Do you have some DNS requests/replies you could share?
Looking at DNS traffic it looks like it has been a busy month, but traffic seems to have dropped off.
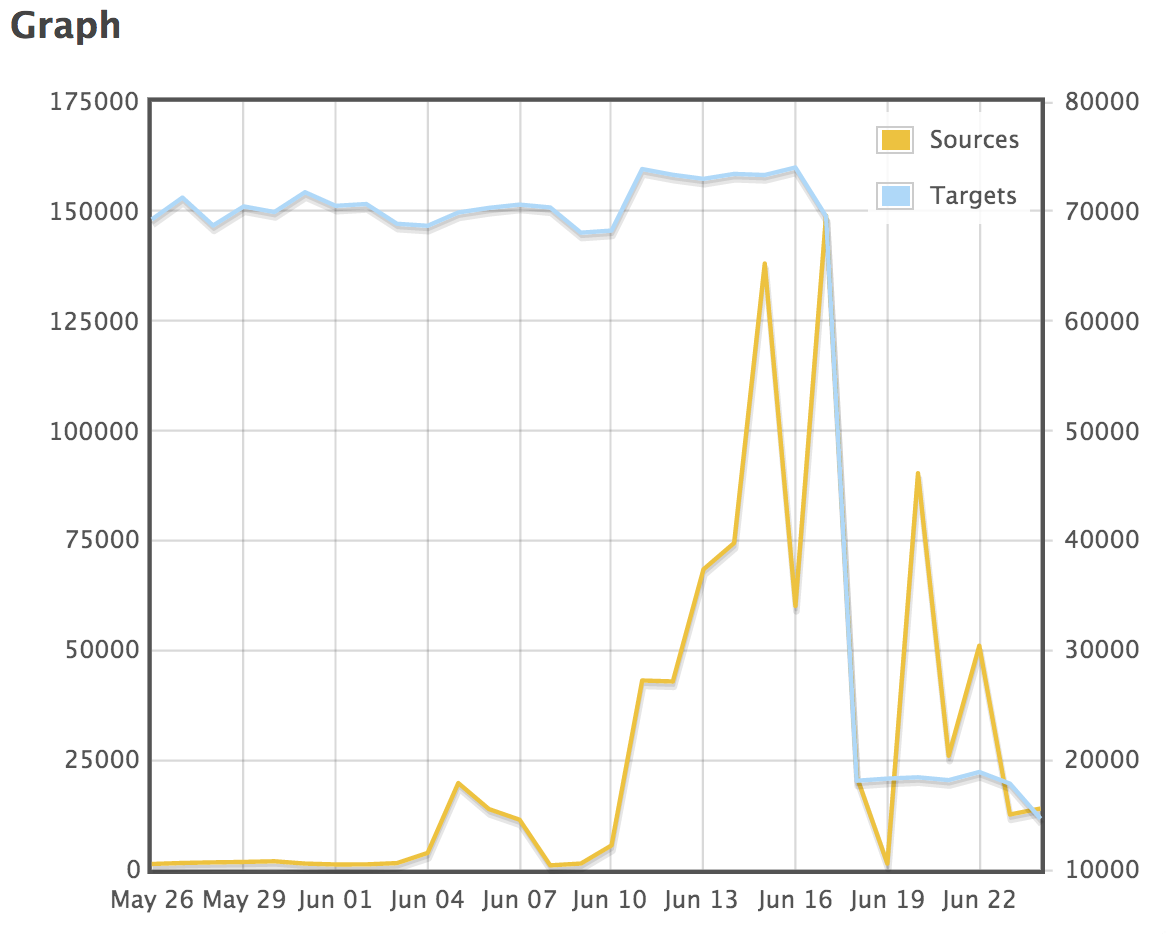
port 53 as a target has dropped off and during June there was an increase in traffic with a source port of 53. Something that we've seen on various IDS. We either see one of two types of packets. A request for any for a particular domain with the packet size set to 65535 and a spoofed source IP (i.e. the target). So that accounts for the traffic to port 53.
The second types of requests we see is from port 53. Typically with a random source ports and typically to a number of servers in the target network. The only thing that changes is often the queryid. So these are likely attempts to poison the cache.
The third type we see are DNS requests to check for open resolvers and a final type of query we see a lot of are DNS queries with HTTP elements in the traffic.
There are a few things I'm interested in. What caused the drop off for port 53 as the target. What DNS queries are you seeing targetting your environment? and if you can share, I'd be interested in the actual request itself.
Regards
Mark H


Comments
Anonymous
Jun 25th 2014
1 decade ago
We don't allow recursion from outside and I blackhole excessive requests with iptables so it's a biased sample. No packets handy but I might grab some and see if source port and packet size are consistent with what you see. A random sample of the source IPs (whether spoofed or not) seems to point to usual suspects eastern Europe and Asia.
Anonymous
Jun 26th 2014
1 decade ago