Blue + Red: An Infosec Purple Pyramid
Introduction
Pyramids provide a good image of tiered activity. In 2015, I wrote a diary about a Security Operations Center (SOC) analyst pyramid of activity SOC analysts will encounter when monitoring their networks for malicious network traffic.
But in recent months, I've used a pyramid to show tiered responsibilities under a mature information security (infosec) program. Today's diary provides my view of infosec as a tiered purple pyramid.
Blue + red = purple
Conventional wisdom divides infosec into defensive and offensive roles. Defensive roles fall under a blue team responsible for monitoring network assets and responding to incidents. Offensive roles fall under a red team responsible for detecting any weaknesses in our infrastructure. This presents a rather misleading view of red team as attackers and blue team as defenders.
In recent years, the phrase "purple team" has appeared with various meanings. Some sources describe purple team as a combination of blue and red team functions. Other sources define purple as a separate team that coordinates the efforts of blue and red team members.
However, blue and red teams both serve the same objective: protecting our information technology (IT) assets. We can view blue and red team functions within the combined model of a purple infosec pyramid.
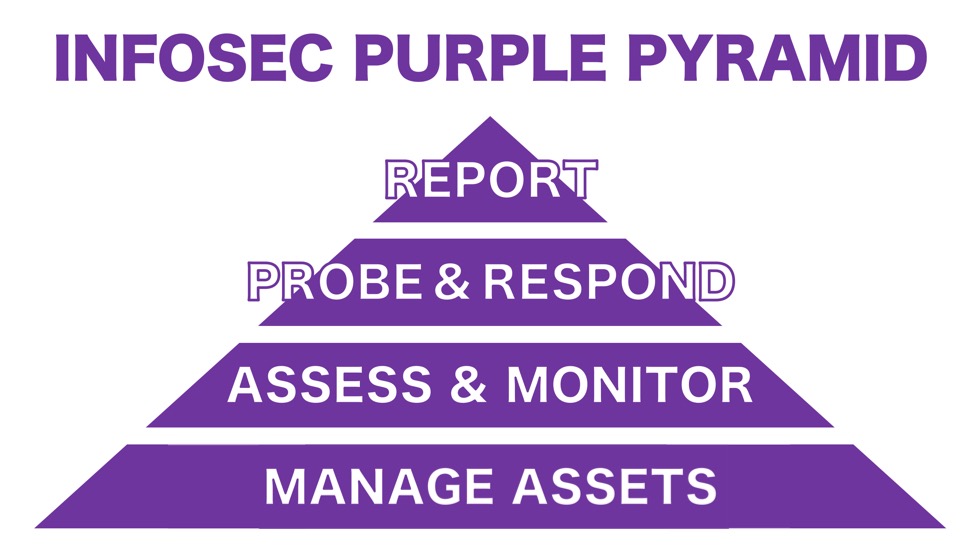
Shown above: An infosec purple pyramid.
Managing Assets
The base of this pyramid covers all tasks for managing your IT assets. These functions include:
- Inventory management
- Access controls
- Software patching and updates
- Hardware refreshes
These basic IT functions are essential to supporting the remaining tiers of an infosec pyramid. Without inventory management, we cannot properly secure our infrastructure, because we don't fully understand everything on our network. Access controls are also critical to ensure only properly-authorized people are utilizing our IT assets. Some of these roles may not be handled by security personnel, but they directly affect the security of our network.
Assess and Monitor
This tier of the pyramid involves both blue and red team functions. Red team members assess network security through vulnerability scans, while blue team members monitor the network for intrusions or other malicious activity. These assessments should be periodic and relatively frequent. Monitoring should be constant, with near-real-time detection and analysis of suspicious activity.
Probe and Respond
When vulnerabilities are discovered through assessments, red team members probe to determine how easy they are to exploit. If blue team monitoring reveals malicious activity, security personnel must respond. This tier consists of activity like penetration tests and incident response procedures.
Report
The top tier of the purple pyramid is based on reporting. Red team members send the results of assessments and penetration tests to managers and other decision makers. Blue team members report on malicious activity and how the issues were resolved. Decision makers use this data to adjust processes and procedures in lower tiers of the pyramid. This should provide a continual cycle of feedback designed to improve an organization's security.
Final words
Blue and red team functions can mislead people into thinking they are opposing roles working against each other. However, these functions are better seen as a combined color with the same objective of protecting our IT assets. When viewed within the tiered model of a purple infosec pyramid, we can better understand how blue and red teams work together to provide an effective defense.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments