Analyzing a YouTube Sponsorship Phishing Mail and Malware Targeting Content Creators
One of our Stormcast listeners, Kevin, wrote in to share that his friend Jon had received a direct spear-phishing e-mail. We requested for more information, and Jon kindly provided us with the corresponding e-mails and data to analyze. The spear-phishing e-mail sent to Jon masqueraded as an individual representing NordVPN (note: NordVPN had published an advisory about scammers posing as NordVPN representatives earlier this year [1]) and enquired about the possibility of a YouTube sponsorship/collaboration with his YouTube channel. I took the liberty to examine the phishing e-mail and its associated artifacts, noting the details I observed from my analysis.
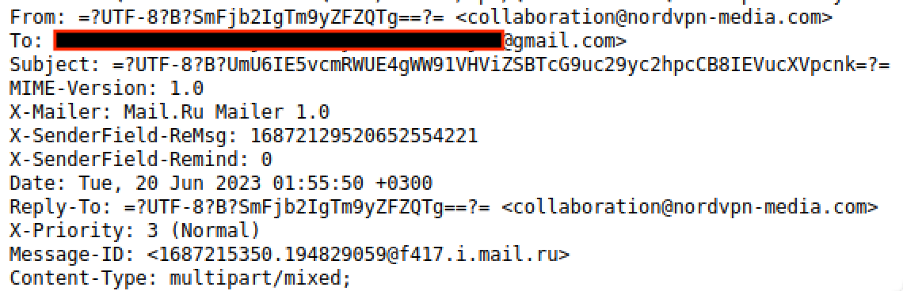
I first examined the e-mail headers, noting the observation of the mail.ru header in the X-Mailer field. (with reference to Figure 1). The e-mail address that the adversary used was collaboration@nordvpn-media[.]com, which had a very close domain name to the original domain name (nordvpnmedia[.]com) that NordVPN had stated to be genuine [1].
I went through the content of the e-mail, and it revolved around discussing the purported sponsorship details. However, another small titbit caught my eye (with reference to Figure 2).
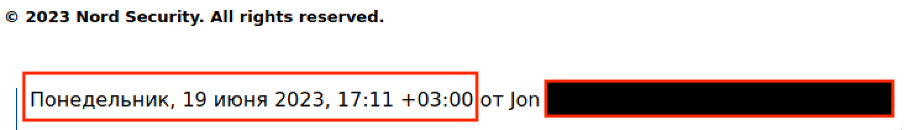
I noticed the presence of Russian characters within the e-mail thread. The Russian characters (highlighted within the red box) translate to “Monday, 19 June 2023”, and an UTC offset of +3 was observed. A quick search for the time zones used in Russia indicates that UTC +3 is currently being used for Moscow.
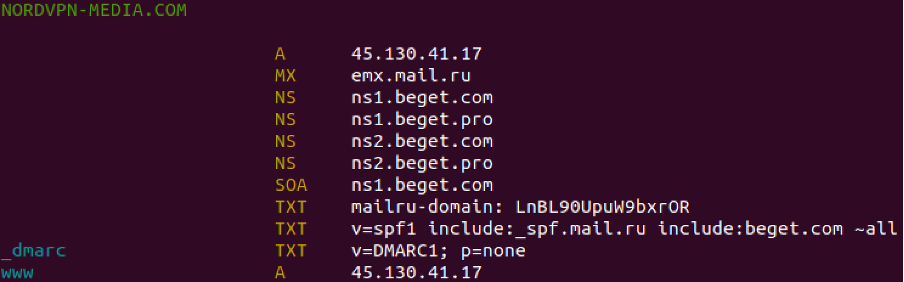
I turned my attention to the domain nordvpn-media[.]com and wondered who had registered the domain. After checking the Whois records, it appeared that the site was hosted in Russia and registered since March 5th, 2023 (Figure 3). However, the hosting provider seemed to have blocked the page. Unfortunately, a little journey to the Wayback Machine did not yield any decent results either.
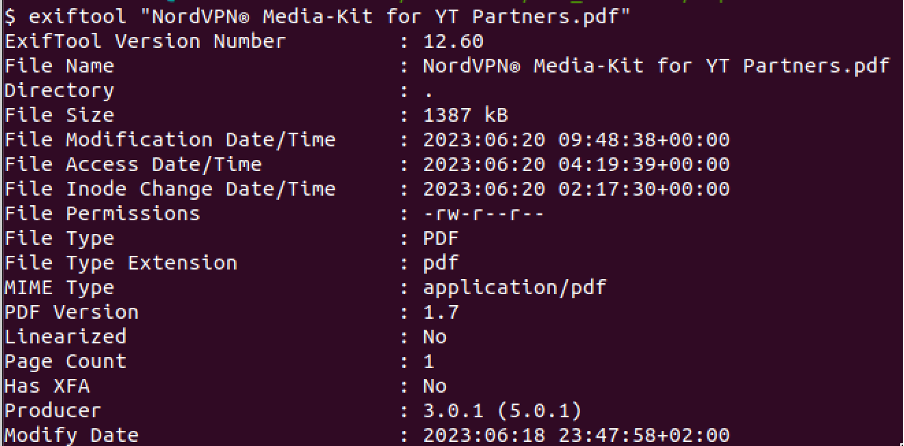
There was a pdf file titled “NordVPN® Media-Kit for YT Partners.pdf”. I wondered if there were any malicious files embedded within it and proceeded to perform some PDF file analysis. I first used exiftool to gather some basic metadata of the attached PDF file (Figure 4). It was interesting to observe that though Figure 2 had a UTC offset of +3, Figure 4 showed that the modification date of the file had a UTC offset of +2.
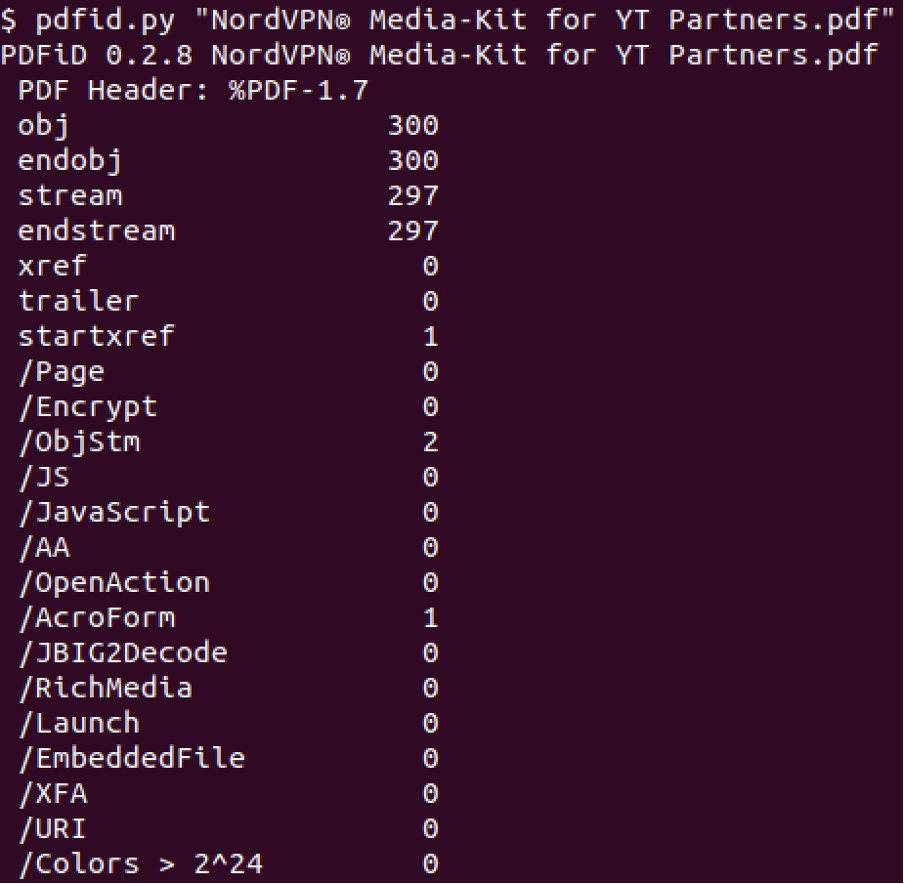
Our SANS ISC Handler, Didier Stevens, has published many excellent tools [2]. I took the opportunity to use one of the tools he created, pdfid.py, to investigate if the PDF file was malicious. With reference to Figure 5, the file appeared to be harmless.
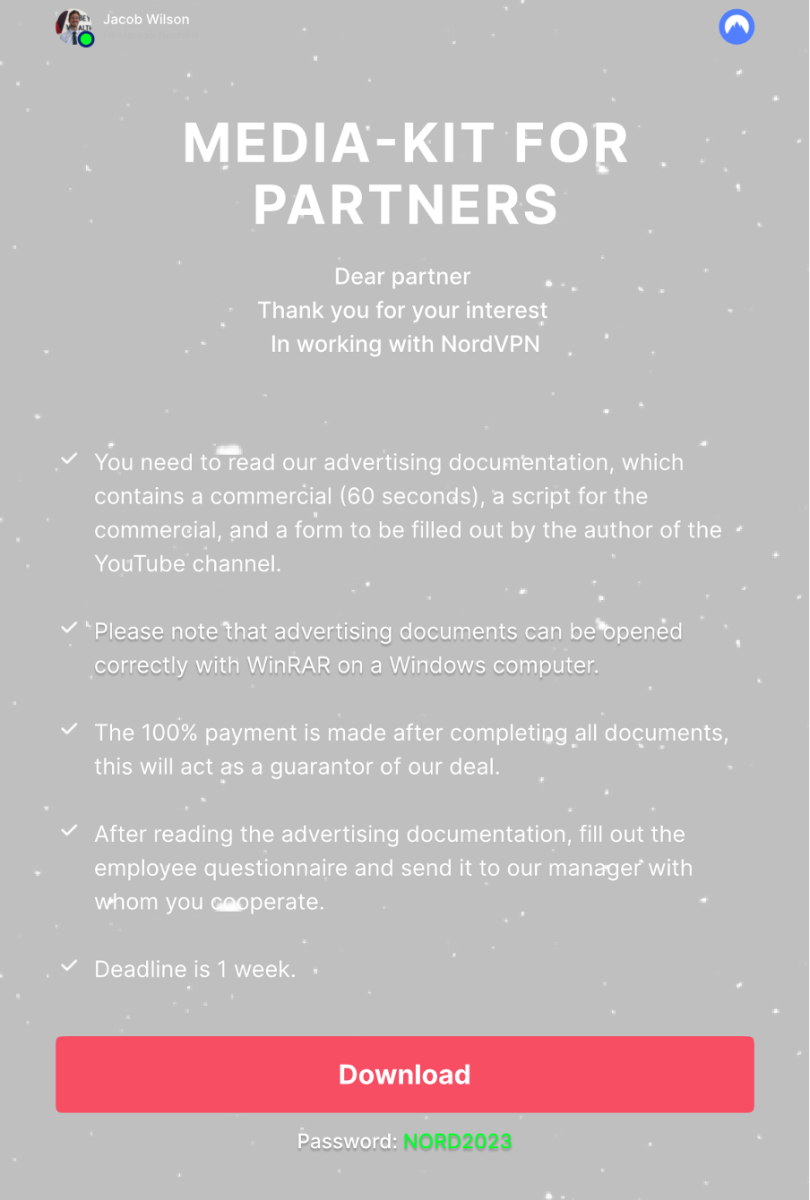
I proceeded to investigate the attached PDF file, and Figure 6 shows the content of the rendered PDF file. I briefly investigated the name used in the top left of the PDF file. While the name was associated with a few reviews of NordVPN submitted online, the picture that was used was lifted off the first Google result of the utilized name. There was also a Download button within the PDF file and hyperlinked to a Dropbox link (hxxps://www[.]dropbox[.]com/s/4b9cqh7oxlq4g0t/NordVPN®%20Promotional%20Materials%20June%202023[.]rar?dl=1).
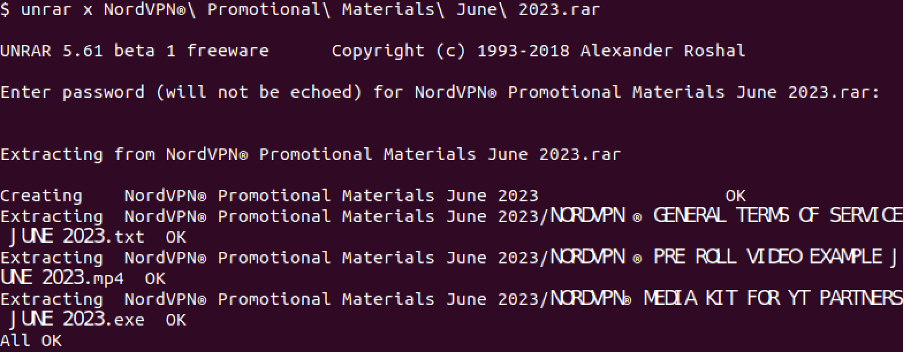
Clicking on the link would immediately trigger a download of the compressed RAR archive. Unpacking the RAR file (with the password shown in the PDF) would yield 3 files, as shown in Figure 7.
Of the 3 files, only the .exe file appeared suspicious. The other 2 files (.txt and .mp4) had previously been uploaded to VirusTotal. I performed brief static and dynamic analysis of the .exe file, and obtained a few interesting observations. For example, I found a reference to a .pdb file named plan4cvartal2otchet.pdb (possibly Russian, given the earlier observations). The executable also had an imphash of f34d5f2d4577ed6d9ceec516c1f5a744, and I found at least one other similar piece of malware that was uploaded on June 10, 2023 (albeit with a different hash) [3]. The following information was also extracted:
{
"c2": [
"176.113.115.23:27556"
],
"attr": {
"auth_value": "9d33ed88bc78fe9fbb90806afbd547df"
},
"rule": "RedLine",
"botnet": "kek18",
"family": "redline"
}
A quick literature review online yielded several references to the RedLine Stealer, which was often transacted in underground forums [4]. This malware is capable of exfiltrating a variety of data such as saved passwords, credit card data, computer and username configuration, and even stealing cryptocurrency. [4] Although this incident may be isolated, it demonstrates the possibility of a potential campaign towards unsuspecting content creators who genuinely want to have fruitful collaborations with global brands on popular platforms such YouTube, Instagram and TikTok. With the ability to purchase malware as a subscription or as a standalone product via underground means [4], the complexity of pulling off similar cyber heists has been greatly reduced for current and budding cybercriminal groups. Constant vigilance when receiving unsolicited e-mail is vital, no matter how tempting a collaboration offer appears to be.
Indicators of Compromise (IoCs):
45.130.41.17
nordvpn-media[.]com
collaboration@nordvpn-media[.]com
hxxps://www[.]dropbox[.]com/s/4b9cqh7oxlq4g0t/NordVPN®%20Promotional%20Materials%20June%202023[.]rar?dl=1
a6f54e972c40ac38a958c3ee10343e49992ad1d6 (SHA1 hash of NordVPN® Media-Kit for YT Partners.pdf)
612cf3ed13976c7b20d4ae1a7832105ac1982a6e (SHA1 Hash of NordVPN® Promotional Materials June 2023.rar)
c8c73d8a25872d0c5300cea264f92abe3993feee (NORDVPN® MEDIA KIT FOR YT PARTNERS JUNE 2023.exe)
176.113.115.23 (C2)
References:
1. https://nordvpn.com/blog/nordvpn-creators-scam/
2. https://blog.didierstevens.com/my-software/
3. https://www.virustotal.com/gui/file/12ab0f4389fb376011431b9ffc35cd90447edc980b75574b6b376ef0fd50fd59/details
4. https://malpedia.caad.fkie.fraunhofer.de/details/win.redline_stealer
-----------
Yee Ching Tok, Ph.D., ISC Handler
Personal Site
Mastodon
Twitter


Comments