Playing With Sandboxes Like a Boss
Last week, Guy wrote a nice diary to explain how to easily deploy IRMA to analyze suspicious files. Having a good tool to work on files locally is always interesting for multiple reasons. You are doing some independent research, you don't always have a safe Internet connectivity or you simply don't want to generate some traffic that could ring a bell at the attacker's side. By "safe" connectivity, I mean a "dirty Internet" connectivity (like a DSL residential line) to bypass the corporate infrastructure. Locally running tools are also a nice way to prevent files to be sent to cloud services. This applies not only to bad guys but also to pentesters who are preparing their attacks and generate targeted samples (think about the Veil framework)
If tools like IRMA or Cuckoo are good tools, they must be adapted and tuned to your own environment because running them out of the box will not produce the best results. Nothing against free tools, the same problem affects commercial products. They are delivered with standard sandboxes mimicking classic setup (WinXP, Win7, ...) but each organization has its own "image" to deploy workstations with, sometimes, very tricky configurations.
For a while, malware developers know that their software will be analyzed and tortured by such tools. To prevent this, they are trying to detect as soon as possible in which environment they are running. The key question is: Is the malware executed on a real victim's computer or in a sandbox? If the malware detects to be running in a sandbox, its behavior will change. Some will simply terminate themselves, others could have be "funny" and mimick another malware! Attackers and defenders are playing a continuous cat and mouse game to improve the evasion for the first and the detection for the second.
From an defender's perspective, it is critical to harden your sandbox. Basic tests are performed by pieces of malware like:
- To test the presence of a debugger
- To slowdown the malware execution by adding sleep() calls here and there (A malware has plenty of time to remain below the radar and perform tasks later. On the other side, a sandbox analysis must be completed as soon as possible. Speed is a key).
- To test the host MAC address - Virtualization tools use dedicated pools of MAC addresses.
But they are also plenty (but very effective) things that can be tested/probed!
First of all, about the user's behavior:
- Is the mouse moving? Most sandboxes keep the mouse at the center of the screen.
- Are they icons on the desktop?
- Is there a wallpaper (and not the standard one)
- Are they applications running?
- Are they bookmarks saved in the browser?
Classic desktops look more like this and contain plenty of shortcuts:
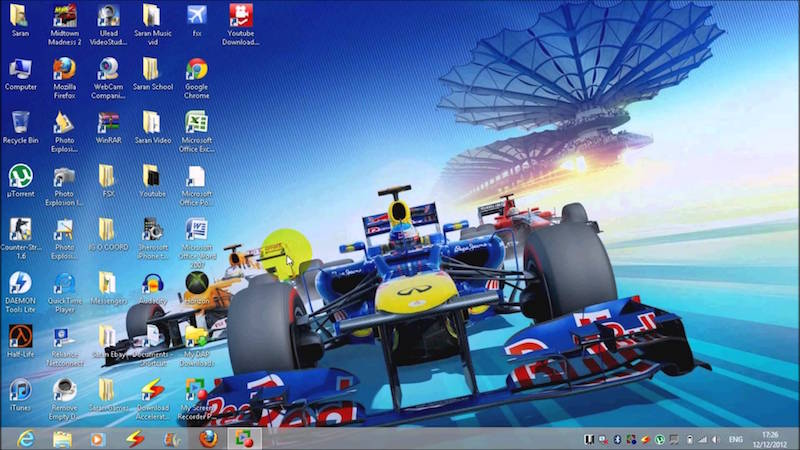
More tests against the system can be performed:
- What is the system uptime? (a sandbox is rebooted from a clean snapshot for each new analyze)
- What's the system drive C: size? (sandboxes do not have plenty of storage)
- How many CPU / cores are available?
- The memory size is also a good indicator (who's running a sandbox with less than 8GB of RAM today?)
- The screen resolution (99% of users have a screen resolution > 1024x768)
- The computer model (sandboxes emulate often old computers like Dell desktops)
- The hostname ("sandbox001" or "win7_001")
- Is there a printer defined
- No temporary files nor application data
- Does the sandbox have no Internet connectivity?
- Does the sandbox run suspicious processes (python.exe or perl.exe are not common on a corporate computer)
- No antivirus installed? Really? On a classic desktop?
- Is the sandbox part of a domain? Is it linked to a domain controller? Are shares available?
- What about the presence of tools/applications: VMware tools, Microsoft Office, ...
If you need to deploy a sandbox, the best way is to base it on a real user workstation and update it with user behavior facts. If you're looking for a sandbox system, check if they can be customized! To conclude, here is an interesting Python tool which will test most of the points listed above: Sandbox_tester. Happy malware analysis!
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments