Look at the same phishing campaign 3 months apart
While going through a batch of malicious e-mails, which were caught by my mail filters in March, I noticed a simple phishing e-mail, which carried an entire credential-stealing page in its attachment. This, although interesting in its own way, would not be that unusual[1,2]. While I was analyzing it, however, I found that a nearly identical e-mail message, which was obviously part of the same campaign, was uploaded to Any.Run[3] back in January. Since I had two samples from nearly 3 months apart, I thought it might be interesting to take a look at how much has changed in this phishing campaign over that time.
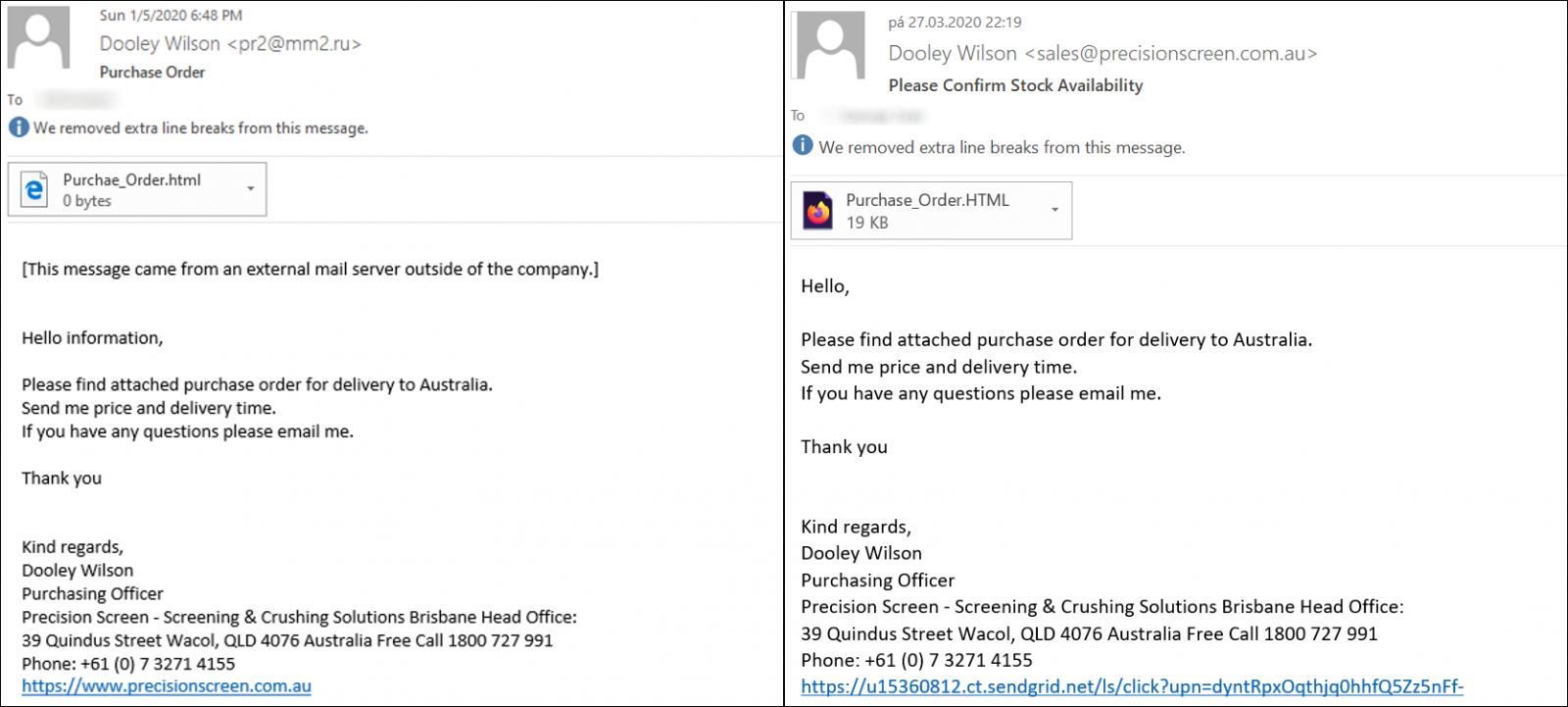
The message from Any.Run, which may be seen on the left, was delivered on January 5th and came from a SMTP server of a Russian hospital. The phishers probably used a compromised account on the server as the same e-mail address was used to push other phishing e-mails as well around the same time[4]. The more recent message was sent through sendgrid.net – an e-mail marketing platform.
