Are You Still Storing Passwords In Plain Text Files?
"Infostealer" malware have been in the wild for a long time now. Once the computer's victim is infected, the goal is to steal "juicy" information like passwords, cookies, screenshots, keystrokes, and more. Yesterday, I spotted an interesting sample. It's delivered through an FTP connection. The file (SHA256:2bf9a44bd546e0fd1448521669136220dc49146b0f3a5cd7863698ac79b5e778) is unknown on VirusTotal.
The malware behavior is pretty simple: It scans the complete drive for interesting files. Here is an example: "*pass*.txt":
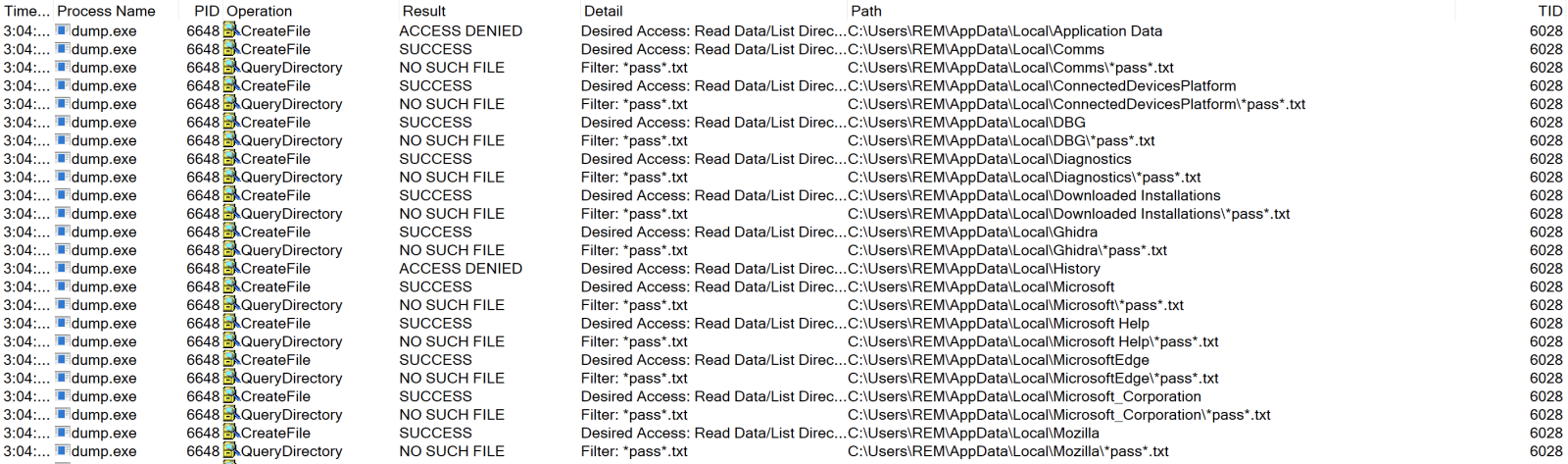
I also discovered that it searches for other files:
- *seed*.txt
- *ledger*.txt
- *trezor*.txt
- *metamask*.txt
- *bitcoin*.txt
- *words*
- *wallet*.txt
- *.kbdx
Simple but efficient. C2 communications are performed with slimtvsocico[.]fun.
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
My next class:
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |
×
![modal content]()
Diary Archives


Comments
C:\Users\USER\AppData\Roaming\Notepad++\backup
%AppData%\Notepad++\backup
On an admin machine, flip a coin on whether or not "unsaved temporary .txt files" are actually cached here.
Dustin
Sep 29th 2023
2 years ago
Cobus
Sep 30th 2023
2 years ago