An Analysis of Jester's QR Code Attack. (Guest Diary)
[This is a guest diary contributed by STI Student TJ O'Connor ] [Many claim this to a be a hoax]
This week saw an interesting turn in the US government's battle against the Hacker Group Anonymous. Official court documents and details emerged that finally showed that #sabu was turned by the US government as an informant to arrest and dismantle members from the LulzSec splinter cell. (Bray, 2012) In the last two days, another dramatic turn of events highlighted the demise of the once though invincible hacker group; a group the Director of the NSA said could be capable of hacking the power grid within a year or two. (Liebowitz, 2012)
A lone-wolf patriot hacker, known as Th3J35t3r, claims to have successfully targeted, exploited, and raided personal information from members of Anonymous, LulzSec, and Anti-Sec alongside Islamic Extremists and Al Qaeda, and Rhode Island State Representative Dan Gordon. If you are living in a cave and haven't heard about the Jester, read the SANS whitepaper. (OConnor, 2011) So how did the attack occur? And how can you protect yourself? Lets quickly answer these questions.
The Jester laid the groundwork for his attack over two weeks ago when he changed the ICON for his Twitter account @th3j35t3r.
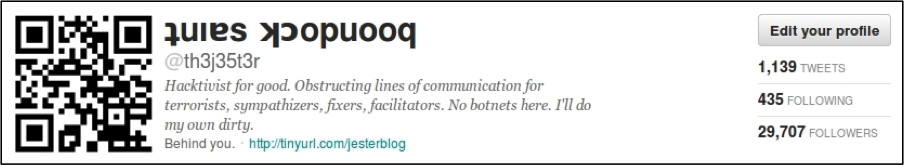
Here's where the Jester really relied upon his adversaries' technical prowess and curiosity as a weakness. Changing the photo to a QR-code, The Jester encoded a url address into the photo as seen in the photo. The victims used their mobile phones to scan the QR code and then visit the tinyurl address out of sheer curiosity. Since most of us (including the author) use our mobile phones to scan QR-codes, this allowed The Jester to scope his attack to browsers for the IOS and Android Operating Systems,. Both IOS and Droid rely heavily upon the WebKit framework for their web browser.
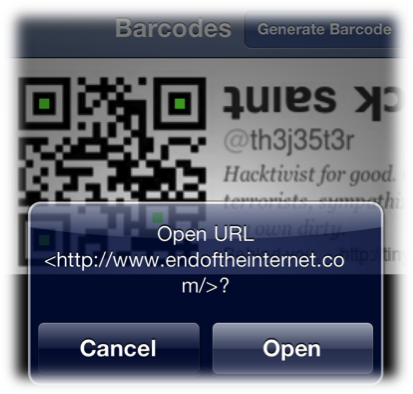
A Webkit exploit isn't necessarily novel. Previously exploits have succeeded in targeting Webkit. In 2010, Itzhak (Zuk) Avraham wrote a use-after free exploit for Webkit for the Droid 2.1 framework. (Abraham, 2010) Dr. Charlie Miller followed in March 2011 with a use-after-free Webkit exploit the IOS 4.2.1 operating system. (Naraine, 2011)
For a great example of how use-after-free exploits work, check out the Grey Corner Blog. Use-after-frees have been seen in usage for a while, especially during Advance Persistent Threat Attacks. Notably, the Operation Aurora attack that targeted Google succeeded via an Internet Explorer use-after-free vulnerability. By allocating memory for a specific object, then freeing the memory for the object, followed by accessing the pointer to the object's pointer can trigger arbitrary code execution. This can easily be combined with a technique known as heap spraying, filling the heap with executable code in multiple locations. When combined with a heap-spraying, a use-after free can jump to the heap to find its payload (shell code) and executes it.
In the Jester's attack this code executed a netcat command, passing the Twitter credentials to the Jester. At this point, the patriot hacker checked the credentials against a list of known targets before proceeding in his attack. Specifically targeted in the attack were @alemarahweb,@HSMPress @AnonymousIRC, @wikileaks, @anonyops, @barretbrownlol, @DiscordiAnon, @RepDanGordon.
Even under the current IOS 5.1, the com.atebits.Tweetie2 database contains com.atebits.Tweet2.plist which holds Twitter username, recent searches, device UDIDs, among other information that makes identifying specific users easy if they have the default Twitter application installed.
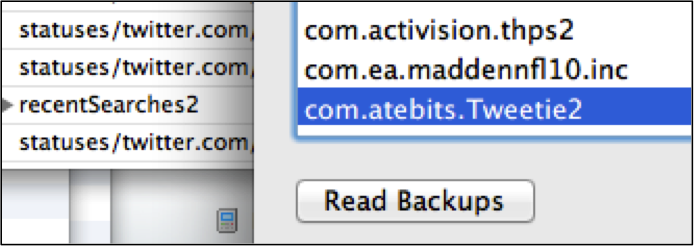
Next, the Jester raised his permissions on each exploited device. Under the IOS operating system, this proves trivial since the IOS has a default username/password combination of root/alpine. (Heider, 2012) Under Android, there are a variety of privilege escalation attacks. (Davi, 2010) With elevated privileges, the Jester then targeted specific databases that contained the SMS, Voicemail, Call Logs, and Email on the phone. Since, the default applications store all this data in default databases on the phone ; extracting this proves as easy as writing a few sqlite3 queries.
th3j35t3r$ sqlite3 sms.db SQLite version 3.7.9 2011-11-01 00:52:41 Enter ".help" for instructions Enter SQL statements terminated with a ";" sqlite> select address, text from message; +15555551234| Where can I download LOIC? +15555551234| Whats the new IRC Hivemind Server? +15555551234| Where can I find a good attorney?
At this point, the Jester has threatened to upload the contents of the raid to the Internet, holding the victims hostage. Unapologetic for the attack, the Jester continues his patriot hacking campaign.
"I also had a list of "targets" twitter usernames I was interested in, these were comprised of usernames of: Islamic Extremists, Al Qaeda Supporters, Anonymous Members, Lulz/Antisec Members EVERYONE else without exception was left totally "untouched" so to speak. This was a Proof of Concept QR-Code based operation against known bad guys, the same bad guys that leak YOUR information, steal YOUR CC nums, and engage in terror plots around the world. I do not feel sorry for them. In the interests of convenience I will be taking the liberty of uploading the captured bad-guy data in a signed PGP encrypted file to a suitable location very soon. How's that for "lulz"?
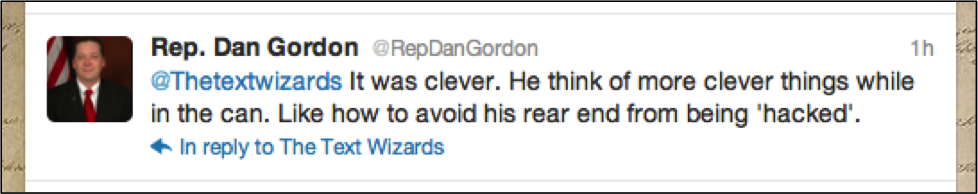
Included in the attack was US State Representative Dan Gordon. Angered over a 2010 new article about the US State Representative, (CBS, 2010) The Jester made the attack personal against the Representative. The twitter account for the US representative holds messages indicating that the FBI will now target The Jester under crimes ranging from threating a state official to hacking the cellular phone of the representative. As with all developing news, it is still unclear whether the representative's Twitter account has also been hacked with his phone. A less than professional message on Twitter leads us to believe his Twitter account has been hacked. This brings us to an interesting lesson learned in the attack. Once compromised on a mobile device, you must consider all your accounts compromised. Since our mobile devices often contain multiple mail, phone, contact, social media, and personal information ; we must consider all this information compromised.
Some technical questions still remain. The Pw2Own exploit used by Charlie Miller in 2011 could not bypass Address Space Layout Randomization (ASLR). Since OS 4.2.3, The iPhone has had a limited ASLR implementation that would have made Miller's exploit not work correctly. Did the Jester recycle Miller's 1-year-old exploit or did he upgrade it for iOS? If so, how did he bypass ASLR? Further, CVE-2010-1807 only works for Android 2.1 and below devices. How was this exploit upgraded? Additionally, would changing the default credentials on iOS (through jail-breaking the device) have prevented the privilege escalation portion of the attack against iOS? If the victims used non-standard mail, twitter, and SMS applications ; the attacker would not have not noticed them (Win one for security through obscurity.)
Although we are constantly reminded of the threats facing us, at least this threat was targeted and against specific members of Anonymous and Al Qaeda, which the majority of us do not belong in. But it reminds us of the threat that is out there. I'll repeat again what I've said multiple times: Cyber is assymetric warfare ; it favors the individual, it favors the adversary. Did the Jester just accomplish in two weeks what it took the federal government months and deals with a known criminal? Maybe, the details have yet to emerge.
References
Avraham, I. (2011, November 14) Android 2.0 / 2.1 Use-After-Free Remote Code Execution ÷ Packet Storm. Packet Storm ÷ Full Disclosure Information Security. Retrieved March 11, 2012, from http://packetstormsecurity.org/files/95850/Android-2.0-2.1-Use-After-Free-Remote-Code-Execution.html
Bray, C. (2012, March 9). FBI's 'Sabu' Hacker Was a Model Informant - WSJ.com. Business News & Financial News - The Wall Street Journal - Wsj.com. Retrieved March 11, 2012, from http://online.wsj.com/article/SB10001424052970204603004577269844134620160.html?mod=googlenews_wsj
CBSNEWS, (2011, November 24). Lawmaker's Gulf War claims, records don't match - CBS News. Breaking News Headlines: Business, Entertainment & World News - CBS News. Retrieved March 11, 2012, from http://www.cbsnews.com/2100-250_162-20111212.html
Davi, L. (2010, November 13). Privilege Escalation Attacks on Android. System Security Lab Ruhr-University Bochum, Germany. Retrieved March 11, 2012, from www.ei.rub.de/media/trust/veroeffentlichungen/2010/11/13/DDSW2010_Privilege_Escalation_Attacks_on_Android.pdf
Heider, J. (2012, February 27). Further Information on iOS Password Protection. Fraunhofer Institute for Secure Information Technology (SIT). Retrieved March 11, 2012, from http://sit.sit.fraunhofer.de/studies/en/sc-iphone-passwords-faq.pdf
Liebowitz, M. (2012, February 21). Could Anonymous Really Knock Out the Power Grid? - Technology & science - Security - msnbc.com. msnbc.com - Breaking news, science and tech news, world news, US news, local news- msnbc.com. Retrieved March 11, 2012, from http://www.msnbc.msn.com/id/46468844/ns/technology_and_science-security/t/could-anonymous-really-knock-out-power-grid/
Naraine, R. (2011, March 10). Charlie Miller wins Pwn2Own again with iPhone 4 exploit | ZDNet . Technology News, Analysis, Comments and Product Reviews for IT Professionals | ZDNet. Retrieved March 11, 2012, from http://www.zdnet.com/blog/security/charlie-miller-wins-pwn2own-again-with-iphone-4-exploit/8378
OConnor, T. (2011, December 30). SANS Reading Room. The Jester Dynamic. Retrieved March 11, 2012, from http://www.sans.org/reading_room/whitepapers/attacking/jester-dynamic-lesson-asymmetric-unmanaged-cyber-warfare_33889
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Basically jester bluffed, & Dan has called him on it. Now it's pure lulz as T0x1c ownz jest.
DeHeyS_fuzz
Mar 12th 2012
1 decade ago
- h4zzmatt
h4zzmat
Mar 12th 2012
1 decade ago
Tisiphone
Mar 12th 2012
1 decade ago
Phil
Mar 13th 2012
1 decade ago