The signature seems to belong to a real person from a company in Australia, which really uses the domain precisionscreen[.]com[.]au and this lends the messages at least some credibility.
UPDATE: Howard Solomon, aka @HowardITWC, kindly mentioned to me that the company in question says on its website that phishing e-mails trying to appear as their communication are being sent under several names, Dooley Wilson being one of them, and that these are all illegitimate. Howard further pointed that Arthur "Dooley" Wilson was the actor who played Sam the piano player in the movie "Casablanca" and it is possible that this was intended as a joke by the author of the phishing.
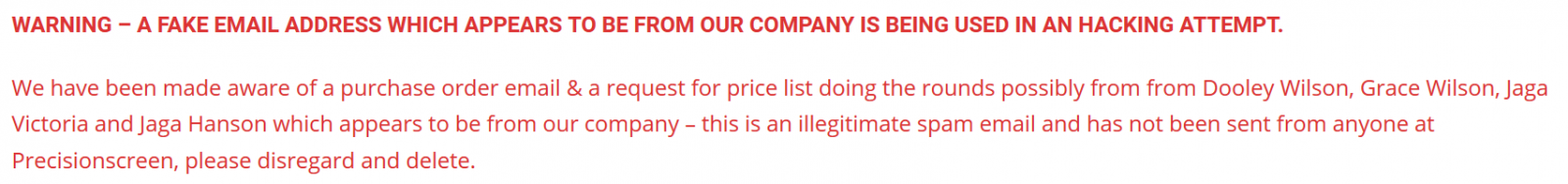
Text of both messages is identical, as you may see, but the sender address in the second case looks much more believable. It should be mentioned that at the time of writing, the domain already had a SPF record published, but headers from the received e-mail show that this has only been a recent change.
Both attachments are nearly identical as well. Each HTML document is composed of several blocks of URL-encoded data, which is decoded by JavaScript when the page is loaded by a browser.
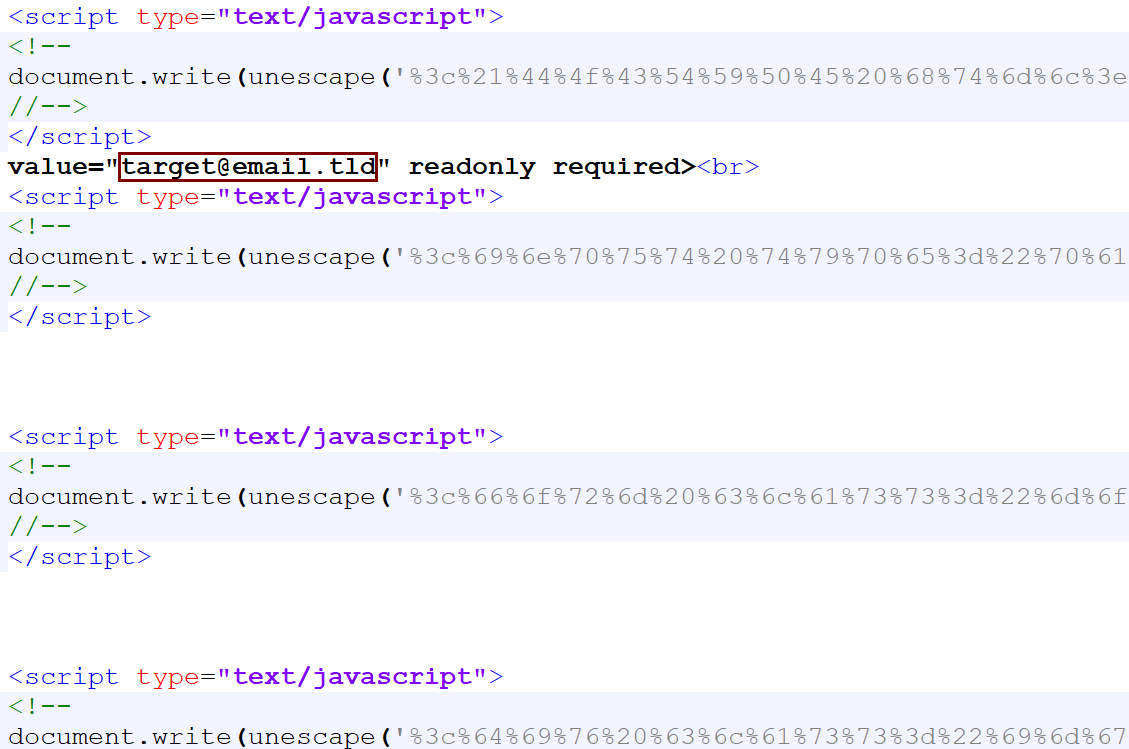
What is most interesting about the HTML page, besides the fact, that it holds the entire credential-stealing mechanism, is that it appears to be customized for each target. You may see this in the code above and in the page itself, shown bellow this paragraph.
