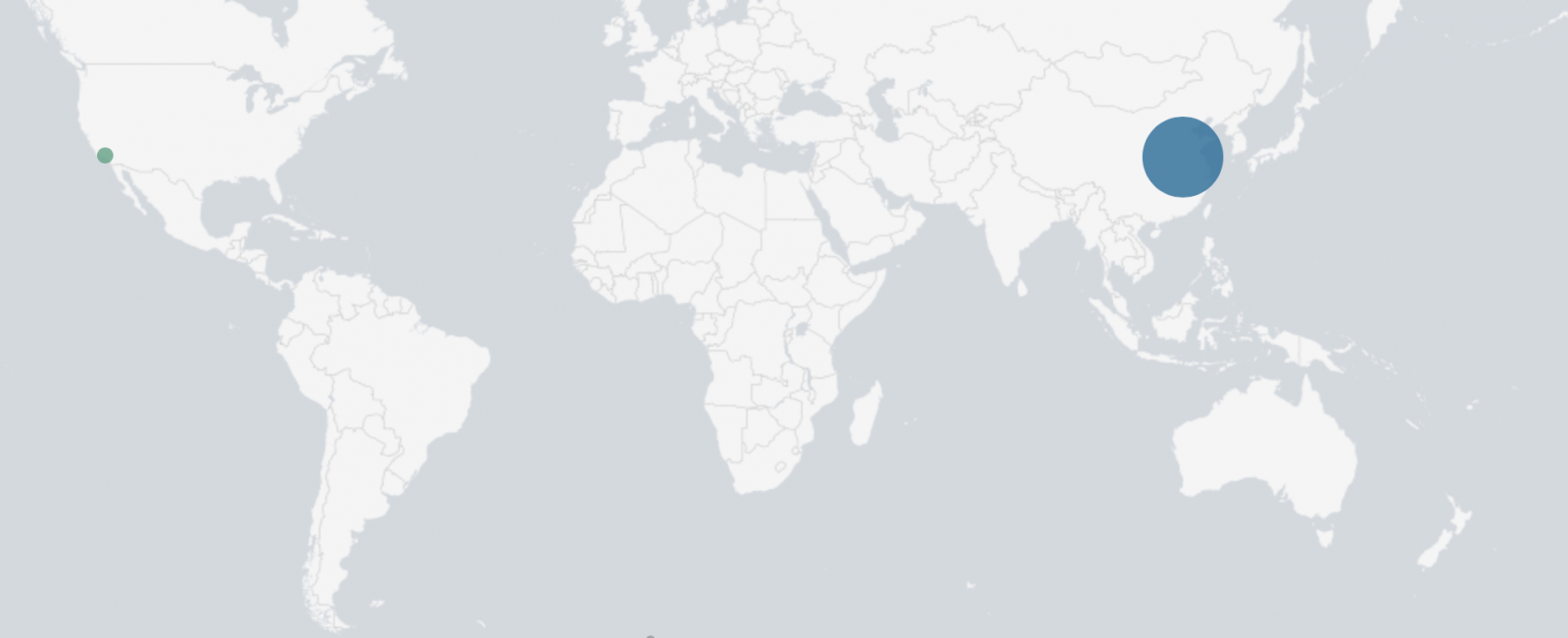
The scan in itself is not critical (except if you're still running a vulnerable version of phpcms of course) but what's interesting here? An alert created in your SIEM or log management solution a long time ago can still be relevant!
[1] http://www.cmsmatrix.org/matrix/cms-matrix/phpcms#
[2] https://github.com/ab1gale/phpcms-2008-CVE-2018-19127
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments