Campaign evolution: Hancitor malspam starts pushing Ursnif this week
Introduction
Today's diary reviews noteworthy changes in recent malicious spam (malspam) pushing Hancitor.
Background: Malspam pushing Hancitor (also known as Chanitor or Tordal) is a long-running campaign I frequently document on my malware traffic analysis blog. Infections from this malspam tend to follow predictable patterns and usually end with Zeus Panda Banker as the follow-up malware. However, this campaign occasionally tries new techniques or sends different follow-up malware.
In recent months, a baseline Hancitor infection used Word macros to push Pony malware and Evil Pony to system RAM, and it also pushed Zeus Panda Banker to disk as a persistent follow-up infection.
However, last week we noticed some changes. I documented a wave of Hancitor malspam on Monday 2018-10-22 that only pushed Pony malware and didn't send Zeus Panda Banker. This week, a Hancitor infection on Monday 2018-10-29 sent Ursnif as the follow-up malware.
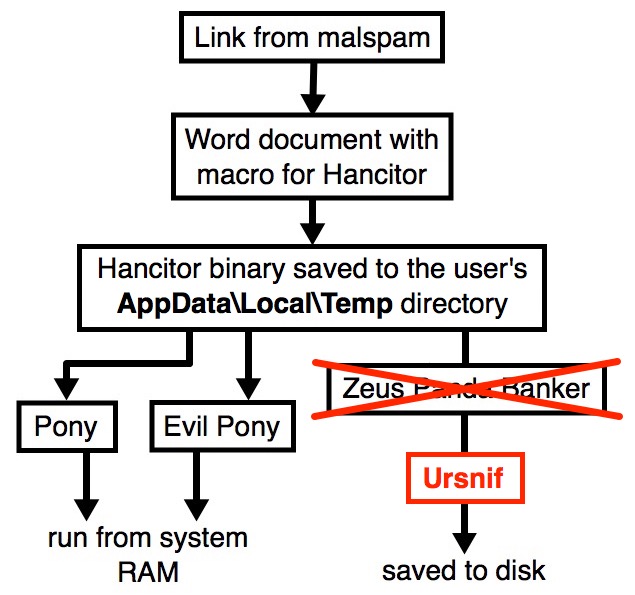
Shown above: Flow chart for a Hancitor malspam infection on Monday 2018-10-29.
The emails
Malspam from this campaign spoofs different online services, and Monday's example spoofed HelloFax. As a deception technique, this campaign also spoofs domains from legitimate businesses. Monday's example spoofed warrencountyga.com. Neither HelloFax nor Warren County GA are actually involved with this malspam. Criminals behind this campaign were simply impersonating names and domains from those two organizations.
Various elements in the email headers change from email to email in this malspam. For example, subject lines, X-Mailer lines, and even names associated with spoofed sending addresses can change each message.
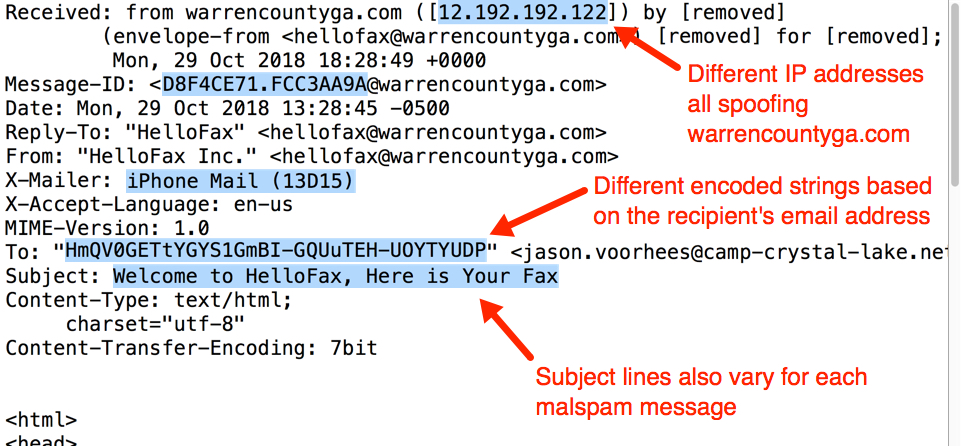
Shown above: Email headers you might find in this malspam.
