Introduction to EvtxEcmd (Evtx Explorer)
This is a guest diary by Ahmed Elshaer.
In this diary, I wanted to talk about Event Explorer EvtxEcmd by SANS Instructor Eric Zimmerman. EvtxEcmd is a Windows Event Log (evtx) parser, that can parse a single event log file or a directory recursively. EvtxEcmd has some great features like:
- Custom Maps to parse different Windows Event IDs
- Ability parse log files from Volume shadows
- Can be used by KAPE!!
Introduction
As we know Starting from Windows VISTA Windows event logs are in C:\windows\system32\winevt\logs\. And they are in Binary XML Format which is a lot easier to work with, performant and enabled Windows to have a lot of more specific Event Log Files.
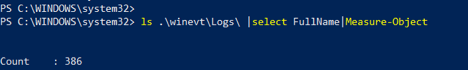
Example of what I have on my system out of 386 different log files.
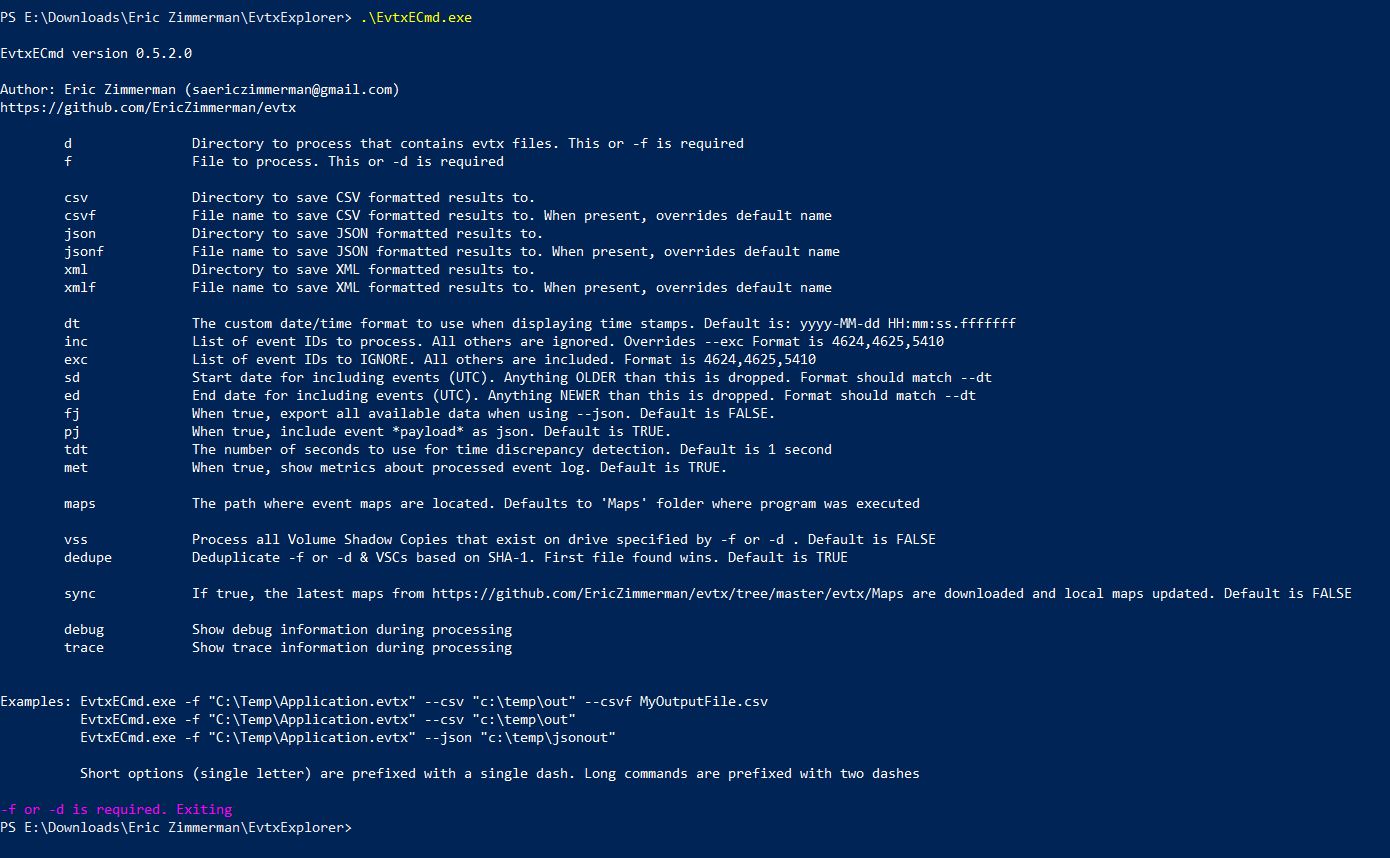
By looking at the different options offered by the tool we notice it has sets of options. Input options like file or directory, export options like csv, json or xml, other options like include and exclude set of event IDs. We are going to notice very important options like maps which are custom parsing maps for different event IDs, and VSS which mount all