What is BIMI and how is it supposed to help with Phishing.
Earlier this week, I talked about how Phishing is still a huge problem and how compromised WordPress installs and free file hosting services are abused. But the root cause why Phishing works is more "human": Phishing works because it is hard to figure out if an email or a website is authentic. Over the years, many technical solutions have been implemented to make it easier to recognize valid senders or a valid website. TLS helps, but not if the attacker comes up with a decent look-alike domain or can obscure the hostname with lengthy prefixes. DKIM and SPF help, but they again do nothing against look-alike domains.
The latest attempt to find a better way to authenticate an email sender visually is "BIMI," short for "Brand Indicators for Message Identification" [1]. It will add a company logo to each email, and the logo may be verified.
Of course, to make this work, we need yet another DNS TXT record: [selector]._bimi.[domain]. The [selector] can decide which logo will be used. But typically, you should see default._bimi.example.com.
e.g., for dshield.org:
v=BIMI1;l=https://dshield.org/images/dshieldbimi.svg;
The image must be in SVG format.
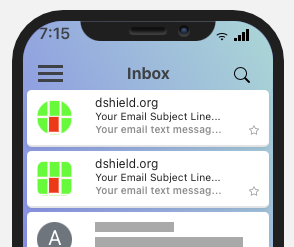
Preview generated by bimigroup.org
So what prevents a phishing site from copying your BIMI logo, just like it reproduces all your other artwork? Certificates! You may use BIMI without certificates (like I do for DShield.org), but the value is limited, and not all email clients may show it (more about that later). But you can use an optional "Verified Mark Certificate" (VMC) to improve BIMI.
So what is a VMC, and how do you get one? In short, the VMC verifies that you own a trademark for a particular logo. Start by obtaining a trademark. Future versions of the standard may no longer require this step, but that will get you started for now. Next, you have to get your certificate. There are no free options so far. I have seen them offered for around $1,000-$1,500 per year. So it is in no way cheap. There may be a manual process in approving the request, which is likely why they are so expensive. Also, the lack of a free option may contribute to the cost. Most organizations will already have a trademarked logo, but if not, that will add another $500 or so.
So far, Yahoo, Google, Fastmail, and Pobox are supporting BIMI. Others are considering it. But note that neither Apple nor Microsoft has announced any plans so far (according to [1]). With Outlook/Office 365 and iOS/macOS out, it is hard to justify the cost of a "complete" BIMI implementation (it is not just the cost of the certificate, but it is also something else that could break with email, another certificate to maintain, and a logo that needs to be created in the right format).
Pros and Cons? Should you do it?
+ it does offer another visual indicator that an email is authentic
- it is expensive to do it "right"
- support is limited
[1] https://bimigroup.org
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
All Gmail shows me is "B" for the bounces email address.
Anonymous
Apr 7th 2022
3 years ago
Anonymous
Apr 8th 2022
3 years ago
tldr: your need a graphic artist with non free software
Anonymous
Apr 8th 2022
3 years ago
I'm reading from the perspective of an organizations email gateway.
What I understood is, it's a client side verification, not supported by the major brands in business world and just an option for some hosted mail accounts. The "Key value propositions" seem to be out of scope for business partners in this scenario.
One more visiual indicator on the client is not the solution for organizations, it should be verified on a gateway, not reaching the real "target", if identified as fake.
I got, the only protection for BIMI is an expensive certificate, but it works also without one. ==> no hurdle for a fake domain?
Regards,
Ron
Anonymous
Apr 8th 2022
3 years ago
Just like SSL certificates did.
We have DMARC, DKIM, SPF on all our domains, including the 500+ not used (typosquatting etc), yet the domains are still used by stupid scammers. My personal domain with everything enabled is used by scammers. So it does not work.
And remember, there was a time before all this, where marketing just told customers to whitelist sender address to ensure they got the spam. Microsoft in one of the the DMARC non-compliant orgs. If the recipient has whitelistet a sender, then all DMARC checks are skipped, and the scammer will get mails delivered in the inbox - with all checks failing.
It used to be that google was the defacto standard, and they follow the RFCs. But now in their latest push to get rid of power users / IT people (closing google for my domain) everything will get more muddy again.
Anonymous
Apr 11th 2022
3 years ago
I got, the only protection for BIMI is an expensive certificate, but it works also without one. ==> no hurdle for a fake domain?
[/quote]
Some mail providers only shows the expensive signed logo. Other, like Google shows anything. So not really worth it at this time.
Anonymous
Apr 11th 2022
3 years ago
Sam
May 8th 2023
2 years ago