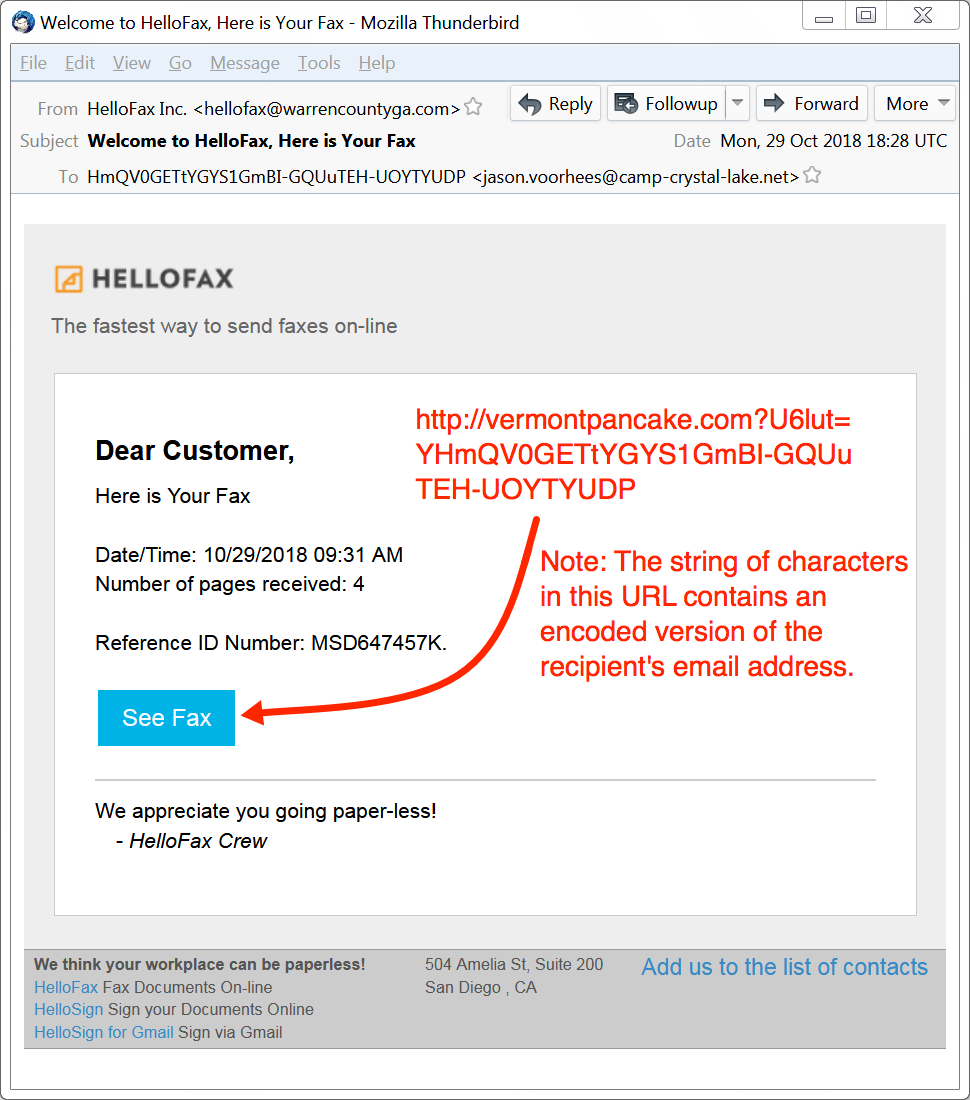
Shown above: Screenshot from one of the emails in Monday's wave of malspam.
The downloaded Word document
Links from these messages are designed to download a malicious Word document. Opening one of these Word documents and enabling macros will infect a vulnerable Windows host.
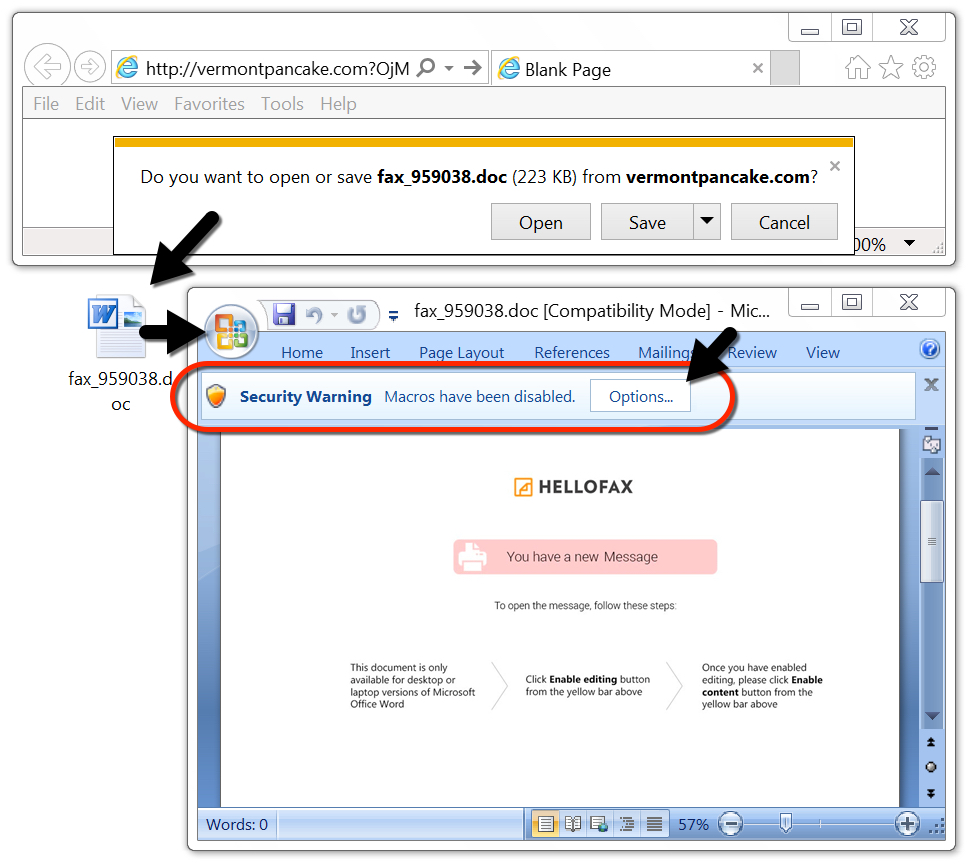
Shown above: Downloading a malicious Word document from one of the emails.
Researchers like @James_inthe_box quickly figured out follow-up malware from these infections was Ursnif instead of Zeus Panda Banker. @Mesa_matt pointed out the Word macro checked for Malwarebytes on an infected Windows host.

Shown above: Tweet from @James_inthe_box about the follow-up malware.
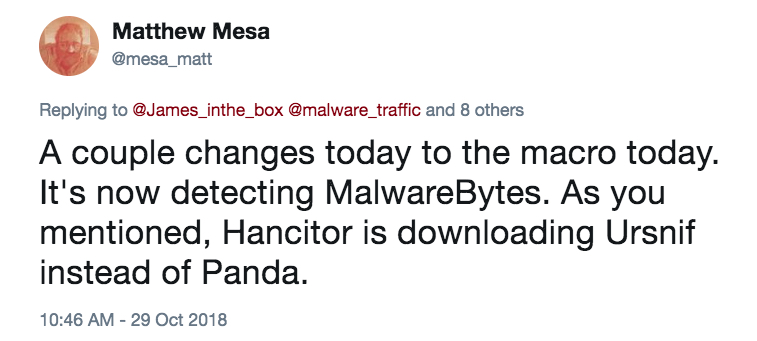
Shown above: Tweet from @Mesa_matt about Hancitor checking for Malwarebytes.
This got me curious, so I used Officemalscanner to extract macros from the downloaded Word doc. Reviewing the macros showed code that checked for the following antivirus solutions:
- PSUAMain - Panda Cloud Antivirus
- n360 - Norton 360
- PccNT - Trend Micro PC-cillin
- uiSeAgnt - Trend Micro Worry-Free Business Security
- mbam - Malwarebytes
- mbamtray - Malwarebytes
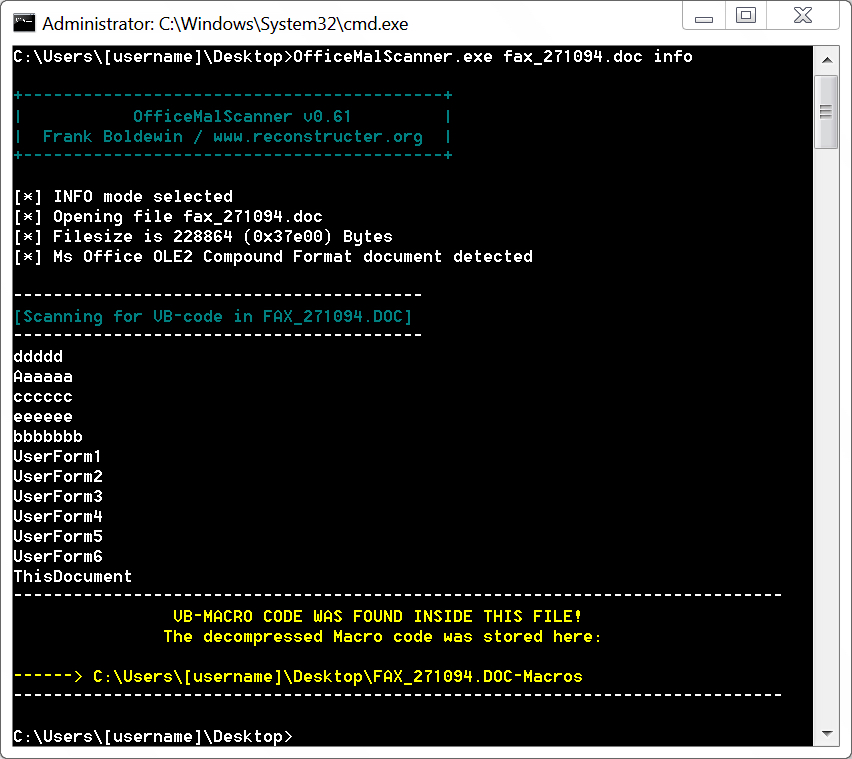
Shown above: Using Officemalscanner to extract macros from the malicious Word doc.
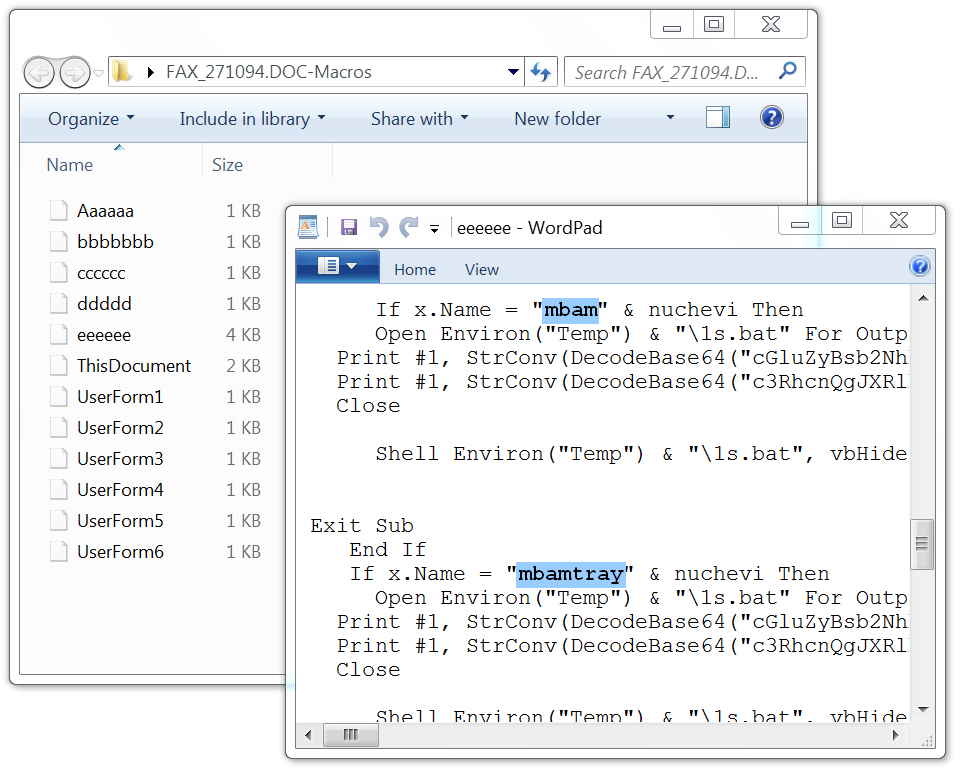
