Twitpic, EXIF and GPS: I Know Where You Did it Last Summer
Modern cell phones frequently include a camera and a GPS. Even if a GPS is not included, cell phone towers can be used to establish the location of the phone. Image formats include special headers that can be used to store this information, so called EXIF tags.
In order to test the prevalence of these tags and analyze the information leaked via EXIF tags, we collected 15,291 images from popular image hosting site Twitpic.com. Twitpic is frequently used together with Twitter. Software on smart phones will take the picture, upload it to twitpix and then post a message on Twitter pointing to the image. Twitpic images are usually not protected and open for all to read who know the URL. The URL is short and incrementing, allowing for easy harvesting of pictures hosted on Twitpic.
We wrote a little script to harvest 15,291 images. A second script was used to analyze the EXIF information embedded in these images. About 10,000 of the images included basic EXIF information, like image resolution and camera orientation. 5247 images included the Camera Model.
Most interestingly: 399 images included the location of the camera at the time the image was taken, and 102 images included the name of the photographer. Correlating the camera model with the photographer field, we found that it was predominantly set for the Canon and Nikon cameras. Only few camera phones had the parameter set.
GPS coordinates where only set for phones, with one single exception (a Nikon Point and Shoot camera, which does not appear to come with a build in GPS. The location may have been added manually or by an external GPS unit). The lion share of images that included GPS tags came from iPhones.
The iPhone is including the most EXIF information among the images we found. The largest EXIF data set we found can be found here. It not only includes the phone's location, but also accelerometer data showing if the phone was moved at the time the picture was taken and the readout from the build in compass showing in which direction the phone was pointed at the time.
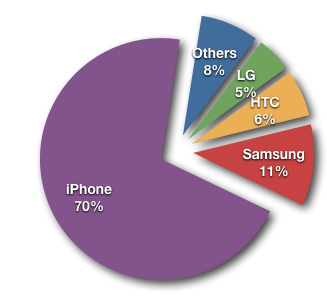
Figure 1: Pictures with GPS coordinates broken down by Phone manufacturer.
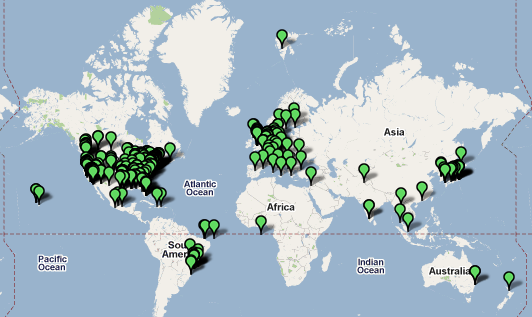
Figure 2: Geographic Distribution of Images
Now the obvious question: Anything interesting in these pictures? The images all the way up north shows an empty grocery store (kind of like in the DC area these days). The picture at the Afghan - Pakistan border shows a pizza... Osama got away again I guess.
The scripts used for this can be found here: http://johannes.homepc.org/twitscripts.tgz (two scripts, also needs "exiftools" to pull out the data).
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
My name is not in the EXIF data for the iphone, but the pictures from my canon do have my name (I know I put it in the camera).
John
John
Feb 11th 2010
1 decade ago
The note says that all diary products have moved elsewhere. The picture is from Longyearbyen, Spitsbergen.
tyldis
Feb 11th 2010
1 decade ago
My Android phone has a setting for "Store location in pictures", which can be turned off if you desire.
The phones have several mechanisms for determining location. It can use the location of the nearest cell towers as an approximation, and those coordinates can obviously be off by quite a bit. If I turn on real GPS in the phone, it is quite close. But I choose to leave it turned off - it really sucks down the battery, and I simply don't need it 99% of the time.
Jack Russell
Feb 11th 2010
1 decade ago
Greg
Feb 11th 2010
1 decade ago
Dr. Phil
Feb 11th 2010
1 decade ago
Regarding GPS and the iPhone: The iPhone will use cell phone towers if it doesn't get a clean GPS signal. In that case, accuracy is not that great. GPS signals take a while to acquire and if you just pull your phone and take a quick snapshot, chances are that you are using the non-GPS coordinates.
I guess they could add the location accuracy to the EXIF data (if it is not already in there somewhere)
Dr. J
Feb 11th 2010
1 decade ago
What an idea! I bet there is a code. Maybe if you overlay a map to the pizza, the meat pieces mark attack sites. Or maybe a grid that then is used to encode words!
Dr. J
Feb 11th 2010
1 decade ago
Ben K.
Feb 11th 2010
1 decade ago
David
Feb 12th 2010
1 decade ago
I use the exif utility (http://libexif.sourceforge.net) to remove or scramble the EXIF data on my images before I post them.
No Love.
Feb 12th 2010
1 decade ago