Malspam pushing Lokibot malware
Introduction
I've frequently seen malicious spam pushing Lokibot (also spelled "Loki-Bot") since 2017. This year, I've written diaries about it in February 2018 and June 2018. I most recently posted an example to my blog on 2018-11-26. This type of malicious spam shows no signs of stopping, so here's a quick diary covering an example from Monday 2018-12-03.
The email
Templates for malicious spam pushing Lokibot vary, and the example from Monday 2018-12-03 was disguised as a purchase quotation. The email contained an Excel spreadsheet with a macro designed to infect vulnerable Windows hosts with Lokibot malware. Potential victims need to click through warnings, so this is not an especially stealthy method of infection.

Shown above: Screenshot of the email with an attached Excel spreadsheet.
Infection traffic
A macro from the Excel spreadsheet retrieved Lokibot malware using HTTPS from a URL at a.doko[.]moe. I used Fiddler to monitor the HTTPS traffic and determine the URL. The HTTPS request to a.doko[.]moe had no User-Agent string. If you use curl to retrieve the binary, you must use the -H option to exclude the User-Agent line from your HTTPS request.
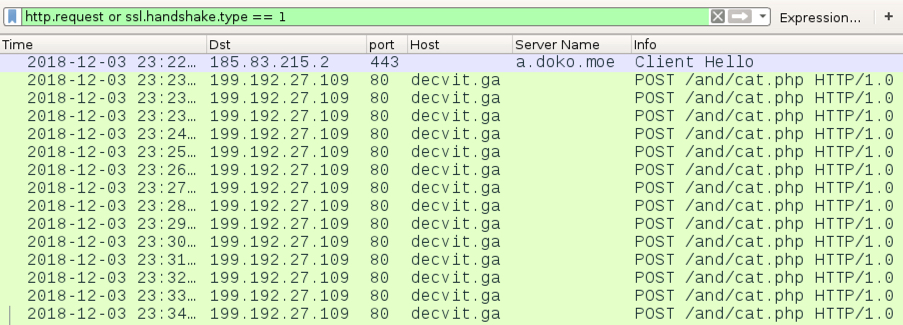
Shown above: Traffic from the infection filtered in Wireshark.
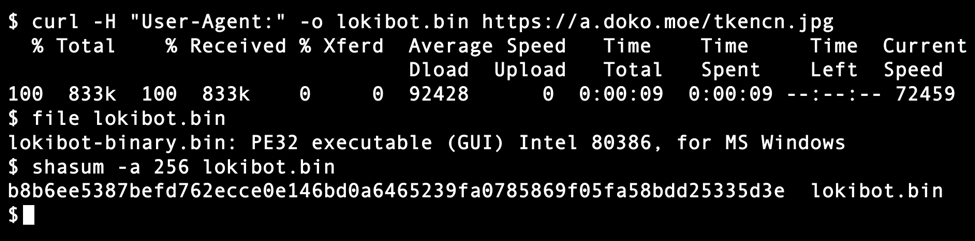
Shown above: Using curl to retrieve the Lokibot malware binary from a.doko[.]moe.

Shown above: Post-infection traffic from the Lokibot-infected Windows host.
Forensics on the infected host
The infected Windows host made Lokibot persistent through a Windows registry update. This registry update was quite similar to previous Lokibot infections I've generated in my lab environment. In this example, the infected host also had a VBS file in the Windows menu Startup folder. This pointed to another copy of the Lokibot malware executable; however, that executable had deleted itself during the infection. The only existing Lokibot executable was in the directory path listed in the associated Windows registry entry.
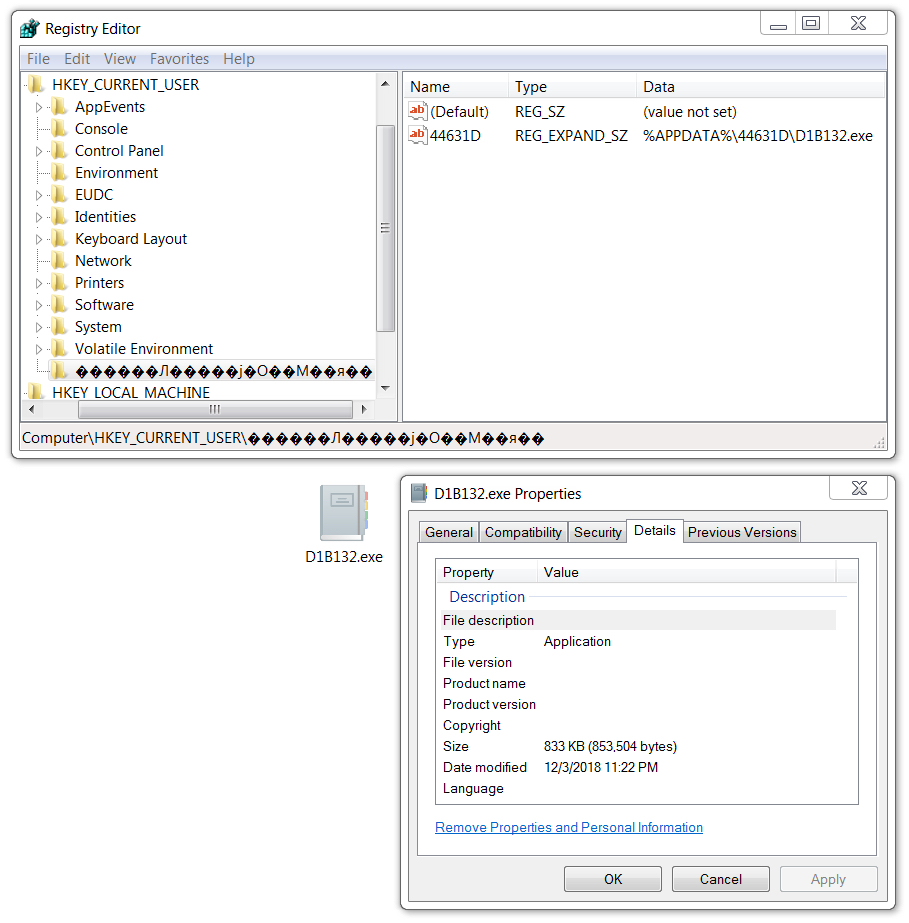
Shown above: Windows registry update to keep Lokibot persistent.

Shown above: VBS file in the Startup menu folder specifying a location where the malware had deleted itself.
Indicators
The following are indicators from an infected Windows host. Any URLs, IP addresses, and domain names have been "de-fanged" to avoid any issues when viewing today's diary.
Traffic from an infected windows host:
- 185.83.215[.]3 port 443 - a.doko[.]moe - GET /tkencn.jpg (encrypted HTTPS traffic)
- 199.192.27[.]109 port 80 - decvit[.]ga - POST /and/cat.php
Malware from an infected windows host:
SHA256 hash: 58cea3c44da13386b5acfe0e11cf8362a366e7b91bf9fc1aad7061f68223c5a8
- File size: 853,504 bytes
- File name: 62509871.xls
- File description: Attached Excel spreadsheet with macro to retrieve Lokibot
SHA256 hash: b8b6ee5387befd762ecce0e146bd0a6465239fa0785869f05fa58bdd25335d3e
- File size: 853,504 bytes
- File location: hxxps://a.doko[.]moe/tkencn.jpg
- File location: C:\Users\[username]\AppData\Roaming\44631D\D1B132.exe
- File location: C:\Users\[username]\AppData\Roaming\sticik\stickiy.exe (deleted itself during the infection)
- File description: Lokibot malware binary
Final words
Email, pcap, and malware for the infection can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments