Example of Phishing Campaign Project File
We all have a love and hate relation with emails. When newcomers on the Internet starts to get emails, they are so happy but their feeling changes quickly. Then, they hope to reduce the flood of emails received daily... Good luck! Of course, tools have been developed to organize marketing campaigns. From marketing to spam or phishing, there is only one step. Bad guys started to use the same programs for malicious purpose.
Yesterday, I found on VT an interesting file. It triggered one of my hunting rules because the file contained a reference to one of my customer’s domain. I had a look at the file named “EwoExcel (1).mmp’ (SHA256:0e016a41b6df3dc7daf076805e3cbb21df1ff33712b615d38ecf066cd25b6e06)[1].
I was not aware of the file extension “.mmp” (it’s not a “.mpp” used by Microsoft Project). But it seems to be a project file:
00000050: 5072 6f6a 6563 7443 7265 6174 696f 6e44 ProjectCreationD 00000060: 6174 65e7 1100 3130 2f32 352f 3232 2038 ate...10/25/22 8 00000070: 3a31 333a 3332 700d 5072 6f6a 6563 7441 :13:32p.ProjectA 00000080: 7574 686f 72e7 0000 0c50 726f 6a65 6374 uthor....Project 00000090: 4e6f 7465 73e7 0000 0c50 726f 6a65 6374 Notes....Project 000000a0: 5469 746c 65e7 0000 0e50 726f 6a65 6374 Title....Project 000000b0: 4d61 6e61 6765 72e7 0000 0e50 726f 6a65 Manager....Proje 000000c0: 6374 4465 7363 7269 70e7 0000 0e50 726f ctDescrip....Pro 000000d0: 6a65 6374 5665 7273 696f 6ee7 0400 3532 jectVersion...52 000000e0: 2e30 1650 726f 6a65 6374 5665 7273 696f .0.ProjectVersio 000000f0: 6e4f 7269 6769 6e61 6ce7 0400 3531 2e30 nOriginal...51.0 00000100: 0466 726f 6de7 3f00 3d3f 5554 462d 383f .from.?.=?UTF-8? 00000110: 423f 5158 5230 5957 4e6f 5a57 5167 5a47 B?QXR0YWNoZWQgZG 00000120: 396a 4947 5a76 6367 3d3d 3f3d 205b 5b2d 9jIGZvcg==?= [[- 00000130: 5573 6572 2d5d 5d20 3c6a 6a68 4064 6875 User-]] <jjh@dhu
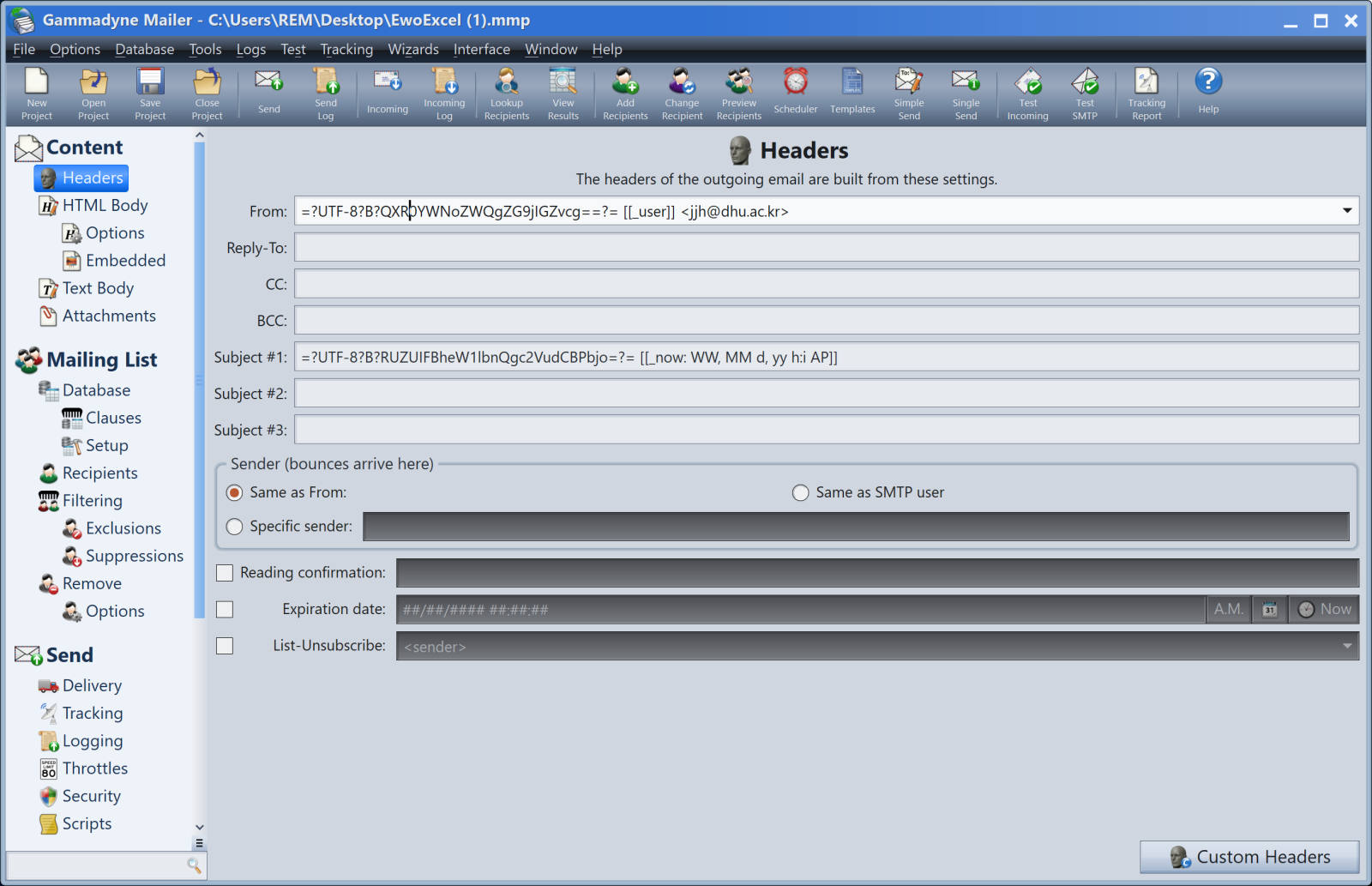
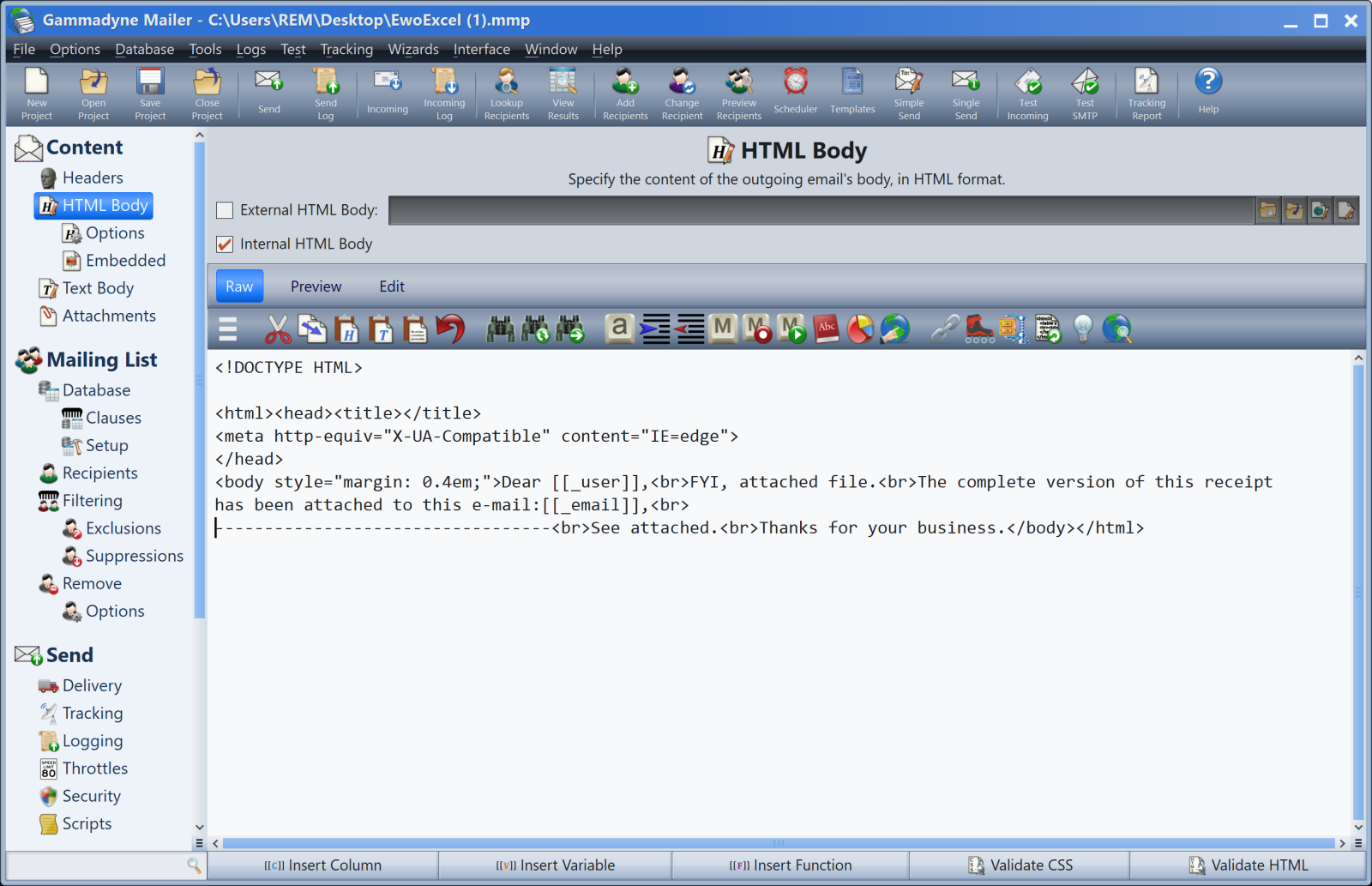
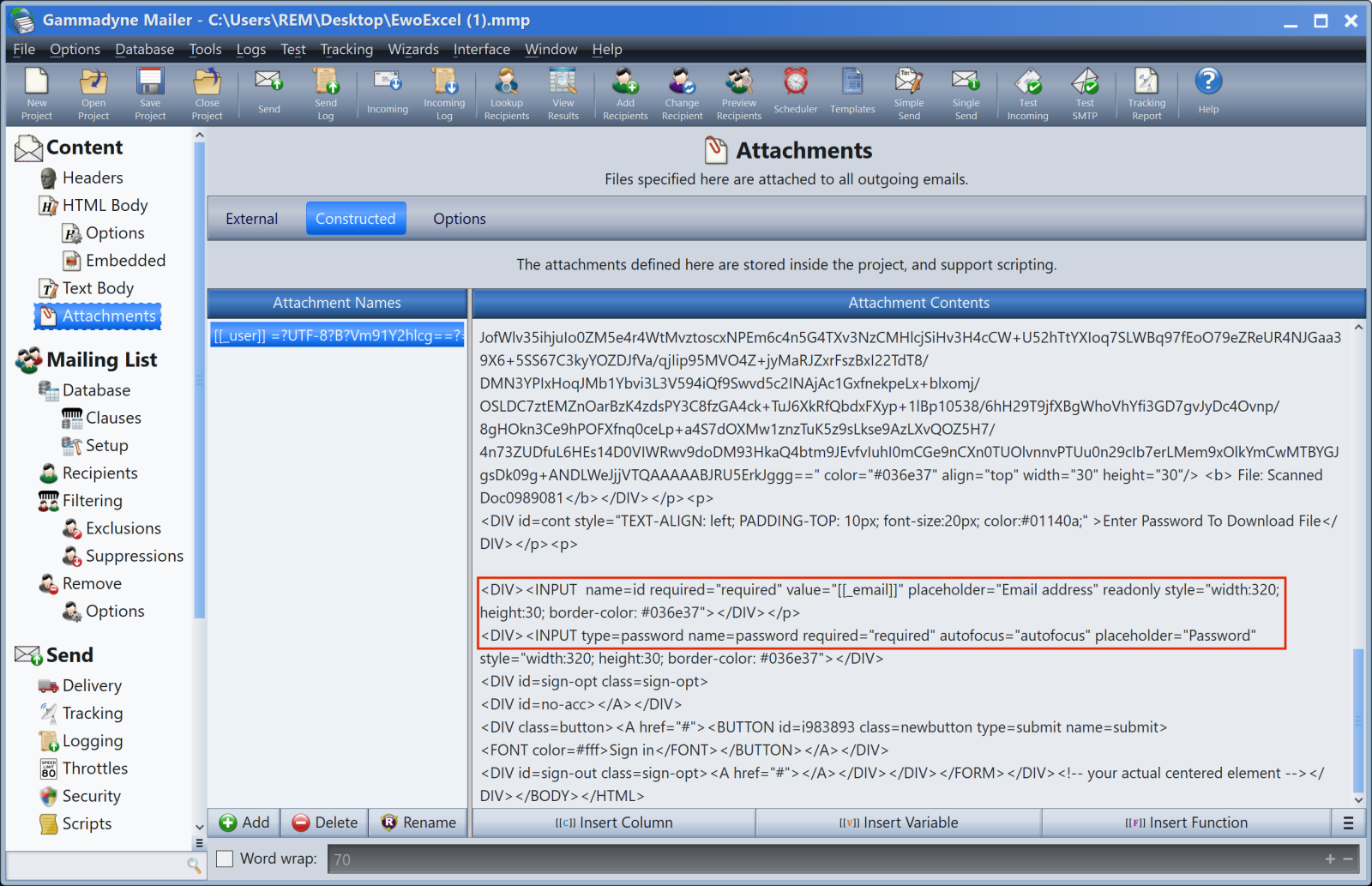
The file was created in 2022 but was recently uploaded on VT. Such documents are managed via an application called “GammaDyne”[2]. Once installed in my sandbox, the application was able to handle the file and reveal its secrets. It’ contains defailts about a classic phishing campaign project:
The mail subject contains "Attached doc for" (Base64-encoded).
As you can see, attackers do not re-invent the wheel and use classic tools to organize their phishing campaign.
Funny wrap-up: I found that Didier discovered the same type of file already in 2020![3]
[1] https://www.virustotal.com/gui/file/0e016a41b6df3dc7daf076805e3cbb21df1ff33712b615d38ecf066cd25b6e06/detection
[2] https://www.gammadyne.com/email_software.htm
[3] https://isc.sans.edu/diary/File+Selection+Gaffe/26694
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments