Name All the Things!
With our more and more complex environments and processes, we have to handle a huge amount of information on a daily basis. To improve the communication with our colleagues, peers, it is mandatory to speak the same language and to avoid ambiguities while talking to them. A best practice is to apply a naming convention to everything that can be labeled. It applies to multiple domains and not only information security. Examples:
- Computers (hosts)
- People (logins, email addresses, profiles)
- Programs & source code (functions, classes and variables names)
- Files & directories
- Databases (index, fields, ...)
- ...
A good naming convention is the one that is approved by all the parties and that will help you to perform your job better. If everybody is free to define a new one (while I was working for a company in Belgium, the servers were named with Belgian beers), there are some rules to follow. The example of Belgian beers is a good one: even we have many beers, a big organization with plenty of servers will be limited in the choice of names. Some names will be very simple, other too complex. Here are some rules to follow if you need to implement a naming convention:
- Choose easily and readable identifier names
- Favor readability over brevity
- Do not non-alphanumeric characters (stick to '[a-z][0-9][-_]')
- Avoid using identifiers that conflict with keywords of widely used terms
- Keep it in "English"
Some rules are more specific to certain types of data. Example for files and directories, use timestamps like 'YYYYMMDDHHMMSS' in the beginning of file names to have an automatic order. Prepending names with the project number or the customer's ID can be useful to find quickly details about a customer.
In the security landscape, we can apply naming conventions to many "objects" or "assets". In the configuration of security tools, objects must respect a naming convention. Examples:
- Objects in a firewall configuration
- Rules in an IDS server
- Groups and IOCs' in a threat intelligence solution
- In Forensics investigation (files, evidences)
This sounds easy to implement but it's not always the case. There are also bad examples like the anti-virus vendors who often use their own names to identify a piece of malicious code. Have a look at a sample report on VT to have an idea of the disaster:
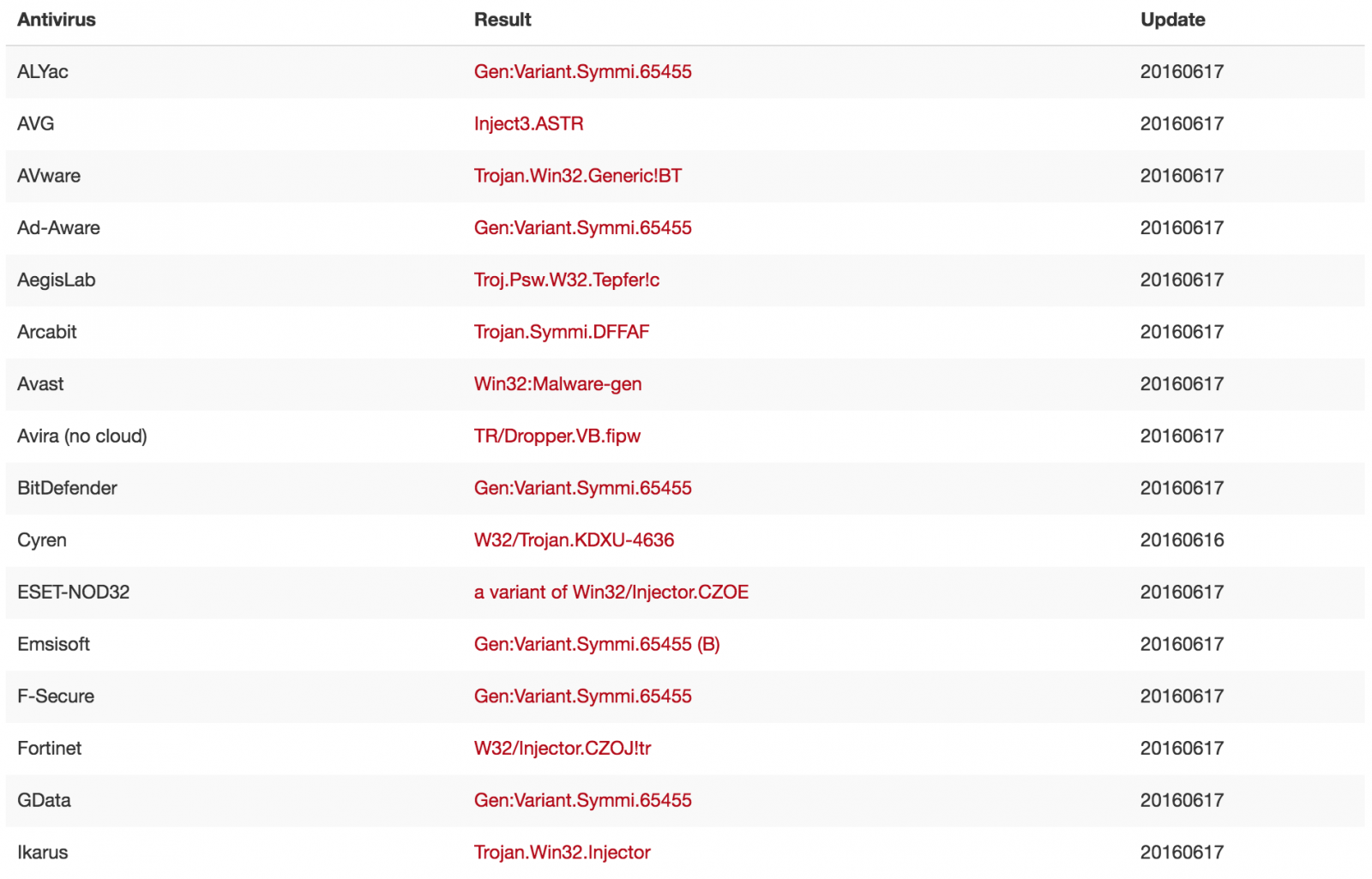
This isn't a recent issue, it was already discussed in 1991(!): http://www.caro.org/articles/naming.html.
And you? Do you have good rules to share to build a naming convention? What did you normalize? Feel free to share.
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Correct: YYYY-MM-DD,HH.MM.SS.
Wrong: YYYDDMM...
Anonymous
Jul 15th 2016
9 years ago
Anonymous
Jul 15th 2016
9 years ago
Anonymous
Jul 15th 2016
9 years ago