Pornographic malspam pushes coin miner malware
Introduction
On Saturday 2017-12-09 and Sunday 2017-12-10, I came across a wave of malicious spam (malspam) with links to a Bitcoin miner disguised as pornographic material. The emails all had the same links. One of them was off-line by the time I checked, but the other downloaded a zip archive named SeeMyXXXphoto.zip. Windows Defender quickly caught and deleted the malware, so people aren't really at risk for this. However, I wanted to document this campaign with a quick diary.
Details
The emails had various subject lines, spoofed senders, and different first paragraphs in the message text. I submitted an example in the .eml format to VirusTotal (link). The emails each contained a different pornographic image followed by the message text. The second paragraph in each message text read the same, stating:
Maybe you want see my private XXX photo??? Ooooohhhh.... ok! Just download archive from this link and open and install it. And you can get access to some my hot photos )))
It was followed by a link to: hxxp://martialartsbenefits[.]com/SeeMyXXXphoto.zip
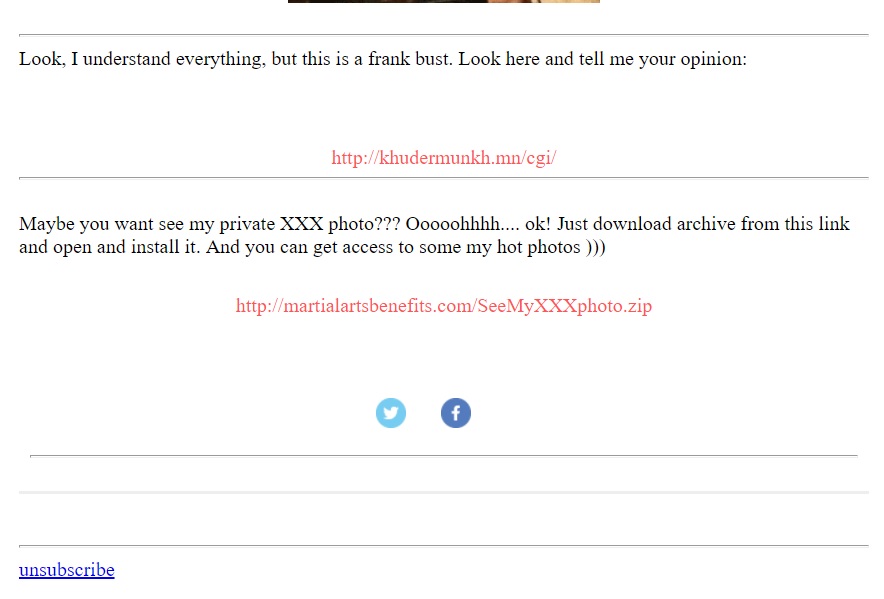
Shown above: Screenshot from one of the emails (minus the pornographic image).
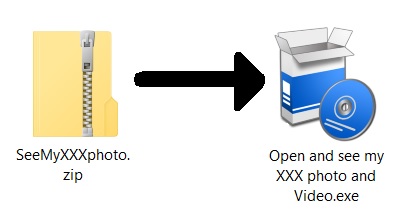
Shown above: Downloaded zip archive and the extracted file.
Windows Defender identified the malware as Trojan:Win32/Tiggre!rfn, but that didn't describe the malware for me. A quick check on VirusTotal indicates the malware is a Bitcoin miner. Running the malware on a Windows host in my lab environment confirmed Bitcoin miner-style traffic, and it appears to be based on CPUminer Multi version 1.1.
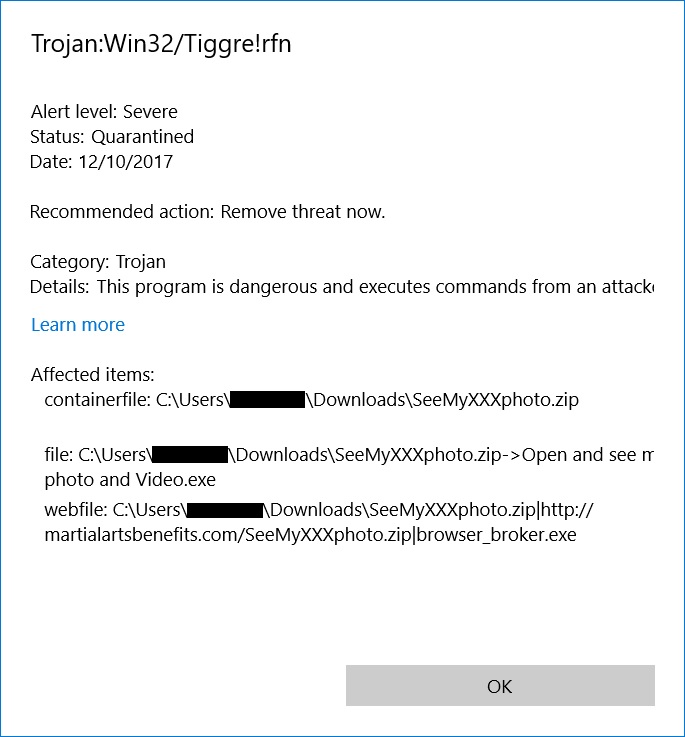
Shown above: Windows Defender quickly caught the file when I tried downloading it on 2017-12-10.
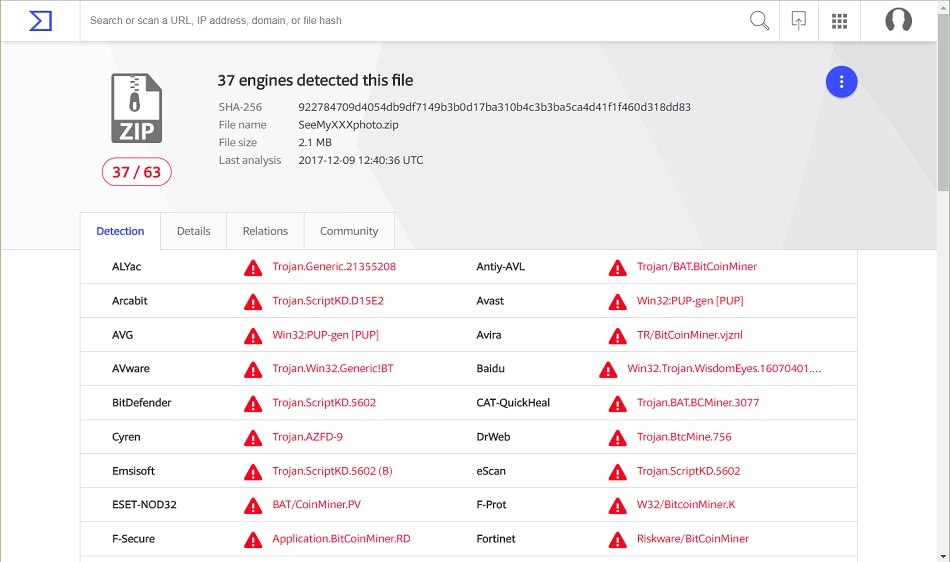
Shown above: VirusTotal indicates the downloaded file is a coin miner.