volume shadow copies and parses the log files from them and deduplicate the events. Let us not forget to "–sync", which gets the latest Maps from Eric’s Repository.
How to Use EvtxEcmd:
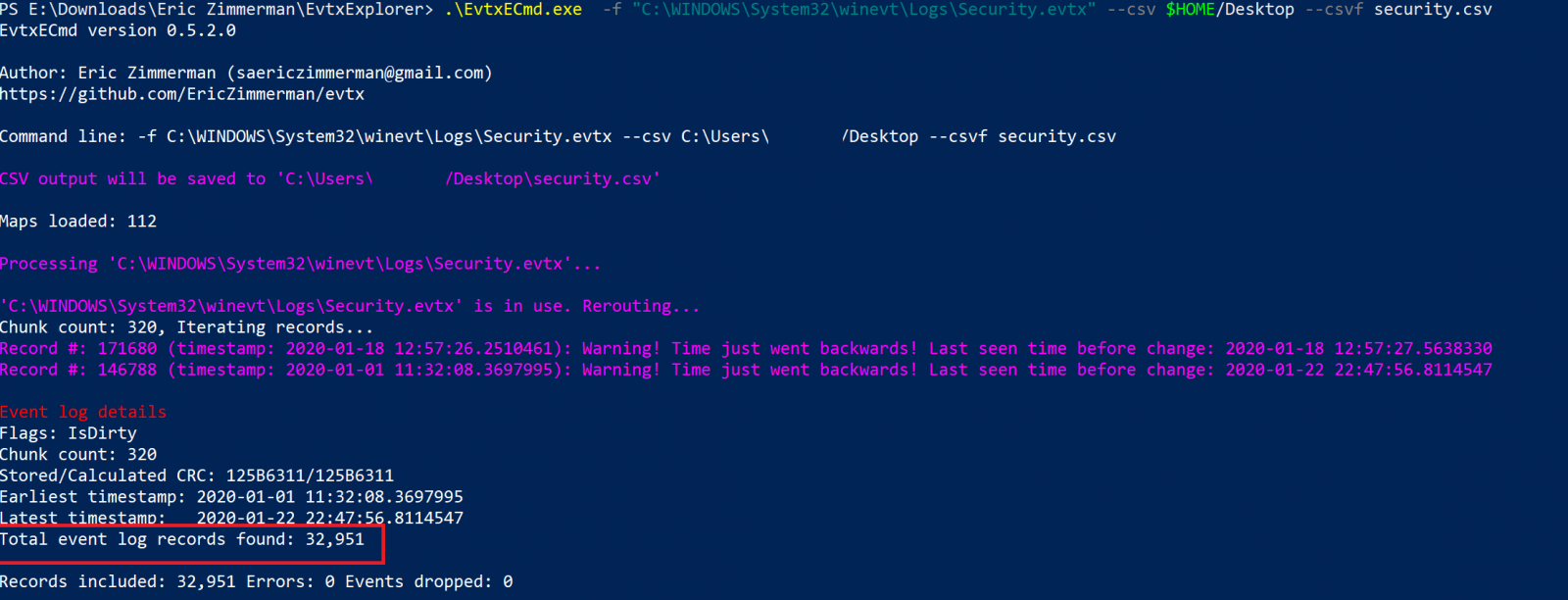
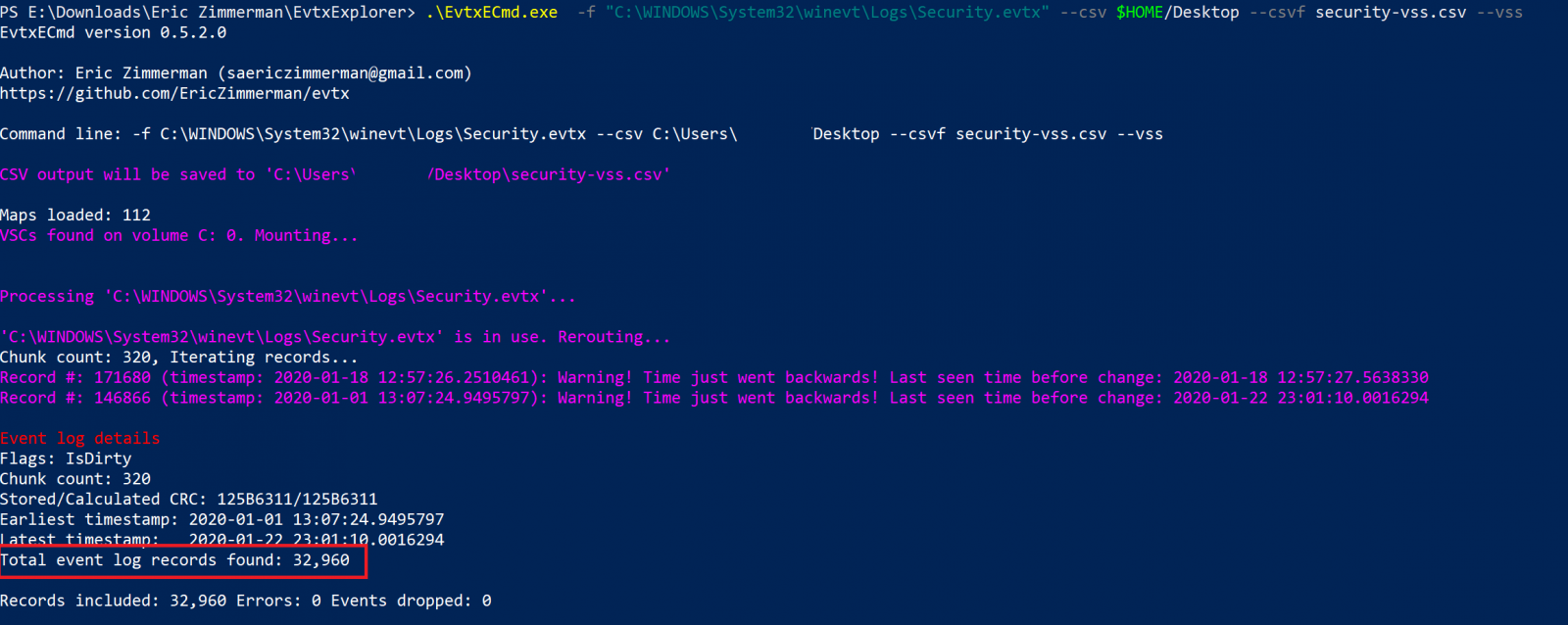
I’m going to showcase a couple of examples for how to use the tool, and can’t emphasize enough how fast it can process the event logs. Here you can see I’m parsing the Security Log File; it took 12 seconds to process 32951 Events. Exported the logs to a csv file which can be viewed by another great tool from Eric’s Arsenal “Timeline Explorer”.
It’s important to note here, that all events are normalized across all event types and event log file types. Maps are actually used to convert the custom data from different events types into standard fields.
Another example, I used here VSS option to mount all Volume Shadow Copies and process the Security Event Log, by default the tool will deduplicate the events.
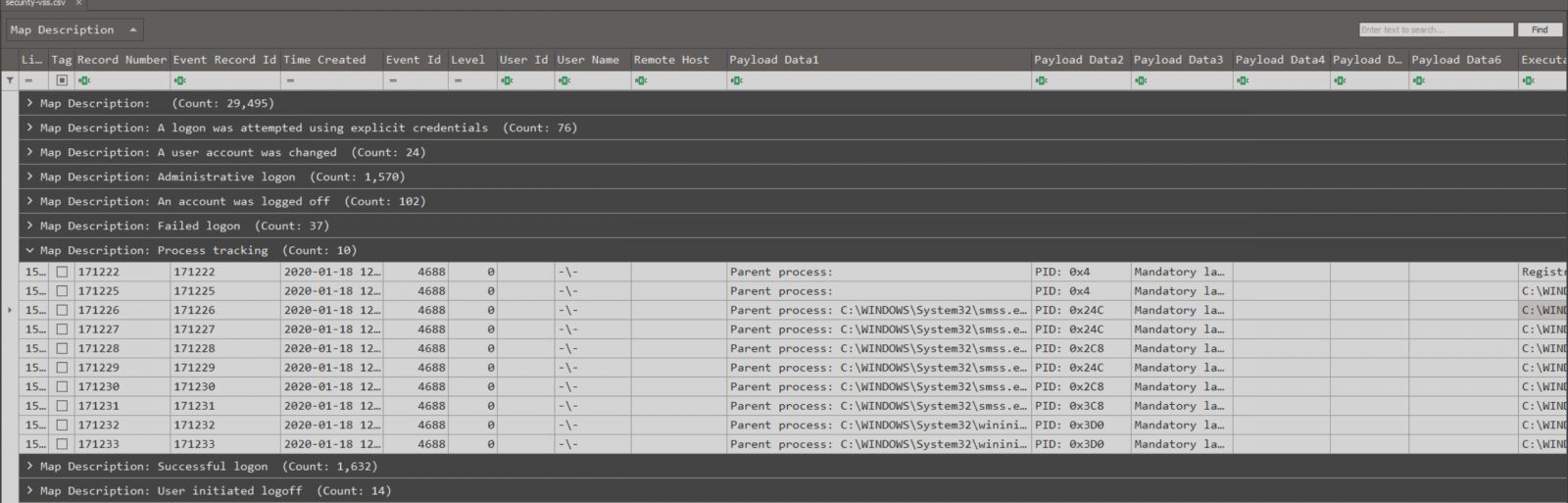
We can then open any of these exported files with TimeLine Explorer. Here I’m using grouping which makes the investigation a lot easier.
