Commando VM: The Complete Mandiant Offensive VM
The good folks at Mandiant have created the Commando VM, a fully customized, Windows-based security distribution for penetration testing and red teaming.
From the project’s About Commando VM content:
“Penetration testers commonly use their own variants of Windows machines when assessing Active Directory environments. Commando VM was designed specifically to be the go-to platform for performing these internal penetration tests. The benefits of using a Windows machine include native support for Windows and Active Directory, using your VM as a staging area for C2 frameworks, browsing shares more easily (and interactively), and using tools such as PowerView and BloodHound without having to worry about placing output files on client assets.”
Many of the expected tools are available on this platform, over 140, including:
- Nmap
- Wireshark
- Covenant
- Python
- Go
- Remote Server Administration Tools
- Sysinternals
- Mimikatz
- Burp-Suite
- x64dbg
- Hashcat
The team claims support for blue teams as well. In their own words, “Commando VM provides blue teams with the tools necessary to audit their networks and improve their detection capabilities. With a library of offensive tools, it makes it easy for blue teams to keep up with offensive tooling and attack trends.” While a bit more in spirit than reality with the Commando VM, any aspirations to support the purple team approach are welcome and admirable.
Installation is extremely straightforward, the platform is built out via Boxstarter, Chocolatey, and MyGet packages, and takes a bit of time to complete, more than an hour in multiple test scenarios for me. Full, thorough installation guidelines are here. The fast and furious version is simply this:
- Create and configure a new Windows Virtual Machine, update it completely, then take a snapshot
- Download and copy install.ps1 on the newly configured and updated VM
- Open an elevated PowerShell console
- Enable script execution:
Set-ExecutionPolicy Unrestricted - Execute the installer script:
.\install.ps1
Be patient, let it finish, and keep an eye on the console from time to time as it progresses.
As always, please read the project content in full. You can also download the full Commando VM repository from GitHub as a zip package or clone it accordingly.
Given its Windows-centric focus, Commando VM includes a few tools that have advanced Windows exploitation practices, with particular attention to .NET and WMI.
In the reverse engineering category, there’s ILSpy, the open-source .NET assembly browser and decompiler.
For command and control, there’s Covenant, “a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers.”
From FortyNorth Security, also see WMImplant, “a PowerShell based tool that is designed to act like a RAT. Its interface is that of a shell where any command that is supported is translated into a WMI-equivalent for use on a network/remote machine.” FortyNorth Security and Chris Truncer also offer up WMIOps, “a powershell script which uses WMI for various purposes across a network.”
WMIOps is used to “perform a variety of actions on hosts, local or remote, within a Windows environment and is designed primarily for use on penetration tests or red team engagements.” As such, it includes:
- Process functions:
Get-RunningProcessesWMI(accounts with active processess) - User operations:
Find-ActiveUsersWMI(whois on target) - Host enumeration:
Get-ActiveNICSWMI(dump target NICs) - System manipulation operations:
r Invoke-ServiceManipulation(service buggery) - File operations:
Invoke-FileTransferOverWMI(exfil)
In the big bucket o’ exploitation tools, a few favorites lurk.
EvilClippy, as part of its role as a cross-platform assistant for creating malicious Microsoft Office documents, includes the likes of VBA stomping (P-code abuse). EvilClippy puts fake VBA code from a text file (VBA) in all modules, while leaving P-code intact, abusing an undocumented feature of module streams. It’s a straightforward as EvilClippy.exe -s fakecode.vba macrofile.doc
A wise and recent red team re-orientation towards C# opportunities is also well represented. FuzzySec’s Sharp-Suite, GhostPack, and SharpSploit are all present and accounted for. Commando VM owes a great debt to the hard work of the SpecterOps team. Ryan Cobb produced Covenant as well as SharpSploit.
Ryan states that there is a “trend developing on the offensive side of the security community in porting existing PowerShell toolsets to C#. With the added security features in PowerShell (ie. ScriptBlock Logging, AMSI, etc.), it makes sense that red teamers are investing in other options, and C# is the logical next step from PowerShell.” Note that SharpSploit is designed as a library, so there is only a SharpSploit.dll.
Ryan’s teammate, Will Schroeder aka harmj0y, created GhostPack, generically referred to as “collection of security related toolsets.” ;-)
Therein, you will find the likes of Seatbelt, a “C# project that performs a number of security oriented host-survey safety checks relevant from both offensive and defensive security perspectives.”
Given the spirit of purple team embraced by the Commando VM team, Seatbelt seems like an ideal way to bring us to conclusion for this quick Commando VM overview. In order to make use of Seatbelt you need to compile it yourself, the project team is not releasing binaries.
To do so, simply download Visual Studio Community 2019 on your Commando VM, set it up for Windows development (.NET, desktop, and UWP), and then open Seatbelt.sln, found in C:\tools\GhostPack\Seatbelt. Be sure to run Visual Studio as administrator for this step. In Solution Explorer, right-click Seatbelt and select Build. You’ll then find Seatbelt.exe in C:\tools\GhostPack\Seatbelt\Seatbelt\bin\Debug.
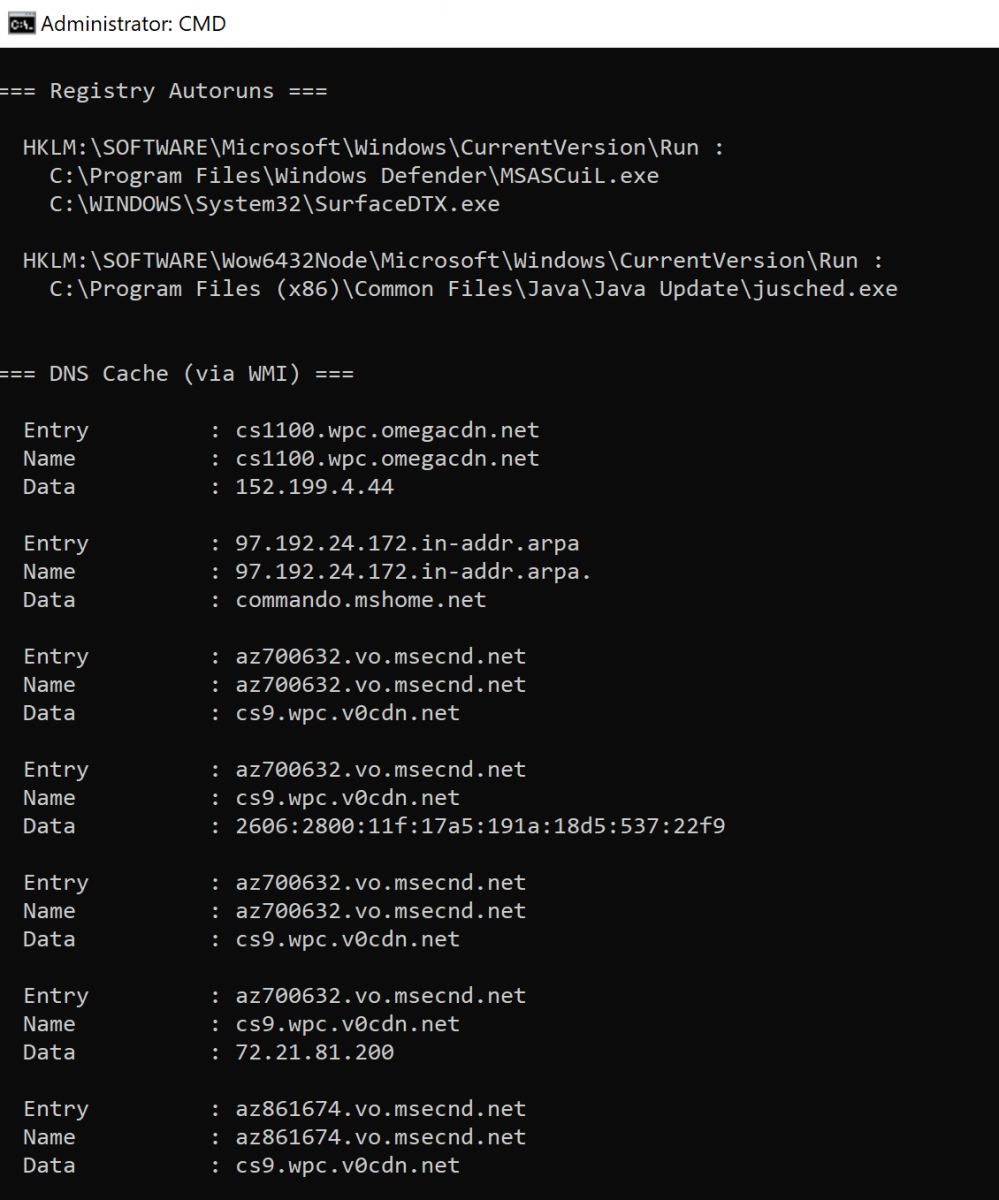
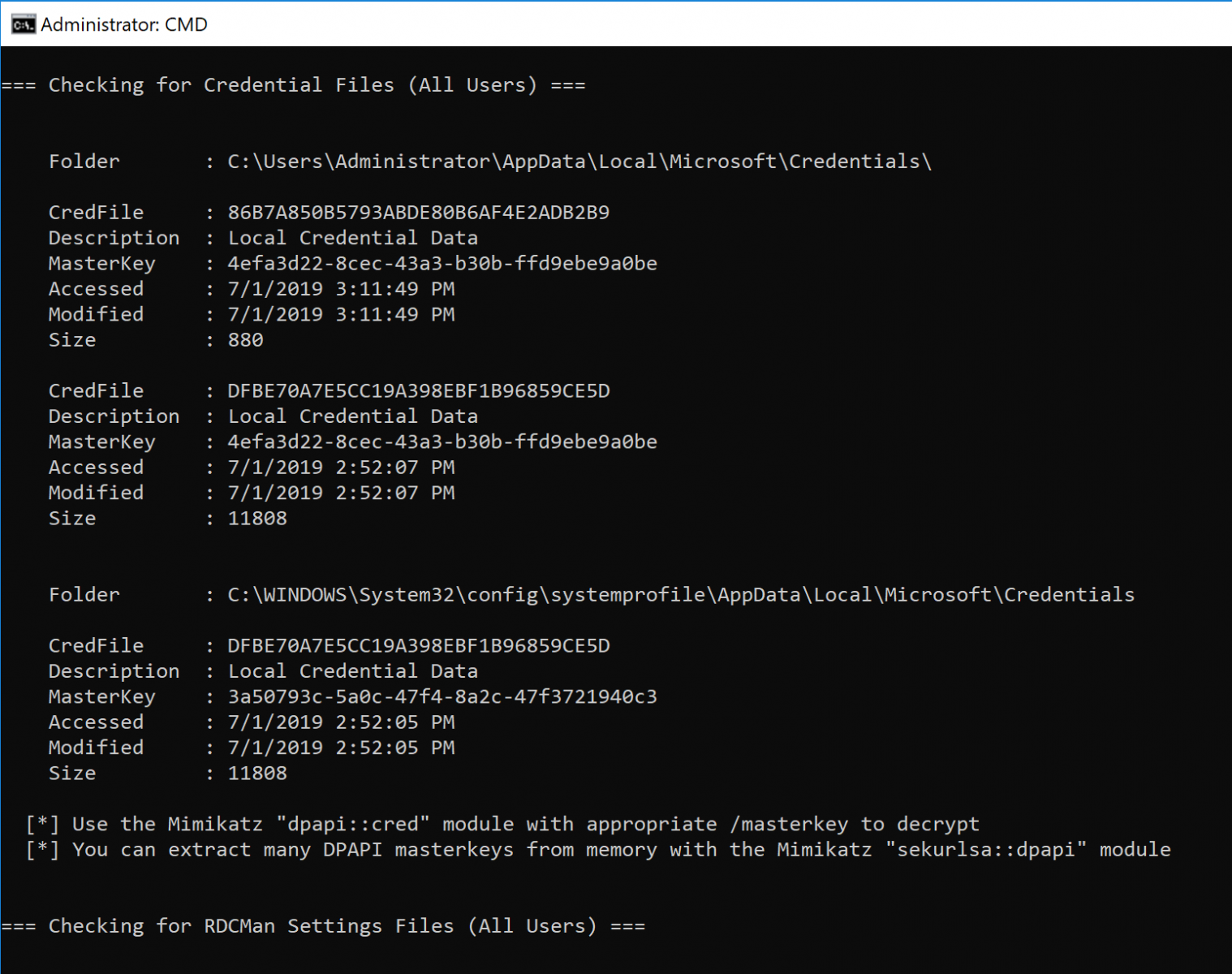
Pop a command shell, run Seatbelt.exe all and revel in the results, including the likes of system data (incoming RDP sessions, firewall rules, autoruns, etc), user data (saved RDP connections, 7 days of IE bookmarks and history, saved credential in Windows Vault, etc), and other collection options such as listing Kerberos tickets, Kerberos TGTData (ALL TEH TGTZ!), 4624 events from the security event log, and installed patches via WMI.
You can quickly see how Seatbelt can serve both red and blue causes.
Great stuff from the Mandiant team for Commando VM, a complete Mandiant offensive VM indeed. As alway, be cautious in your use, lots of chaos to be created with this platform, ensure you have permission and purview.
Cheers…until next time.



Comments