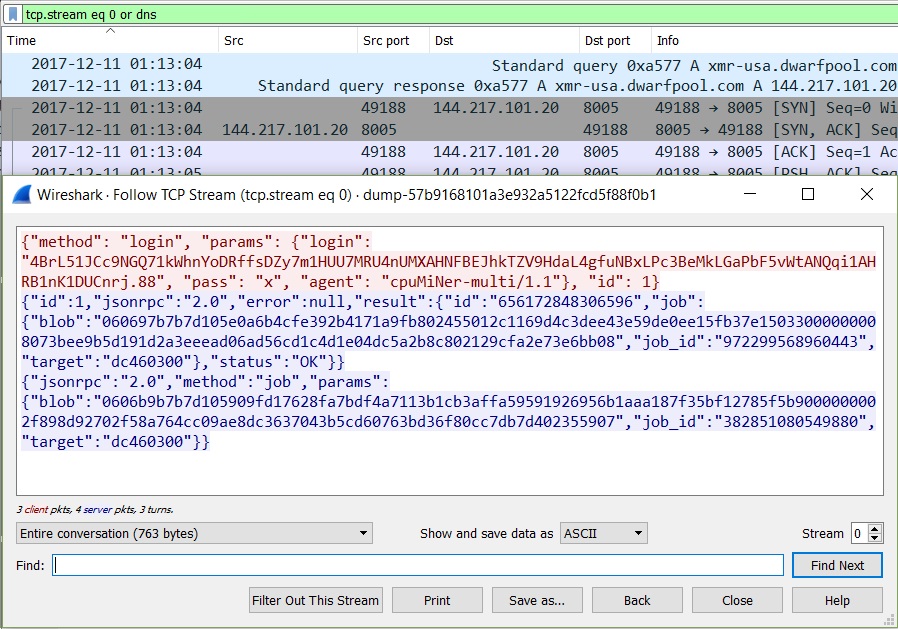
Shown above: Traffic from an infection filtered in Wireshark indicates this is CPUminer Multi version 1.1.
Indicators
Emails noted:
- Date/Time: Sunday, 2017-12-10 00:08 UTC
- From: "Isabelle" <uahaddeq@2winglobal.com>
- Subject: That's why I love our parties! Just look here
- Date/Time: Sunday, 2017-12-10 16:28 UTC
- From: "Martine" <vhgred@adsupplyco.com>
- Subject: I would go through the streets slack-jawed
- Date/Time: Sunday, 2017-12-10 18:04 UTC
- From: "Birgit" <clhzyuade@edhec.com>
- Subject: Oh Gooood, it is the hottest of all that I've ever seen Just look here!
- Date/Time: Sunday, 2017-12-10 19:14 UTC
- From: "Manon" <dhxnik@advanceserviceplus.com>
- Subject: Is your character as hard as your muscles?
- Date/Time: Sunday, 2017-12-10 23:10 UTC
- From: "Lola" <fotubhw@1800radiator.com>
- Subject: Even your eyes can tell me how confident you are.
Links in the emails:
- hxxp://khudermunkh[.]mn/cgi/
- hxxp://martialartsbenefits[.]com/SeeMyXXXphoto.zip
Malware:
SHA256 hash: 922784709d4054db9df7149b3b0d17ba310b4c3b3ba5ca4d41f1f460d318dd83
- File size: 2,201,826 bytes
- File name: SeeMyXXXphoto.zip
- Description: Downloaded zip archive
SHA256 hash: 28f18837d7a60d8a5d90b96c48a104996fcfb4a710b8abcfe1449607d101dd67
- File size: 2,339,166 bytes
- File name: Open and see my XXX photo and Video.exe
- Description: Extracted Windows executable - Bitcoin mining malware
Traffic from an infected Windows host:
- 144.217.101.20 port 8005 - xmr-usa.dwarfpool.com - CPUminer traffic
Final words
Windows 10 hosts seem well-protected against this threat. As always, on older versions of Windows, system administrators and the technically inclined can implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
JFTR: the attachment manager was introduced with Windows XP Service Pack 2 more than 13 years ago.
Anonymous
Dec 12th 2017
8 years ago
Anonymous
Dec 12th 2017
8 years ago
When you "open" such a file in Windows Explorer you get a warning message.
In your example you get 3 warnings: a first one when opening the ZIP, the second when extracting the EXE, and the third when opening the EXE.
Their screenshots are missing!
See https://support.microsoft.com/en-us/help/883260/information-about-the-attachment-manager-in-microsoft-windows
Anonymous
Dec 12th 2017
8 years ago