Kids Like Cookies, Malware Too!
Recently, a vulnerability has been disclosed by Vectra that affects Microsoft Teams[1], the very popular communication tool used daily by millions of people (me too). Security researchers found that Teams stores session tokens in clear text on the file system. I won’t discuss the vulnerability here; read the blog post if you want to learn more. The critical element is that once the token has been stolen, an attacker can impersonate the user.
At the end of the blog post, Vectra lists interesting files to watch on the file system. For the Windows operating system, there are:
%AppData%\Microsoft\Teams\Cookies %AppData%\Microsoft\Teams\Local Storage\leveldb
After reading this, I was curious to see if this is already exploited in the wild. I created a new hunting rule on VT and crossed my fingers. After a few false positives, I got a hit! A DLL was uploaded and contained one of the two strings above.
The file was called “RwWork.dll” (SHA256:5092a18330debda930a73835c8e77c6a7fb3a5904bdc04aad61c6c4136f0d24b). It currently has a VT score of 56/71[2]. The file looks indeed for Teams cookies but even more:
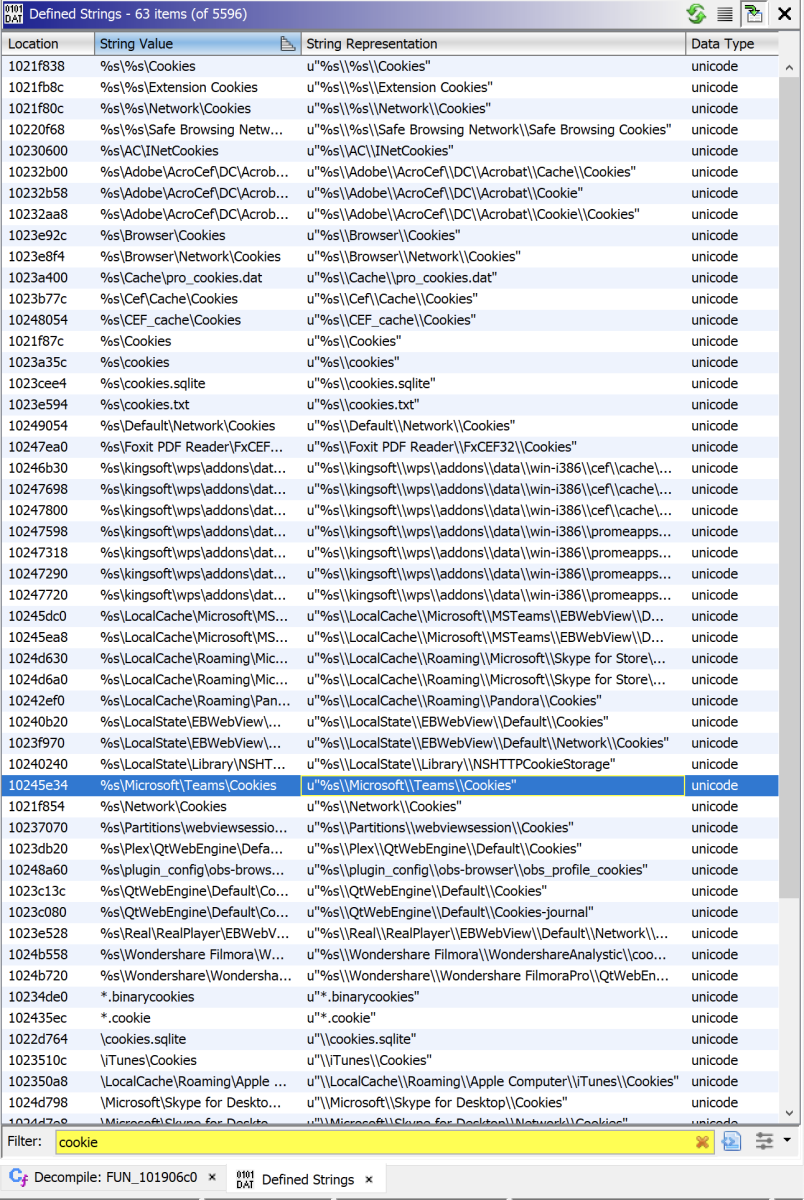
As you can see, many files related to cookies are searched. The malware is from the Floxif family...
[1] https://www.vectra.ai/blogpost/undermining-microsoft-teams-security-by-mining-tokens
[2] https://www.virustotal.com/gui/file/5092a18330debda930a73835c8e77c6a7fb3a5904bdc04aad61c6c4136f0d24b/details
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Sep 23rd 2022
3 years ago