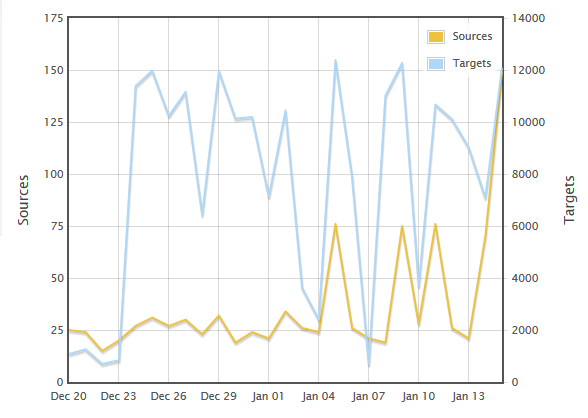
tcp/6379 trolling - Redis NoSQL? Or something else?
DShield sensors report an uptick of scanning for tcp/6379, currently mostly originating from 61.160.x and 61.240.144.x, which are both CHINANET/UNICOM. tcp/6379 is the default port of the Redis NoSQL database (http://redis.io) and Redis by default accepts connections from "any". This has been known for a while though, and is also quite prominently mentioned in the Redis documentation (http://redis.io/topics/security):
Redis is designed to be accessed by trusted clients inside trusted environments. This means that usually it is not a good idea to expose the Redis instance directly to the internet
which makes us wonder if the service scanned for in this case is indeed Redis, or something else? Does anyone have a packet capture of the commands that the scanners try next when they find the port open? If yes, please share via our contact form or the comments below.


Comments
I am seeing an uptick on this on my home honeypot, and was wondering if he ever got any responses on this.
Additionally, if he figured out what people are actually looking, redis, or something else.
Thank-You!
-= Bruce D. Meyer
Anonymous
May 1st 2018
7 years ago