More malspam pushing password-protected Word docs for AZORult and Hermes Ransomware
Introduction
This is a follow-up to a previous diary from last month on malicious spam (malspam) distributing password-protected Word docs with malicious macros designed to infect vulnerable Windows computers with ransomware.
Details
Today, I found five examples of malspam with password-protected Word docs using 1234 as the password. The Word doc had a malicious macro that retrieved AZORult malware. The AZORult malware conducted callback traffic, then the infected host retrieved Hermes ransomware.
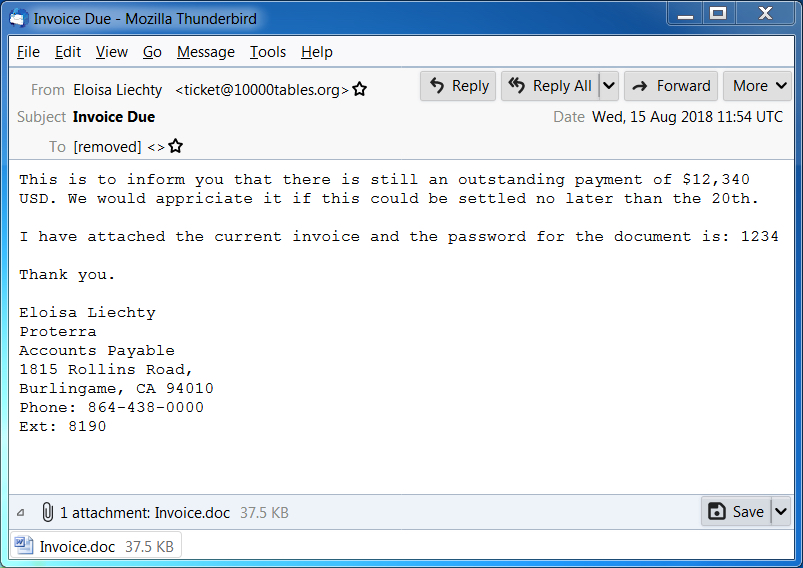
Shown above: Screen shot of a malspam example from today (1 of 2).
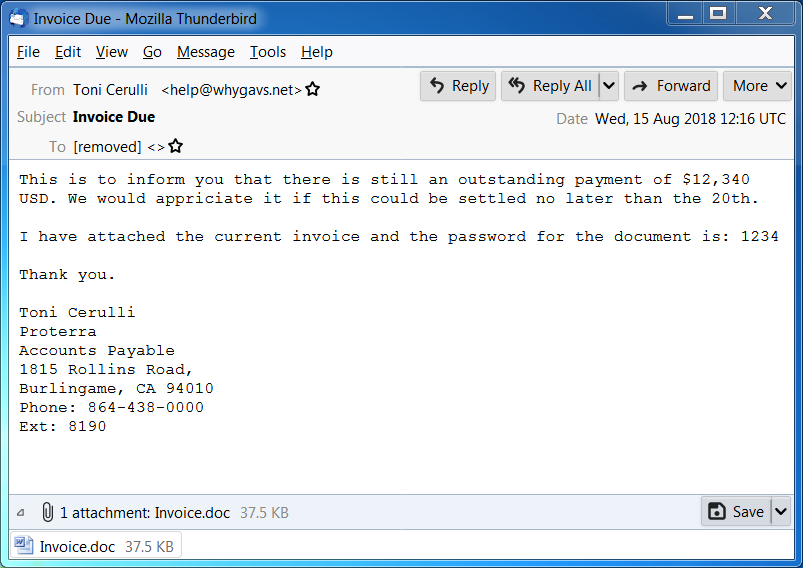
Shown above: Screen shot of a malspam example from today (2 of 2).

Shown above: Opening the password-protected Word doc on a Windows host.
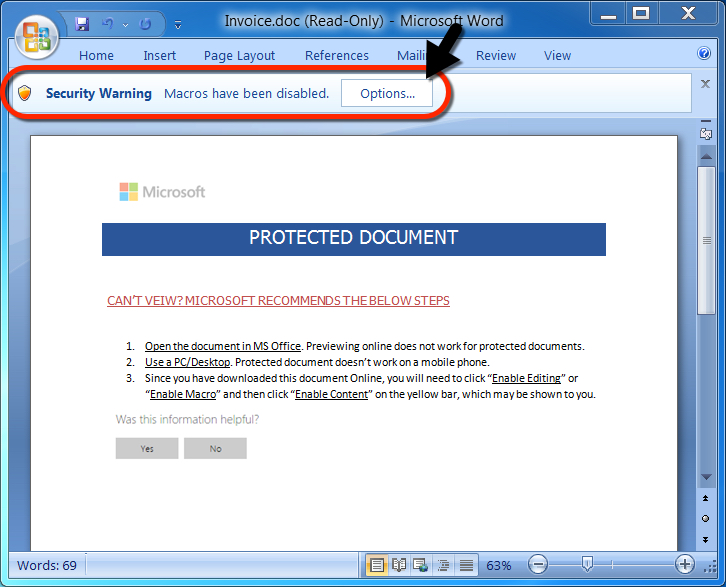
Shown above: After entering the password, a victim must enable macros.

Shown above: Traffic from an infection filtered in Wireshark.
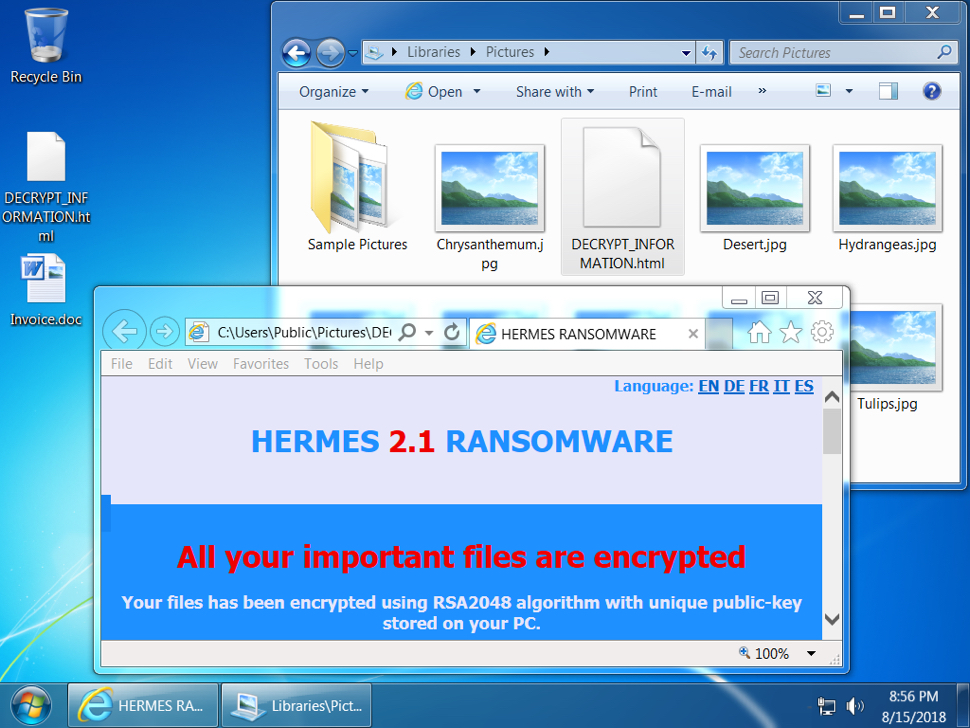
Shown above: Desktop of an infected Windows host.
Indicators
Malspam information from 5 email samples:
- Date: Wednesday 2018-08-15
- Received: from 180connection.org ([46.161.42.24])
- Received: from 10000tables.org ([46.161.42.9])
- Received: from 160h.com ([46.161.42.21])
- Received: from 135798.com ([46.161.42.18])
- Received: from whygavs.net ([46.161.42.20])
- From: Karan Fabiano =?UTF-8?B?wqA=?= <billing@180connection.org>
- From: Eloisa Liechty =?UTF-8?B?wqA=?= <ticket@10000tables.org>
- From: "Edgar Blanding =?UTF-8?B?wqA=?=" <mail@160h.com>
- From: "Jackqueline Wroblewski =?UTF-8?B?wqA=?=" <admin@135798.com>
- From: "Toni Cerulli =?UTF-8?B?wqA=?=" <help@whygavs.net>
- Subject: Invoice Due
- Attachment name: Invoice.doc
Network traffic:
- 209.141.59.124 port 80 - 209.141.59.124 - GET /azo.exe
- 149.129.216.194 port 80 - briancobert.com - POST /index.php (AZORult traffic)
- 149.129.216.194 port 80 - briancobert.com - POST /index.php (AZORult traffic)
- 209.141.59.124 port 80 - 209.141.59.124 - GET /hrms.exe
Associated malware:
- SHA256 hash: 05e3783379157ed6bdc936f306d14b23927b6f682273d37f490349990532c305
- File size: 38,440 bytes
- File description: Password-protected Word doc from malspam with macro for malware
- SHA256 hash: a7b8e4988e9da83ac55b4613bff4bccca62e208c2fed0c850ca024163b27dc09
- File size: 348,160 bytes
- File location: hxxp://209.141.59.124/azo.exe
- File location: C:\Users\[username]\AppData\Local\Temp\qwerty2.exe
- File description: First-stage malware, AZORult
- SHA256 hash: 2698c141c7fb2660fd009ce9c083022a531c28c8ae8258555027a2f7852de13d
- File size: 348,160 bytes
- File location: hxxp://209.141.59.124/hrms.exe
- File location: C:\Users\[username]\AppData\Local\Temp\hrms.exe
- File description: Second-stage malware, Hermes ransomware
Contact info from the decryption instructions:
- primary email: 4234234fdssdfdsaf@tutanota.com
- reserve email: decryptsupport1@cock.li
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments