Quick Answers in Incident Response: RECmd.exe
[This is a guest post written by Logan Flook, one of our SANS.edu undergraduate interns https://www.linkedin.com/in/loganflook]
It is imperative to answer many different questions quickly and accurately during security incidents. Incident Responders need to identify critical pieces of information that could significantly impact understanding the security incident and handling it accordingly. To do this, Incident Response personnel need capable tools to gather this information. Filling this necessity, amongst others, are the massively popular Eric Zimmerman tools publicly available on his website [1]
Within this set of tools lies RECmd.exe, also known as the command-line equivalent to Registry Explorer – Eric Zimmerman's pioneer Windows Registry analysis tool. RECmd.exe allows an incident responder to conduct automated, scripted analysis of a Windows Registry hive and output findings into a CSV formatted file. This is done by providing RECmd.exe a custom batch file, a directory path to a registry hive (or directory of hives), and a directory path to where the user wants results to be stored.
PS C:\Tools\RECmd> .\RECmd.exe --bn BatchExample.reb -f C:\Users\User\NTUUSER.DAT --csv C:\Output.csv
Here we see the command structure as:
RECmd.Exe --bn <Batch File> -f <Path to Registry Hive> --csv <Path for output>
With input such as this RECmd.exe will run searches for registry keys found in the batch file against the specified registry hive and output the results to a specified directory as a .csv file.
RECmd.exe comes with over a dozen pre-written batch files already created by Eric Zimmerman and the team at Kroll Security. However, users can write their custom scripts as well. This is what sparked my interest in writing a RECmd.exe batch file. I've written a 'User Activity' file to look for a wide array of registry keys that indicate user activity. These include UserAssist, Typed Paths, Recent Files, BAM, DAM, and others. Below is a screenshot of the first 30-odd lines:
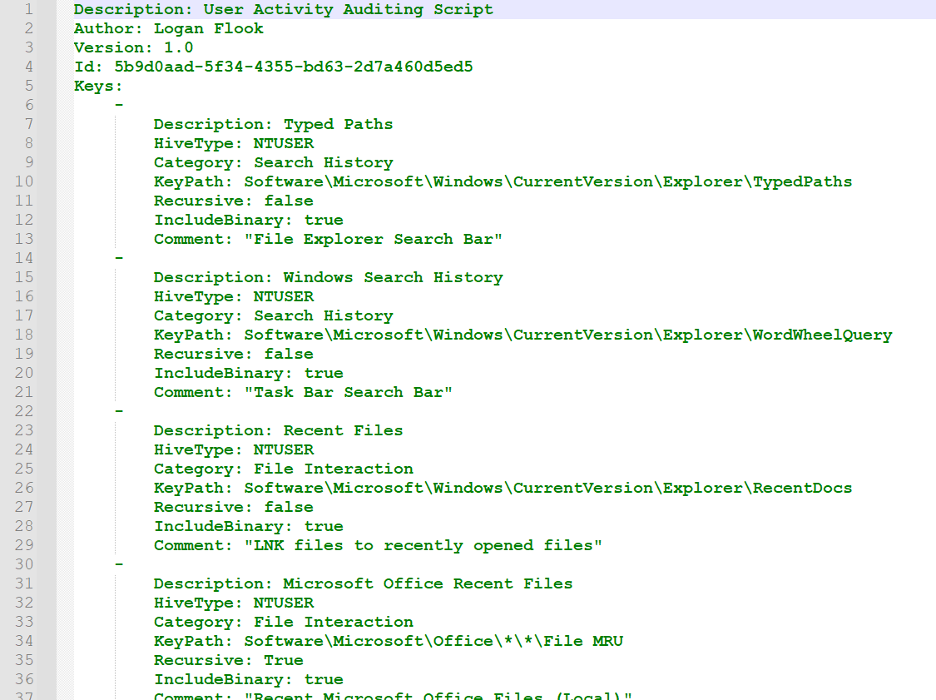 Figure 1: User Activity Auditing Script Output
Figure 1: User Activity Auditing Script Output
As you can see, RECmd.exe batch files are relatively simple to write. All you need to provide is the hivetype and keypath variables. Everything else is optional parameters to instruct RECmd.exe to include the binary values of keys, look recursively at all subkeys, or add informational tags like descriptions or comments.
The goal of the above script, when run against a NTUSER.DAT hive, is to quickly gain answers to questions such as:
- What files did the user interact with recently?
- What direct paths has the user navigated to in file explorer?
- What has the user searched for in the Windows Taskbar?
- Where has the user recently saved files to?
- What commands has the user ran through the 'Run' utility (Windows Key + R)?
- What shortcut links has the user interacted with?
Running RECmd.exe is incredibly fast, as this example shows RECmd.exe was able to parse one NTUSER.DAT file and retrieve 81 pairs in 0.642 seconds.
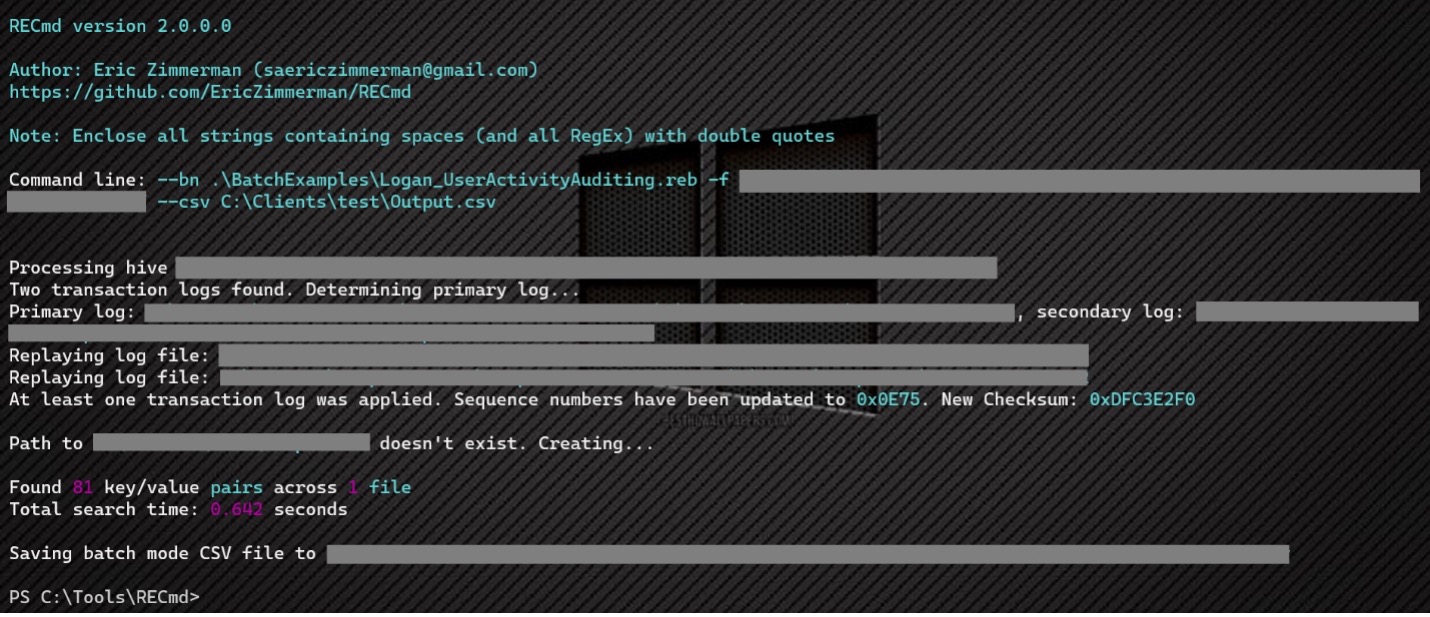 Figure 2: RECmd runtime output
Figure 2: RECmd runtime output
The way an Incident Responder can answer these questions is by partnering the RECmd.exe output with another Eric Zimmerman tool: Timeline Explorer. This tool is built for incident responders to parse CSV formatted files.
When opening the RECmd.exe output Timeline Explorer will look like this:
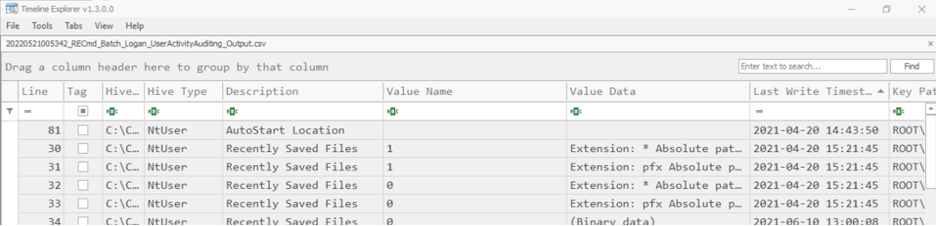 Figure 3: RECmd.exe output in Timeline Explorer
Figure 3: RECmd.exe output in Timeline Explorer
From here, incident responders can analyze the information in the columns to review data. However, where Timeline Explorer truly shines is in its ability to group by columns. This is done by dragging a column header to the space between the CSV name and the columns. Once this is done Timeline Explorer will adjust the view to groups by the values in the dragged column. Let's see how this looks by grouping by the 'Description.'
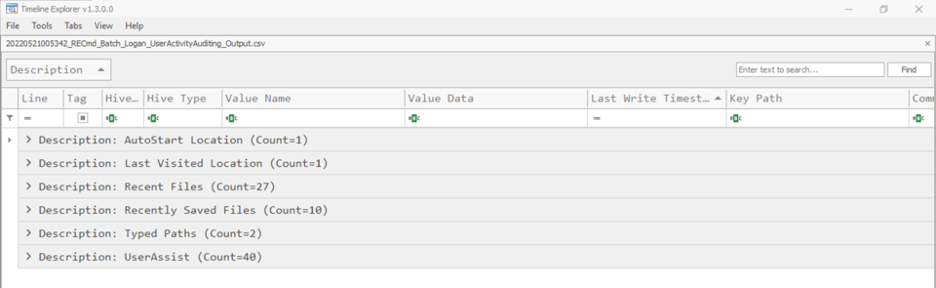 Figure 4: RECmd Output Grouped by Description
Figure 4: RECmd Output Grouped by Description
Timeline Explorer now shows six rows, each with a different Description as its title – remember this Description coincides with the description tag that was provided for each registry key in the original RECmd.exe batch file. Let's expand the 'Typed Paths' row and analyze the data here. We see that the user of this NTUSER.DAT file typed in two direct paths into file explorer, as well as the last write timestamp to that registry key.
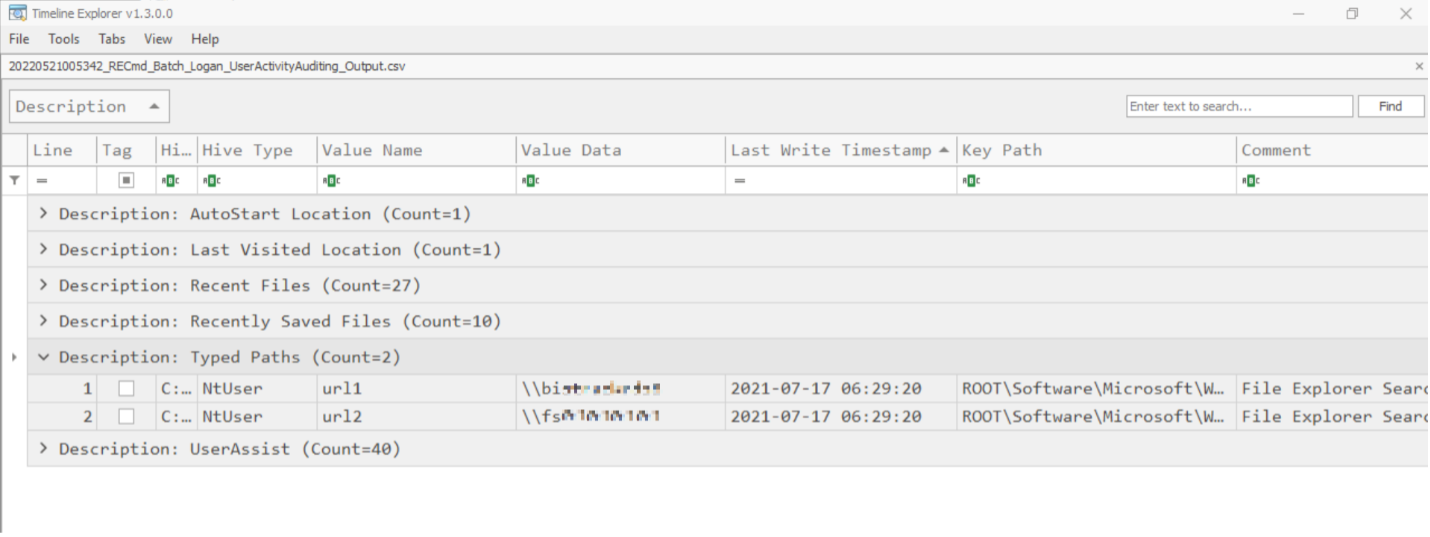 Figure 5: Last write timestamp to registry key example.
Figure 5: Last write timestamp to registry key example.
More pertinent information for a security incident can be found in the other columns quickly and effectively.
Combining RECmd.exe's incredibly lightweight and fast analysis with Timeline Explorer's simple grouping view, Incident Responders can gain critical information at an impressive and game-changing pace.
[1] https://ericzimmerman.github.io/#!index.md
Logan Flook
Incident Response Specialist
SANS.edu Undergraduate Intern
https://www.linkedin.com/in/loganflook
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments