Parasitic Sharepoint Exploits
Last week, newly exploited SharePoint vulnerabilities took a lot of our attention. It is fair to assume that last Monday (July 21st), all exposed vulnerable SharePoint installs were exploited. Of course, there is nothing to prevent multiple exploitation of the same instance, and a lot of that certainly happened. But why exploit it yourself if you can just take advantage of backdoors left behind by prior exploits? A number of these backdoors were widely publicised. The initial backdoor "spinstall0.aspx", was frequently observed and Microsoft listed various variations of this filename [1].
Since then, we have observed attempts to access these backdoors. The scans started a week ago, just as the exploits (and the name of the backdoors) became better known.
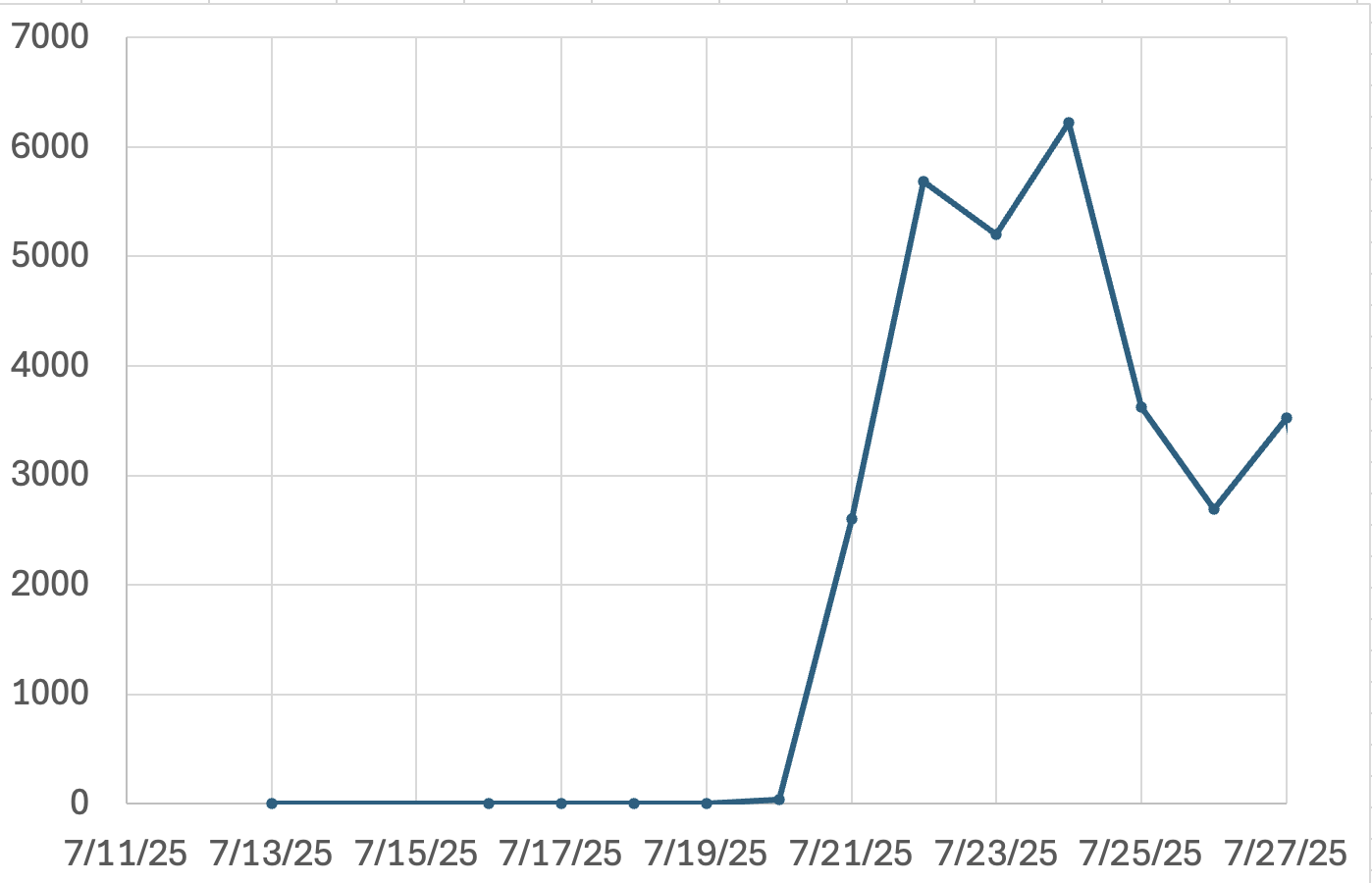
The graph displays the number of requests we see in our honeypots each day for URLs like "'/_layouts/.*\.aspx". This includes some exploit attempts, as they also match this pattern. But see a few "untargeted" exploit attempts at this point. Many of the requests originate from researchers counting the number of exploited systems.
Here is the complete list of possible URLs, including the date they were first detected by our honeypots:
| Firt Seen | Path |
|---|---|
| 2025-07-13 | /_layouts/15/teamslogon.aspx |
| 2025-07-16 | /_layouts/15/ToolPane.aspx |
| 2025-07-19 | /_layouts/15/spinstall0.aspx |
| 2025-07-20 | /_layouts/16/template/layouts/11.aspx |
| 2025-07-20 | /_layouts/16/template/layouts/asks.aspx |
| 2025-07-20 | /_layouts/16/template/layouts/owa/resources/iii.aspx |
| 2025-07-20 | /_layouts/16/template/layouts/z.aspx |
| 2025-07-23 | /_layouts/15/xxx.aspx |
| 2025-07-23 | /_layouts/16/3plx.aspx |
| 2025-07-23 | /_layouts/16/spinstall8.aspx |
| 2025-07-23 | /_layouts/16/spinstallx.aspx |
| 2025-07-23 | /_layouts/16/xxx.aspx |
| 2025-07-23 | /_layouts/65/xxx.aspx |
| 2025-07-24 | /_layouts/15/spinstallb.aspx |
| 2025-07-24 | /_layouts/15/sys1ayouts.aspx |
| 2025-07-24 | /_layouts/15/ToolPane.aspx/3c2b2a626c2a443387a56ad8c689b721.aspx |
| 2025-07-24 | /_layouts/15/toolpane.aspx/lkx?DisplayMode=Edit&lkx=/ToolPane.aspx |
| 2025-07-24 | /_layouts/15/ToolPane.aspx/Tool?DisplayMode=Edit&a=/ToolPane.aspx |
| 2025-07-24 | /_layouts/15/versions.aspx |
| 2025-07-24 | /_layouts/16/spinstallb.aspx |
| 2025-07-24 | /_layouts/16/spinstallp.aspx |
| 2025-07-24 | /_layouts/16/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx |
| 2025-07-24 | /_layouts/settings.aspx |
| 2025-07-24 | /_layouts/viewlsts.aspx |
| 2025-07-25 | /_layouts/15/ghostfile384.aspx |
| 2025-07-25 | /_layouts/15/ghostfile692.aspx |
| 2025-07-25 | /_layouts/15/httpmanago.aspx |
| 2025-07-25 | /_layouts/15/ToolPane.aspx/1ad07ef185eb4beb9a263ddf8d4a058a.aspx |
| 2025-07-25 | /_layouts/15/ToolPane.aspx/?DisplayMode=Edit&a=/ToolPane.aspx |
| 2025-07-25 | /_layouts/15/ToolPane.aspx?DisplayMode=Edit&lkx=/ToolPane.aspx |
| 2025-07-26 | /_layouts/15/start.aspx/_layouts/15/start.aspx |
| 2025-07-27 | /_layouts/15/Error404.1.aspx |
| 2025-07-27 | /_layouts/15/Error404.11.aspx |
| 2025-07-27 | /_layouts/15/httpmanago.aspx/_layouts/15/httpmanago.aspx |
| 2025-07-27 | /_layouts/15/ToolPane.aspx/krgpjijzesqohx?DisplayMode=Edit&bgzrickdnpmoilrh=/ToolPane.aspx |
| 2025-07-27 | /_layouts/15/ToolPane.aspx/mdqxusjqiohhgxr?DisplayMode=Edit&qcahctzh=/ToolPane.aspx |
| 2025-07-27 | /_layouts/15/ToolPane.aspx/uzvazxjefwkvk?DisplayMode=Edit&nfhzxzghtrookegq=/ToolPane.aspx |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments