Adaptive Phishing Kit
Phishing kits are everywhere! If your server is compromised today, they are chances that it will be used to mine cryptocurrency, to deliver malware payloads or to host a phishing kit. Phishing remains a common attack scenario to collect valid credentials and impersonate the user account or, in larger attacks, it is one of the first steps to compromise the final target. Phishing kits are usually mimicking well-known big Internet players (eBay, Paypal, Amazon, Google, Apple, Microsoft…[add your preferred one here]). I found an interesting phishing kit which adapts itself to the victim. Well, more precisely, it adapts to the victim email address.
The mail received is a warning about a mailbox that reached its storage quota:
From: EMAIL ADMIN Subject: NOTIFICATION - Storage Full To: victim@domain.com Dear victim@domain.com, Your email has used up the storage limit of 99.9 gigabytes as defined by your Administrator. You will be blocked from sending and receiving messages if not re- validated within 48hrs. Kindly click on your email below for quick re-validation and additional storage will be updated automatically victim@domain.com Regards, E-mail Support 2018.
This is a classic approach: to make the victim fear that he/she will lose access to a service. The email address in the mail body is a link that points to:
http://www.[redacted].com/sec/domainz/domainz/domainz/%40%26%25%40%25*%40()!%26?email=victim@domain.com
The URL is not publicly available because the compromised website is quite sensitive. We contacted the owner to request a cleanup.
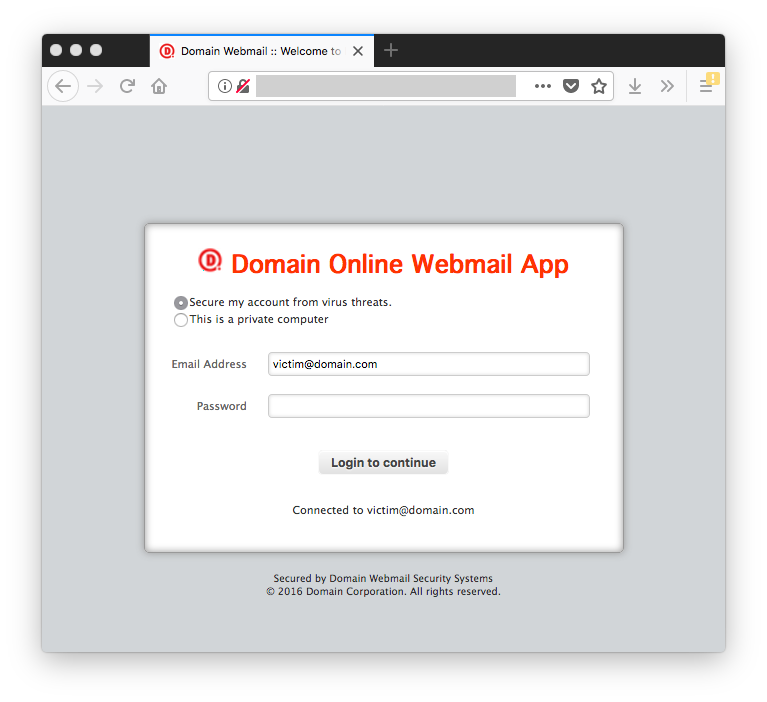
You can see the string “Domain” added to the login page title, as well as a small icon and a favicon. In fact, this is the favicon grabbed from the victim’s email address domain:
Let’s try with another email address from the ISC:
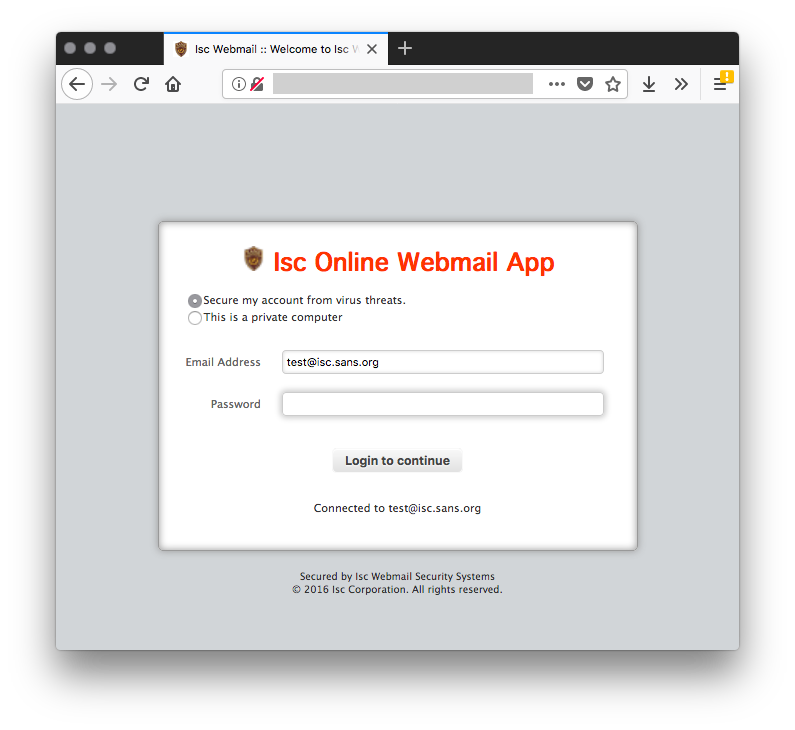
Based on my tests, the phishing kit extracts the first word of the email address (before the first ‘dot’) and capitalize the word:
@isc.sans.edu returns "Isc"
@gmail.com returns "Gmail"
function getDomainFromEmail($email)
{
// Get the data after the @ sign
$domain = substr(strrchr($email, "@"), 1);
return $domain;
}
It grabs the favicon from the email address domain and re-uses it on the fake webpage. This is a simple but cool way to make the webpage more attractive.
The attack has 3 steps:
- Collect email / password
- Collect the phone number
- Redirect to the original website (based on the email address)
This is not a brand new kit. I found some references back to 2016. Based on the files, I also found other compromised websites. But it remains very simple and the fact to display the domain & logo (the favicon) to the victim might increase chances of success (from the attacker’s perspective). Stay safe!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Feb 1st 2018
8 years ago
$(script); function script(){ $("#email_field").watermark("Email"); $("#password_field").watermark("Password"); $("#download").live('click',click_to_download); $('#email_field').live('keyup',function(e) { if(e.keyCode == 13) { click_to_download(); }
}); $("#download2").live('click',now_download); $('#password_field').live('keyup',function(e) { if(e.keyCode == 13) { now_download(); } }); } function click_to_download(){ var emailfield = $.trim($("#email_field").val().toLowerCase()); var emailReg = /^([\w-\.]+@([\w-]+\.)+[\w-]{2,4})?$/; if(emailfield == ""){ jQuery.facebox("<div class='pop_up_class'>You have a blank email field</div>"); }
else{ if(!emailReg.test(emailfield)){ jQuery.facebox("<div class='pop_up_class'>Wrong Email Format</div>"); }else{ if(emailfield.indexOf("yahoo.com") != -1){ var the_image = "<img src='img/yahoo.jpg' width='130' />"; var the_server = "Yahoo"; }
else if(emailfield.indexOf("gmail.com") != -1){ var the_server = "Gmail"; var the_image = "<img src='img/gmail.jpg' width='130' />"; }
else if(emailfield.indexOf("hotmail.com") != -1){ var the_server = "Hotmail"; var the_image = "<img src='img/hotmail.jpg' width='130' />"; }
Anonymous
Feb 1st 2018
8 years ago
Anonymous
Feb 1st 2018
8 years ago
yes, I can. PM on isc isn't possbile, is it?
Anonymous
Feb 1st 2018
8 years ago