First Hurricane Matthew related Phish
Dr. J. put out an appeal earlier today for readers to send in any Scams related to Hurricane Matthew. Literally within minutes Matthias sent us a Hurricane Matthew Phish that hit his inbox today. It purports to be from online payment company Stripe.
---
Welcome to Stripe!
Due To Hurricane Matthew, our servers have been affected and We be updated and all Users with 2-step verification should disable this function for the mean Time
Before we can fully provision your account, we need a few moments to verify some of the information you have provided.
We typically notify our customers of their provisioning status within an hour after severs are updated . However, in some cases we need to verify your information over the phone first. The call shouldn't take long, but due to many users on our system we can't be able to reach every one so we ask you update and confirm your details to be on a safe side
further action may be required on your part. Please login to Your Dash board hxxps://dashboard.stripe.com/Hurricane Matthew- verification/ to update details
Users with wrong information would be banned from Our service
Regards,
Account Review Team
----
Of course the email is not from Stripe. Checking the usual; the spelling and grammar are okay; the formatting and punctuation are horrible; it was sent from an account in the ruby.net domain; and the dashboard link points to hxxp://fund2pay.org/stripe/ST/.
If you click through to the landing page. Google is already catching this as a phishing site.
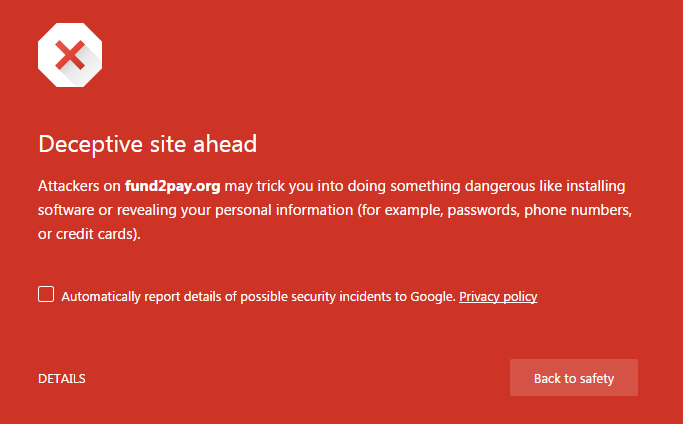
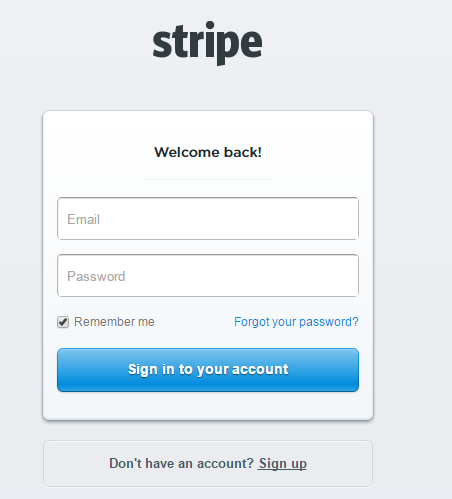
If you do click through, the page is an excellent rendition of the Stripe login page.
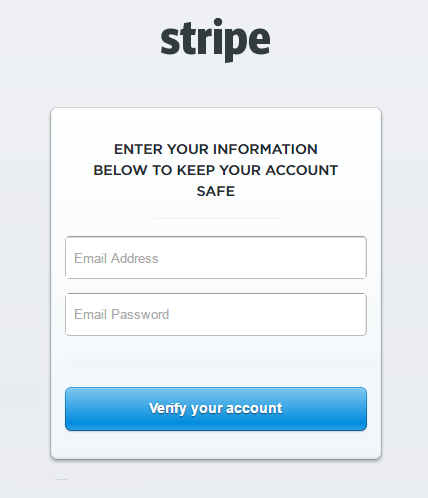
If you do enter your credentials it takes you to a very similar page, presumably so you can verify your credentials. If you are going to Phish someone you should make sure you get it right!
After you verified your credentials it passes you through to the real Stripe login page. Although Stripe notices the redirect.
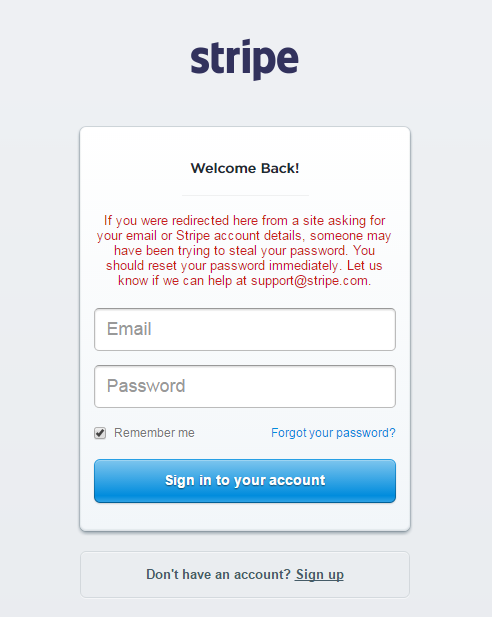
Probably most interesting is that it requests Stripe users to disable their 2-factor authentication. So assuming you do enter your credentials 3-times and disable your 2FA, the Phishers would have unimpeded access to the account. Tricky!
In my mind this falls into the realm of low probability of success, but as P.T. Barnum said "There's a sucker born every minute."
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments
Anonymous
Oct 8th 2016
9 years ago
Anonymous
Oct 8th 2016
9 years ago