Detecting Compressed RTF
I was asked how I knew that the content of the email in my last diary entry, was compressed RTF.
At first, I didn't know this. The reader, Salil, told us that he suspected that the URLs he was looking for, were in stream 67. I looked at stream 67, but couldn't find the content of the email.
Then I analyzed the content of the stream with my tool byte-stats.py, and noticed it was about 5 KB with a high entropy: 7.5...
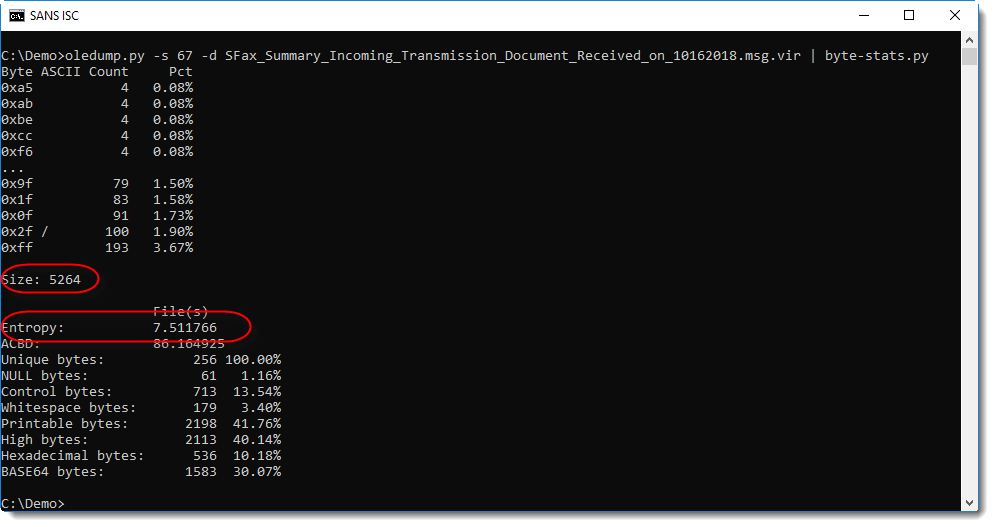
So I thought that the content of this stream was probably compressed. But looking at the hexdump, I didn't recognize the compression method:
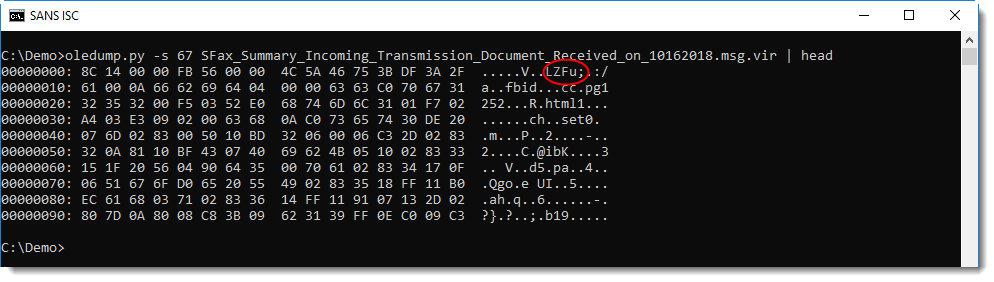
The first string in this hexdump is LZFu. LZ reminded me of Lempel-Ziv compression. A Google search for LZFu gave this:
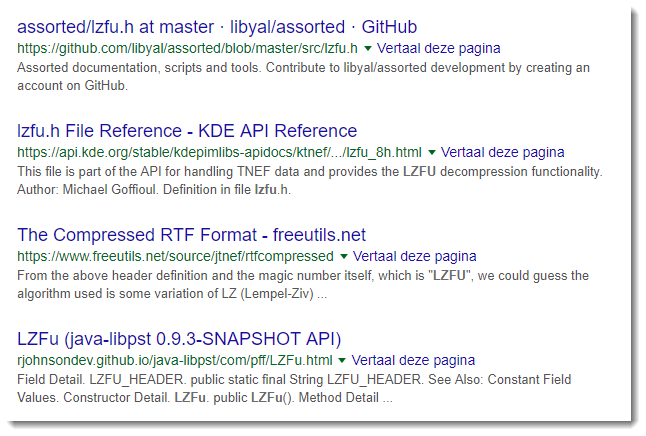
That's when I found out about Compressed RTF, and then I created a decompression tool with the right module and a couple of lines.
I also updated my file-magic tool to detect Compressed RTF using this definition:
# 2018/10/26
#------------------------------------------------------------------------------
# Compressed RTF: file(1) magic Compressed RTF
#
8 string LZFu Compressed RTF
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments