Fileless Powershell Dropper
I found an interesting Powershell script that drops a malware on the victim's computer. The dropped malware is not new (It's kinda old, though) but the dropper has a very low Virustotal score. The script was detected by one of my hunting rules on VT. It is called "autopowershell.ps1" and has only a score of 3/61 (SHA256:3750576978bfd204c5ac42ee70fb5c21841899878bacc37151370d23e750f8c4)[1]. By "fileless", it means that the malware tries to reduce at the minimum interactions with the file system. But, to achieve persistence, it must write something on the disk. Most of the time, it's done through registry keys. That's what happens with this sample:
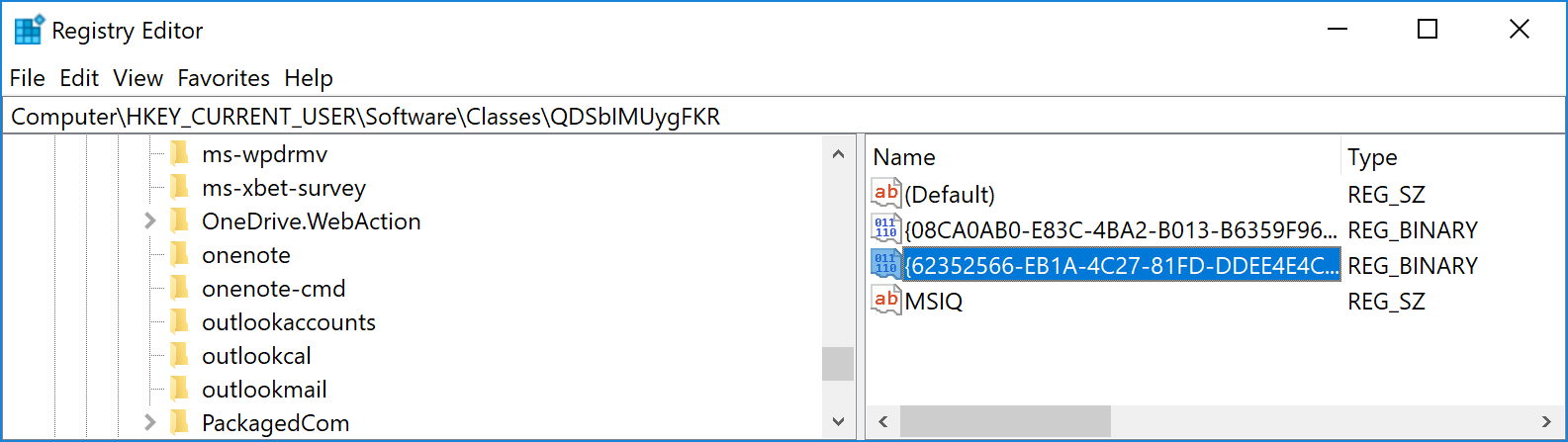
Suspicious keys are stored in "HKCU\Software\Classes\QDSbIMUygFKR". Note that key names are not randomized, which makes them very interesting IOCs.
In "MSIQ", we find another Powershell script that will be used for persistence.
In "{08CA0AB0-E83C-4BA2-B013-B6359F962B16}", we find the encrypted payload
In "{62352566-EB1A-4C27-81FD-DDEE4E4CFF50}", we find the key to decrypt the payload
The second Powershell script will extract another Base64-encoded script that provides all the classic functions to perform ReflectivePEInjection from PowerSploit[2]. The injected payload is read from the registry, decrypted and injected. It's a DLL file with a VT score of 30/62 (SHA256:9b3e2e56863fc5a85c5c9f16a82a55c5bc88f5ed049f2e8b21e4e8895e25ec21)[3]. Nothing new, it was first uploaded in 2020!
[1] https://www.virustotal.com/gui/file/3750576978bfd204c5ac42ee70fb5c21841899878bacc37151370d23e750f8c4/detection
[2] https://powersploit.readthedocs.io/en/latest/CodeExecution/Invoke-ReflectivePEInjection/
[3] https://www.virustotal.com/gui/file/9b3e2e56863fc5a85c5c9f16a82a55c5bc88f5ed049f2e8b21e4e8895e25ec21/detection
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
In "{08CA0AB0-E83C-4BA2-B013-B6359F962B16}", we find the encrypted payload
In "{08CA0AB0-E83C-4BA2-B013-B6359F962B16}", we find the key to decrypt the payload
Anonymous
Oct 18th 2022
3 years ago
I just fixed it!
Anonymous
Oct 18th 2022
3 years ago
The PowerShell loader is -- http://blog.trendmicro.com/trendlabs-security-intelligence/look-js_powmet-completely-fileless-malware/ -- https://malpedia.caad.fkie.fraunhofer.de/details/js.powmet
9b3e2e56863fc5a85c5c9f16a82a55c5bc88f5ed049f2e8b21e4e8895e25ec21 -- (e.dll) -- also appears to be similar and include code found in the -- bff21cbf95da5f3149c67f2c0f2576a6de44fa9d0cb093259c9a5db919599940 -- https://malpedia.caad.fkie.fraunhofer.de/details/win.andromeda -- sample from that Trend blog post's PowMet -- e27f417b96a33d8449f6cf00b8306160e2f1b845ca2c9666081166620651a3ae
Anonymous
Oct 18th 2022
3 years ago
Anonymous
Oct 18th 2022
3 years ago
Anonymous
Oct 20th 2022
3 years ago