IDS Comparisons with DShield Honeypot Data
by What does an IDS say about honeypot traffic? (Version: 1)
An Intrustion Detection System (IDS) can be helpful to identify suspicious activity. The information recieved from these tools needs to be tuned to the environment so the tool can highlight what is unusual. When looking at honeypot data, it is anticipated to see internet scanners and malicious traffic. What's the point of looking at IDS data for a honeypot? Well, it can be useful to test and IDS or compare different IDS tools. In my lab environment, network data is captured and analyzed with Suricata[1] (via Corelight[2]) and is also behind a Palo Alto[3] firewall.
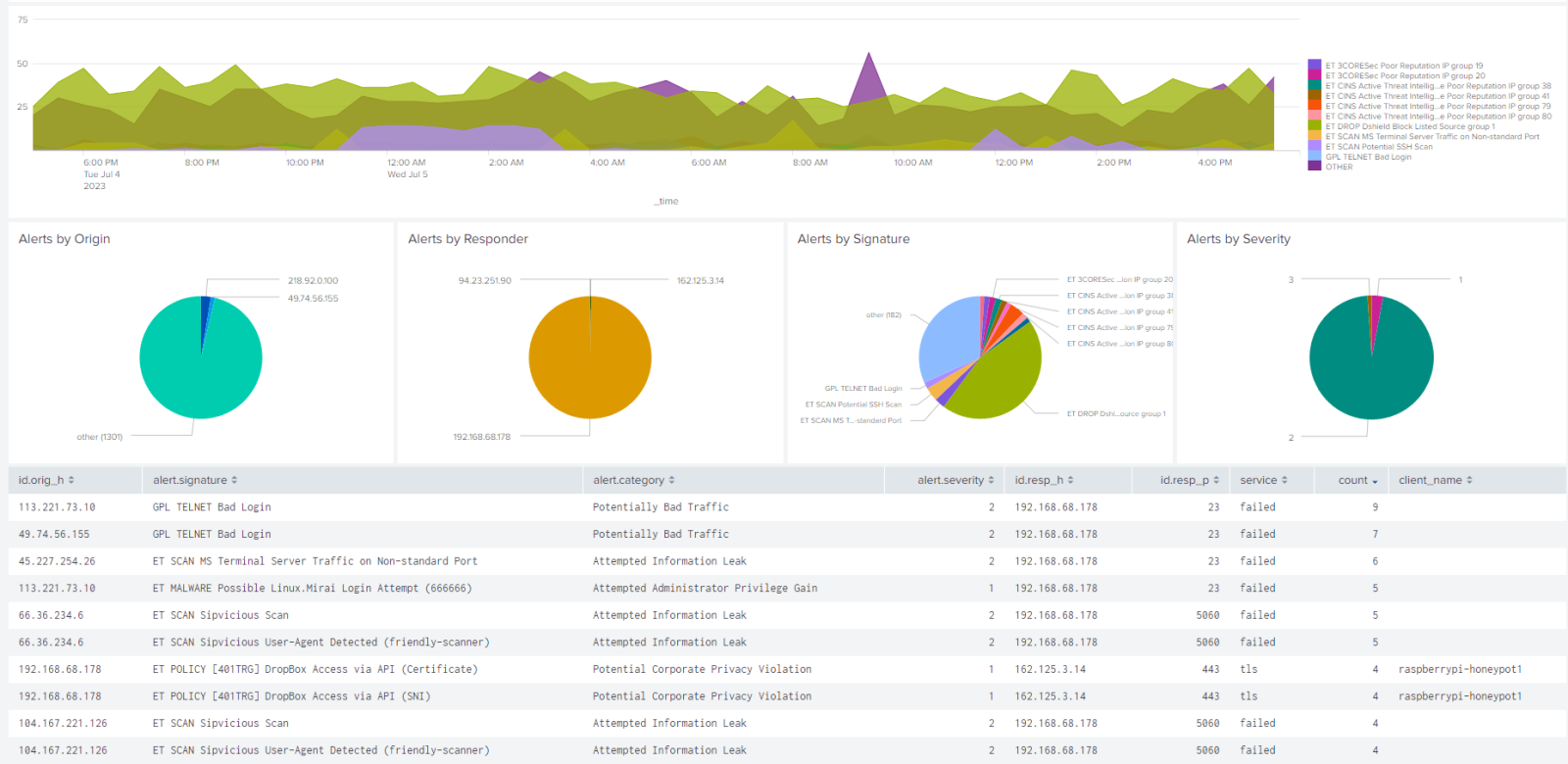
Figure 1: Example Dashboard of Suricata IDS data
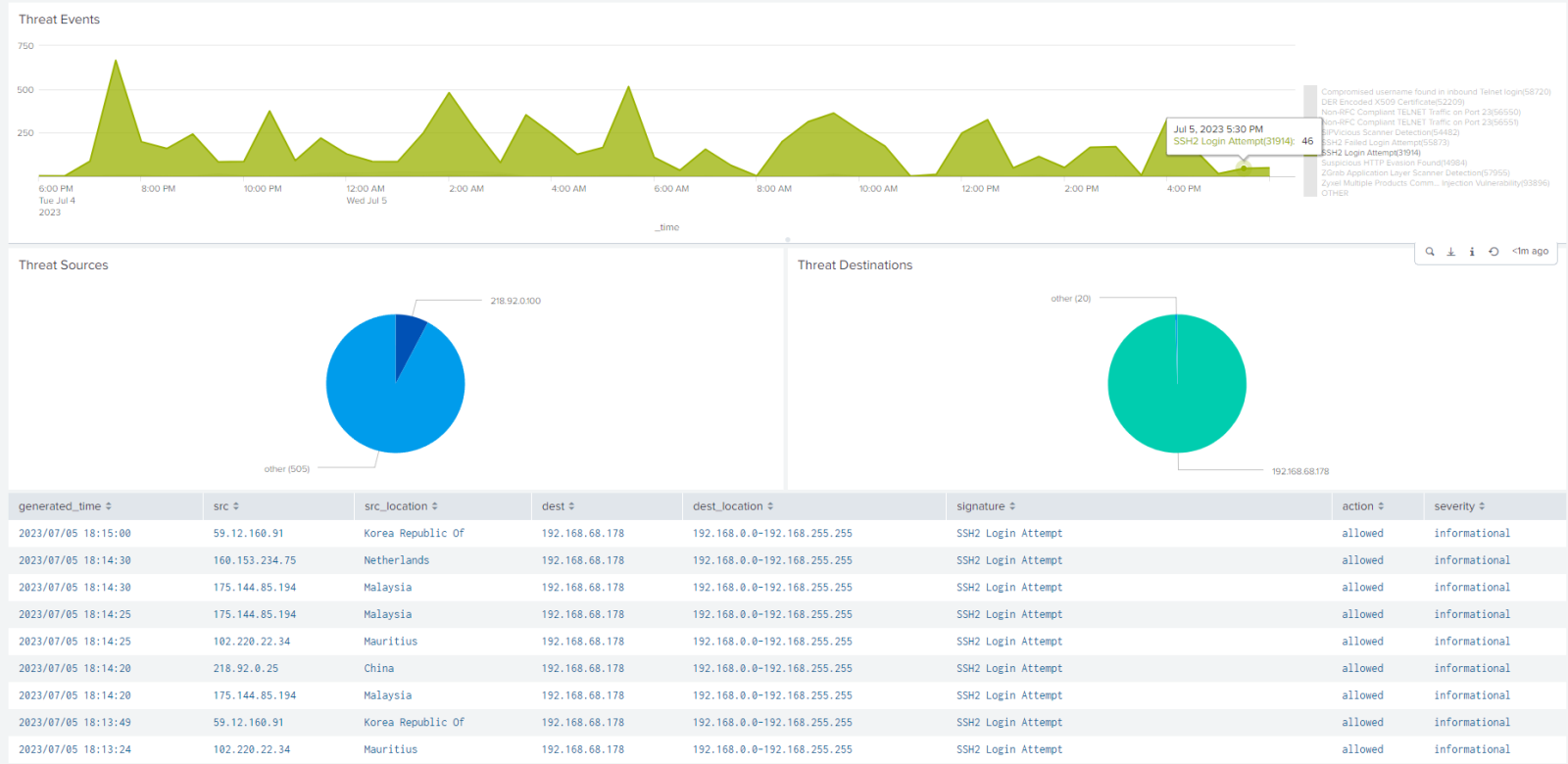
Figure 2: Example Dashboard of Palo Alto threat data
Suricata Data
Let's take a look at the last three (3) months of Suricata alert data. The data is split up into categories and signatures.
| alert.signature | alert.category | Count | Percentage |
| ET DROP Dshield Block Listed Source group 1 | Misc Attack | 144228 | 30.16% |
| ET DROP Dshield Block Listed Source group 1 | Unknown Classtype | 54374 | 16.28% |
| ET SCAN Potential SSH Scan | Attempted Information Leak | 22889 | 8.19% |
| ET SCAN MS Terminal Server Traffic on Non-standard Port | Attempted Information Leak | 14903 | 5.81% |
| ET INFO SSH-2.0-Go version string Observed in Network Traffic - Inbound | Misc activity | 6572 | 2.72% |
| GPL TELNET Bad Login | Potentially Bad Traffic | 6066 | 2.58% |
| ET SCAN Potential SSH Scan | Unknown Classtype | 4287 | 1.87% |
| ET INFO SSH-2.0-Go version string Observed in Network Traffic - Inbound | Unknown Classtype | 3929 | 1.75% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 84 | Misc Attack | 3363 | 1.52% |
| ET SCAN Suspicious inbound to MSSQL port 1433 | Potentially Bad Traffic | 3315 | 1.52% |
| GPL TELNET Bad Login | Unknown Classtype | 3016 | 1.41% |
| ET 3CORESec Poor Reputation IP group 18 | Misc Attack | 2767 | 1.31% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 81 | Misc Attack | 2701 | 1.30% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 83 | Misc Attack | 2514 | 1.22% |
| ET SCAN Sipvicious Scan | Attempted Information Leak | 2448 | 1.20% |
| ET SCAN Sipvicious User-Agent Detected (friendly-scanner) | Attempted Information Leak | 2420 | 1.21% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 78 | Misc Attack | 2305 | 1.16% |
| ET 3CORESec Poor Reputation IP group 17 | Misc Attack | 2263 | 1.15% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 77 | Misc Attack | 2113 | 1.09% |
| ET 3CORESec Poor Reputation IP group 19 | Misc Attack | 1997 | 1.04% |
Figure 3: Suricata Top 20 Signatures
We see a variety of alerts related to Emerging Threats (ET) [4] and many of these are related to DShield honeypot data [5]. This is not a big surprise in this case since this data is directly generated from DShield honeypot traffic. Collective Intelligence Network Security (CINS) entries are also similar using a variety of network sensors and other network data to generate their reputation lists. Some consumers of this data may simply user these signatures to block suspicious sources when using Suricata or other products as an Intrusion Prevention System (IPS).
Looking at this list, we can see a few items of note:
- Potential SSH Scan
- MS Terminal Server Traffic on Non-Standard Port
- TELNET Bad Login
- Suspicious Inbound to MSSQL port 1433
- Sipvicious Scan
- Sipvicious User-Agent Detected (friendly-scanner)
SSH and telnet attacks are very common and anticipated. How about the least common signatures seen?
| Suricata alert.signature | Suricata alert.category | Count | Percentage |
| ET DOS Possible NTP DDoS Inbound Frequent Un-Authed MON_LIST Requests IMPL 0x02 | Unknown Classtype | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 10 | Unknown Classtype | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 12 | Unknown Classtype | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 13 | Unknown Classtype | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 14 | Misc Attack | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 17 | Unknown Classtype | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 7 | Unknown Classtype | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 8 | Misc Attack | 1 | 0.00% |
| ET EXPLOIT AVTECH Authenticated Command Injection in CloudSetup.cgi | Attempted Information Leak | 1 | 0.00% |
| ET EXPLOIT AVTECH Unauthenticated Command Injection in DVR Devices | Attempted Information Leak | 1 | 0.00% |
| ET EXPLOIT Apache HTTP Server 2.4.49 - Path Traversal Attempt (CVE-2021-41773) M1 | Attempted Administrator Privilege Gain | 1 | 0.00% |
| ET EXPLOIT F5 TMUI RCE vulnerability CVE-2020-5902 Attempt M1 | Attempted Administrator Privilege Gain | 1 | 0.00% |
| ET EXPLOIT Fortra MFT Deserialization Remote Code Execution Attempt (CVE-2023-0669) M3 | A Network Trojan was detected | 1 | 0.00% |
| ET EXPLOIT HiSilicon DVR - Application Credential Disclosure (CVE-2018-9995) | Attempted Administrator Privilege Gain | 1 | 0.00% |
| ET EXPLOIT Linksys E-Series Device RCE Attempt | Attempted Administrator Privilege Gain | 1 | 0.00% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 52 | Misc Attack | 530 | 0.11% |
| ET EXPLOIT Possible Vacron NVR Remote Command Execution | Unknown Classtype | 1 | 0.00% |
| ET CINS Active Threat Intelligence Poor Reputation IP group 93 | Misc Attack | 529 | 0.11% |
| ET MALWARE BPFDoor V2 UDP Magic Packet Inbound | A Network Trojan was detected | 1 | 0.00% |
| ET DROP Spamhaus DROP Listed Traffic Inbound group 3 | Misc Attack | 529 | 0.11% |
Figure 4: Top 20 least common Suricata signatures
These are a bit more interesting that may call for further investigation since they're less seen, even for a device we anticipate to be attacked regularly.
Palo Alto Data
Now digging into the last three (3) months of Palo Alto Threat log data.
| Palo Alto Threat Signature | Count | Percentage |
| SSH2 Login Attempt | 788446 | 83.97% |
| Suspicious HTTP Evasion Found | 29816 | 3.18% |
| Non-RFC Compliant TELNET Traffic on Port 23 | 28997 | 3.09% |
| SSH2 Failed Login Attempt | 18040 | 1.92% |
| SSH User Authentication Brute Force Attempt | 15273 | 1.63% |
| Compromised username found in inbound Telnet login | 8881 | 0.95% |
| Ncrack RDP scan | 6062 | 0.65% |
| SIPVicious Scanner Detection | 5410 | 0.58% |
| Possible HTTP Malicious Payload Detection | 4300 | 0.46% |
| Suspicious File Downloading Detection | 3395 | 0.36% |
| Suspicious TLS Evasion Found | 3380 | 0.36% |
| LinkSys E-series Routers Remote Code Execution Vulnerability | 3057 | 0.33% |
| Microsoft Communicator INVITE Flood Denial of Service Vulnerability | 2207 | 0.24% |
| ZGrab Application Layer Scanner Detection | 1993 | 0.21% |
| Non-RFC Compliant DNS Traffic on Port 53/5353 | 1631 | 0.17% |
| ELF File | 1263 | 0.13% |
| DNS ANY Request | 1159 | 0.12% |
| DER Encoded X509 Certificate | 1023 | 0.11% |
| Hypertext Preprocessor PHP File | 907 | 0.10% |
| trojan/Linux.mirai.dxxe | 814 | 0.09% |
Figure 5: Top 20 most common Palo Alto threats
These threats are more specific and not necessarily related to a particular threat list/feed. Let's take a look at the least common threats.
| Palo Alto Signature | Count | Percentage |
| DoS/Linux.xorddos.c | 1 | 0.00% |
| GTPv1-C Create PDP Context Request Message | 1 | 0.00% |
| Tunneling:zhangsh08.com | 1 | 0.00% |
| BZIP2 | 2 | 0.00% |
| Bash Remote Code Execution Vulnerability | 2 | 0.00% |
| JavaServer Pages JSP File | 2 | 0.00% |
| Kolibri WebServer HTTP GET Request Buffer Overflow Vulnerability | 2 | 0.00% |
| Shellshock Bash Remote Code Execution Vulnerability | 2 | 0.00% |
| Suspicious or malformed HTTP Referer field | 2 | 0.00% |
| TP-Link Archer Router Command Injection Vulnerability | 2 | 0.00% |
| Virus/Linux.WGeneric.dymlyv | 2 | 0.00% |
| Virus/Linux.WGeneric.dyoqem | 2 | 0.00% |
| Virus/Linux.WGeneric.dypncj | 2 | 0.00% |
| Windows Executable | 2 | 0.00% |
| new:ap-5590.com | 2 | 0.00% |
| new:nar7878.com | 2 | 0.00% |
| new:qphgcrh.cn | 2 | 0.00% |
| Encrypted ZIP | 3 | 0.00% |
| Non-RFC Compliant HTTP Traffic on Port 80 | 3 | 0.00% |
| ASUS/Netcore Router Default Credential Remote Code Execution Vulnerability | 4 | 0.00% |
Figure 6: Top 20 least common Palo Alto Threats
Comparing Attack Data and Signatures
There was only one "ET DOS Possible NTP DDoS Inbound Frequent Un-Authed MON_LIST Requests IMPL 0x02" signature alert, which should give some good data points to pivot with.
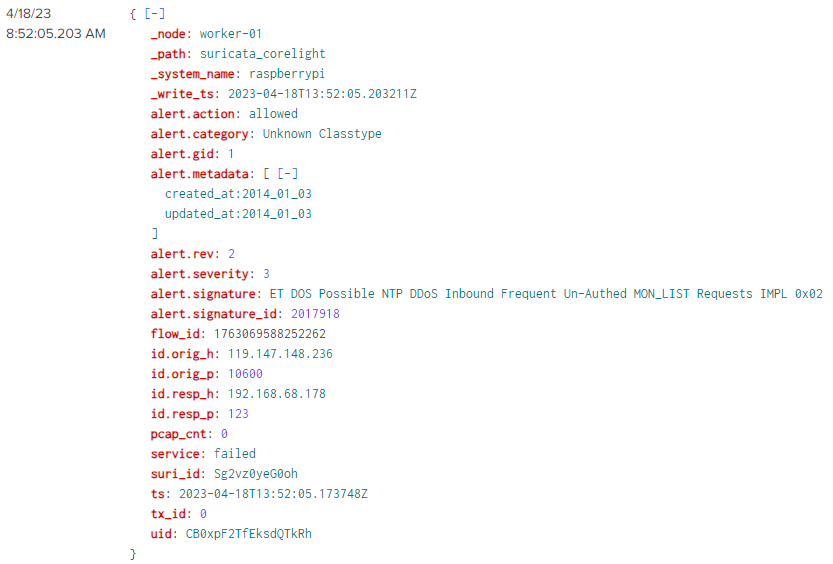
Figure 7: Suricata alert data for Possible NTP DDoS attack
Looking into the Palo Alto data, the traffic logs are seen that may correlate, but no specific threat data showed up in the collected logs.
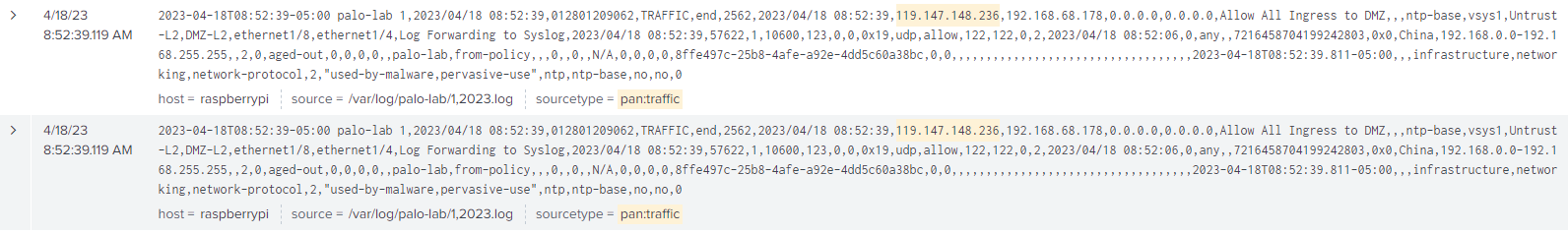
Figure 8: Traffic logs from Palo Alto nearest to Suricata alert
Luckily, I also collect full PCAPs of my honeypot using tcpdump. While there have been issues noted with some of these captures in the past[7], it can be useful in just these kinds of sutations since no additional information is logged directly by the honeypot itself.
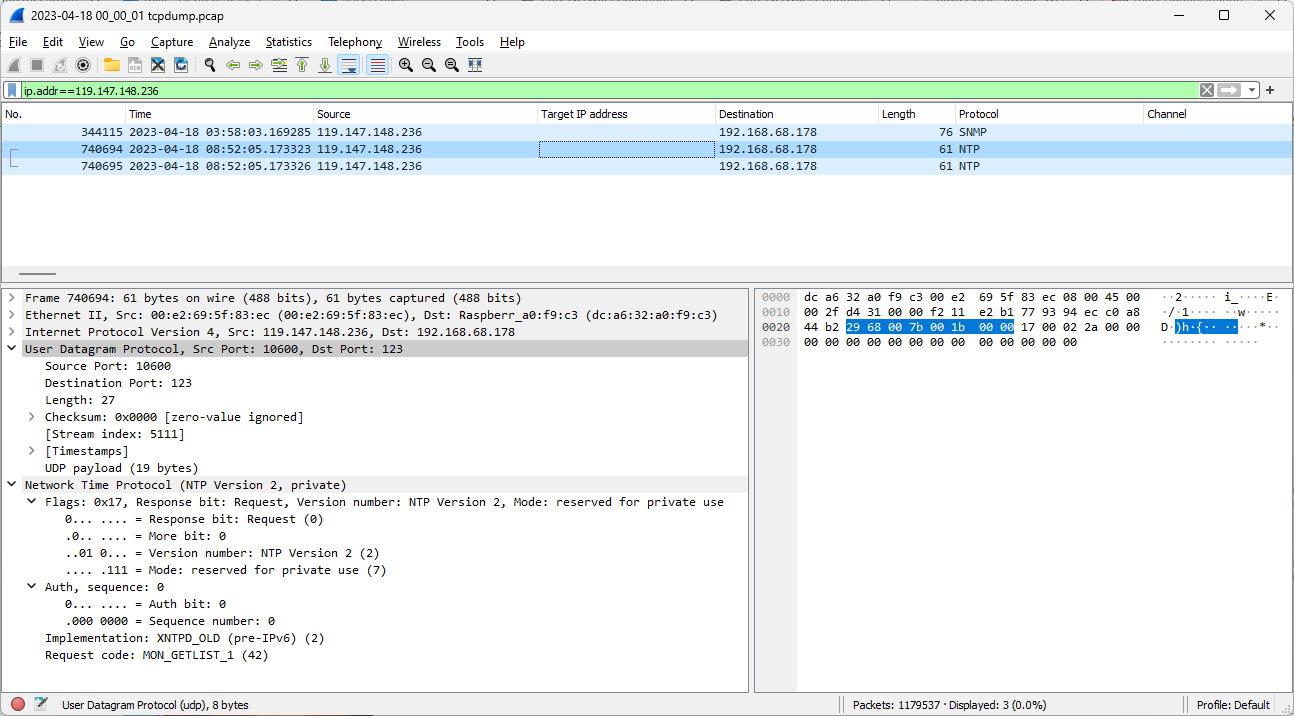
Figure 9: PCAP data that generated Suricata alert
Since we have the full packet capture, we can also compare this with the Suricata rule [8].
alert udp any any -> any 123 (msg:"ET DOS Possible NTP DDoS Inbound Frequent Un-Authed MON_LIST Requests IMPL 0x02"; content:"|00 02 2A|"; offset:1; depth:3; byte_test:1,!&,128,0; byte_test:1,&,4,0; byte_test:1,&,2,0; byte_test:1,&,1,0; threshold: type both,track by_dst,count 2,seconds 60; reference:url,www.symantec.com/connect/blogs/hackers-spend-christmas-break-launching-large-scale-ntp-reflection-attacks; classtype:attempted-dos; sid:2017918; rev:2;)
The rule appears to be from late 2017, but for whatever reason this information wasn't logged by the Palo Alto. There could be several reasons for this, like any tool:
- Palo Alto did not have this traffic content identified as an alert on the day/time of the event
- This may have not been deemed suspicious traffic by Palo Alto
- Information was not logged properly
- Resource contraints caused problems processing or storing the data
- The Suricata rule may not be accurate
An IDS can help identify traffic of interest, but must be tailored to the environment. In addition, different tools have different results. Testing your tools by replicating traffic of interest can help identify whether they work as desired. This is also an interesting comparison between different tools, of which Suricata has more community supplied content. Community supplied rules may not always be accurate, although that does not mean this was the case in the last NTP example.
[1] https://suricata.io/
[2] https://corelight.com/
[3] https://www.paloaltonetworks.com/
[4] https://rules.emergingthreats.net/open/suricata-5.0/
[5] https://www.dshield.org/block.txt
[6] https://cinsarmy.com/active-threat-intelligence/
[7] https://isc.sans.edu/diary/Network+Data+Collector+Placement+Makes+a+Difference/29664
[8] https://github.com/seanlinmt/suricata/blob/master/files/rules/emerging-dos.rules
--
Jesse La Grew
Handler


Comments