9 Fast and Easy Ways To Lose Your Crypto Coins
Looking at the cost of cryptocurrencies this weekend, it looks like many of you will find a few bitcoins under your tree instead of a new game console. It appears to become a big holiday gift. With all the attention given to cryptocurrencies, they have also become a top target for criminals this season. In many ways, stealing someone's crypto wallet is more lucrative than stealing a credit card number and in many ways easier. Creditcards can be blocked very quickly, and credit card companies are actively looking for fraud, often detecting it before the customer does. In some cases fraudulent credit card transactions can be reversed. With cryptocurrencies, you have to watch out for fraud yourself and there is little recourse if a wallet is stolen, in particular, if you do not realize right away that it has been stolen.
But stealing your wallet is far from the only fraudulent activity we have observed recently.
First of all the obligatory cryptocurrency primer: What is a "Cryptocurrency Wallet"? Unlike a real wallet, a cryptocurrency wallet does not hold a "balance" in the traditional sense. A cryptocurrency wallet is a secret key. You can use the secret key to prove that you are the owner of a particular address, and the public blockchain ledger will allow others to figure out your current balance. So the secret you need to safeguard is this secret key.
A second activity that is often discussed is "mining". Mining refers to assisting in maintaining the public ledger for a cryptocurrency. As a user of cryptocurrencies, you do not have to mine. But if you do, you are rewarded by receiving more "coins".
You do not even have to maintain your own wallet. Instead, you can keep your coins with a cryptocurrency exchange that acts in some ways like a bank.
So how are bad guys abusing this system?
1 - Crypto Pick Pockets
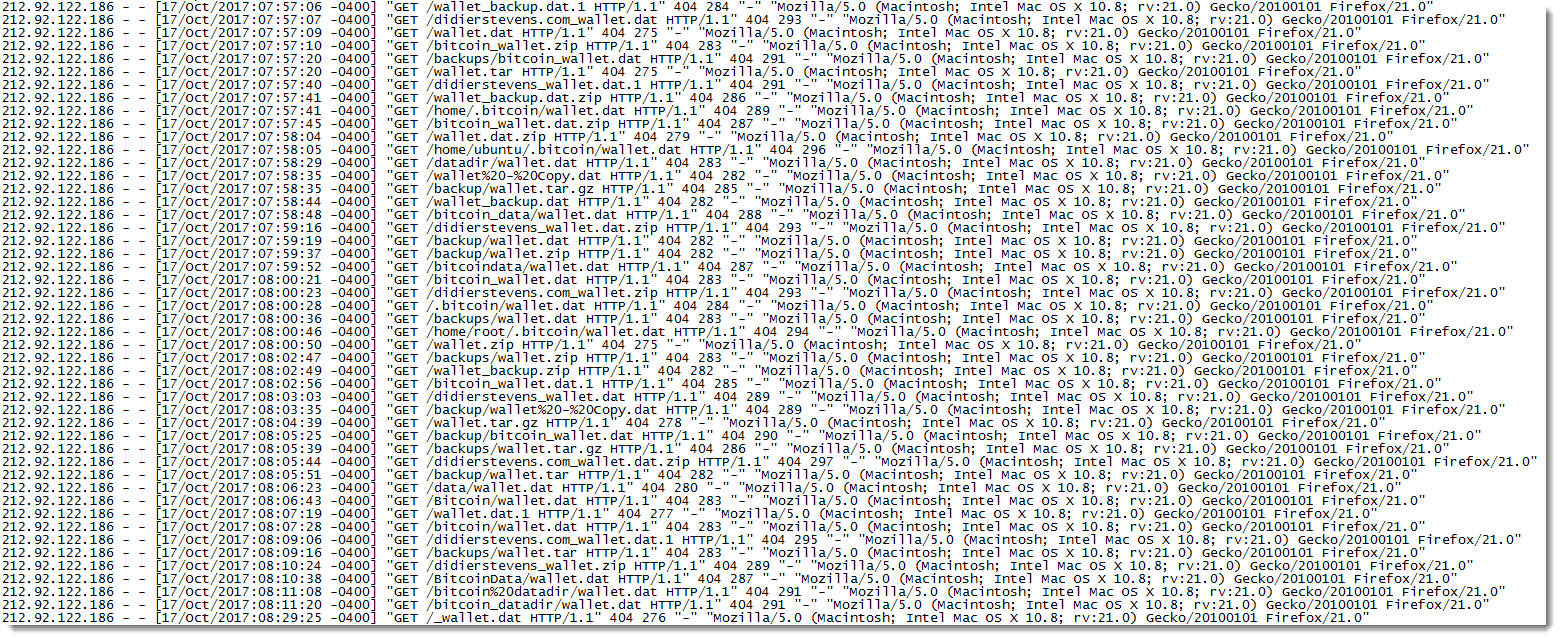
As discussed above, a wallet is a secret key. Typically, the key is protected with a password. But just like any other password, these passwords are not always all that safe. The key itself is a file that can be copied (stolen) just like any other file. We have seen last week how some criminals are searching websites for carelessly exposed wallets. Various pieces of malware have also started stealing cryptocurrency wallets just like they steal credit card numbers.
2 - Rogue Crypto Currency Miners.
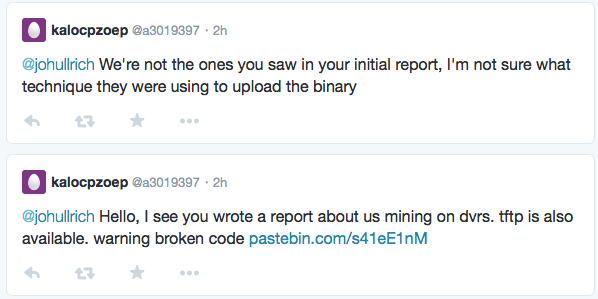
This variant takes advantage of the fact that mining pays. The problem with mining cryptocurrencies is that it is a computationally expensive process. Professional equipment to do so is expensive and can take a lot of power to operate. The "solution" here is to use someone else's equipment to "mine". To do this, the miscreant will compromise systems, and install mining software on them. Mining software typically does not require any special privileges. A simple exploit against an outdated Wordpress install, or a weak FTP password, can be used to install a miner. The victim is stuck with the power bill, and the miscreant will earn the cryptocurrency. Of course, client software can also be used and we have certainly seen traditional client-side exploit kits that install crypto coin miners. But these miners tend to be most effective on servers that have substantial CPUs or graphics cards and are on 24/7.
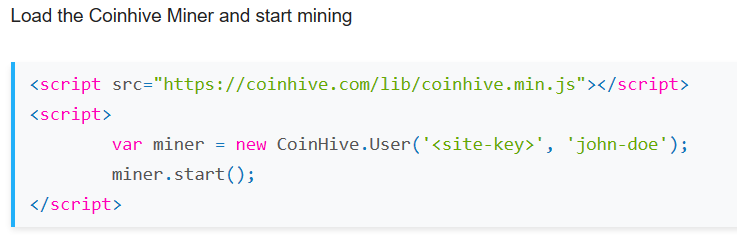
3 - Cryptojacking - Javascript Miners
At first, rogue miners were typically installed on systems via a vulnerability that allowed arbitrary code execution. A exploit-free option, that has become quite popular recently is the use of Javascript miners. Coinhive has quickly become a market leader to make it easy to install miners in someone's browser. The intent is not always malicious. Coinhive typically requires consent from the user. But we have seen the script installed more often without asking for consent. Also, Coinhive does not take advantage of any vulnerabilities. Instead, it uses regular Javascript to mine. Javascript miners tend to mine Monero, a cryptocurrency that was designed to be mined using commodity equipment, and that has strong privacy features making it much more difficult to trace transactions.
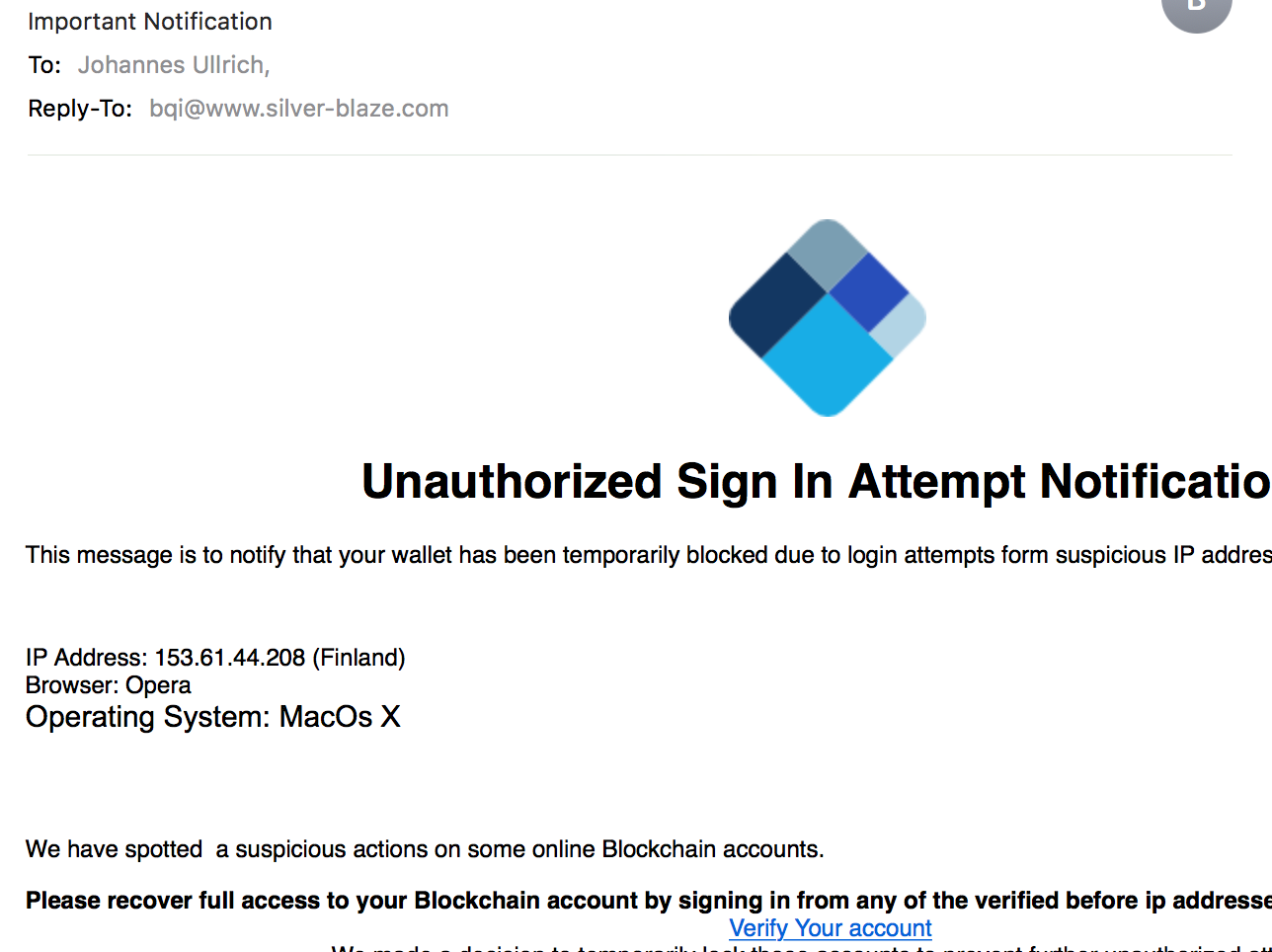
4 - Phishing
Good old phishing is often used to extract credentials for currency exchanges from users. Some exchanges have moved to two-factor authentication, but not all have. These phishing attacks have become quite sophisticated and in some cases exceed the quality of an average online banking phish. For example, just last week I came across one that used an international domain name and a valid TLS certificate to impersonate a cryptocurrency exchange.
5 - Attacks Against Mining Equipment
In the end, a "Cryptocurrency Mining Rig" is a computer. It is vulnerable to all the same problems that any other computer is vulnerable too. For example, many of them use standard ssh usernames and passwords. If an attacker has access to the equipment via SSH, they can use the username and password to take over the equipment and have it mine for the new owner. This is a bit like the rogue miners above, with the difference that the equipment is designed to mine.
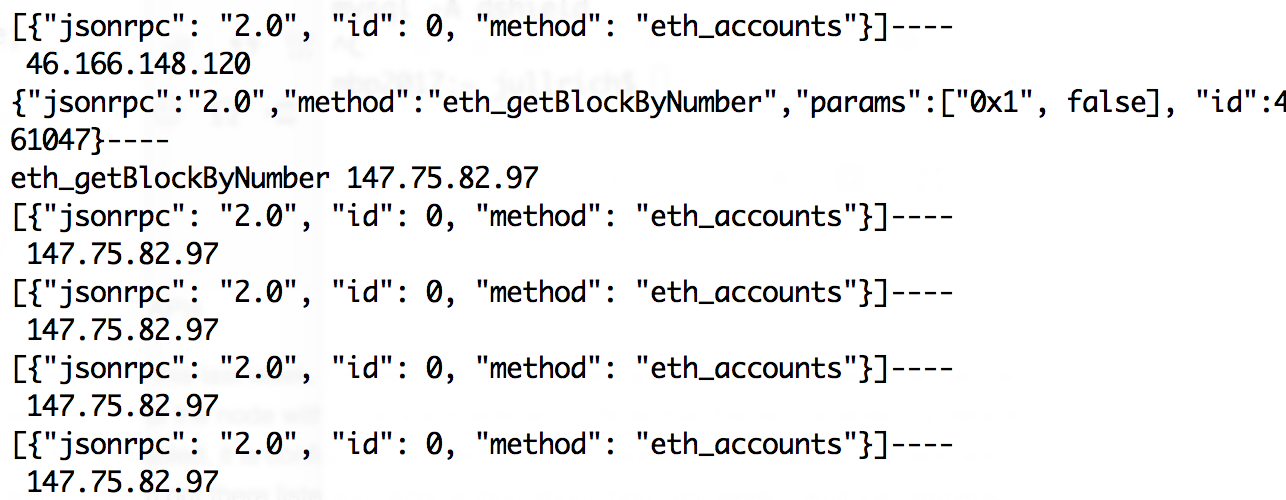
6 - Attacking APIs
I wrote about this last week. Ethereum nodes have an optional RPC interface that can be used to control the node without any authentication. Note that this isn't enabled by default, and if it is enabled, it is configured to listen only on "loopback", but apparently there are plenty of them out there listening. After writing about them last week, Dimitrios Slamaris reached out via twitter that he has observed these scans before (see his blog here: https://blog.3or.de/internet-wide-ethereum-json-rpc-scans.html ). We will have more about this in a couple days.
7 - Weak Random Numbers
As mentioned above, the security of your bitcoin wallet depends on a secret key. If this secret key is not random, then an attacker is able to guess it and take over your wallet without ever touching your system. There have been some wallet implementations in the past that have used known bad random number generators. In particular mobile applications appear to be affected by this issue. The secret key is not created by the user, and its randomness is not depending on the password. (But a strong password is still a good idea to protect the key.
8 - Stealing Power
You got a high-end cryptocurrency mining rig, but the power bill is eating all your profits? Use someone else's power. For example, having a mining rig under a work desk to use company power.
9 - Don't make backups
This doesn't involve anybody stealing your money, but it is an important issue to mention. You are in full control of your cryptocurrency wallet. Nobody else is. This means, that it is your sole responsibility to guard the wallet. If the wallet is every lost (for example a crashed hard drive), then you will have no way to recover your money. One common way is to create a "paper wallet" (print the key, typically in the form of a QR code). Only keep the money you currently need in electronic form. It is easy to copy the paper wallet. But again: Make sure you don't let other's see the code.
In conclusion: With cryptocurrencies, there are no bank or other institutions or regulations that will cover you in case of a loss. If a bitcoin exchange goes under, or if it turns out to be fraudulent, then there is very little you can do to get your money back. As they say: With great freedom comes great responsibility.
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments