Incident Response with Triage-ir
In many cases having a full disk image is not an option during an incident. Imagine that you are suspecting that you have dozen of infected or compromised system. Can you spend 2-3 hours to make a forensic copy of hard disks hundred computers? In such situation fast forensics is the solution for such situation. Instead of copying everything collecting some files that may contain an evidence can solve this issue. In this diary I am going to talk about an application that will collect most of these files.
Triage-IR
Triage-ir is a script written by Michael Ahrendt . Triage-ir will collect system information, network information, registry hives, disk information and it will dump memory. One of the powerful capabilities of triage-ir is collecting information from Volume Shadow Copy (v.851) which can defeat many anti-forensics techniques.
Triage-ir can be obtained from http://code.google.com/p/triage-ir/downloads/list . The triage-ir itself is just a script that depend on other tools such as Sysinternals Suite[i], Dupmpit[ii][iii] , Regripper[iv],md5deep[v] ,7zip[vi] and some windows built-in commands .
Here are the installation steps:
- Download Triage-ir
- Unzip it
- Download the dependencies
- Place Sysinternals Suite and Regripper on their own folders under tools foler.
- Place the other dependencies under tools folder
In case of incident you would like to keep minimum residues as much as you can therefore I would suggest to copy it to USB drive ,one issue here if you are planning to dump the memory the USB drive should be larger than the physical ram.
Once you launch the application you can select which info you would like to collect. Each category is separate tab.
Let say that you would like to collect the Network Information only. All you have to do is click on Network Information tab and click on Select none then select all information you would like to collect then click run.
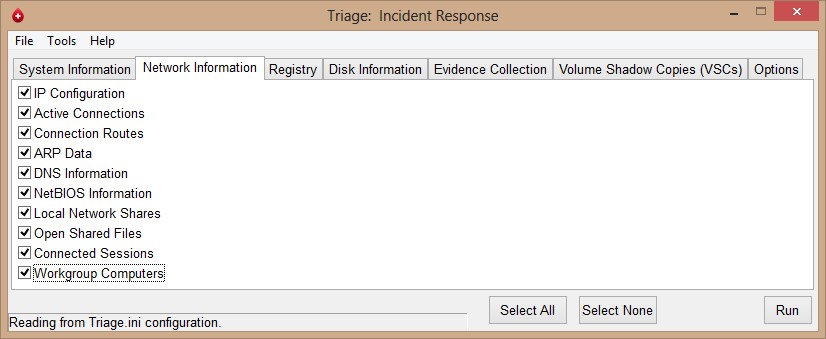
Once the collection process finished triage-ir will prompt you that
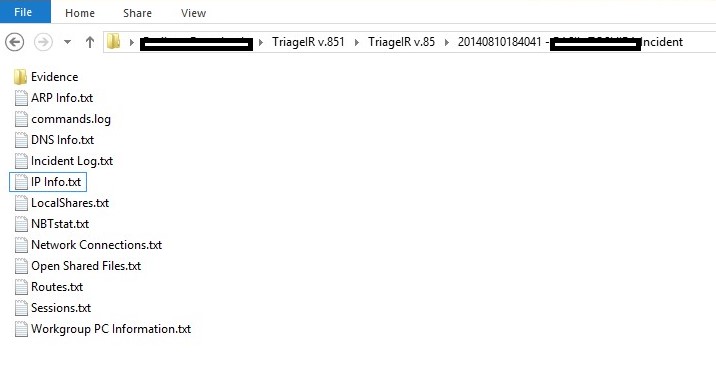
All the collected information will be dumped in a new folder with date and the system name.


Comments
Anonymous
Aug 13th 2014
1 decade ago