Malicious Post-Exploitation Batch File
Here is another interesting file that I found while hunting. It is a malicious Windows batch file (.bat) which helps to exploit a freshly compromised system (or... to be used by a rogue user). I don't have a lot of information about the file origin, I found it on VT (SHA256: 1a611b3765073802fb9ff9587ed29b5d2637cf58adb65a337a8044692e1184f2)[1]. The script is very simple and relies on standard windows system tools and external utilities downloaded when neede.
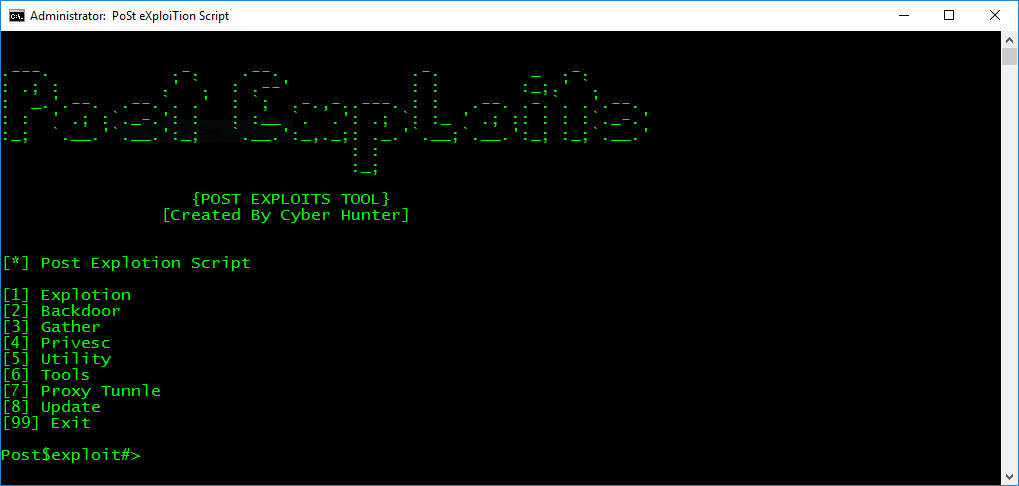
Here is an overview of the available options. This should give you a good overview of the batch capabilities:
Exploitation - Add User Account - Show/hide User Account - Enable Telent Service - Enable Psexec Service - Enable Remote Desktop Service - Remote Login bypass backdoor (setch.exe or utilman.exe) - EternalBlue - MS1710-Psexec Backdoor - Meterpreter - Cmd_shell - Vnc_Powershell - Winvnc - JRrat - Download/Execute ps1_script - Download/Execute - Post_exploits_script command shell - Persis - Ammyy Admin Trojan - Radmin Gather - Mimikatz - Mimikittenz - Hashdump - Wifi Password Dump - Sherlock (Local privilege escalation vulnerabilities Scanner) - Chrome Passwd Dump - Firefox Passwd Dump - Powerup (Vulns Founder) - Get System info - Get IPAddress - Arp Scan - Port Scanner - Get Shares List - Get Net View - Netstat - Get Process - Scan MS17-010 Vulnerablity - MS1710-Psexec_Scanner - Port Forword Privsec - MS11-046 - Invoke-BypassUAC - Invoke-WScriptBypassUAC - Invoke-MS16032 - Invoke-MS16135 - Invoke-EventVwrBypass - Invoke-EnvBypass - Invoke-FodHelperBypass - Invoke-SDCLTBypass - Invoke-PsUACme - UAC-TokenMagic - EventVwrBypass (Win=7,8,8.1,10) Tools - Install Python27 - Install Ruby187 Proxy Tunnel - Setup Proxy Tunnle - Delete Proxy Tunnle - Show All Proxy Tunnle Update
Note the numerous typo errors (I left them as is). The script is a good example of demonstrating how easy it is to interact with a system only from a .bat file. Manipulation of users, registry keys, network, etc. The script has an update feature that fetches files from hxxp://remotebot.000webhostapp[.]com/powershellbot/. Many tools are also fetched from a GitHub repository[2] when needed.
[1] https://www.virustotal.com/intelligence/search/?query=1a611b3765073802fb9ff9587ed29b5d2637cf58adb65a337a8044692e1184f2
[2] https://github.com/cyberhunter00/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments