Anybody Doing Anything About ANY Queries?
(in an earlier version of this story, I mixed up Firefox with Chrome. AFAIK, it was Firefox, not Chorme, that added DNS ANY queries recently)
Recently, Firefox caused some issues with it's use of ANY DNS queries [1]. "ANY" queries are different. For all other record types, we got specific entries in our zone file. Not so for ANY queries. RFC 1035 doesn't even assign them a name [2]. It just assigned the query code (QCODE) of 255 to a "request for all records". The name ANY is just what DNS tools typically call this query type.
The "ANY" record works a bit differently depending on whether the query is received by a recursive or authoritative name server. An authoritative name server will return all records that match, while a recursive name server will return all cached values. For example, try this:
1. Send a DNS "ANY" query for "evilexample.com" to the authoritative name server
dig evilexample.com ANY @ns1.dshield.org
I am getting 44 records back. Your number may be different.
2. Next, request a specific record using your normal recursive DNS server
dig evilexample.com
I am getting one answer and two authority records (YMMV)
3. Finally, send an "ANY" query for evilexample.com to your recursive name server
dig ANY evilexample.com
You should get essentially the same information as you got in step 2. The recursive name server will only return data that is already cached. UNLESS, there is no cached data, in which case the recursive name server will forward the query, and you will get the complete result.
So in short, if there is cached data, ANY queries are not that terrible, but if there is no cached data, then you can get a huge amplification. The "evilexample.com" result is close to 10kBytes in size. (Btw: never mind the bad DNSSEC configuration.. it is called "evilexample" for a reason).
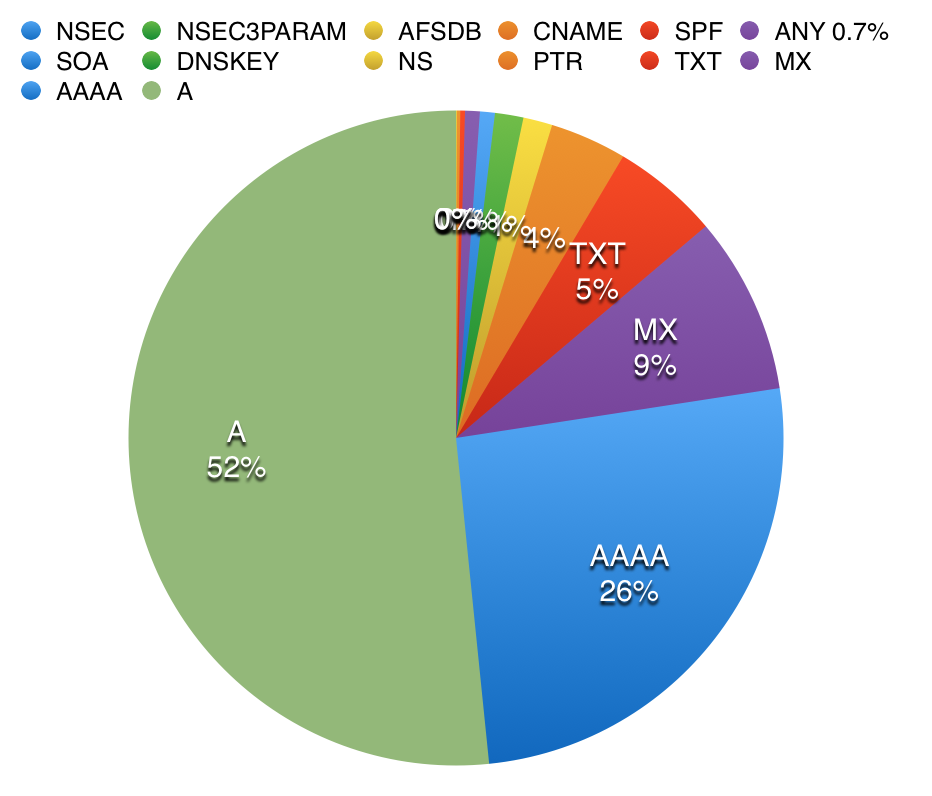
So but how common are these "ANY" queries? I took a quick look at a recursive and an authoritative name server. The recursive name server had no ANY queries at all in its query log (I am not using the latest version of Chrome on Windows). The authoritative name server had 0.7% of ANY queries. (click on image for full size)
 |

|
| Authoritative Name Server | Recursive Name Server |
As expected, the recursive name server, which is only forwarding requests for a few internal hosts, is a lot "cleaner". The authoritative name server, which is exposed to "random" queries from external hosts, is a lot more "dirty" and with many networks still preferring the legacy IPv4 protocol, A queries outnumber AAAA queries. Any queries make up less then 1%, and they follow a typical scheme. For example:
| Time | Client IP |
|---|---|
| 16:23:37 | 212.113.164.135 |
| 16:23:38 | 212.113.164.133 |
| 16:23:38 | 212.113.164.131 |
| 16:23:39 | 212.113.164.128 |
| 16:23:39 | 212.113.164.131 |
| 16:23:40 | 212.113.164.132 |
| 16:23:41 | 212.113.188.75 |
| 16:23:43 | 212.113.164.132 |
| 16:23:43 | 212.113.164.133 |
| 16:43:31 | 212.113.164.132 |
| 16:43:33 | 212.113.164.135 |
| 16:43:33 | 212.113.188.75 |
| 16:43:33 | 212.113.164.129 |
| 16:43:35 | 212.113.164.131 |
| 16:43:35 | 212.113.164.131 |
Short "surges" of queries arriving for the same ANY record from the same /24. This is not "normal". All these hosts should probably use the same recursive name server, and we should only see one single ANY request that is then cached, if we see it at all. This is typical reflective DDoS traffic. In this case, 212.113.164.0/24 is under attack, and the attacker attempts to use my name server as an amplifier.
Is it safe to block all ANY requests from your authoritative name server? IMHO: yes. But you probably first want to run a simple check like above to see who and why is sending you ANY requests. Mozilla indicated that they will remove the ANY queries from future Firefox versions, so this will be a minor temporary inconvenience.
[1] https://bugzilla.mozilla.org/show_bug.cgi?id=1093983
[2] https://www.ietf.org/rfc/rfc1035.txt
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Most of the source of those attacks just do not give a damn for more than 15 years.
See BCP38.
Easy fix to implement.
Anonymous
Mar 5th 2015
1 decade ago
Anonymous
Mar 5th 2015
1 decade ago
https://bugzilla.mozilla.org/show_bug.cgi?id=1093983
Anonymous
Mar 5th 2015
1 decade ago
Anonymous
Mar 5th 2015
1 decade ago
http://fanf.livejournal.com/122220.html
The patch half way down the page will change qmail's resolution from ANY to CNAME queries which fixes the issue.
Anonymous
Mar 5th 2015
1 decade ago
Anonymous
Mar 6th 2015
1 decade ago
> For me I see prefetching as the problem here, is it really needed?
In general - yes, we're moving towards more speculative processing: dns, tcp, ssl, and even document retrieval and rendering will all be possibilities at some point.
Reaction time to user input is the main goal.
------------------------
Will Firefox become a "resource-hog" when it does all of the above, both on the local computer, and placing additional load on the TCP/IP connection?
What about the other web-browsers (Safari, Opera, Chrome) -- will they keep-up with Firefox, by bloating their software with such "feature-creep" ?
Yes, the days of 64MB (not GB) of RAM, and 900 Mhz single-core CPUs are gone, but should web-surfers need to "beef-up" their computer to run Firefox?
My sympathies go to network gurus at colleges/universities, when all that "speculative" Internet traffic from literally thousands of on-campus student computers causes "traffic-management" problems on the institution's Internet gateway.
Anonymous
Mar 10th 2015
1 decade ago