Tracking Website Defacers with HTTP Referers
In a previous diary, I explained how pictures may affect your website reputation[1]. Although a suggested recommendation was to prevent cross-linking by using the HTTP referer, this is a control that I do not implement on my personal blog, purely for research purposes. And it successfully worked!
My website and all its components are constantly monitored but I’m also monitoring online services like pastebin.com to track references to my domains, IP addresses and other interesting information. A few days ago, I received an alert about a mention to my blog[2]. It contained some HTML code used to deface websites:
<html lang="en-US"><head><title>Indonesian-Defacer</title> <link rel="icon" type="image/x-icon" href="https://blog.rootshell.be/wp-content/uploads/2012/02/blackhat-nl.png"> <meta property="og:title" content="nginxDEX"> <meta property="description" content="Jemb4t"> <meta property="og:author" content="Jemb4t"> <meta property="og:image" content="http://i.imgur.com/F2KaExC.jpg"> <meta charset="UTF-8"> </head> <script type="text/javascript”> …
As you can see a group of website defacer (MagelangN00bs[3]) is using a direct link to an image on my blog as favicon[4] file. I think that they used my image because it looks like the Indonesian flag with a "black hat" head on top of it:

Here is an example of defaced website by this group:
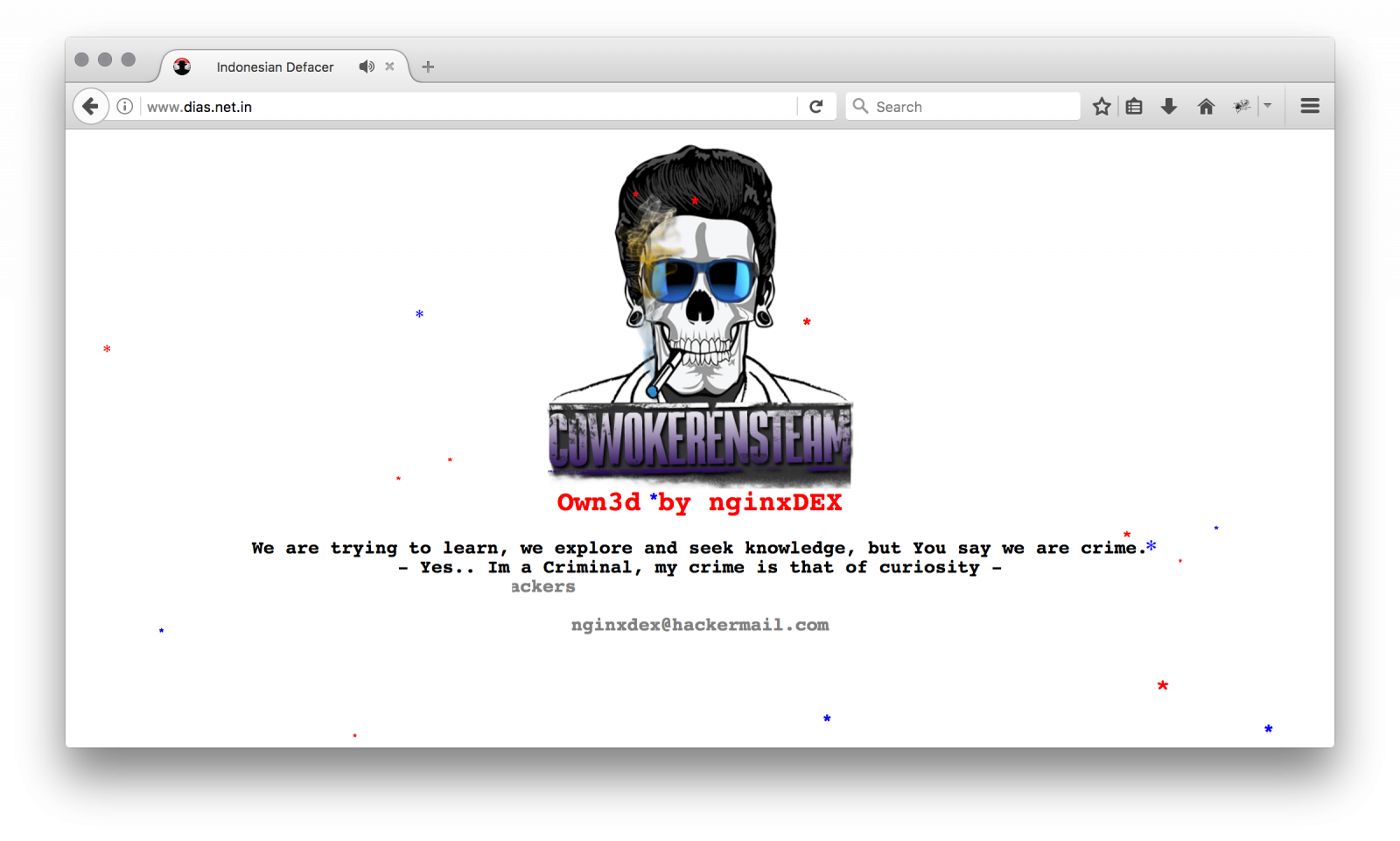
Well, nothing fancy, just a logo, some nasty music... Let's have a look at my logs and search for references to the original pictures. The group started its activity around the 15th of March:

And what about the targets? After cleaning the referers (Google being of course the top-1), 90 websites were reported as defaced. Some examples:
- hxxp://www.dias.net.in (restored)
- hxxp://unitedyouthmission.com/ (still defaced)
- hxxp://learnwellme.com/ (restored)
- hxxp://www.mekallifestyle.in/ (still defaced)
- hxxp://politicalvartha.com/ (restored)
- hxxp://www.fundookids.in/ (restored)
The group is still active and new websites are defaced almost every day. Once again, this is a good example of the power of HTTP referers.
[1] https://isc.sans.edu/forums/diary/How+your+pictures+may+affect+your+website+reputation/22151/
[2] https://pastebin.com/Zq8Ceebu
[3] http://www.magelang1337.com/
[4] https://en.wikipedia.org/wiki/Favicon
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
That can cause a lot of confusion and bad times. Even more for us that work with security, someone just will think that you are doing the thing, but is not.
So we need to protect our selves from a bad reputation that we are not guilty.
Anonymous
Apr 7th 2017
8 years ago
Anonymous
Apr 7th 2017
8 years ago
Can you change the contents of the image that they "deep-link" to, to become a much-larger file,
while changing all your references to your image to reference a different image?
Imagine them fetching an 800-by-600 image, and causing it to be displayed whenever somebody views the compromised page?
Anonymous
Apr 8th 2017
8 years ago
Anonymous
Apr 12th 2017
8 years ago