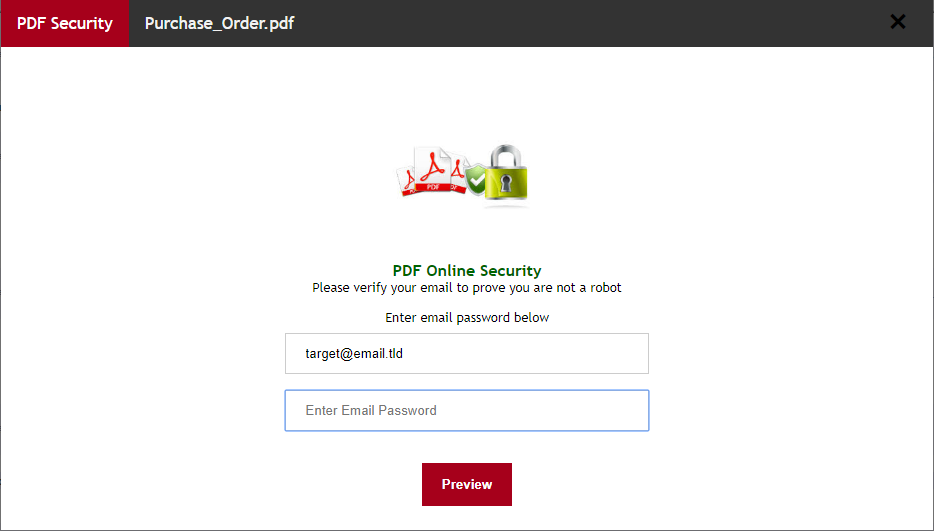
It is worth noting that the page itself is a bit more complex than one might expect. After a user enters a password, it doesn’t simply send the credentials to a remote server, but instead displays a warning about the password being incorrect and asks the user to re-type it. The second password is then sent to a remote server, along with the relevant e-mail address.
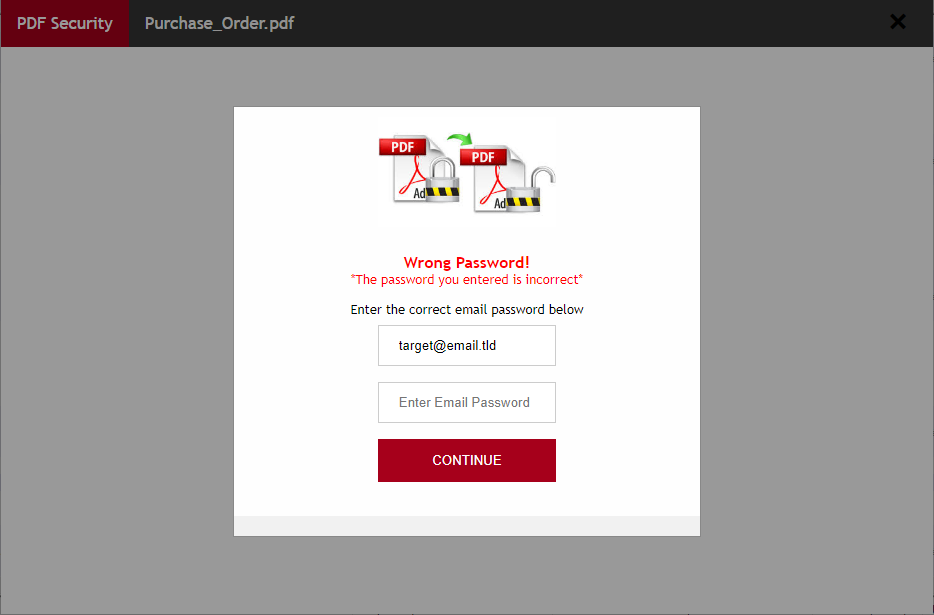
This was probably done in order to make the user take extra care while typing the password and minimize the amount of unusable credentials gathered by the attackers.
The HTML page attached to the e-mail from January sent data to https[:]//interaktiva[.]com[.]pl/wp-admin/css/colors/midnight/report-pdf.php and the HTML page from the more recent message send data to https[:]//easb[.]edu[.]sg/administrator/includes/order/report-pdf.php.
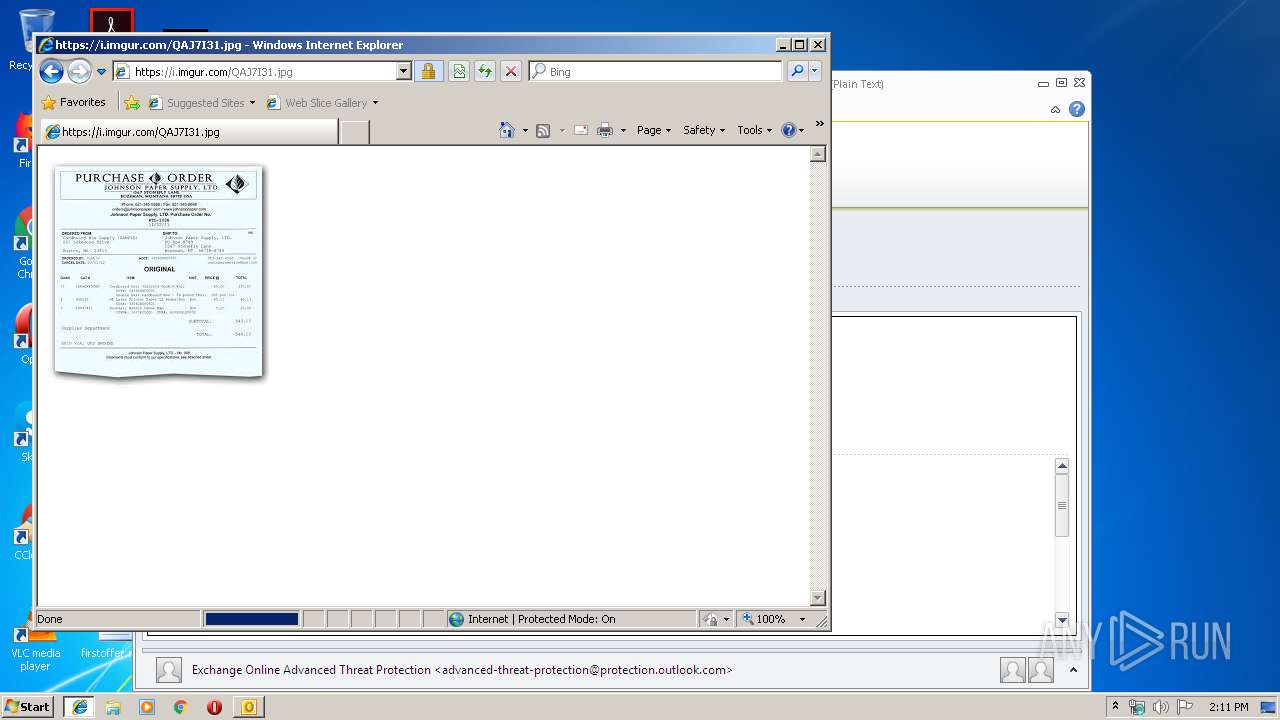
In both cases, the browser was then redirected to https[:]//i[.]imgur[.]com/QAJ7I31.jpg. The image at that URL is no longer available, but since it was captured during the Any.Run analysis in January, we can see it was a sample image of a purchase order, which the phishers probably “borrowed” from here.
As we may see, even though the two phishing messages were sent nearly 3 months apart, they are almost identical – besides the use of different SMTP servers to push the phishing, the only differences were in the personalization of the HTML documents and the use of different domains to which the pages sent the stolen data.
It seems that the phishers behind this campaign are firm believers in the old adage “If it ain’t broke, don’t fix it”.
[1] https://isc.sans.edu/forums/diary/100+JavaScript+Phishing+Page/25220/
[2] https://isc.sans.edu/forums/diary/Phishing+with+a+selfcontained+credentialsstealing+webpage/25580/
[3] https://app.any.run/tasks/e569984a-19d8-4b62-a072-195733db5070/
[4] https://stopscamfraud.com/viewtopic.php?t=792


Comments