A blast from the past - XXEncoded VB6.0 Trojan
While going over what my e-mail malware quarantine caught during this week, I found a message which made me feel rather nostalgic. Among the usual maldocs, ZIPs and ACEs, there was also an e mail carrying an XXE file in its attachment.
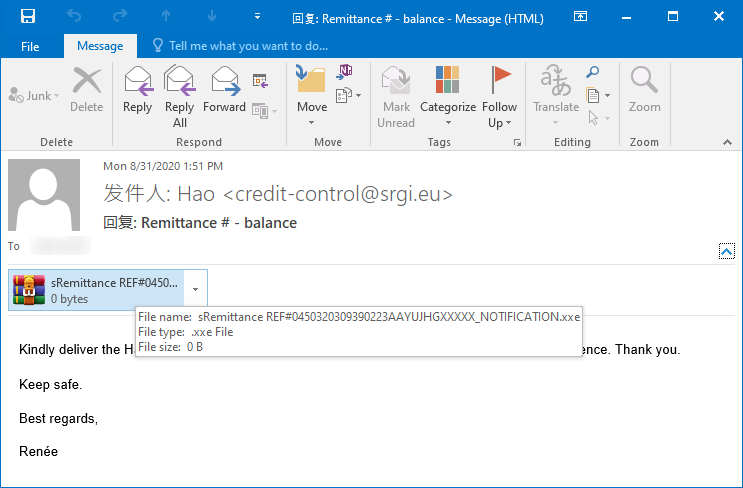
XXE is an archive format which uses xxencoding[1], a form of archaic binary-to-text encoding, which was historically used mainly for transferring files over e-mail[2]. Although the encoding has not been in common use for many years, some archiving utilities (e.g. WinRAR[3]) still support its use, which is why malware authors sometimes try to use this format to bypass AV scans[4]. I haven’t seen any such attempts nor mention of them for some time now though, which is why it caught my eye.
The file was generated by PowerArchiver and inside of it, there was another example of historical file format – a Visual Basic 6.0 executable. The EXE currently has a 21/68 "score" on VirusTotal[5].
Although it is fairly old, VB6.0 is still sometimes used by malware authors since it can make certain aspects of detection and analysis of their creations a bit more difficult. In this case, the code is packed and heavily obfuscated and I didn’t have time to go over it in detail yet, but from what I’ve seen so far, it seems probable that it might be a version of the GuLoader Trojan[6].
Whether this assumption turns out to be true or not, seeing a campaign, which uses xxencoding along Visual Basic 6.0 is an interesting trip down the memory lane and goes to show that even archaic technologies and formats may have a future when it comes to malware…
Indicators of Compromise (IoCs)
Demimonderneoverk9.exe / sRemittance REF#0450320309390223AAYUJHGXXXXX_NOTIFICATION.exe (100 kB)
MD5 - 0eae49ec06ffc2593b4d6bb0ea5a48bc
SHA1 - be57f56d3b98196c0043fa03f306757cd04abc4f
[1] https://en.wikipedia.org/wiki/Xxencoding
[2] http://www.math.utah.edu/cgi-bin/man2html.cgi?/usr/local/man/man1/xxencode.1
[3] https://extension.nirsoft.net/xxe
[4] https://wapacklabs.blogspot.com/2018/04/new-pony-loader-obfuscation-technique.html
[5] https://www.virustotal.com/gui/file/8759a203b452c780a8fb8b630a25e1b246fcffe34470dd7d57da1bb01984c368/details
[6] https://www.crowdstrike.com/blog/guloader-malware-analysis/


Comments