Exploit Attempts for "Stagil navigation for Jira Menus & Themes" CVE-2023-26255 and CVE-2023-26256
Today, I noticed the following URL on our "first seen URLs" page:
/plugins/servlet/snjFooterNavigationConfig?fileName=../../../../etc/passwd&fileMime=$textMime
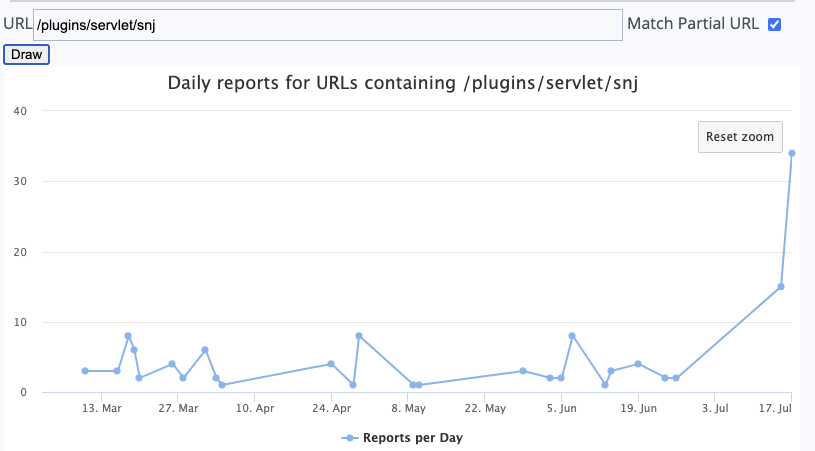
We had one report for this URL on March 28th, but nothing since then. Yesterday, the request showed up again and reached our reporting threshold.
All of yesterday's requests appear to come from a single Chinese consumer broadband IP address: 124.127.17.209.
The vulnerability was disclosed in March as one of two vulnerabilities in "Stagil navigation for Jira – Menus & Themes" [1]. The tool is a plugin for Jira to customize the look and feel of Jira. It is distributed via the Atlassian Marketplace.
CVE-2023-26255 and CVE-2023-26256 were both made public at the same time and describe similar directory traversal vulnerabilities. These vulnerabilities allow attackers to retrieve arbitrary files from the server. As you can see in the exploit above, the attacker attempts to download the "/etc/passwd" file. Typically, '/etc/passwd/ is not that interesting. But it is often used to verify a vulnerability. The attacker may later retrieve other files that are more interesting.
Jira is always a big target. It organizes software development and can be an entry point to a supply chain attack.
After seeing the attacks for one fo the vulnerabilities, I went back to look for attempts to exploit the second directory traversal vulnerability, and indeed, it is also being exploited. Two days earlier, we saw a small increase in requests from %%112.118.71.111%%, an IP address associated with an ISP in Hongkong.
The request used is similar in that it attempts to retrieve "/etc/passwd":
/plugins/servlet/snjCustomDesignConfig?fileName=../../../../etc/passwd&fileMime=$textMimeLooking further, I was able to find attempts to retrieve "/dbconfig.xmlpasswd" using the vulnerability:
/plugins/servlet/snjCustomDesignConfig?fileMime=$textMime&fileName=../dbconfig.xmlpasswd
Jira uses dbconfig.xmlpasswd to store database passwords [2]
As usual, be careful installing plugins for Jira. Plugins have been a significant source of vulnerabilities in the past. Jira should also not be exposed to the internet directly but needs to be protected by a VPN or other measures. It is too important and too juicy of a target to expose it. Even Jira itself had a number of vulnerabilities before installing any plugins.
It is not clear if the two scans for either vulnerability are related. Having two larger scans for a vulnerability like this within a short time span is suspicious. The scans use different user agents, but this doesn't mean that the scans were launched by different groups/individuals. Neither IP address is associated with a known threat group, as far as I know.
/plugins/servlet/snj"
[1] https://github.com/1nters3ct/CVEs/blob/main/CVE-2023-26256.md
[2] https://confluence.atlassian.com/jirakb/startup-check-creating-and-editing-the-dbconfig-xml-file-881656915.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
PW
Jul 18th 2023
2 years ago