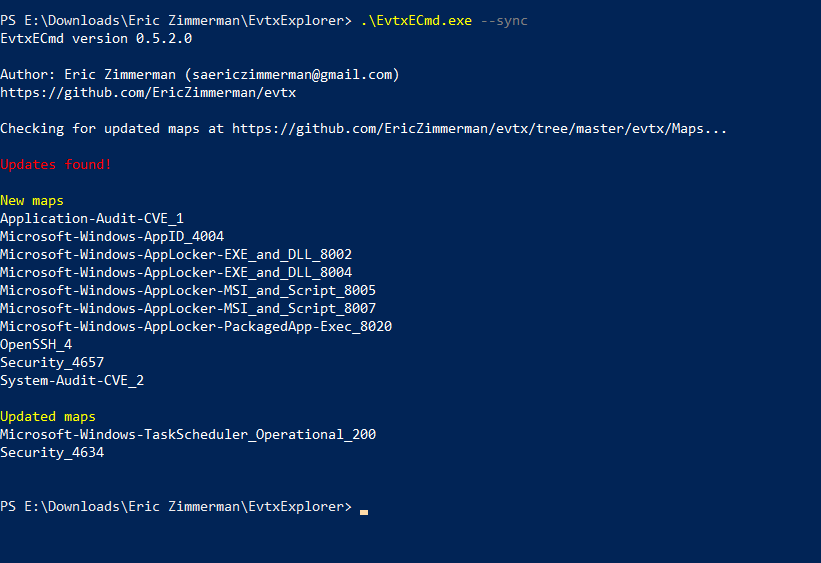
New Maps:
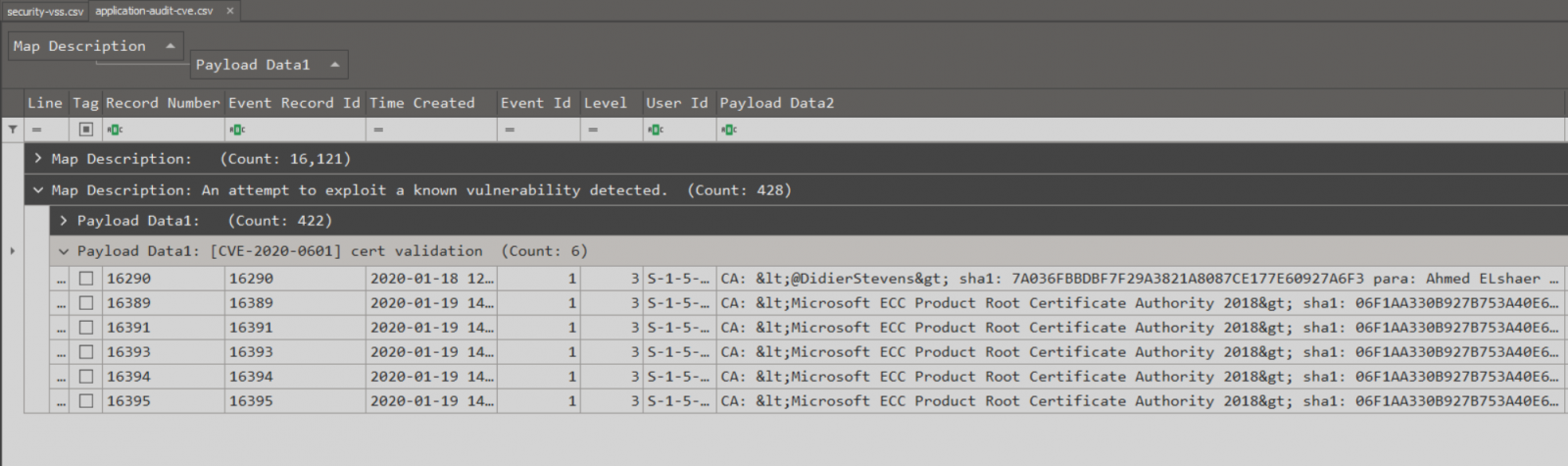
As we all know about the CurveBall Vulnerability which was addressed in CVE-2020-0601, a patched Windows system will write a log in the Application Event Log with Event ID 1 Audit-CVE when a manipulated certificate attempt to be validated. I made a try to update the tool with the latest Maps, and surprisingly I found Eric providing new maps for Audit CVE Events.
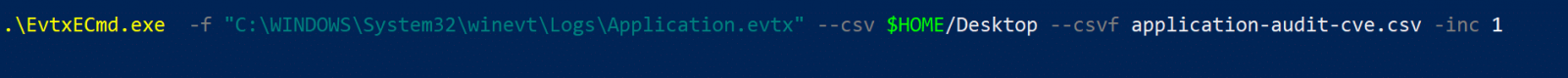
Launching the tool against Application Event Log, and only targeting Event ID 1. This would get us all application logs with event ID 1, but the map Eric provided was specifically to Audit-CVE.
To get a better view in TimeLine Explorer I had to group with Map Description then Group with Payload to only focus on “Cert Validation” Events. Note: below I was testing with Didier Stevens’s “Using CveEventWrite from VBA”, and curveballtest.com.
Extending Maps:
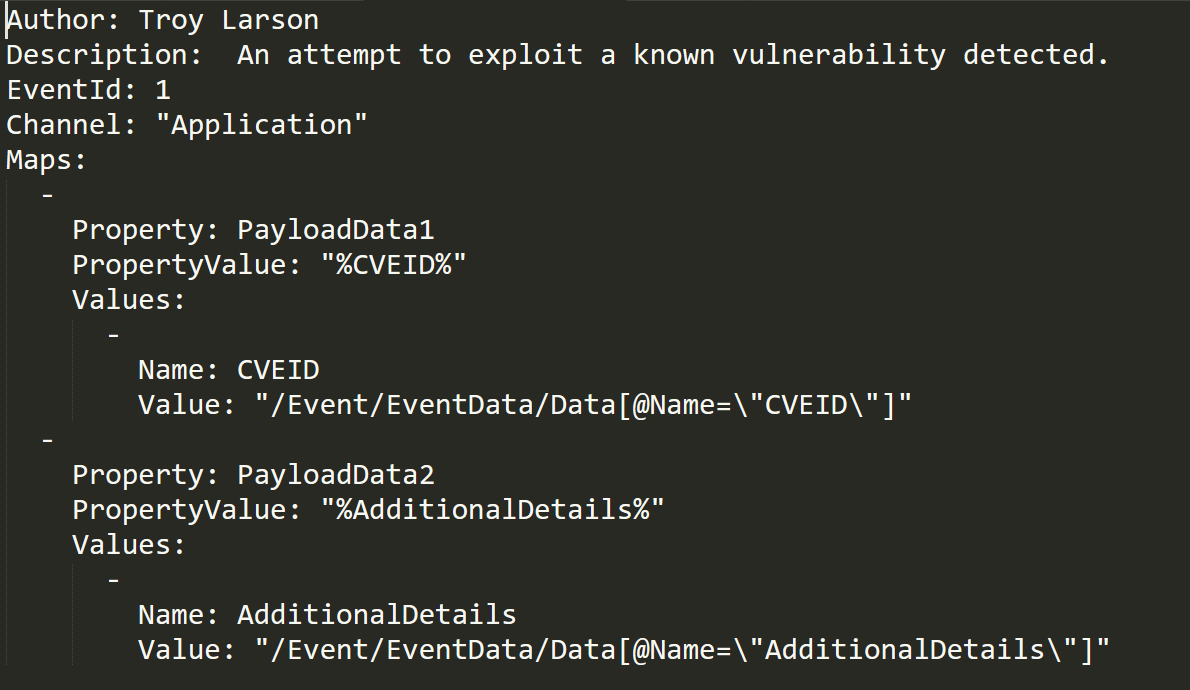
EvtxEcmd is very extendable and I really recommend taking a lot at different maps and start adding and contributing to the existing maps by finding interesting event IDs and creating a map to parse them. below is the map that parses Application Audit-CVE Event ID 1.
References:
https://ericzimmerman.github.io/#!index.md
https://github.com/EricZimmerman/evtx/tree/master/EvtxECmd
https://binaryforay.blogspot.com/2019/04/introducing-evtxecmd.html
https://blog.didierstevens.com/2020/01/15/using-cveeventwrite-from-vba-cve-2020-0601/
https://isc.sans.edu/forums/diary/Summing+up+CVE20200601+or+the+Lets+Decrypt+vulnerability/25720/
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments