Follow-up to: Stop calling it a ransomware "attack"
Introduction
Earlier today, I posted a diary protesting an overall trend of calling ransomware infections "ransomware attacks" [1]. Unfortunately, that previous diary didn't include information on attacks that actually have involved ransomware.
Some tweets about my original write-up got me thinking about it some more... So this diary goes into more detail.
Shown above: Commenting on the first diary, @DanielGallagher notes Samsam.
Shown above: Commenting on the first diary, @fwosar discusses RDP attacks.
Distribution: both large-scale and targeted
As previously stated, I frequently find ransomware during daily investigations of exploit kit (EK) traffic and malicious spam (malspam) campaigns. However, my visibility is limited. I rarely, if ever, run across activity I consider a targeted attack. That field of view doesn't include ransomware infections seen after brute force attacks using Microsoft's Remote Desktop Protocol (RDP). Examples of brute force RDP attacks resulting in ransomware infections have been published as recently as May [2, 3] and June 2016 [4].
Other sources have reported targeted attacks involving ransomware known as Samas, SamSa, or SamSam [5, 6, 7, 8, 9 to name a few]. Most of these write-ups say organizations in the health industry (as well as other industries) have been targeted. These reports document a trend where an attacker first gains unauthorized access to an organization's network, then the attacker deploys ransomware on hosts within that network.
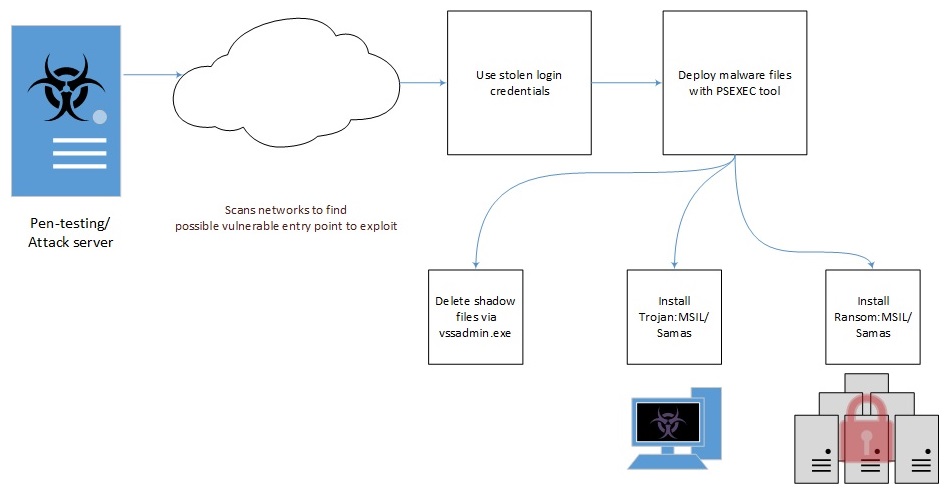
Shown above: Diagram of a Samas infection chain from the Microsoft report [8].
That's certainly an attack.
I'd be crazy not to include this information when discussing my disdain for the term "ransomware attack." And it's something I foolishly omitted in my previous diary on the subject. Ransomware is, indeed, distributed in both large-scale and targeted campaigns.
Large-scale does not equal targeted
Most reports of ransomware infections, especially in the health care industry, imply some sort of targeted attack. But that's not always the case.
For example, in March 2016 we saw reports that a Kentucky-based Methodist Hospital was infected with Locky ransomware through malspam. The malspam contained a Word document with malicious macros masquerading as an invoice [10]. The press played it up as an attack, but malspam is a common tactic of large-scale campaigns distributing Locky, where some messages occasionally slip through spam filters. Even Krebs called it an "opportunistic attack" when reporting on the incident [11].
However, opportunistic is not targeted.
In March 2016, Wired published an in-depth write-up on why hospitals are perfect targets for ransomware [12]. In that article, the author discusses Methodist Hospital and other Locky incidents while including targeted attacks by criminals spreading Samsa ransomware. Although the author notes Locky involves "spray-and-pray phishing campaigns" involving mass emails, this method is still described as a "Locky attack."
Wired's article is well-written and worth a read. It includes plenty of detail on the reasons why health care organizations are at risk. But readers who only skim the article will miss some key points, and they could easily confuse large-scale Locky distribution with a targeted attack. In cases like this, I think authors should use "Locky campaign" instead of "Locky attack."
Final words
Even considering targeted attacks involving ransomware, I still feel we're putting too much emphasis on the attackers and not enough focus on fixing our own vulnerabilities.
Furthermore, I believe media reporting leads some people to confuse large-scale ransomware campaigns with targeted attacks.
The number of ransomware samples found in large-scale campaigns far outweighs the number of ransomware samples reported from targeted attacks. I still believe that, odds are, any given ransomware "attack" is probably the result of a large-scale campaign.
I'd rather see people use "ransomware incident" instead of "ransomware attack."
My thanks to @DanielGallagher and @fwosar for their tweets. They helped keep me a bit more honest.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://isc.sans.edu/forums/diary/Stop+calling+it+a+ransomware+attack/21345/
[2] https://blog.fox-it.com/2016/05/02/ransomware-deployments-after-brute-force-rdp-attack/
[3] http://researchcenter.paloaltonetworks.com/2016/05/unit42-bucbi-ransomware-is-back-with-a-ukrainian-makeover/
[4] http://blog.emsisoft.com/2016/06/29/apocalypse-ransomware-which-targets-companies-through-insecure-rdp/
[5] http://researchcenter.paloaltonetworks.com/2016/03/evolution-of-samsa-malware-suggests-new-ransomware-tactics-in-play/
[6] http://blog.talosintel.com/2016/03/samsam-ransomware.html
[7] https://www.secureworks.com/blog/samas-ransomware
[8] https://blogs.technet.microsoft.com/mmpc/2016/03/17/no-mas-samas-whats-in-this-ransomwares-modus-operandi/
[9] http://blog.trendmicro.com/trendlabs-security-intelligence/lesson-patching-rise-samsam-crypto-ransomware/
[10] http://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/locky-ransomware-strain-led-kentucky-hospital-to-an-internal-state-of-emergency
[11] http://krebsonsecurity.com/2016/03/hospital-declares-internet-state-of-emergency-after-ransomware-infection/
[12] https://www.wired.com/2016/03/ransomware-why-hospitals-are-the-perfect-targets/


Comments
> ...visibility is limited.
Agreed; that applies to all of us, to some extent.
Another bit of ransomware that has been deployed following RDP logins is Le Chiffre:
https://blog.malwarebytes.com/threat-analysis/2016/01/lechiffre-a-manually-run-ransomware/
> Most of these write-ups say organizations in the health industry (as well as other industries) have been targeted.
As the author of this post:
https://www.secureworks.com/blog/ransomware-deployed-by-adversary
..and having assisted with reference [7], I have been trying to make it clear that the media focus on hospitals and health care is a misconception, and a dangerous one, at that.
> ...media reporting leads some people to confuse large-scale ransomware campaigns with targeted attacks.
Agreed. I would also suggest that we take a look at one of the references, specifically:
https://blogs.technet.microsoft.com/mmpc/2016/03/17/no-mas-samas-whats-in-this-ransomwares-modus-operandi/
Read through it carefully. Throughout the write-up, "it" is used to refer to the ransomware..."it has a more targeted approach", "It starts with a pen-testing/attack server...", "It can use other information-stealing malware...".
From what I've seen, the Samas ransomware doesn't do any of this...the person or group using it does.
Anonymous
Aug 18th 2016
9 years ago