Domaincop malpsam
Introduction
Last month on 2016-11-22, I saw 10 items of malicious spam (malspam) sent to my spam folder. The messages all had links to malware. Unfortunately, by the time I examined those emails, the links were no longer active. I sent a tweet about it and moved on to other things [1].
Flash forward to this week. On Tuesday 2016-12-13, @malwrhunterteam noticed the same type of malspam [2]. I checked my spam folder and found another four similar messages. This time, the links were still active, and I generated a full chain of infection traffic. That wave of malspam distributed Cerber ransomware.
The very next day on Wednesday 2016-12-14, I noticed another two messages in my spam folder with the same characteristics using a different domain. This wave of malspam also distributed Cerber ransomware.
Today's diary looks at indicators from these three waves of malspam. Perhaps we can get a better idea of the actor behind this activity.
Chain of events
The four emails from 2016-12-13 have links that downloaded a .js file. In my lab environment, double-clicking the .js file downloaded and installed Cerber ransomware. The two emails from 2016-12-14 have a link for a Microsoft Word document. The Word document has a malicious macro. In my lab environment, enabling the macro also downloaded and installed Cerber ransomware.
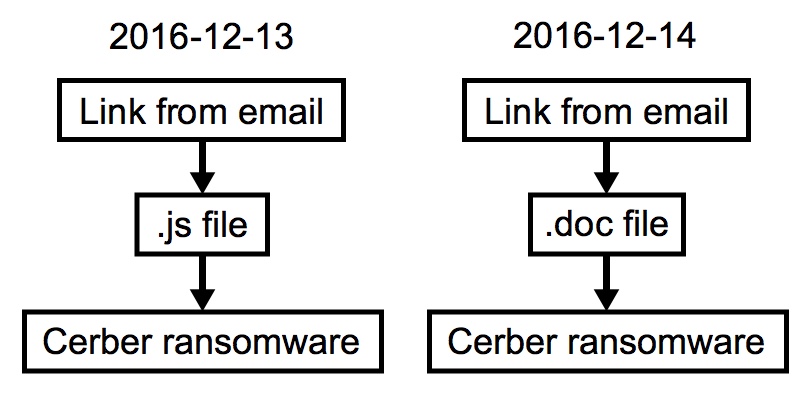
Shown above: Chain of events for both days.
The emails
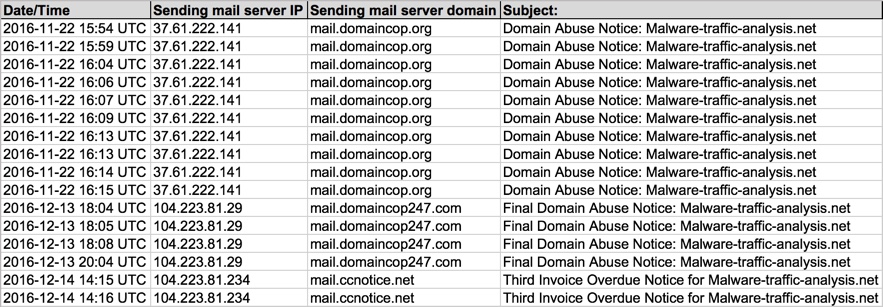
Shown above: Data on the malspam (part 1 of 2).
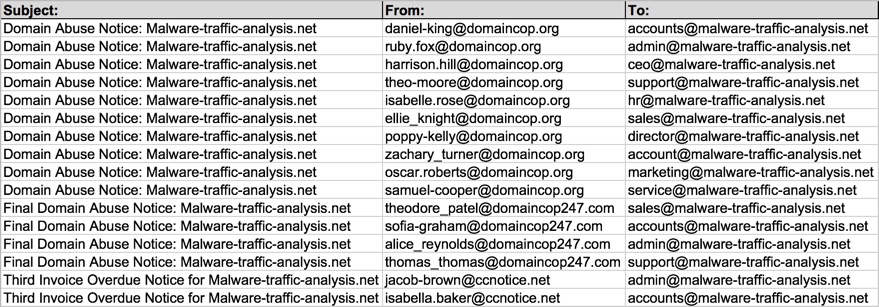
Shown above: Data on the malspam (part 2 of 2).
Below are the recipient email addresses in the malspam I received during all three waves:
- account@[your domain name]
- accounts@[your domain name]
- admin@[your domain name]
- ceo@[your domain name]
- director@[your domain name]
- hr@[your domain name]
- marketing@[your domain name]
- sales@[your domain name]
- service@[your domain name]
- support@[your domain name]
Below are the subject lines I saw for each of the three waves:
- 2016-11-22 - Subject: Domain Abuse Notice: [your domain name]
- 2016-12-13 - Subject: Final Domain Abuse Notice: [your domain name]
- 2016-12-14 - Subject: Third Invoice Overdue Notice for [your domain name]
For each wave I saw, the emails all came from the same mail server. These servers also hosted the malicious links within the malspam. The servers were:
- 2016-11-22 - 37.61.222.141 - mail.domaincop.org
- 2016-12-13 - 104.223.81.29 - mail.domaincop247.com
- 2016-12-14 - 104.223.81.234 - mail.ccnotice.net
Based on the domain names and IP addresses, the criminals likely abused commercially available services. Below is the registration info and date registered for each domain.
- First wave domain Name: domaincop.org
- Sponsoring registrar: Namesilo, LLC
- Date registered (creation date): 2016-11-22
- Date I received the malspam: 2016-11-22
- Second wave domain Name: domaincop247.com
- Registrar: eNom, Inc (Reseller: Namecheap.Com)
- Date registered (creation date): 2016-11-30
- Date I received the malspam: 2016-12-13
- Third wave domain name: ccnotice.net
- Registrar: eNom, Inc (Reseller: Namecheap.Com)
- Date registered (creation date): 2016-12-12
- Date I received the malspam: 2016-12-14
All domains used a privacy guard service for the registration info, and all domains used name servers from cloudflare.com. Below is information on the IP addresses hosting the malspam domains:
- First wave: 37.61.222.141 - Germany: velia.net Internetdienste GmbH
- Second wave: 104.223.81.29 - US: Quadranet, Inc
- Third wave: 104.223.81.234 - US: Quadranet, Inc
Links from the emails were unique for each email during the first two waves. The two messages from third wave I saw on 2016-12-14 had the same URL that led directly to a Word document.
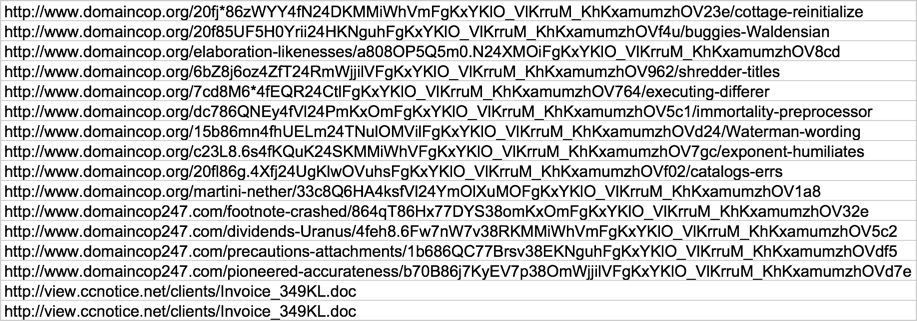
Shown above: Links from the emails.
For details, see the spreadsheet available here.
Traffic
In both waves I have traffic for, the same URL for the Cerber ransomware executable was generated, whether it was the .js file from 2016-12-13 or the .doc macro from 2016-12-14. Below are images from the pcaps of the traffic in Wireshark that help illustrate the chain of events.
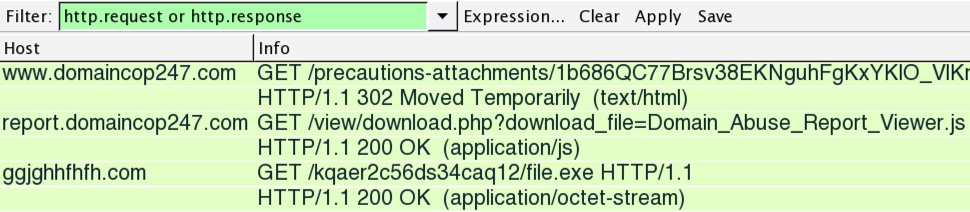
Shown above: .js file from 2016-12-13 getting the Cerber executable.
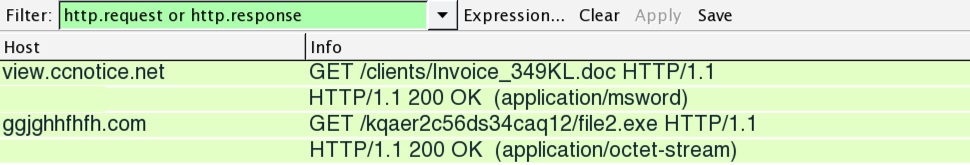
Shown above: .doc macro from 2016-12-14 getting the Cerber executable.
The ransomware was different each day, each with a different file hash, and each with different IP addresses and domains during the post-infection traffic. Both Cerber samples had .8637 for the file extension in the files they encrypted.
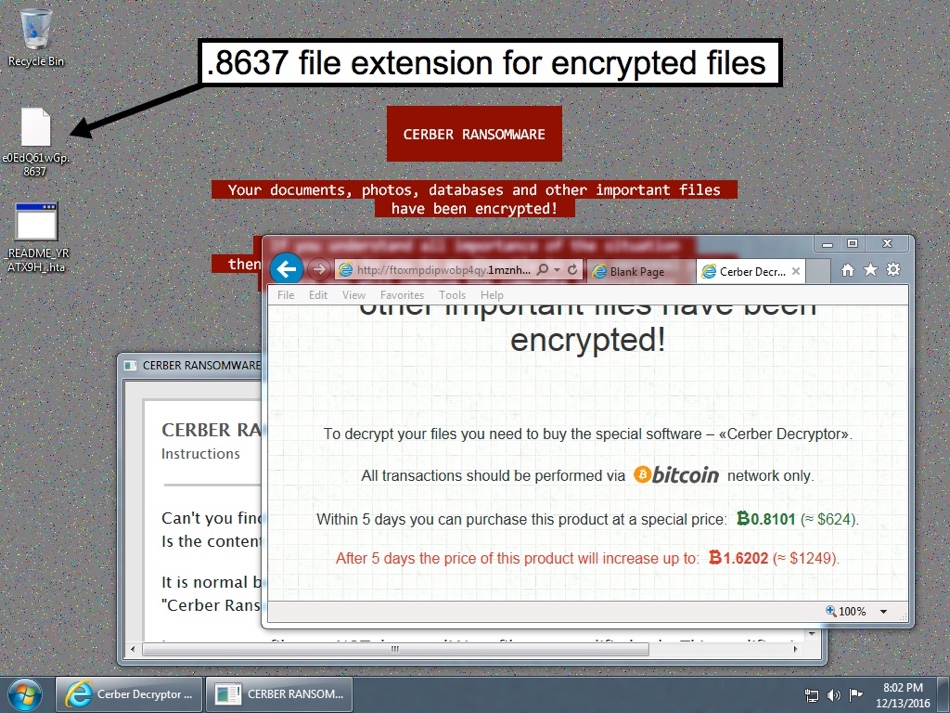
Shown above: Windows desktop from the 2016-12-13 infection.
Below are indicators of compromise (IOCs) for traffic generated from the 2016-12-13 wave of malspam:
- 104.28.11.141 port 80 - www.domaincop247.com - various GET requests redirect to next URL
- 104.28.10.141 port 80 - report.domaincop247.com - GET /view/download.php?download_file=Domain_Abuse_Report_Viewer.js
- 185.153.198.117 port 80 - ggjghhfhfh.com - GET /kqaer2c56ds34caq12/file.exe
- 15.49.2.0 to 15.49.2.31 (15.49.2.0/27) UDP port 6892 - Cerber post-infection UDP traffic
- 122.1.13.0 to 122.1.1331 (122.1.13.0/27) UDP port 6892 - Cerber post-infection UDP traffic
- 194.165.16.0 to 194.165.17.255 (194.165.16.0/23) UDP port 6892 - Cerber post-infection UDP traffic
- 37.10.71.202 port 80 - ftoxmpdipwobp4qy.1mznhc.top - Cerber post-infection HTTP traffic
Below are IOCs for traffic generated from the 2016-12-14 wave of malspam:
- 185.153.198.117 port 80 - view.ccnotice.net - GET /clients/Invoice_349KL.doc
- 185.153.198.117 port 80 - ggjghhfhfh.com - GET /kqaer2c56ds34caq12/file2.exe
- 1.11.32.0 to 1.11.32.31 (1.11.32.0/27) UDP port 6892 - Cerber post-infection UDP traffic
- 55.15.15.0 to 55.15.15.31 (55.15.15.0/27) UDP port 6892 - Cerber post-infection UDP traffic
- 194.165.16.0 to 194.165.17.255 (194.165.16.0/23) UDP port 6892 - Cerber post-infection UDP traffic
- 185.45.192.155 port 80 - ffoqr3ug7m726zou.19dmua.top - Cerber post-infection HTTP traffic
Below is information for the associated .js file, .doc file, and Cerber ransomware executables:
File name: Domain_Abuse_Report_Viewer.js
- File size: 9,032 bytes
- SHA256 hash: 12c72ccf0b64bc1b288c80e3ba8eb18bc88967264ca3ad392992354be9b51eb9
File description: Cerber downloaded by .js file from ggjghhfhfh.com on 2016-12-13
- File location: C:\Users\[username]\appdata\Local\Temp\ixjobi7na.exe
- File size: 255,018 bytes
- SHA256 hash: 5e396520da517174e5556e5b2c3b6e6ff25214c083e4458248f1be2e89967c65
File name: Invoice_349KL.doc
- File size: 206,120 bytes
- SHA256 hash: 12c72ccf0b64bc1b288c80e3ba8eb18bc88967264ca3ad392992354be9b51eb9
File description: Cerber downloaded by Word macro from ggjghhfhfh.com on 2016-12-14
- File location: C:\Users\[username]\Desktop\error.bat (or whatever directory the Word doc was opened in)
- File size: 262,111 bytes
- SHA256 hash: 5e396520da517174e5556e5b2c3b6e6ff25214c083e4458248f1be2e89967c65
Final words
A copy of the infection traffic, associated emails, malware, and artifacts can be found here.
Other people have noticed these malspam runs, and they've gotten some public attention through various blogs [3, 4, 5]. They never last long. I assume that's because the associated IOCs are reported fairly quickly, and the emails I've seen always get flagged as spam.
Fortunately, best security practices will help prevent infections like the ones in today's diary. A good email filtering system, properly administered Windows hosts, and an educated workforce mean users are much less likely to be infected.
Nonetheless, I assume this activity is somehow profitable for the people behind it. The criminals must be having some sort of success with these Cerber ransomware malspam runs. Why else would it keep happening?
---
Brad Duncan
brad [at] malware-traffic-analysis.net
[1] https://twitter.com/malware_traffic/status/801330398370418688
[2] https://twitter.com/malwrhunterteam/status/808752888063332352
[3] https://www.namepros.com/threads/these-domaincop-idiots-are-at-it-again.989576/
[4] https://www.blackmoreops.com/2016/11/23/domaincop-org-domain-abuse-notice-spam/
[5] http://onlinedomain.com/2016/11/22/domain-name-news/spamscam-email-domaincop-net-targeting-domain-name-website-owners/


Comments