Shown above: Finding the macro code that checks for Malwarebytes.
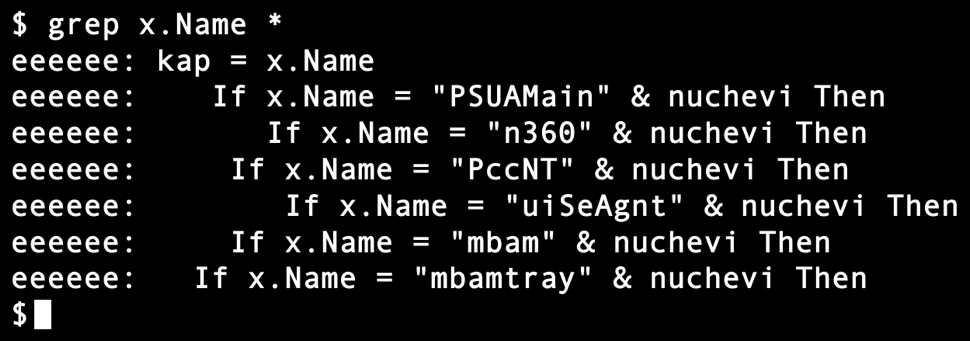
Shown above: Searching the extracted macro to see if it checks for other antivirus solutions.
Infection traffic
Infection traffic was similar to previous Hancitor infections I've recently generated in my lab, except there was no Zeus Panda Banker infection traffic. Instead, I saw post-infection traffic for Ursnif.
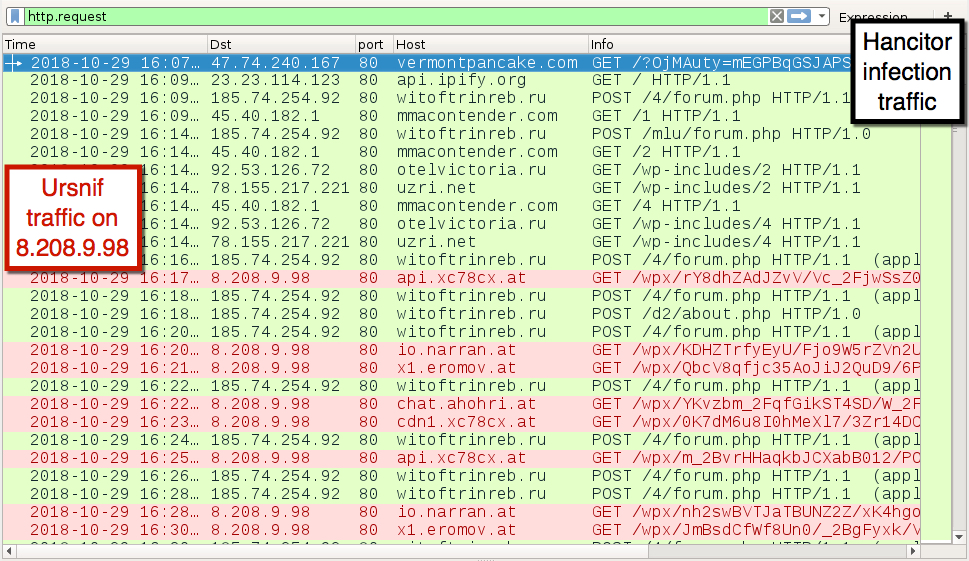
Shown above: Traffic from the infection filtered in Wireshark.
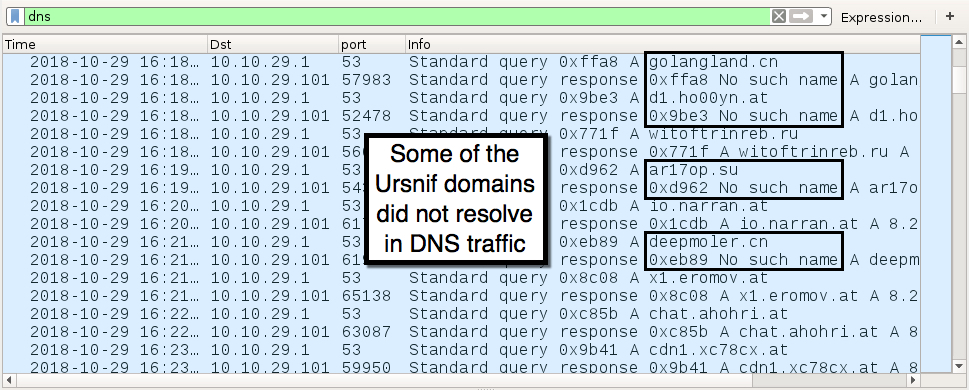
Shown above: DNS traffic from the infection shows additional domains for Ursnif.
Malware from an infected Windows host
Malware from this infection was not persistent. It did not survive a reboot of my infected Windows host. Like Zeus Panda Banker from previous Hancitor infections, follow-up Ursnif malware was saved to the victim's AppData\Local\Temp folder as a .tmp file. Unlike previous Zeus Panda Banker infections, Ursnif malware from this infection did not copy itself anywhere else. It ran as the same .tmp file and was not made persistent to survive a reboot.
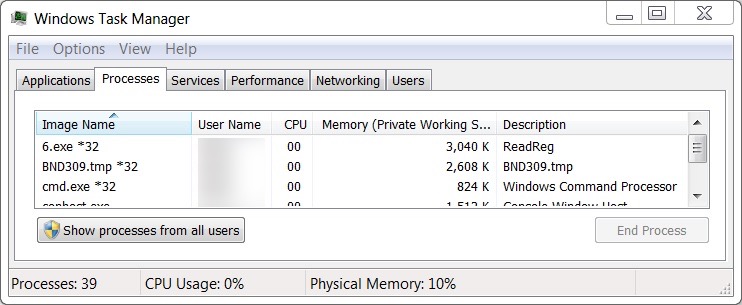
Shown above: Task Manager showed processes by Ursnif and other malware from the infection.
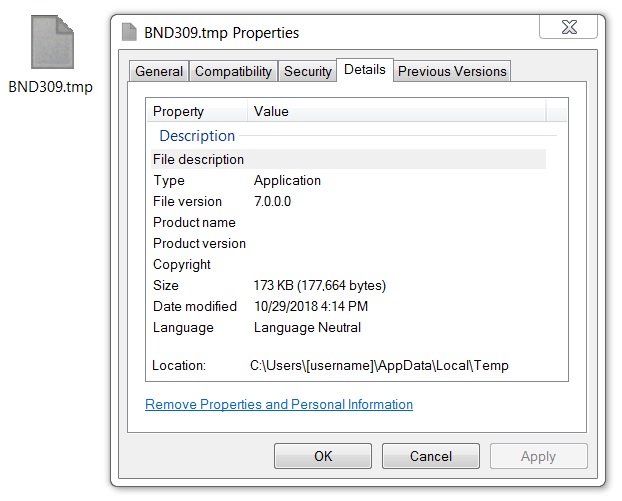
Shown above: Ursnif malware binary retrieved from my infected Windows host.
Indicators
Indicators of traffic from my infected lab host follow:
- Start date/time: Monday 2018-10-29 at 16:07 UTC
Downloading the Word document from a link in the email:
- 47.74.240.167 port 80 - vermontpancake.com - GET /?[string of characters]=[encoded string representing recipient's email address]
IP address check by the infected Windows host--not inherently malicious on its own:
- port 80 - api.ipify.org - GET /
Traffic for the follow-up malware (Pony, Evil Pony, and Ursnif):
- 45.40.182.1 port 80 - mmacontender.com - GET /1
- 45.40.182.1 port 80 - mmacontender.com - GET /2
- 45.40.182.1 port 80 - mmacontender.com - GET /4
- 92.53.126.72 port 80 - otelvictoria.ru - GET /wp-includes/2
- 92.53.126.72 port 80 - otelvictoria.ru - GET /wp-includes/4
- 78.155.217.221 port 80 - uzri.net - GET /wp-includes/2
- 78.155.217.221 port 80 - uzri.net - GET /wp-includes/4
Post-infection traffic for Hancitor, Pony, and Evil Pony:
- 54.38.145.209 port 80 - oneningsitar.com - attempted TCP connections but no response
- 185.74.254.92 port 80 - witoftrinreb.ru - POST /4/forum.php
- 185.74.254.92 port 80 - witoftrinreb.ru - POST /mlu/forum.php
- 185.74.254.92 port 80 - witoftrinreb.ru - POST /d2/about.php
Post-infection traffic for Ursnif:
- 8.208.9.98 port 80 - api.xc78cx.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - io.narran.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - x1.eromov.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - chat.ahohri.at - GET /wpx/[long string of characters]
- 8.208.9.98 port 80 - cdn1.xc78cx.at - GET /wpx/[long string of characters]
DNS queries for additional Ursnif domains:
- DNS query for golangland.cn - response: No such name
- DNS query for d1.ho00yn.at - response: No such name
- DNS query for ar17op.su - response: No such name
- DNS query for deepmoler.cn - response: No such name
- DNS query for go.xiroxaro.at - response: Server failure
- DNS query for ab.pontlap.at - response: No such name
Malware retrieved from my infected lab host follows:
SHA256 hash: 73d7f5cabfc82d7bd8a54e03ecb51567d81ac5dfa8dc1bd36670daede4e6c482
- File size: 228,864 bytes
- File name: fax_271094.doc (random numbers in the file name for each download)
- File description: Downloaded Word document with macros to cause Hancitor infection
SHA256 hash: 846d1e1d019d5bc2a05940b119e19a07643f2e3851184f843960cfd949280894
- File size: 81,920 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\6.exe
- File location: C:\Users\[username]\AppData\Local\Temp\6.pif
- File description: Hancitor malware binary (Windows executable)
SHA256 hash: 07aa5e78498bcf67458770e22590da1529463b9f65213c8f916b3f680d075fdd
- File size: 81,920 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\BND309.tmp (random characters before .tmp in the file name)
- File description: Ursnif malware binary (Windows executable)
Final words
My standard warning still applies. Properly-administered Windows hosts are not susceptible to this type of infection. However, for a variety of reasons, many people run older versions of Windows that are not fully patched or up-to-date. That's why criminals continue to run these malspam campaigns. As long as a small percentage generates a successful infection, these campaigns will remain profitable.
My background is not in system administration, so I don't have details on tools like SRP or AppLocker that can help prevent these malspam-based attacks. My previous diary has a comment about an article from Aaron Margosis to simplify AppLocker deployment (link). For those with Office 2013 and later versions, you have an option to block macros in documents downloaded from the Internet (link).
If you find this diary helpful or have any suggested improvements, please leave a comment.
Email examples, pcap, and malware associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments